Risky Biz News: Clop linked to MOVEit hacks, 100+ orgs breached so far
In other news: $35 million stolen in mysterious crypto-wallet hacks; Russian official took $27.7 million bribe from Infraud gang; and passkeys come to Google Workspace and Google Cloud.
This newsletter is brought to you by Stairwell. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Microsoft has identified the threat actor behind the recent exploitation of MOVEit file-transfer servers as our "old friend," the Clop cybercrime group.
Clop itself confirmed its involvement in the attacks in responses to email inquiries sent to Reuters and BleepingComputer reporters.
If the name sounds familiar, this is the same Russian cybercrime group that has previously exploited vulnerabilities in FTA Accellion and Fortra GoAnywhere, two other popular file-transfer appliances.
Just like before, the Clop gang is following the same playbook. The group did its own in-house research, identified a zero-day vulnerability in the MOVEit server (CVE-2023-34362, an SQL injection), and exploited it to backdoor servers by installing a webshell named LEMURLOOT.
The attacks were swift and coordinated. They appear to have started on May 27, over the US Memorial Day extended weekend, when most companies would have been running with skeleton security teams.
The group deployed the webshell and immediately started stealing massive amounts of customer data, grabbing everything they could before they could be detected.
And they were detected. It's unclear by who (although some signs point to Google's Mandiant division), but by Wednesday, May 31, Progress Software released patches for the MOVEit zero-day and started emailing customers about the attacks and the need to patch.
Just like before, Clop is now sitting on a mountain of data, which the group will most likely use to extort companies into paying ransoms. Depending on what they managed to get their grubby little hands on, companies will either choose to ignore their demands or silently reach an agreement with the gang to avoid leaks of intellectual property or regulatory data breach fines.
100+ orgs hacked so far
According to IoT search engines Censys and Shodan, there are currently between 2,500 and 3,500 MOVEit servers exposed on the internet, so the gang's extortion division will probably have its hands full for the coming weeks or months.
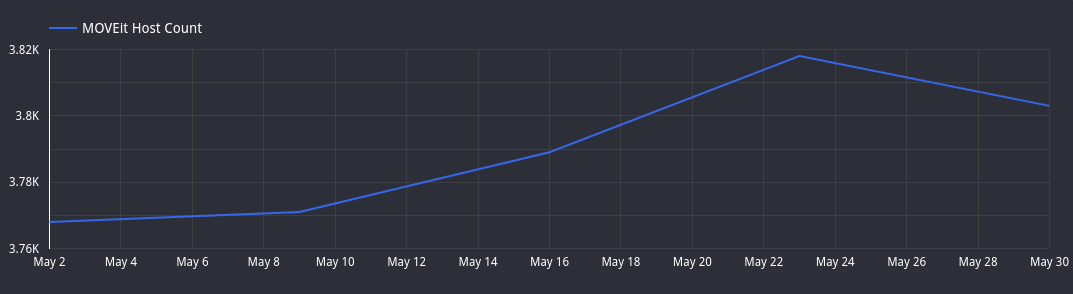
Since the gang's webshell sits on public MOVEit servers, it is easy to track the number of organizations impacted by the hacks. Cybersecurity researcher Kevin Beaumont says there are more than 100 organizations that have had their MOVEit file-transfer servers compromised so far.
Some of them have come out and said they got hacked. Victims who confirmed they'd been breached include the government of Nova Scotia, the University of Rochester, Irish airline Aer Lingus, and payroll service Zellis. The Zellis breach has its own mini-breaches, with the BBC, British Airways, and UK retailer Boots confirming their employee data was taken during the Zellis intrusion.
Mandiant says it was "aware of multiple cases where large volumes of files have been stolen from victims' MOVEit transfer systems," so this list is most likely to grow over the next months as companies have to disclose breaches to national data privacy and regulatory bodies.
Professionalization of cybercrime
But this wasn't a script-kiddie operation. Not even close to it. If anything, the MOVEit attacks are the perfect example of how advanced the cybercrime ecosystem has become, with some of its top players (like Clop) operating on the same level as APT groups and intelligence agencies.
According to GreyNoise, the company says it saw public scans for MOVEit servers as far back as March 3.
This suggests that Clop not only spent time looking for a suitable MOVEit zero-day, but they also compiled lists with servers that could be exploited almost two months before the attacks. That's your typical preparation phase done "à la carte."
The execution phase was also flawless. With more than half of MOVEit servers hosted in the US, it was timed to take place over a major US holiday. As Mandiant and other security firms pointed out, the attacks were swift. Servers were exploited, backdoored, and data was immediately exfiled. No lurking for months.
The monetization phase is now underway, and while not all companies are going to pay, some will. And if you're Clop, you don't need everyone to pay. You just need a few desperate ones, and you immediately turn a huge profit.
Clop members know this, which is why they were upfront with reporters and claimed they're not interested in extorting any problematic victims like military, police, and government organizations. The threat of US CyberCommand or the FBI nuking your servers, seizing domains, or doxxing members still looms large over the cybercrime ecosystem after what happened to operations like Darkside and REvil.
"I want to tell you right away that the military, GOV, children's hospitals, police end etc like that we not to attack. and their data erased. [sic]"
The gang knew what it was after, how to do it, how to prepare the attacks, how to execute them for a maximum success rate, and will most likely squeeze every penny out of victims.
When all of that's done, they'll have a video conference, select the next software suite to attack and use the same playbook again. At this point, it's not a matter of if another wave of attacks will happen. It's a matter of what video conference platform they're using. Is it Zoom or Google Meet? </sarcasm>
As for victims, there is some good news. Rapid7 has identified a way to determine which data was exfiltrated from their MOVEit cloud or on-premise servers and how much was exfiltrated. See the link below.
You can find more on the MOVEit hacks in reports from Deepwatch, HuntressLabs, Mandiant, Rapid7, TrustedSec, and Trustwave.
Breaches and hacks
SAS extortion: Totally-not-Russian hacktivist group Anonymous Sudan is continuing its lame extortion of Scandinavian Airlines. The group is now requesting $10 million from the company to stop DDoS attacks on its websites. This whole thing started from $3,500. If SAS didn't pay that, they're not paying $10 million. This is just a dumb stunt for media coverage. And—of course—as soon as Outlook had an outage this week, this squad claimed responsibility, with zero evidence. They'd wish they had the firepower to crash Outlook.
Atomic Wallet crypto-heist: Users of the Atomic cryptocurrency wallet service have lost more than $35 million worth of crypto-assets after a mysterious threat actor started siphoning funds from their accounts. Atomic Wallet has confirmed the hacks but has yet to discover how they're taking place. The company says that only 1% of its users have been affected. The largest theft was $2.8 million worth of crypto-assets, but multiple accounts also lost six-figure sums. According to blockchain sleuth ZachXBT, the attacks are still ongoing, and they could easily pass $50 million.
Hacked government websites push hacking ads: A threat actor has breached multiple government websites and has published advertisements for hacking services. Official websites that listed the hacking ads included the government portals for six US states, several US counties and local governments, and the federal Administration for Community Living. Websites for 21 US and UK universities were also found to host the same ads, including the sites for Yale, Stanford, UC Berkley, and Oregon State. [Additional coverage in TechCrunch]
Deutsche Leasing incident: German leasing giant Deutsche Leasing says it was the victim of a cyberattack that took place over the last weekend. The company says it detected the attack right away and shut down impacted systems. This includes the company's internal IT systems and its email servers. Deutsche Leasing is one of the world's largest leasing companies, providing leasing services for vehicles, industrial machines, IT hardware, energy equipment, and real estate.

General tech and privacy
YouTube to allow voting disinformation: YouTube has updated its anti-disinformation policy to allow videos questioning the results of elections back on the site. The company says people should have "the ability to openly debate political ideas," bla, bla, bla, more misleading statements that cover the company's fear it might get censored in autocratic countries and lose all that sweet ad revenue.
GitHub adds Swift support: GitHub has added support for the Swift programming language to the platform's security features. Starting this week, GitHub's Dependabot can warn project owners about vulnerabilities in their Swift project's dependencies. Furthermore, support for Swift has also been added to GitHub's CodeQL code scanning feature, allowing researchers to identify basic vulnerabilities in their code with predefined CodeQL queries.
Firefox 113: Mozilla released version 114 of its Firefox browser. One of the most important security-related changes is below.
"Users on macOS, Linux, and Windows 7 can now use FIDO2 / WebAuthn authenticators over USB. Some advanced features, such as fully passwordless logins, require a PIN to be set on the authenticator."
Safari 17 locks private browsing: At its WWDC developer conference this week, Apple announced that with the release of iOS 17 later this year, Safari would include a new feature to allow users to lock their private browsing windows under a FaceID check.
Passkeys come to Google Workspace: Google has announced the general availability of passkey support on its Workspace (formerly G-Suite) and Cloud Platform service. Passkey support is expected to roll out to more than 9 million organizations in the coming days. The feature will allow users to log into their accounts by authenticating against their device using a PIN or biometric challenge instead of typing passwords on Google's login page.
Zoom EEA data storage: Video conferencing platform Zoom has announced new privacy features for its European paid customers allowing clients in the European Economic Area to store certain account data on EU-based servers instead of having it transferred for storage in the US. The move comes after the EU fined Meta a record €1.2 billion for sending the personal data of EU citizens to the US. In addition, Zoom is also adding EU-based support teams to avoid having EU personal data accessed by non-EU staff.
FTC fines Microsoft: Microsoft has agreed to pay a $20 million civil penalty to the US Federal Trade Commission to settle charges that it violated US child privacy laws (COPPA). The FTC says Microsoft collected the personal information of children who signed up for its Xbox gaming system without notifying parents or obtaining their consent. The company also illegally retained children's personal data for years, even from accounts where the parents failed or didn't finish the account creation process.
Government, politics, and policy
More Pegasus in Mexico: Traces of the Pegasus spyware have been found on the phone of Camilo Vicente Ovalle, the Mexican government's lead investigator into human rights abuses by Mexico's armed forces. The news comes two weeks after the Pegasus spyware was also found on the phone of Mexico's under-secretary for human rights, Alejandro Encinas, another investigator on the same team. The pair are investigating the Mexican's army involvement in extra-judicial killings, disappearances, torture, and use of spyware against civilian targets. The Mexican Armed Forces is a known customer of the NSO Group.
Texas passes Data Privacy and Security Act: The US state of Texas has passed the Data Privacy and Security Act. The act has been sent to be signed into law by Texas Governor Gregg Abbott. Once signed, Texas will become the sixth US state to pass a data privacy law. The law will enter into effect on July 1, 2024.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Chris St. Myers, Threat Intelligence Lead at Stairwell, on how the company Inception platform can be used to find old or new threats that sometimes may go unnoticed.
Cybercrime and threat intel
Russian official detained: Russian authorities have arrested one of the lead prosecutors of the Investigative Committee of the Russian Federation for taking a bribe from the Infraud cybercrime group. The committee is Russia's anti-corruption agency and lead prosecuting body. The official has been identified as Marat Tambiev, the head of the Investigative Committee of the Russian Federation (ICR), the country's anti-corruption agency. According to reports in Russian media, Tambiev took a bribe of 1032 bitcoin ($27.7 million) from members of the Infraud cybercrime syndicate in April 2022, months after four of their members were detained by the FSB. Officials believe the bribe played a role in the four Infraud members being set free in March of this year after receiving suspended sentences and after Tambiev's team failed to seize their assets. Russian media claims the case is the largest bribe ever received by a Russian law enforcement officer. Investigators found the bribe on Tambiev's laptop in the form of private keys for two Bitcoin wallets, ironically stored in a folder named "Pension." [Additional coverage in Kommersant and RBC; h/t Brian Krebs]
Jewelry Team: Russian authorities have detained the members of a cybercrime gang named the Jewelry Team that is believed to have scammed Russians out of tens of millions of rubles since January 2021. The group operated using fake ads on Russian travel and carpooling sites, from where they lured victims on phishing sites, hijacked their online accounts, and then attempted to empty bank accounts.
Indian fraud ring busted: Something we missed last month was a massive raids by Indian police in the Nuh district of the Haryana state. Officials say they detained members of a cybercrime group that scammed and defrauded more than 28,000 victims across India of more than $12 million (₹100 crore). The group posted phony sale ads on online marketplaces, collected money from buyers, and then stopped responding. Raids took place in 14 villages, involved more than 5,000 cops, and resulted in the arrest of 125 suspects.
ImpulseTeam's crypto-scams: A Russian cybercrime group known as the ImpulseTeam is behind thousands of websites hosting various cryptocurrency scams. The group used Twitter and TikTok spam to lure victims to their sites and either collect fees or hijack victims' crypto accounts. Cybersecurity firm Trend Micro says it gained access to one of the gang's Telegram accounts, where victim payments were tallied using a bot. The company says that over the course of three months between December 2024 and March 2023, the gang made more than $5 million worth of cryptocurrency. The group's total profit is believed to be much larger, as they've been active for more than two years.
Killnet: Here's another profile on everybody's favorite pro-Kremlin hacktivist group Killnet, this one from Flashpoint. I'm joking. Nobody likes Killnet. They're just a bunch of self-pretentious a-holes.
PCVARK malicious ad-blockers: AdBlock Plus creator Wladimir Palant has published a profile on PCVARK, a company that is behind several malicious Chrome ad-blocker extensions available on the Web Store.
SpinOk: Last week, Dr.Web found 101 Android apps installed by more than 421 million users that contained a malicious SDK. Additional apps containing the same SDK, which is now being tracked as the SpinOk malware, have been found by Indian security firm CloudSEK. This latest finding brings the total to 193 apps. CloudSek says 43 are still available through the Play Store.
Another joint CISA, FBI, NSA guide: CISA, the FBI, and the NSA have released another joint security guide, this time on securing remote-access software against being hijacked and weaponized by attackers against the companies that use it for remote IT administration and management.
Deepfake sextortion warning: The FBI has published a public statement announcement about a recent rise in incidents where scammers have taken benign photos and used deepfake technology to create explicit videos of a person and then extort the victim. Threat actors typically request money, gift cards, or that victims record and send over actual sexually explicit images or videos. Some of these victims have been minors. It's not a novel technique, but with the lower thresholds of skill needed to use deepfake services these days, this is getting very common, as the FBI just noted.
"As of April 2023, the FBI has observed an uptick in sextortion victims reporting the use of fake images or videos created from content posted on their social media sites or web postings, provided to the malicious actor upon request, or captured during video chats. Based on recent victim reporting, the malicious actors typically demanded: 1. Payment (e.g., money, gift cards) with threats to share the images or videos with family members or social media friends if funds were not received; or 2. The victim send real sexually-themed images or videos."
PAN network threats report: Palo Alto Networks' Unit42 has published its yearly report on network threats report, and the company says that last year, attacks exploiting vulnerabilities increased by 55% compared to 2021. In addition, the company also noted a 27.5% rise in malware explicitly targeting the operational technology (OT) industry.
Verizon DBIR 2023: One of the seminal reports in the cybersecurity community is out. The 2023 edition of the Verizon Data Breach Investigations Report examined 16,312 incidents, of which 5,199 were confirmed data breaches.There's a lot to unpack, like in any of the past reports, so here are some of the main conclusions.
- DDoS remained the top cybersecurity incident last year (been #1 since 2020).
- 83% of breaches involved the actions of an external actor.
- Stolen creds, phishing, and vulnerability exploitation were the top 3 breach sources last year.
- 24% of breaches last year originated from a ransomware attack.
- Pretexting (email thread hijacking) is now the most prevalent social engineering tactic, beating phishing for the first time.

Malware technical reports
TrueBot: VMWare's Carbon Black has a summary of TrueBot activity in May 2023. Recent TrueBot infections have leveraged a critical flaw in Netwrix (CVE-2022-31199) and the Raspberry Robin worm for initial access and delivery vectors.
Satacom: Kaspersky has a write-up on Satacom, also known as LegionLoader, a malware downloader that has been active since 2019. In recent attacks, Kaspersky says it saw Satacom deliver malicious Chrome extensions.
"The malicious extension has various JS scripts to perform browser manipulations while the user is browsing the targeted websites, including enumeration and manipulation with cryptocurrency websites. It also has the ability to manipulate the appearance of some email services, such as Gmail, Hotmail and Yahoo, in order to hide its activity with the victim's cryptocurrencies shown in the email notifications."
Android adware campaign: Bitdefender has identified more than 60,000 Android applications that contain a new adware strain. The campaign has been active since October 2022 and has used third-party stores to distribute its payloads. The apps mimic popular games, VPN apps, and security tools typically available on the official Play Store. Some apps also offered cracks and unlock tools for paid apps. The malware's main purpose is to show fullscreen ads, bombard users with push notification spam, and redirect browsers to websites showing ads.
Vice Society: Malwarebytes published an analysis of the Vice Society ransomware gang.
Xollam ransomware: Trend Micro has discovered a new version of the TargetCompany ransomware, currently going by Xollam. Previously, this same ransomware gang has also gone under names like Mallox and Fargo.
Cyclops: A new threat actor known as Cyclops has launched an eponymous Ransomware-as-a-Service, which is currently heavily promoted on underground hacking forums. The new Cyclops ransomware is allegedly capable of encrypting Linux and Windows systems. According to security firm Uptycs, the RaaS platform also grants affiliates access to a stealer component meant to facilitate the exfiltration of sensitive data from compromised environments before they're encrypted. The company notes the gang's tools contain various similarities with the Babuk and LockBit ransomware strains, both of which had their code leaked.

Risky Business Demo
Stairwell's Mike Wiacek demonstrates Stairwell's file analysis and threat detection platform to Risky Business host Patrick Gray. Stairwell helps you monitor and analyze every executable file in your organization, automatically collecting crucial intelligence and providing your security team with in-depth visibility and detections.
APTs and cyber-espionage
PowerDrop: Adlumin researchers have spotted a new Powershell malware named PowerDrop that they say has been used in attacks against the US aerospace industry. Researchers have not tied the malware to any particular threat actor but they believe it may be tied to APT activity.
Kimsuky: Qihoo 360 has published a report on Kimsuky operations distributing the open-source Quasar RAT, primarily against targets in South Korea. Another report from SentinelOne looks at the group's recent campaigns where they deployed the ReconShark malware. This last campaign has targeted experts in North Korean affairs from the non-government sector.
TAG-71: Recorded Future has identified infrastructure linked to a North Korean APT group known as TAG-71 that has been used in operations targeting financial institutions and venture capital firms in Japan, Vietnam, and the US. The company says it identified 74 domains and six malicious files linked to the group. The infrastructure was used in operations that took place between September 2022 and March 2023. Recorded Future says TAG-71 activity overlaps with what other security firms track as APT38, Bluenoroff, Stardust Chollima, and CryptoCore.
ITG10: On the same note, IBM X-Force has a similar report on North Korean espionage, this one on ITG10, a group known as ScarCruft, Reaper, and APT37. The campaign targeted the South Korean government, universities, think tanks, and dissidents and delivered the RokRAT malware.
UAC-0099: CERT-UA has published a security alert on an espionage campaign conducted by the UAC-0099 APT that targeted Ukrainian state organizations and media representatives. The agency says the group successfully gained access to several dozens of computers in Ukraine in 2022 and 2023. Malware deployed in the attacks includes the LONEPAGE downloader, the THUMBCHOP infostealer, and the CLOGFLAG keylogger. The group also used new tools like SEAGLOW and OVERJAM, two malware strains written in the Go programming language and on which details are still scarce.
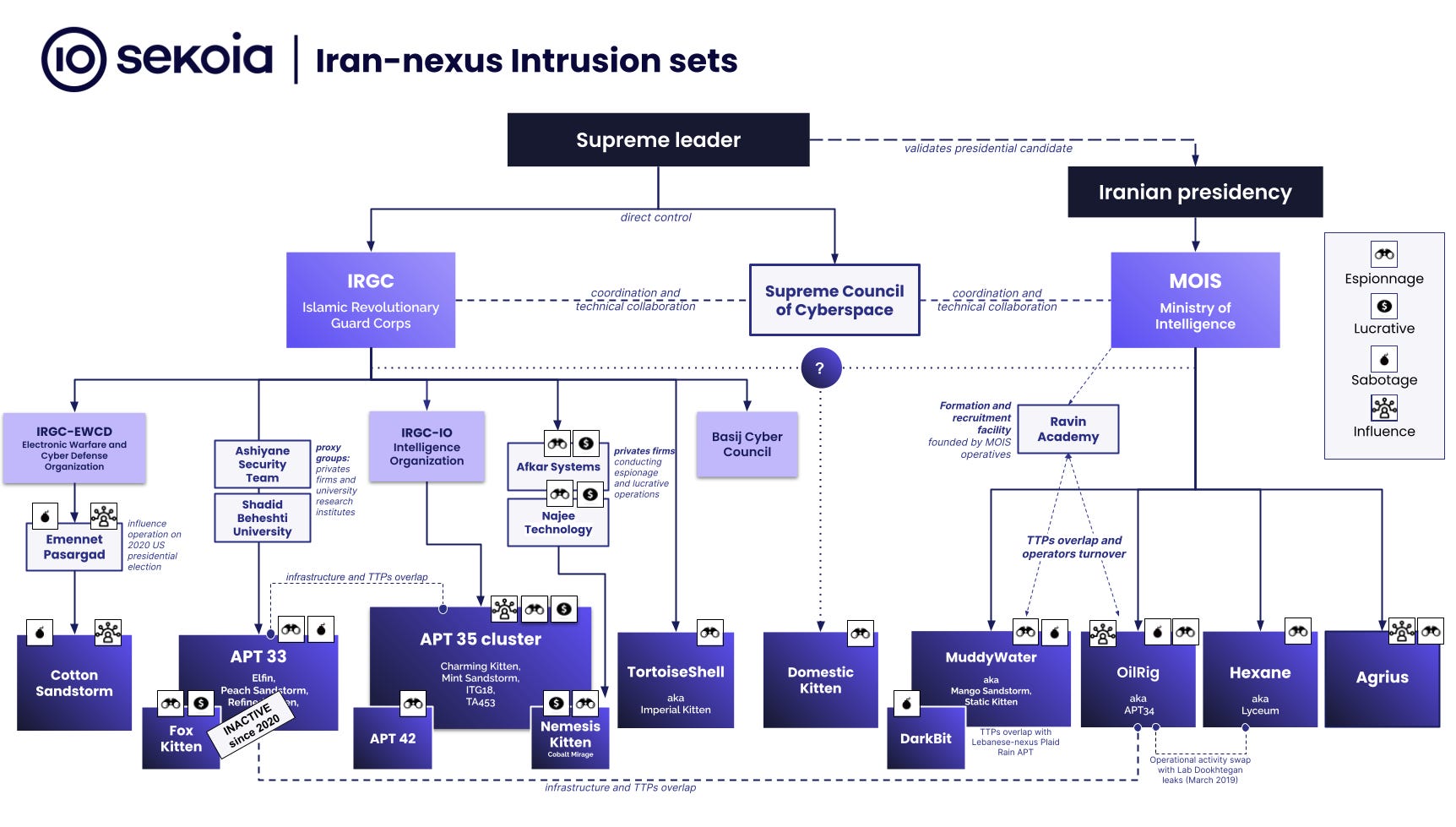
Iranian APTs: Sekoia has published a top-down overview of the Iranian cyber landscape.

Vulnerabilities and bug bounty
Chrome zero-day: Google has released a security update for its Chrome desktop and mobile browser to address a zero-day vulnerability (CVE-2023-3079) exploited in the wild. The zero-day was discovered by its TAG security team.
RCE on Mozilla's Mercurial: GitLab security engineer Joern Schneeweisz has discovered an RCE vulnerability in Mozilla's Mercurial SCM. The issue is now patched. The write-up is here.
Roundcube RCE: Researchers have identified an RCE vulnerability in Roundcube's MarkAsJunk plugin. Roundcube is a popular webmail software package.
Dassault Delmia vulnerabilities: Synacktiv researchers have identified three vulnerabilities [PDF] in Dassault Delmia Apriso, an enterprise performance and process management suite. All issues have been patched.
RenderDoc vulnerabilities: Qualys researchers have identified three vulnerabilities in the RenderDoc graphics debugger.
KeePass security update: Password management app KeePass has released a security update to address CVE-2023-32784, a vulnerability that can be exploited to dump the cleartext version of the app's master password. A PoC was released for this bug last month.
Android security updates: ...for June 2023 are out! This month's updates also include a fix for CVE-2022-22706, a zero-day used by Spanish spyware vendor Variston in attacks against Samsung Browser users in the UAE last year.
Infosec industry
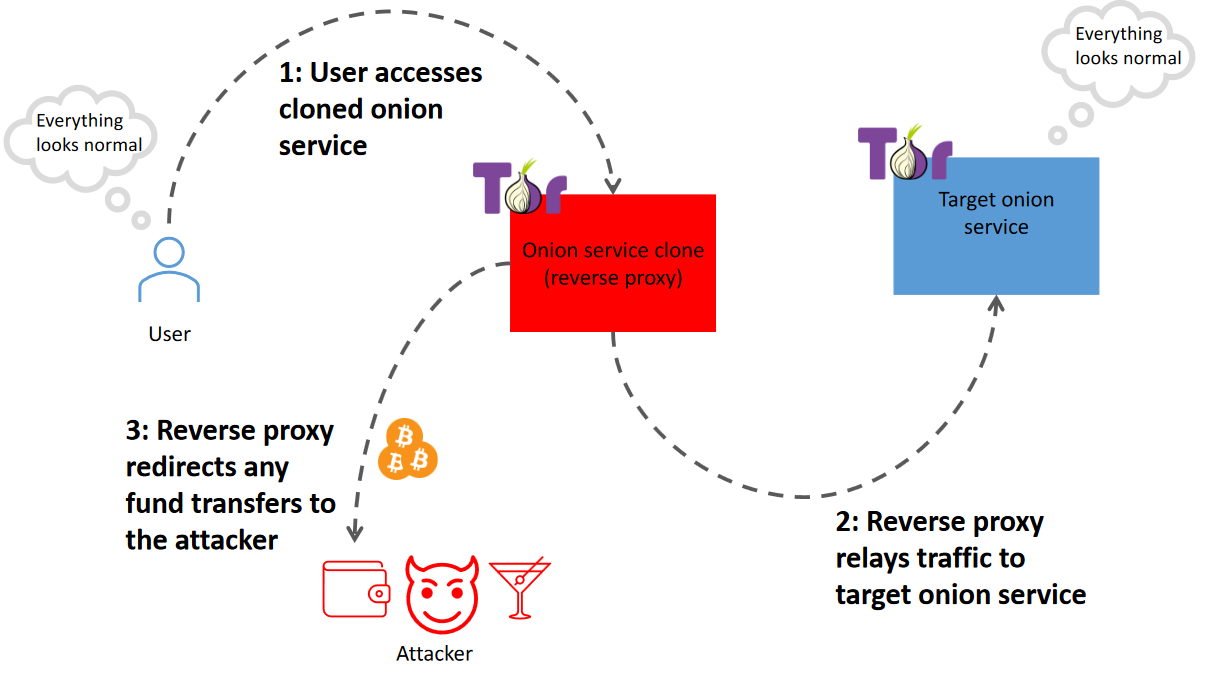
New tool—eBPFGuard: Security firm Deepfence has open-sourced eBPFGuard, a Rust library for writing Linux security policies using eBPF. The company says it uses the library for some of its own security tools.
New tool—OF: Security researcher Valtteri Lehtinen has open-sourced a tool named Onion Fermenter, a proof of concept for Bitcoin stealing man-in-the-middle (MitM) attacks against TOR hidden services on a large scale. Lehtinen argues OF could be used to rip off cybercriminals, but I see situations where this is weaponized against regular Tor users as well (yes, there are a few of those still around).