Risky Biz News: Crypto-crime volumes went down in 2022, ransomware payments too
In other news: Riot Games cancels game updates after hack; T-Mobile discloses eighth breach since 2018; APT group deploys DNS changer on victims' routers.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
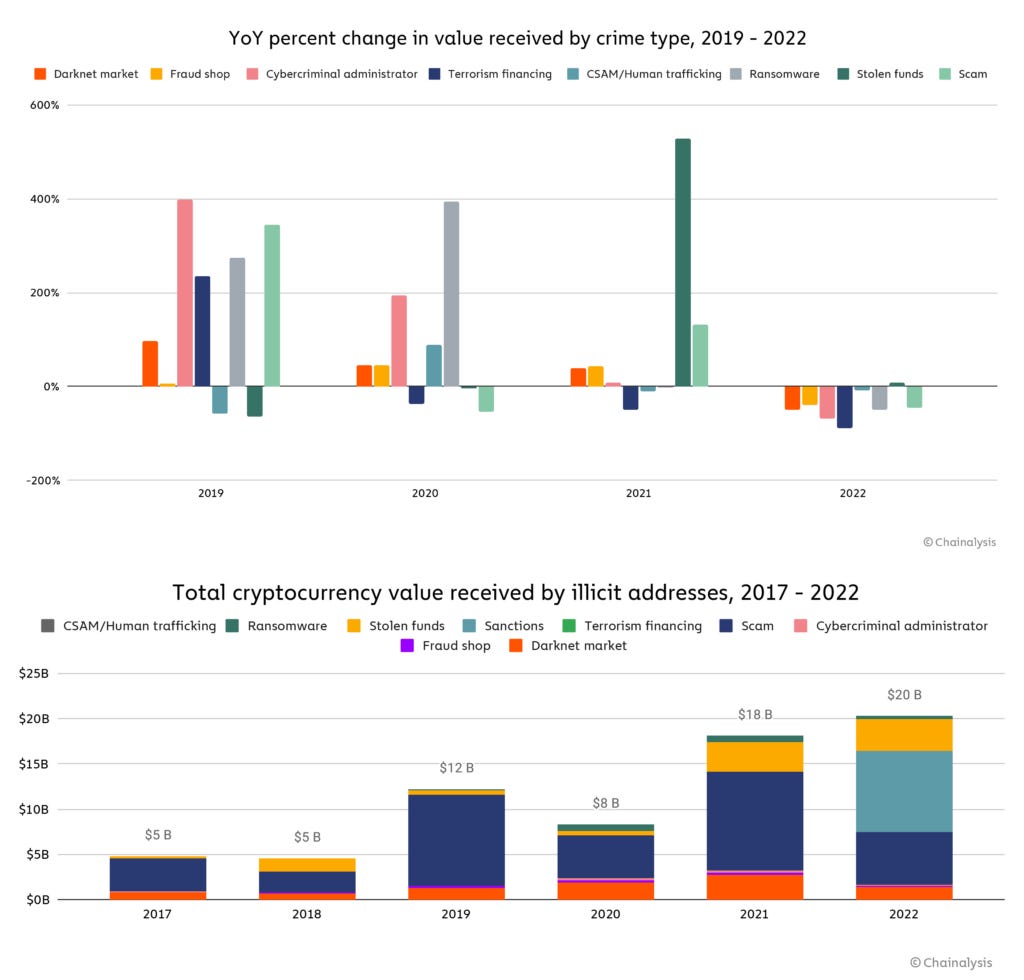
After several years of sustained "growth," 2022 was the first time that the volume of cryptocurrency transactions linked to criminal activity saw a decline (they actually went up, but if we remove the sanctions category, which is more of a gray area, they went down).
Several categories, such as ransomware, scams, darknet markets, financial fraud shops, cybercrime activities, terrorist funding, and CSAM & human trafficking, saw a year-over-year decline compared to 2021, according to a recent report from blockchain analysis company Chainalysis.
The only category that saw growth was "stolen funds," but this comes after a record-breaking year in cryptocurrency platform hacks, with more than $3.9 billion stolen last year.
The reasons for this demise are layered and complex and not the simple and straightforward answer that we can usually find in most cases.
The war in Ukraine, the US Treasury's sanctions crackdown on cryptocurrency money launderers, major law enforcement busts, and the general collapse of the cryptocurrency ecosystem as a whole have all had their role in slowing down criminal operations.
For example, as Chainalysis experts put it—people are less likely to fall for scams if they think the entire ecosystem is down and aren't interested in making new investments.
"The market downturn may be one reason for this. We've found in the past that crypto scams, for instance, take in less revenue during bear markets, likely because users are more pessimistic and less likely to believe a scam's promises of high returns at times when asset prices are declining. In general, less money in crypto overall tends to correlate with less money associated with crypto crime."
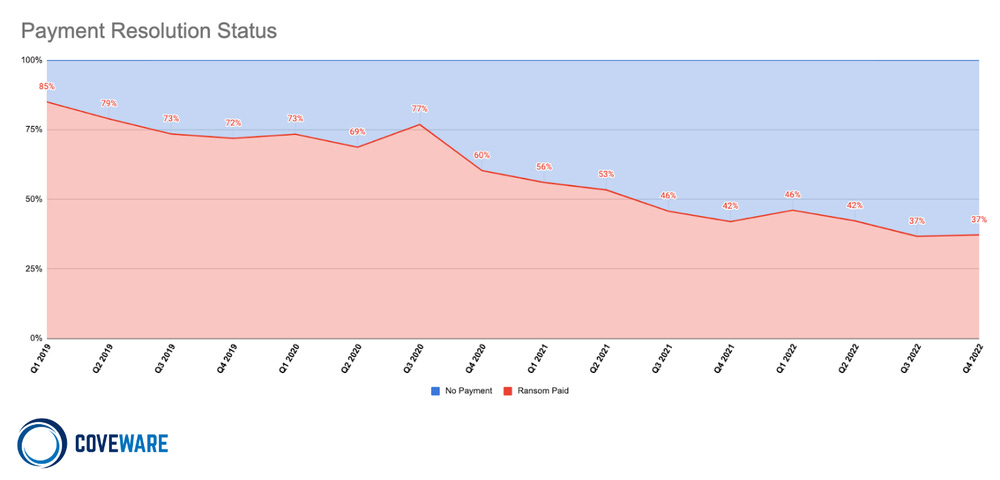
Furthermore, other declines can be explained by other factors. For example, transactions linked to ransomware payments were down last year not because the crypto market was down but because organizations generally stopped paying ransoms as part of a new wider trend—as explained in this separate Coveware report. Chainalysis also saw the same thing and estimated ransomware-linked transactions (payments) last year to be around $456.8 million, down roughly 40% from the $765.6 million ransomware gags made the year before.
Coveware credits this to an improved security posture at many organizations and a wider adoption of backup solutions that made recovering from ransomware attacks without paying to decrypt files less costly.
Obviously, these kinds of reports only cover a small portion of illicit transactions, but they do show some things, such as trends. What we learned over the past year is that government and law enforcement agencies appear to have reached their boiling point when it comes to cryptocurrency and its propensity to be used as a money laundering medium.
Sure, some may criticize the efficiency of the recent sanctions and judicial crackdowns on mixers and shady exchanges. Did these services stop operating? Some, but definitely not all. However, the sanctions have isolated these services and put a damper on some money laundering operations, forcing threat actors to look for new ways to move funds without exposing themselves to tracking and possible asset seizures.
Breaches and hacks
Riot Games breach: Riot Games, the studio behind popular games like Valorant and League of Legends, says it suffered a security breach after one of its employees fell to a social engineering attack. The company says the intruder only gained access to its development environment and that no player data was exposed. Because of the intrusion, Riot says it won't be able to release new content or updates to existing games as it investigates the incident and resecures its systems.
T-Mobile data breach: The US branch of T-Mobile says a threat actor obtained the data of 37 million customers after exploiting its API. In documents filed with the US Securities and Exchange Commission, the carrier said the intruder obtained data such as names, billing addresses, email addresses, phone numbers, and dates of birth. T-Mobile says the data harvesting operation lasted between November 25 of last year and January 5 this year, when its staff detected the intrusion and cut off the attacker's access. The company is currently notifying all impacted users. According to TechCrunch's newest cybersecurity reporter, Lorenzo Franceschi-Bicchierai, the incident represents T-Mobile's eighth breach since 2018.
No-fly-list leak: US airline CommuteAir has leaked a copy of the US' No Fly List, a database of individuals who are not permitted to board flights into or out of the United States. The No Fly List was discovered by Swiss computer hacker Maia Arson Crimew (formerly known as Tillie Kottmann, deletescape, and antiproprietary) while searching the internet for misconfigured Jenkins servers. The researcher told Daily Dot reporters the list contained more than 1.5 million entries, although many were duplicates or different spellings of the same name.
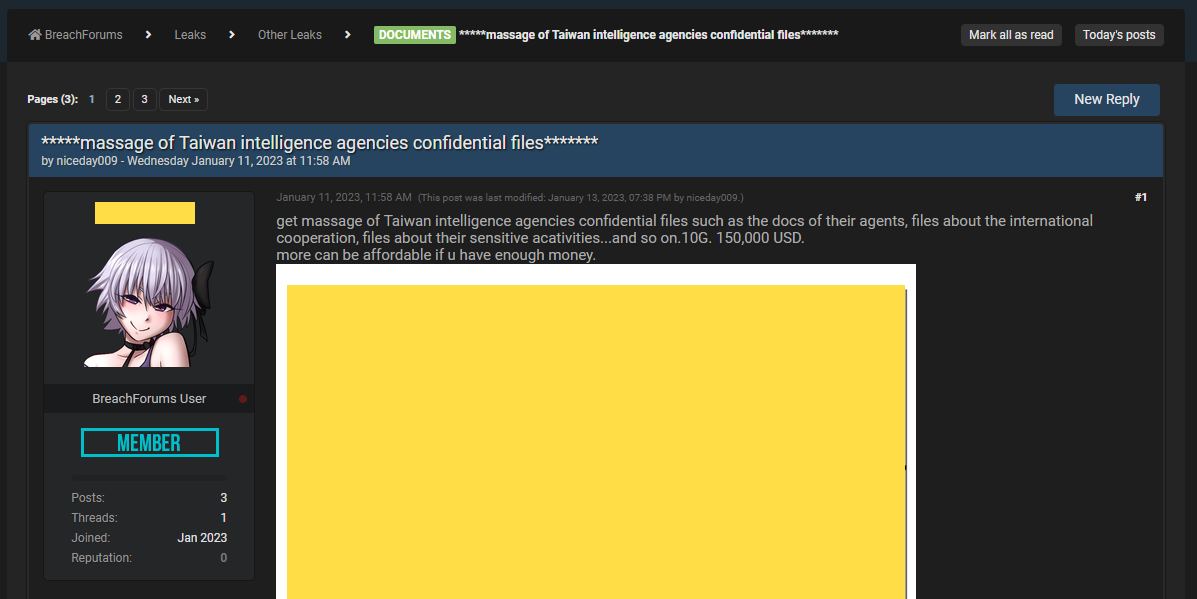
NSB hack: The Taiwanese National Security Bureau (NSB), the country's intelligence agency, is investigating a possible breach of sensitive documents. According to local news outlet Liberty Times, a threat actor leaked a small number of NSB documents on an underground hacking forum earlier this month, asking for a $150,000 payment for the full set of files. Taiwanese authorities have not yet confirmed the authenticity of the leaked documents, most of which are receipts and contracts.
ONACVG hack: Threat actors have breached the servers of the French National Office for Veterans and Victims of War (ONACVG) in December last year. French officials are investigating the incident and if data about French veterans and their veteran card IDs was exposed in the incident. Sources told French news outlet BFMTV they believe the attack was carried out by Russian hackers.
GTA Online hacking: A newly discovered exploit for the Grand Theft Auto Online game allows cheaters to change the status of an account and ban legitimate players. The exploit, which only works against PC players, uses network packets to corrupt game data or alter account settings. Attacks can be prevented using a dedicated Windows firewall rule that detects and blocks network packets typically used by the exploit code. However, the GitLab repo containing this firewall rule was removed over the past weekend as part of a coordinated player boycott against Rockstar Games, the company behind GTA Online. Players are currently urging and warning each other to stop playing until Rockstar fixes their game and the new exploit, which is apparently based on an older bug that was first disclosed last year but has yet to be patched.
General tech and privacy
Netflix to remove account sharing: Movie streaming platform Netflix plans to remove account sharing from its service and re-add the feature as a paid option for subscribers in the coming months, the company said in its most recent earnings report [PDF]. The company's crackdown on users sharing passwords and Netflix accounts comes after Netflix execs identified account sharing as a block to future financial growth in early 2022 [PDF]. The company has more than 230 million paid subscribers but said it expects "some cancel reaction."
Microsoft survey: Because most Exchange servers are years behind on patches and because updating Exchange servers is a known clusterf**k, Microsoft has published a survey and asked for feedback on how it could make the process better.
Firefox security features: Mozilla's security team published a review of its security work on Firefox during Q4 2022. This includes its upcoming WenAuthn+CTAP support, HTTPS by default in Web Extensions, clickjacking & keyboardjacking prevention when using the Clipboard API, and more.
Government, politics, and policy
Cyber-insurance for state-backed cyberattacks: The UK government and insurance companies that provide terrorism-related policies have held talks this week on the possibility of expanding current policies to include state-sponsored and war-related cyberattacks. These types of attacks are not typically covered in classic nor in cyber-focused insurance policies, being usually part of coverage exclusion lists. [More in the Financial Times/non-paywalled link]
Cybercrime in the Netherlands: Dutch police say cybercrime-related complaints have remained at approximately the same levels, with authorities receiving 2% fewer reports compared to the previous year, in 2021 (13,949 incidents last year compared to 14,166 in 2021). However, while they didn't release exact figures, officials said the financial damages last year were "enormous."
Federal agencies sleeping on cybersecurity: A report from GAO, a US government agency watchdog, has found that federal agencies had implemented only 40% of the 335 cybersecurity recommendations GAO had issued since 2010.
NSA IPv6 security guidance: The US National Security Agency has published security guidance [PDF] for the IPv6 protocol so "system administrators identify and mitigate security issues" while they transition to the new protocol from the old IPv4. Some of the NSA's advice includes avoiding using protocol transition tunnels, using "deny all" traffic by default, using security controls that have feature parity between IPv4 and IPV6, using DHCPv6 to mitigate SLAAC leaks, and more. Neal Ziring, NSA Cybersecurity Technical Director:
"The Department of Defense will incrementally transition from IPv4 to IPv6 over the next few years and many DoD networks will be dual-stacked. [...] Networks new to IPv6 lack maturity in IPv6 configurations and tools, and dual-stacked networks, which run on IPv4 and IPv6 simultaneously, have an increased attack surface."
Sponsor section
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. The company has recently released a new type of canary token that's basically a real and valid credit card number. Companies can store the token in one of their systems, and Thinkst will alert them when the card (token) is used somewhere in the real world; alerts that companies can use to investigate possible breaches of their financial data storage systems.
Jacob Torrey on stage at @shmoocon just released our new Credit Card Canarytoken.
— Thinkst Canary (@ThinkstCanary) 5:28 PM ∙ Jan 21, 2023
1) Visit canarytokens.org to create ur own legit credit-card;
2) Place it in a data-store of your choice;
3) Get an alert when an attacker runs that card!
Read more:
blog.thinkst.com/2023/01/swipe-…
Cybercrime and threat intel
More SEO/SERP poisoning: In an edition last week, we covered the rising trend of malware groups switching to using Google search ads to lure users to malicious sites. In case you need one more link, here's a warning about the same trend from the crew at Deutsche Telekom's CERT.
8220 Gang: The 8220 Gang, a Chinese threat actor that is known for targeting and compromising poorly secured cloud servers with crypto-miners and IRC bots, is now heavily targeting Redis database servers. Researchers with cybersecurity firm Radware say they've spotted the gang utilizing an exploit for CVE-2022-0543 to gain access to Redis databases since the start of 2022, attacks that are likely ongoing. In the past, the same gang has also targeted Apache Struts, Apache Hadoop, Apache WebLogic, Atlassian Confluence, and Drupal servers. Back in October 2022, SentinelOne estimated the botnet's size to be around 30,000 infected systems.
Dark web tracking: A team of academics has developed an API that uses information from TLS certificates to link domains from the public internet to their dark web .onion addresses. Their work, also detailed in an academic paper published in December last year, can be used for finding and confirming the legitimate dark web addresses of public websites but can also be used to deanonymize malicious dark web services. Their techniques are not new, but their work has automated a lot of the effort needed to make these connections.
"It is a cooking analogy. An onion that is sauteed becomes transparent."
Malware technical reports
New Emotet evasion technique: BlackBerry researchers have a deep dive into Emotet's latest campaigns and their new evasion modules.
Rhadamanthys: OALABS has IOCs for the new Rhadamanthys stealer.
Album Stealer: Zscaler has a report on the new Album Stealer malware, currently used in a Facebook-hosted phishing operation targeting browser credentials and cookies, but also Facebook Business and Ads-related details. Zscaler researchers believe the threat group launching these attacks may be located in Vietnam. Looks a lot like the Ducktail group, but that would require some additional confirmation from people smarter than me who actually do this for a living.
APTs and cyber-espionage
Gamaredon: Gamaredon, a Russian cyber-espionage group, has developed a novel way of abusing the Telegram instant messaging service as part of its offensive hacking operations. According to BlackBerry security researchers, malicious documents sent to targets will often reach out to a Telegram channel to obtain an IP address where the component for the next stage of the infection process is hosted. BlackBerry says this process repeats several times during an attack in order to make researchers work harder to track the whole attack flow and to find the final payload. Malicious Office documents employing this technique were spotted at the end of last year, and all have targeted organizations located in Ukraine. Previously, Ukrainian officials publicly linked the Gamaredon group to the Sevastopol office of the Russian FSB intelligence agency.
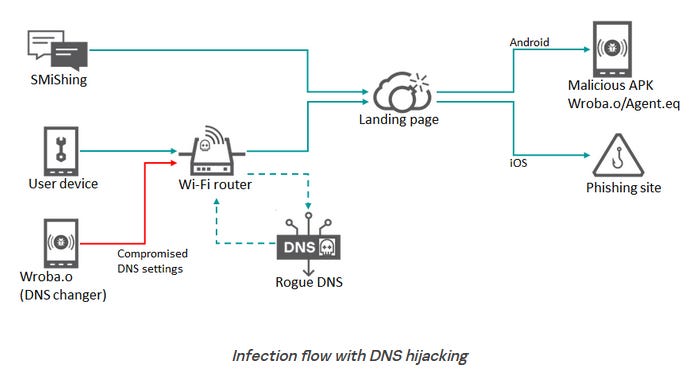
Roaming Mantis: Kaspersky researchers have identified an interesting development in the arsenal of Roaming Mantis, a cyber-espionage campaign that has been active since 2018 and has targeted Asian users with Android malware. According to researchers, the group's Android malware now includes a module that will attempt to hack into a victim's local router and change DNS settings. The role of this new DNS changer module is to redirect a victim's internet DNS queries to a rogue DNS server under the group's control—for both surveillance and to lead users to websites hosting phishing sites or malicious files.
Vulnerabilities and bug bounty
KeePass cleartext passwords: KeePass password manager apps up to version 2.53 are vulnerable to a (disputed) security flaw (CVE-2023-24055) where an attacker with access to a user's system can easily obtain cleartext versions for all passwords stored in the KeePass app by modifying a line in the app's XML config file. Multiple security researchers believe this is a vulnerability because no input from the KeePass owner is required to obtain the passwords, which should not be possible even in situations a threat actor has gained access to a device.
Galaxy App Store: Two vulnerabilities in the Galaxy App Store app (CVE-2023-21433, CVE-2023-21434) can be abused to run malicious JavaScript or install unwanted apps on a device.
"This is a Cobalt Strike (CS) Beacon Object File (BOF) and executable which exploits AMD's Ryzen Master Driver (version 17). It only overwrites the beacon process token with the system process token. But, just like KernelMii, this BOF is mostly just a good foundation for further kernel exploitation via CS. You can utilise it to disable EDR, disable ETW TI, dump LSASS PPL, or do other undetected malicious actions."
CVE-2022-25637: CyberArk researchers have a write-up on CVE-2022-25637, a TOCTOU vulnerability impacting Razer Windows drivers.
EvilESP: IBM X-Force team has a write-up on the EvilESP RCE vulnerability (CVE-2022-34718) in the Windows TCP/IP stack, patched in September last year.
AMD exploitation: Northwave's Tijme Gommers has released a Cobalt Strike beacon that can be used for kernel exploitation on AMD devices.
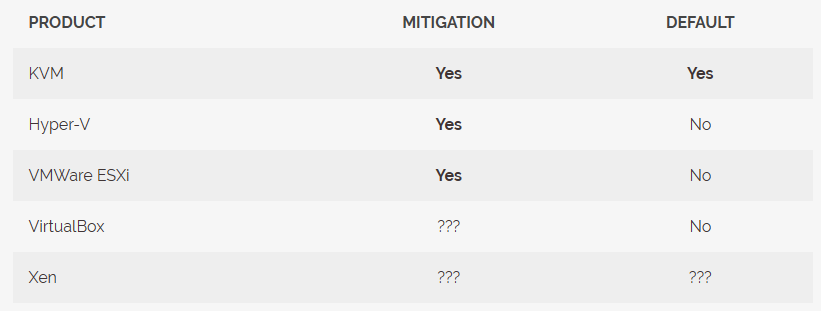
iTLB multihit: Tacito Security researchers have released proof-of-concept code for a vulnerability they named iTLB multihit that affects a large number of Intel CPUs. The vulnerability impacts the translation lookaside buffer (TLB), a cache for the operating system's page table. The bug takes place when the CPU breaks up large chunks of memory and can lead to a DoS attack that can crash cloud servers. Tacito researchers say they discovered the bug in 2017, but they never reported the issue to Intel. Intel eventually found the same issue two years later but said it couldn't patch the bug (CVE-2018-12207) via firmware updates. Instead, operating system and hypervisor vendors released fixes at the software level to add mitigations. However, Tacito says that these mitigations came with a huge performance impact and that most vendors have chosen not to enable them by default, meaning that most hypervisors today are vulnerable to this attack.
Infosec industry
Free courses: MIT's Computer Science & Artificial Intelligence Laboratory (CSAIL) has released more of its free courses. Check out their repo, which has passed over 800 free courses with their latest release.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




