Risky Biz News: Crypto-fraud is now bigger than BEC
In other news: UAC-0050 linked to low-tier Russian hacker-for-hire group; 85% of TeamCity servers have been hacked; and 41 US states ask Meta to fix its account hacking problem.

This newsletter is brought to you by Corelight. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The FBI has published its yearly Internet Crime Report [PDF], and the main takeaway from this year's edition is that Americans are really bad at spotting cryptocurrency-themed investment scams.
For the first time since the FBI started putting out its yearly report in the early 2010s, last year, Americans lost more money to crypto-investment scams than all BEC incidents combined.
Americans lost $4.57 billion to investment scams last year, of which $3.94 billion were linked to crypto schemes.
Losses related to BEC attacks accounted for $2.94 billion, a full $1 billion below the crypto fraud number—marking the first time this has ever happened.
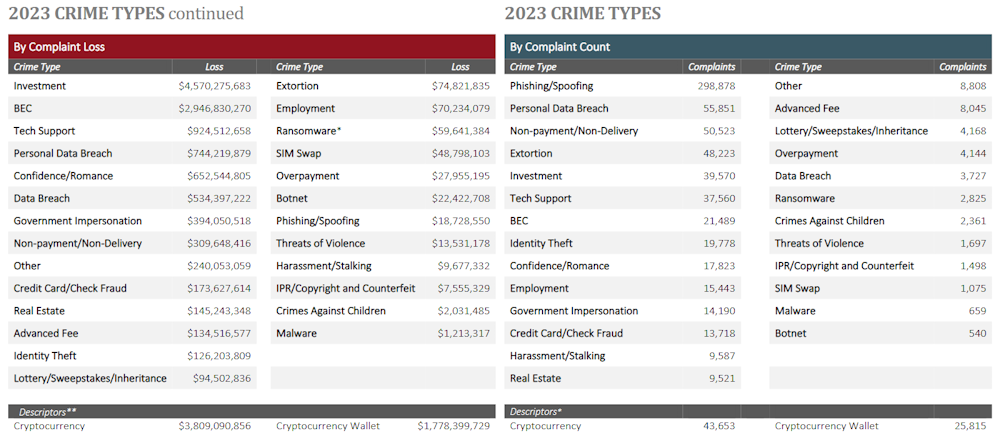
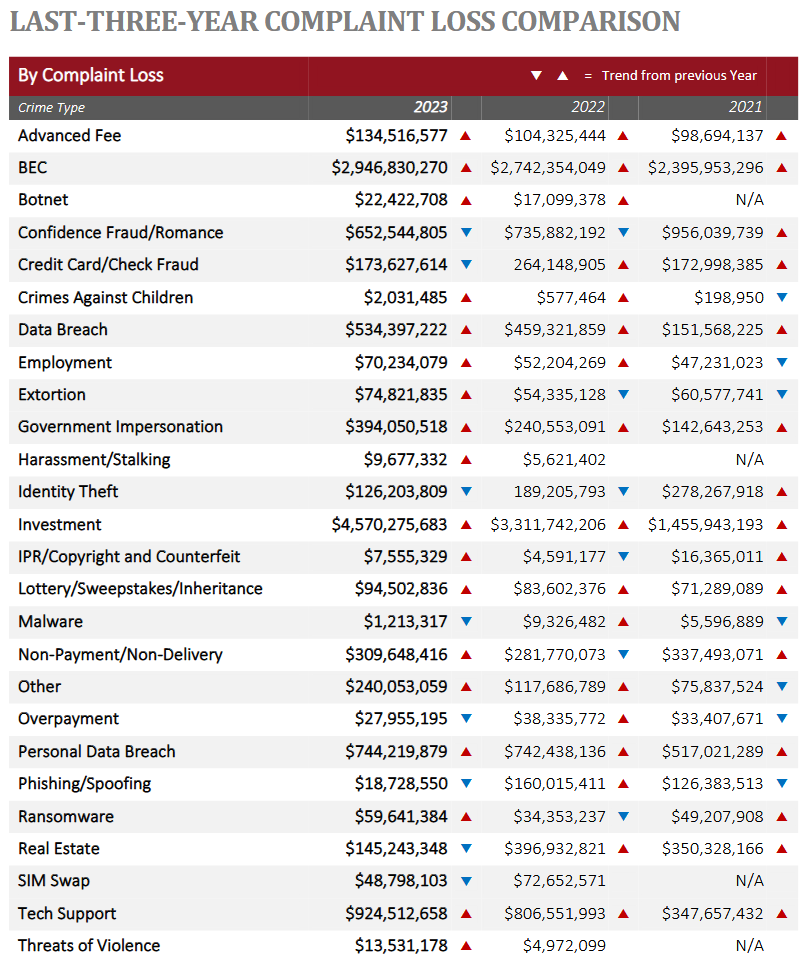
This is significant because BEC had topped the FBI's yearly internet crime report since its first edition and up until 2022 when it was dethroned by investment scams. In 2022, investment fraud accounted for $3.3 billion in losses, with $2.5 billion being crypto-related, while BEC landed around $2.7 billion.
The FBI didn't try to explain why investment and crypto-scams have been so popular last year, but we're gonna give it a go at what we believe led to this explosion.
Reasons are plenty. The easiest one is to look at the Bitcoin exchange rate, which has been going steadily up for the past year. However, that's not really what drives these scams. It only drives users' attention towards the crypto sphere.
A big role in the rise of crypto scams is the proliferation of automated platforms that allow cyber criminals to host fake investment portals with the push of a few buttons.
A large part of the blame is also with social media networks. Companies like Google and Meta often make a profit by not acting on malicious ads that redirect users toward these scams.
At this point, you've probably seen ads using AI-generated voices that impersonate celebrities, financial figures, or politicians, all urging users to invest in this cryptocurrency token or that stock. You've also probably noticed that those ads tend to stay alive for months at a time. If you report some of those ads, you've also probably noticed that both Google and Meta won't remove them.
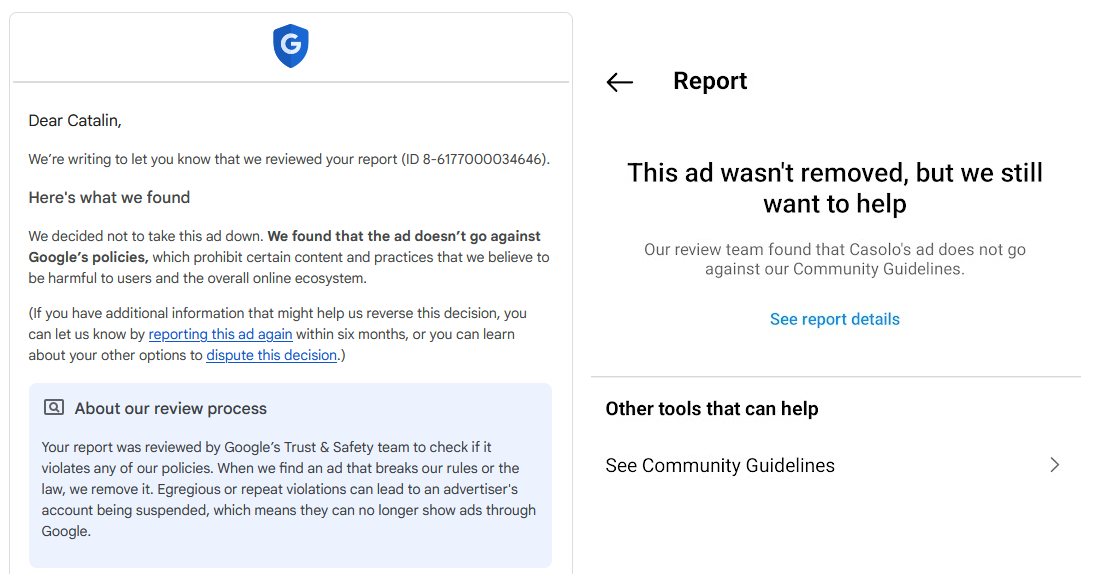
The incentives for social media networks to act on these reports are not there.
Most people also don't really know how this cryptocurrency thing works, so this also breeds fertile ground for more victims to fall for these types of scams in the future.
Apart from the rare law enforcement crackdown on some of these crypto-scam sites and their call centers, it's really not looking good for the non-technical crowd out there genuinely looking to make a valid investment only to be scammed out of their hard-earned money.
Breaches, hacks, and security incidents
Change Healthcare lawsuits: Multiple class-action lawsuits have already been filed against Change Healthcare following its recent ransomware incident. The attack caused a prolonged outage of payments and prescription systems across US pharmacies and healthcare units, and they may actually have a good chance of winning. [Additional coverage in The HIPAA Journal]
FINTRAC incident: The Financial Transactions and Reports Analysis Centre of Canada (FINTRAC), the country's anti-money laundering agency, has been hit by a cybersecurity incident, the agency said this week.
Duvel breweries: Belgian brewery Duvel is dealing with a ransomware attack on its IT systems. The company has halted production at its breweries in Belgium and Kansas, US site. The company says it has enough stock to continue sales. [Additional coverage in VRT News]
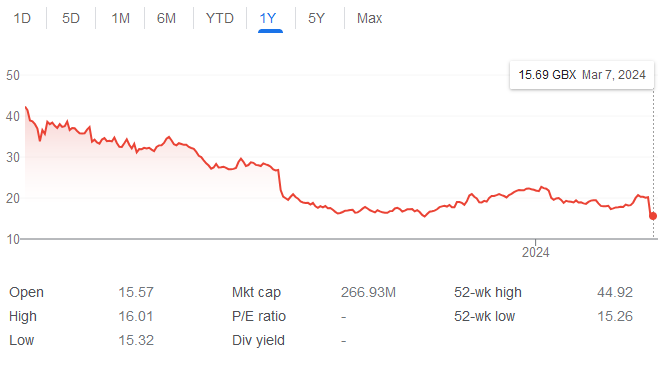
Capita cyber losses: British outsourcing company Capita has reported losses of more than £106 million pounds for the 2023 fiscal year. The company says that almost a quarter (£25.3 million) of the losses are directly tied to a ransomware attack from March of last year. The company's share price went down by 20% following the announcement. The share price is down more than 50% from the day of the attack. [Additional coverage in The Register]
General tech and privacy
Gleam v1: Another memory-safe programming language—named Gleam—has reached its first v1.0.0 stable version.
LineageOS EOL: LineageOS 18.1 has been EOLed since the OS was based on Android 11, which does not receive security updates anymore.
Microsoft WSA EOL: Microsoft has retired its Windows Subsystem for Android (WSA), the technology that allows users to run Android apps on Windows devices.
Signal usernames go live: Signal has rolled out this week version 7.0 of its secure instant messaging client. The new version will allow users to select a username for their account. The username will replace phone numbers as a Signal user's main identifier. Privacy and security researchers have long asked the company to switch from phone numbers to usernames to protect users' identities.
Election and AI misinformation report: The Center for Countering Digital Hate—the organization that got sued by Twitter and Musk for exposing the site's hate speech and misinformation problem—has published a report warning that most AI image generators have easy-to-bypass defenses in place. The research group warns these tools are primed for abuse during the upcoming elections. [Additional coverage in CNN]
AI whistleblower: A lead of one of Microsoft's AI teams has sent a letter to the FTC and the company's top execs warning that Microsoft's AI tools can be abused to generate violent and sexual content. Shane Jones claims the company has yet to address the issues, which have been known for months. [Additional coverage in CNBC]
Google Search's AI spam: Google is rolling out changes to its search ranking to downgrade results from AI content farms. The company says it will also mark as spam websites that had their domain expire and then re-registered by a new entity that then starts pushing low-quality content.
ICO looks at "consent or pay" schemes: The UK's privacy watchdog has started an investigation and a request for comment on "consent or pay" schemes. Also known as Pay-or-Okay, the scheme gives users the option to pay for their privacy online or use a website for free but have their data used for ads. Meta pioneered the scheme as part of its EU GDPR compliance. Several EU privacy groups have filed complaints against the company shortly after the scheme's rollout. They described the new scheme as akin to extortion.
HP quantum-proof PCs: HP has announced a new line of more secure business PCs. The new models will ship with firmware that's resistant to quantum computing attacks. HP plans to implement the feature by deploying various quantum-resistant cryptographic algorithms in their code. More on this new feature is available here.
Meta's IM interoperability: Meta has published details about how it plans to support interoperability with other IM services in the EU.
Epic-Apple drama: Apple has terminated Epic Games' developer account. For those who have not been following the topic, Epic Games is the company behind the immensely successful Fortnite game and Unreal game engine. Epic Games' efforts have led to the EU (and soon other countries) forcing Apple and Google to open their walled gardens to third-party app stores and payment systems.
"In terminating Epic's developer account, Apple is taking out one of the largest potential competitors to the Apple App Store. They are undermining our ability to be a viable competitor and they are showing other developers what happens when you try to compete with Apple or are critical of their unfair practices."
Apple DMA compliance: And since we're on the topic, Apple has published a document on how it plans to comply with the EU's Digital Markets Act. The document details the company's new alternative app store policy.
Government, politics, and policy
US bill seeks full TikTok ban: Two US senators have introduced a bill seeking to ban TikTok from US app stores and US web hosting providers. The two senators claim that TikTok is controlled by a foreign adversary and poses a threat to US national security. The bill would have Chinese company ByteDance divest TikTok in order for the app to survive and avoid a ban. [Additional coverage in CNBC]
NSA zero-trust guidance: The NSA has published another one (its fourth) of its zero-trust guides.
US bill seeks to improve food benefit cards: US lawmakers have proposed a bill to enhance the cybersecurity of food benefit cards. The new Enhanced Cybersecurity for SNAP Act mandates the use of encrypted chip technology for food benefit cards distributed across the US. It forces the US Department of Agriculture and state agencies to issue food benefit cards with secure chips instead of magnetic strips. The proposed bill comes after reports of cybercriminals cloning food benefit cards and stealing funds from vulnerable families.
US OAGs call out Meta over account hacks: Attorneys general from 41 US states have called on social media company Meta to address security issues on its Facebook and Instagram platforms. Officials say Meta has failed to address a "dramatic increase" in user account hacks. Some US states saw complaints about hacked Meta accounts rise from 270% to 740% over the last year. The letter from the 41 US states comes after a similarly embarrassing incident for Meta in the Philippines last week. The country's coast guard had to ask the US embassy for help in regaining access to its hacked account.
"With this letter, we request Meta take immediate action and substantially increase its investment in account takeover mitigation tactics, as well as responding to users whose accounts were taken over. This is crucial not just to protect your users, but to reduce the unnecessary resource burden being placed on our offices to handle these large numbers of user complaints. We refuse to operate as the customer service representatives of your company. Proper investment in response and mitigation is mandatory."
Pakistan backtracks on social media ban: Pakistani senators have withdrawn a resolution that would have banned some social media networks inside the country, such as Facebook, TikTok, Instagram, X (formerly Twitter), and YouTube. [Additional coverage in Dawn]
Russian crime laws: Russian officials are working on an amendment to the Russian criminal code that will classify the use of IT resources to perform a crime as an aggravating circumstance. The update will most likely bring more severe punishments to offenders, although what those are has not yet been decided. [Additional coverage in Izvestia]
Local Russian CERT teams: The Russian government is slowly creating local CERT teams for its various regions that will deal with the increasing number of cyberattacks after its main response center has been flooded since the start of the war. [Additional coverage in Kommersant]
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Vijit Nair, Corelight's VP of Product, about how cloud security was once an afterthought but is now on the improve.

Cybercrime and threat intel
Google engineer charged: The US Justice Department has charged a Google engineer with allegedly stealing the company's AI trade secrets. Officials have identified the suspect as Linwei Ding, a Chinese national living in Newark, California. Ding was detained this week after allegedly transferring more than 500 confidential files on Google's AI technology to his personal account. The secret thefts happened between May 2022 and May 2023. US officials claim Ding was planning to hand over the stolen Google technology to two Chinese AI startups. According to court documents, he was CTO at one of the companies.
BEC scammer pleads guilty: A Nigerian man has pleaded guilty to his role in a BEC group. Henry Onyedikachi Echefu was detained in Canada and extradited to the US in November of last year. One of Echefu's co-conspirators pleaded guilty and was sentenced to 18 months in prison last year.
Incognito exit scam: There are reports that the Incognito dark web marketplace is pulling an exit scam after large sums of Bitcoin were pulled out of the market's wallets.
RU-UA impact on cybercrime: In a paper published this month, British academics say the involvement of cybercrime crews in the Russian and Ukrainian hacktivism scene was "short-lived and fleeting." Researchers say cybercrime groups lost interest in carrying out defacement and DDoS attacks against either Russia or Ukraine after a few weeks. The number of posts on hacking forums also went down in time as cybercrime groups went back to their regular business dealings.
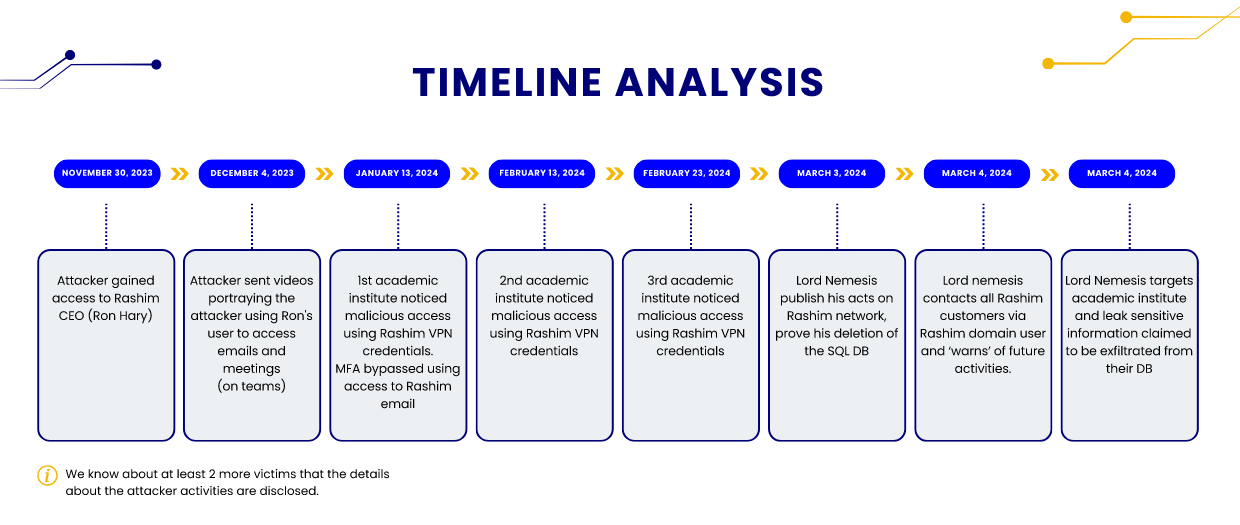
Lord Nemesis activity: OP Innovate has published a report on the recent activity of Lord Nemesis, an Iranian hacktivist also known as Nemesis Kitten. The attacks targeted Israeli organizations.
TA4903: Proofpoint is tracking a new threat actor that is using spoofed US government websites to phish corporate employees and then conduct BEC attacks. TA4903 has launched phishing campaigns that spoofed the US Departments of Labor, Transportation, Commerce, and Agriculture. The group has been active since December 2021 and has used phishing kits capable of bypassing MFA. Proofpoint says the group has increased its tempo, and recent attacks have also relied on QR codes.
Threat/trend reports: Some infosec reports covering industry threats and trends came out from Kaspersky and CIISec.
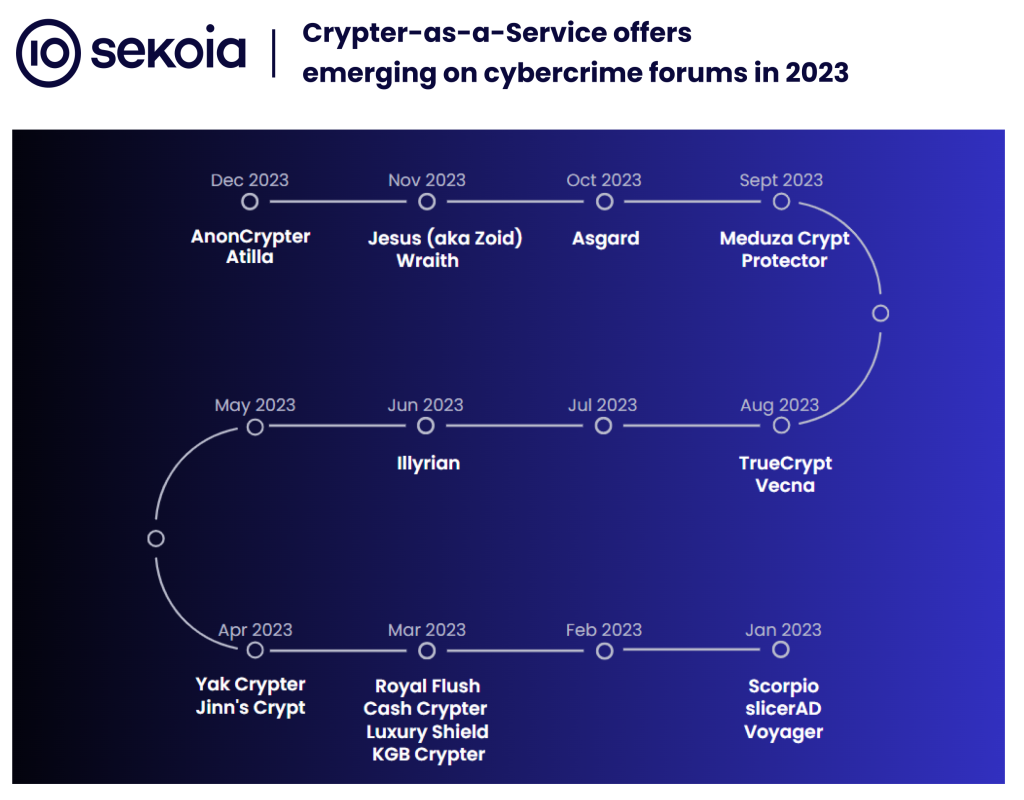
Crypters market: French security firm Sekoia takes a deep and detailed look at crypters and the Crypter-as-a-Service market.
New brute-forcing tactic: A threat actor is using the browsers of users visiting hacked sites to launch brute-force attacks. This is done by placing malicious JavaScript files on compromised WordPress sites. When unsuspecting users visit the site, the script executes in their browser, and they unwittingly test a few credentials pairs as part of the attack. Sucuri says it spotted the new brute-forcing script on more than 1,200 sites.
WP plugin zero-day (allegedly): A threat actor is selling an alleged zero-day in a popular WordPress plugin. The zero-day is being advertised on an underground hacking forum. The attacker claims that more than 110,000 websites are vulnerable to attacks.
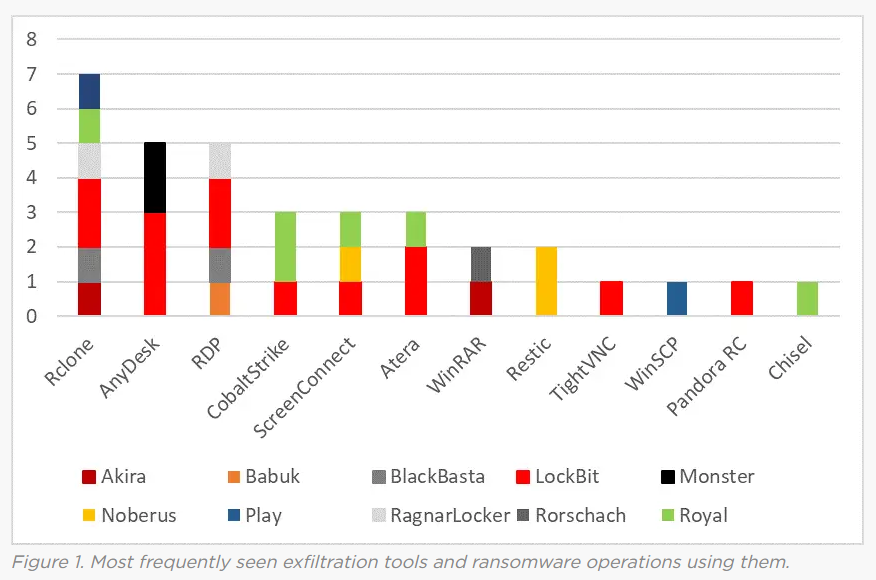
Ransomware data exfiltration trends: Rclone is the tool of choice of most ransomware gangs when it comes to stealing data from compromised networks, according to a new Symantec report.
Malware technical reports
z0Miner: AhnLab takes a look on z0Miner, an old cryptomining botnet that is apparently still alive and still attacking Oracle WebLogic servers.
New botnet: Cado Security has published a report on a new mysterious botnet that is compromising Linux servers running misconfigured or unpatched services like Redis, Confluence, Docker, and Apache Hadoop YARN.
Fakext: IBM X-Force covers a recent Fakext campaign active in LATAM. Fakext is malware disguised in Chrome browser extensions focused on stealing browser data.
CHAVECLOAK: Fortinet has published a technical analysis of CHAVECLOAK, a new banking trojan targeting Brazilian users.
Coper/Octo: Team Cymru has published a deep look at Coper, aka Octo, an Android banking trojan offered as a MaaS on underground cybercrime forums.
AlphV: Something we missed from last week is this report from CrowdStrike on the anatomy of an AlphV ransomware attack. CrowdStrike says the attack they analyzed appears to have been carried out by a rookie. Another report on the same AlphV (BlackCat) gang is available from Trustwave.
"However, it does appear that the different ALPHA SPIDER affiliates who performed the actions described in this blog post have no specific operational security (OPSEC) measures in place to avoid being detected. This lack of OPSEC measures gives defenders numerous opportunities to detect and respond to ALPHA SPIDER affiliates’ operations, as long as they are able to respond in a fast and effective way in the scenario of an ongoing breach."
Sponsor Section
James Pope, Corelight's Director of Technical Marketing Engineering, demonstrates the company's Open NDR Platform and how it combines network detections with a whole host of other data sources.
APTs, cyber-espionage, and info-ops
APT28's OCEANMAP: SecurityScorecard's Vlad Pasca has a technical breakdown of OCEANMAP, a backdoor trojan used by the APT28 Russian cyber-espionage group.
UAC-0050: Equinix threat intel analyst Will Thomas has linked a threat actor tracked as UAC-0050 to a Russian hacker-for-hire gang named The DaVinci Group. UAC-0050 intensified operations after Russia's invasion of Ukraine. It is mainly known for its low-quality spear-phishing attacks against Ukrainian organizations. Ukraine's CERT team previously connected the group to Russian law enforcement. It said that some past intrusions served as initial access for some of the bigger Russian APTs. Thomas described The DaVinci Group as a low-tier cybercrime group trying to move into the Russian cyber contracting sector.
NGC2180: RT-Solar, the security team of Russian telco Rostelecom, says it discovered a new threat actor targeting its customers with a multi-stage malware strain they've named DFKRAT. Researchers say the NGC2180 group has been active since May 2021 and has relied on spear-phishing to deliver its malware.
i-SOON leak: KELA has published its own analysis of the i-SOON Chinese contractor leak.
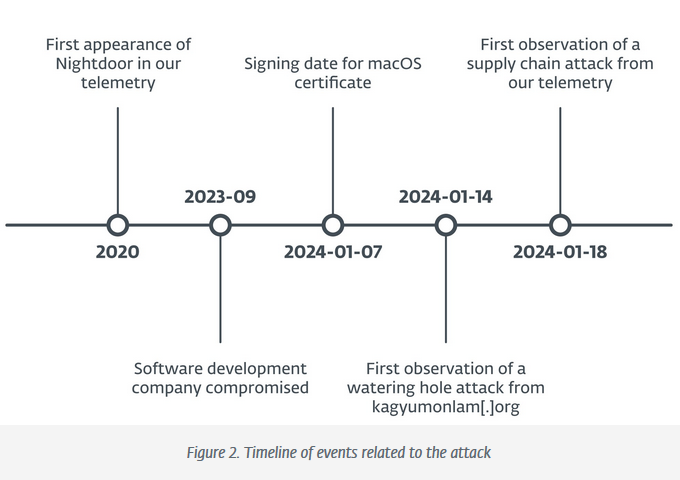
Evasive Panda: A Chinese cyber-espionage group known as Evasive Panda has compromised a Tibetan IT company to deploy malware in its software. The incident took place in January of this year and targeted the company's Tibetan language translation software. The threat actor backdoored the company's Windows and macOS software alike. Security firm ESET says the hack was part of a larger Evasive Panda campaign that started in September of last year and targeted China's Tibetan minority.
Vulnerabilities, security research, and bug bounty
Xunlei Accelerator: Software engineer Wladimir Palant has analyzed the Xunlei Accelerator, a popular Chinese app for boosting download speeds, and found several security issues. These include unpatched third-party code, exposure to MitM attacks, and code execution bugs.
OpenEdge PoC: Security firm Horizon3 has published details and proof-of-concept code for a recently patched authentication bypass in Progress OpenEdge business application servers. The vulnerability is tracked as CVE-2024-1403 and is a rare CVSS 10/10 issue. Exploitation of the issue has been described as trivial. No attacks have been spotted in the wild so far.
JetBrains TeamCity attacks: Threat actors are using two recently patched vulnerabilities to create admin accounts on JetBrains TeamCity servers across the internet. Security firms GreyNoise, LeakIX, and the Shadowserver Foundation have confirmed exploitation. Attacks started earlier this week after proof-of-concept code was posted online. Almost 85% of all internet-connected TeamCity servers have been compromised, according to LeakIX.
Jenkins plugin vulnerabilities: The Jenkins project has published a security advisory warning about vulnerabilities in 12 plugins.
Cisco security updates: Cisco has released or updated seven security advisories for various products.
Unbound security fix: NLnet has released a security update for its Unbound recursive DNS resolver. It fixes CVE-2024-1931, an issue that can lead to infinite DNS loops and server crashes.
Android bug: Meta's red team has published an analysis of CVE-2024-0044, an Android EoP that was patched this month.
Early exploitation reporting: According to a recent VulnCheck infographic, CISA, the Shadowserver Foundation, and Google's Project Zero team have been the top three sources of active exploitation over the past two decades.

Infosec industry
Acquisition news: CrowdStrike has acquired cloud security company Flow Security. The company plans to integrate Flow's products into its Falcon line of products.
New tool—DefenderYara: Security researcher Roadwy has released DefenderYara, a tool to extract YARA rules from the Windows Defender mpavbase and mpasbase databases.
New tool—CloudGrappler: Security firm Permiso has open-sourced a tool named CloudGrappler that can be used for "querying of high-fidelity and single-event detections related to well-known threat actors in popular cloud environments such as AWS and Azure."
New tool—Yasha: Nettitude has open-sourced a new tool named Yasha, a Burp Suite extension to analyze security headers.
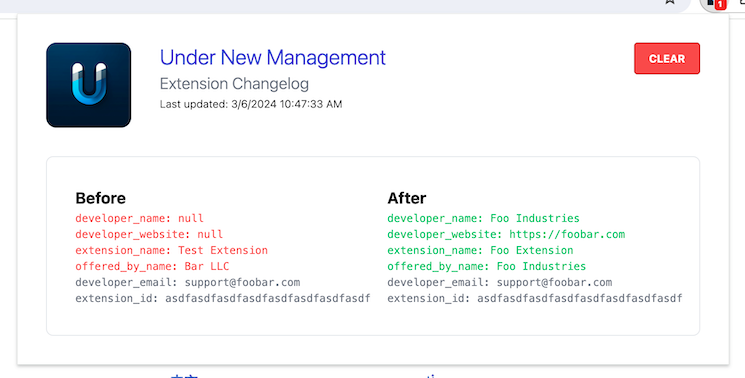
New tool—Under New Management: Software engineer Matt Frisbie has published a Google Chrome extension named Under New Management that detects when your other installed Chrome extensions have changed owner.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the shift that has taken place in Ukraine's cyber strategy as it has gone on the front foot and its cyber forces have launched multiple cyber strikes in the last few months. They discuss reasons why Ukraine might want to make this change and ask whether it makes sense.




