Risky Biz News: Confluence servers under attack due to hardcoded password
In other news: Russian postal service data leaked; new Rowhammer technique disclosed; and new post-quantum cryptography attack.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Confluence server owners are advised to update their installations as news has emerged last week of active exploitation attempts of a vulnerability the company patched in one of its most popular products.
According to Atlassian, the vulnerability (CVE-2022-26138) is a hardcoded password in Questions for Confluence, an app that can be installed on Confluence Server and Data Center on-premise instances to allow employees to ask questions and receive answers from a company's various internal departments.
While Atlassian released a patch that disables this built-in hardcoded account on July 20, Confluence server owners did not get that much of a time window to install fixes, as the username and credentials for this account were published on Twitter a day later by an "annoyed researcher."
As things usually tend to go in Infosecland, it did not take long before these details were put to "good use," and cybersecurity firms Greynoise and Rapid7 reported seeing ongoing exploitation of this vulnerability less than a week after the patch was released.
Since Confluence on-premise servers are broadly used in corporate and government environments, the US Cybersecurity and Infrastructure Security Agency (CISA) has also urged Confluence server owners to check and see if the vulnerable app had been installed on their servers and then install the patches.
Atlassian warned that disabling the app won't fix the issue, and server owners must either install the security fixes or manually disable the hardcoded account created by the Questions for Confluence app:
- User: disabledsystemuser
- Username: disabledsystemuser
- Email: dontdeletethisuser@email.com
News of this issue being exploited in the wild comes after threat actors, including ransomware gangs, exploited another Confluence bug (CVE-2022-26134) a month earlier, and many more other vulnerabilities before that.
I would recommend Confluence be placed behind a VPN or reverse proxy (eg Azure App Proxy) requiring authentication.
— Kevin Beaumont (@GossiTheDog) 8:14 AM ∙ Jul 21, 2022
It’s simply too historically vulnerable to leave online, you’re a sitting duck.
Breaches and hacks
Proxy service hack: The operators of the 911[.]re proxy network said they are shutting down in the aftermath of a data breach that destroyed key components of its business operation, Brian Krebs reported. The shutdown also comes days after the same Krebs published an in-depth look at the shady service earlier this month.
Russian Postal Service leak: Hackers published last week a data trove they claim to have stolen from the official Russian Postal Service. The data contains more than 10 million data points about past shipments. This includes sender and recipient names, addresses, and shipment details. In a statement to local media, Pochta denied the breach and said the hackers obtained the data from a third-party contractor. Russian delivery services have been at the center of several data leaks since Russia's invasion of Ukraine. Past leaks include Yandex Food, DeliveryClub, and CDEK.
OneTouchPoint breach: Marketing platform OneTouchPoint disclosed a security breach last week. The breach is the result of a ransomware attack that took place in April this year, and the company said that 34 healthcare organizations that used its platform had data compromised in the incident.
Another crypto hack: DeFi platform Nirvana lost roughly $3.5 million following a flash loan attack that took place last week. Just like any respectable DeFi platform, Nirvana is now begging the hacker on its knees to return the stolen funds in exchange for a "bug bounty" payment (wink-wink) of $300,000.
1/ 🚨
— FA2 | SolanaFM (@0xFA2) 8:48 AM ∙ Jul 28, 2022
On 28 July, adaptive yield protocol @nirvana_fi was exploited for $3.49M, forcing the protocol’s $ANA token price to collapse over 85%.
The SolanaFM team broke down the key movements involved during the exploit. 👇
Nirvana Hacker Account:
solana.fm/address/76w4SB…
Creos pipeline attack: The operators of the AlphV ransomware claimed to have successfully attacked the Creos Luxembourg natural gas pipeline operator. The company previously disclosed a cybersecurity incident last week but did not specify if it was ransomware.
#Alphv aka #BlackCat claims to have hit a pipeline operator: Creos Luxembourg which operates both natural gas pipelines and electricity networks in the Grand Duchy. 1/3
— Brett Callow (@BrettCallow) 11:15 PM ∙ Jul 29, 2022
Breach costs passed to customers: An IBM report published last week has found that almost 60% of the surveyed companies will pass on the costs incurred and associated with a recent data breach downstream to their customers in the form of price hikes.
General tech and privacy
AdGuard VPN gets blocked in Russia: AdGuard, one of today's largest ad-blocking companies, said that its ad-blocking and DNS privacy services are having issues for Russian users after Russian telecommunications watchdog Roskomnadzor blocked AdGuard VPN servers last week.
Regrettably, their methods were crude, and along with AdGuard VPN, the entire adguard.com domain became unavailable for Russian users. This led to multiple issues with AdGuard Ad Blocker and AdGuard DNS service.
Government, politics, and policy
Tor Android app banned again in Russia: A Russian court re-introduced a ban on the Tor Browser mobile app inside Russia's borders. The Russian government initially ordered Google to remove the app from the official Play Store at the end of May, but the ban was reversed last week following a legal action citing a breach of procedures, only for the ban to be re-introduced days later.
Israel clears police of NSO wrongdoings: An Israeli government commission said last week that Israeli police forces did not break any laws when they deployed the NSO Group's Pegasus spyware in some cases. The Israeli government was forced to investigate the police force's use of the Pegasus spyware after local media claimed they deployed NSO's tools against political activists and not just criminal suspects.
Cybercrime and threat intel
Imminent Monitor RAT author finally charged: Australian authorities have finally charged the creator of the Imminent Monitor remote access trojan, almost three years after Europol cracked down on the operation. Jacob Wayne John Keen, 24, from Brisbane, was charged for creating the widely popular hacking tools, along with his mother, 42, who authorities said profited from the proceeds of her son's crimes.
Russian extortionist sentenced: Russian authorities have detained a suspect in the Kaluga region, near Moscow, on charges of breaking into users' VK social media accounts, stealing private information, and threatening victims to release the data unless they pay a ransom demand.
Raspberry Robin: Microsoft said on Friday that they'd seen instances where the new Raspberry Robin malware has deployed second-stage malware known as FakeUpdates/SocGholish. In the eyes of several security experts, this is a worrying event as the FakeUpdates operation has been previously used to drop ransomware inside corporate networks in the past. More from Katie Nickels, Director of Intelligence at Red Canary, the security firm that initially discovered and documented the Raspberry Robin malware earlier this year.
"Many organizations have observed and publicly discussed Raspberry Robin's initial execution behaviors, but there remained a major gap in that no one seems to have observed any later-stage activity—like an eventual payload. Microsoft's finding that Raspberry Robin has deployed malware called FakeUpdates/SocGholish is an interesting development. Microsoft is certainly credible, but we can't independently verify their claim at this time.
Raspberry Robin itself is an activity cluster that we created based on observed behaviors in multiple different environments. We continue to see Raspberry Robin activity, but we have not been able to associate it with any specific person, company, entity, or country. Ultimately, it's too early to say if Evil Corp is responsible for, or associated with, Raspberry Robin. The Ransomware-as-a-Service (RaaS) ecosystem is a complex one, where different criminal groups partner with one another to achieve a variety of objectives. As a result, it can be difficult to untangle the relationships between malware families and observed activity.
Microsoft's findings suggest that the adversaries behind Raspberry Robin may have some kind of relationship with DEV-0206 and DEV-0243, two groups tracked by Microsoft, but the exact nature of that relationship is unclear. Red Canary has not directly observed Raspberry Robin spreading SocGholish/FakeUpdates, nor are we aware of any clear connection to Evil Corp, DEV-0206, or DEV-0243, but we're watching to see if more evidence emerges to solidify these relationships or if they were simply one-time occurrences."
SafeSound ransomware decrypter: Chinese security firm Rising released a free decryption utility for users impacted by the SafeSound ransomware.
New HiddenAds attacks: McAfee said it discovered 13 apps available on the Play Store that were infected with the HiddenAds adware. The apps were collectively downloaded more than 7.2 million times.
Investment scam network: Security firm Group-IB said it uncovered a network of more than 10,000 malicious sites that are likely being used in an investment scam scheme.
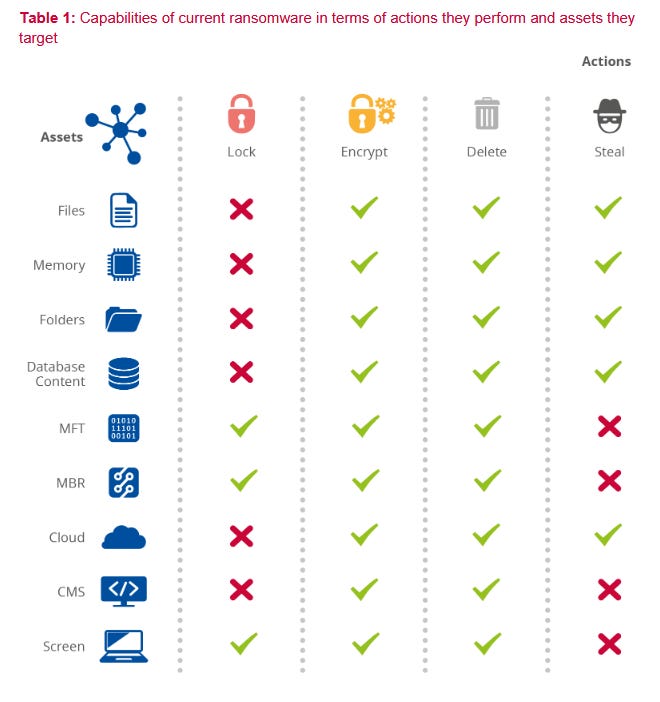
ENISA ransomware report: ENISA, the European Union Agency for Cybersecurity, has published a report analyzing more than 600 ransomware attacks that took place between May 2021 and June 2022. The report introduces the LEDS matrix (Lock, Encrypt, Delete, Steal) that maps ransomware capabilities based on the actions performed and assets targeted.
Malware technical reports
DawDropper: Trend Micro has published a report on DawDropper, a new dropper-as-a-service (DaaS) for Android malware. This new service is advertised on the dark web and has already been seen inside infected apps on the official Google Play Store, where it has been used to push more advanced banking trojans to devices previously infected with the more innocuous DawDropper first-stage payload.
Racoon Stealer v2: Cybersecurity firm Zscaler published a technical analysis of the Racoon Stealer v2 malware. A similar report is also available from Sekoia.
APTs and cyber-espionage
Charming Kitten OpSec mistakes: PwC researchers published a report detailing the operational security (OpSec) mistakes of Charming Kitten (APT35, Yellow Garuda), an Iranian APT known for making such mistakes for years.
Vulnerabilities and bug bounty
New rowhammer research: A team of academics and security researchers from AWS, Google, and others, have published new research last week detailing a new method of conducting rowhammer attacks on computer memory. The attack, named Half-Double [PDF], will be presented at the USENIX security conference in the next few days and is also accompanied by PoC code. According to the research team, the Half-Double attack is "an escalation of [classic] Rowhammer [attacks] to rows beyond immediate neighbors," with the research team creating errors two rows apart from the line of attacked memory cells.
New cryptographic attack: Academics from Belgian university KU Leuven have published details about a cryptographic attack against the Supersingular Isogeny Diffie–Hellman (or SIDH) key exchange algorithm. The SIDH algorithm is an analog of the more well-known Diffie–Hellman algorithm that can be used to establish a secret key between two parties over insecure connections and was designed to resist attacks from quantum computers. According to the research team, their attack can recover keys within one hour. Mathematician Steven Galbraith has more on the topic, along with the following conclusion:
There is no doubt that this result will reduce confidence in isogenies. The sudden appearance of an attack this powerful shows that the field is not yet mature. The relatively recent attack by Ward Beullens on Rainbow has a similar impact on multivariate crypto. The correct response to this is not to attempt to minimise the impact, nor to reflexively declare the subject dead. Instead, we should keep our minds open and let the mathematicians work out the implications, wherever they lead.
Arris router vulnerabilities: Security researcher Derek Abdine published details on Friday on three vulnerabilities in the firmware of Arris routers and all derivative products. Abdine says that while two of the three vulnerabilities are "impractical to exploit," the third is rated critical. The vulnerabilities impact Arris DSL routers, which are usually handed out by ISPs to their customers for at-home connectivity. Abdine says that at least 19,000 such devices can be easily discovered online.
Infosec industry
New tool: Palo Alto Networks has open-sourced a Python library for the extraction of information from .NET Portable Executable (PE) malware files.
SteelCon videos: Talks from the SteelCon 2022 security conference, which took place last week, are now available on YouTube.
TLS test suite: Academics from two German universities have launched a new TLS test suite to evaluate the RFC compliance of Transport Layer Security (TLS) libraries. Named TLS-Anvil, more details will be presented in the next weeks at the USENIX security conference.
As part of our USENIX Security '22 paper, we just released TLS-Anvil, our new blackbox TLS test suite built to uncover even the most subtle bugs within implementations. Let me show you how it works. A 🧵:
— Marcel Maehren (@marcelmaehren) 12:38 PM ∙ Jul 22, 2022




