Risky Biz News: Clarifying the "DOD can't use software with vulnerabilities" misunderstanding
In other news: Estonia reports record DDoS attacks; Brazil police conduct raids in Lapsus$ investigation; and Ryuk money launderer arrested.
This newsletter is brought to you by Airlock Digital, Proofpoint, RunZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Since we launched back in May, the RBN newsletter's format has been to list short summaries of recent cybersecurity-related news and have a featured slot at the top dedicated to an important topic we want to highlight in each edition. Typically, this topic is related to recent events, expanding on ongoing events that have taken place since our last newsletter.
Today, we're taking a different approach, and we're focusing on a viral Twitter thread regarding a clause that was spotted in the National Defense Authorization Act, a bill passed by the US House in July and which authorizes Department of Defense (DOD) activities and expenses for fiscal year 2023.
The tweet claims that contractors would not be able to sell software to the DOD if the software contains any vulnerabilities with a known CVE in it.
However, that is not an accurate read of the bill's text. What that specific section of the bill says is that software vendors will have to submit a software bill of materials (SBOM) for their products, where they will have to list the components/libraries used for the final product and that they are "free from all known vulnerabilities or defects affecting the security of the end product or service."
However, as several security researchers have pointed out already on Twitter, vulnerabilities in some libraries may not impact the final product, as the vulnerable code may not be invoked or might be mitigated through other product design choices.
Furthermore, the same clause also specifies that software can be used if the vendor enumerates and provides mitigation plans for all known vulnerabilities.
As several people have also pointed out, what this NDAA section does is codify POAMs (Plans of Action & Milestones) into law, procedures that allow government agencies to handle and mitigate risk and which have already been in place with most US military and intelligence agencies for many years.
This is just codifying existing POA&M-driven remediation processes into law. Three-letter agencies already do this, so it's nothing new.
— Haris Khan (@hariscodes) 1:28 AM ∙ Aug 18, 2022
There’s a process the DoD uses to do risk assessment and mitigation for things like CVEs, STIG violations, or other flaws in information systems. Sometimes patches or fixes cannot be applied so POAMs are developed to mitigate the risk elsewhere
— The Cyber (@r0wdy_) 3:57 AM ∙ Aug 18, 2022
Most of the time these extremely flawed systems are rubber stamped with risk acceptance anyway because its the best option vs not fielding the system(s). Don’t see any difference here with vendors 🤷♂️
— The Cyber (@r0wdy_) 3:57 AM ∙ Aug 18, 2022
This doesn’t “ban” the DoD from procuring software with cves at all nor does it require software that is perfect. It just codifies the process which documents how the risk of the vulnerability is being mitigated by the vendor. Again, something the DoD already does internally
— The Cyber (@r0wdy_) 4:04 AM ∙ Aug 18, 2022
But one thing that came out of yesterday's misunderstanding is that the Twitter thread also helped surface another section in next year's NDAA, namely that the DOD can now issue funding for open-source projects and help them improve their security posture.
According to section 323 (k), the DOD will soon be able to issue grants to sponsor security audits in open-source projects, fund developers to patch certain vulnerabilities in their projects, and even fund FOSS infrastructure and code overhauls, such as "rewrites of open source software components in memory-safe programming languages." 😎
The US National Defense Authorization Act also includes grants to open source projects for audits, patches, assessment tools, and refactorings, including rewrites "in memory-safe programming languages".
— Arie van Deursen (@avandeursen) 12:48 PM ∙ Aug 18, 2022
Breaches and hacks
WestJet app leak: Canadian airline WestJet suffered a glitch in its mobile app that logged in users into its mobile app into different profiles, allowing them to view other people's personal details.
Kronos ransomware aftermath: Oregon hospital St. Charles Health System is asking its employees to return $2 million mistakenly paid in wages. The hospital paid employees "too much" after a ransomware attack impacted UKG Kronos, its time-keeping service, last year.
General tech and privacy
Google wins defamation lawsuit: Australia's high court ruled [PDF] that Google is not liable for defamation charges just because it listed a "controversial" article in its search results.
DNS failures in China: According to an academic paper, around 13.5% of all DNS queries performed in China fail to get resolved. According to APNIC, the majority of failures occur on a small set of domains.
Joomla adds MFA support: The Joomla team has released v4.2, which now supports multi-factor authentication for securing CMS accounts. Support is included for Yubikeys, WebAuthn, verification codes, or code by email. More here.
Government, politics, and policy
CyberCom faces staffing issues: Cyberscoop reported on Thursday that US Cyber Command has been facing staff shortages, an issue that appears to have been caused by the DOD's regular policy of rotating staff every 2-4 years.
Department of Defense staffing norms require staff to rotate every few years. Since Cyber Command receives talent from outside its ranks, it is also subject to the whims of the various military services, which rotate their brightest people to Cyber Command for anywhere from two to four years, asking for them back, experts and former officials say, just when they have mastered the complexities of the cyber mission.
New CyberCom hunt forward mission: US CyberCom said on Thursday that it successfully concluded its 35th "hunt forward" mission. These are initiatives where the US agency sends cybersecurity experts to countries across the globe to help them uncover advanced malware and defend against incoming cyber-attacks. So far, CyberCom has sent hunt-forward missions to 18 countries, and its last one took place in Croatia, where they worked with the country's Security and Intelligence Agency.
US warns banks: The US Consumer Financial Protection Bureau has urged US banks and financial institutions to deploy software updates to their systems, as well as multi-factor authentication to protect consumer accounts, as failure to do so might lead to fines under the Consumer Financial Protection Act (CFPA).
Lloyd's clarifies cyber-insurance coverage: Lloyd's, one of the world's largest providers of cyber-insurance, has issued guidelines [PDF] to partners to clarify its coverage exclusion policies surrounding incidents linked to state-backed threat actors.
"This clause must be in addition to any war exclusion (which can form part of the same clause or be separate to it)."
Estonia sees record DDoS attacks: The Estonian government said that it saw some of the largest DDoS attacks in its history this week as part of a series of attacks against both public institutions and the private sector, including its e-Estonia portal. Despite this, Luukas Ilves, an official for Estonia's Ministry of Economic Affairs and Communications, said the attacks did not lead to extended disruptions. According to Estonian news site ERR, the attacks were claimed by Russian hacktivist group Killnet.
Yesterday, Estonia was subject to the most extensive cyber attacks it has faced since 2007. Attempted DDoS attacks targeted both public institutions and the private sector. (1/4) @e_estonia
— Luukas Ilves (@luukasilves) 3:25 AM ∙ Aug 18, 2022
Cybercrime and threat intel
Lapsus$ investigation: Brazil's Federal Police carried out eight search and seizure warrants Tuesday as part of an investigation into attacks claimed by the Lapsus$ Group that disrupted the country's Ministry of Health last December. Police did not specifically name Lapsus$ Group in the announcement. However, the details described line up with the Lapsus$ Group attack, The Record reported.
Ryuk money launderer arrested: The DOJ said it managed to secure the arrest and extradition of a Russian national from the Netherlands for his alleged role in laundering funds linked to past Ryuk ransomware payments. Authorities identified the suspect as Denis Mihaqlovic Dubnikov, 29, and said he laundered $400,000 in Ryuk payments as part of a group who laundered at least $70 million in ransom proceeds.
Successful sale: Threat intel analysts reported this week that the source code of the Predator The Thief and Taurus infostealers was successfully sold to a new malware author this week.
Predator The Thief and Taurus Project source codes were sold for $2500 to Alan Wake on the XSS forum. After completing the deal, the seller was banned at his own request.
— 3xp0rt (@3xp0rtblog) 7:32 PM ∙ Aug 17, 2022
Darth Maul market: CuratedIntel's William Thomas has a pretty nifty report on Darth Maul (aka 1977.sh), a new and emerging e-crime market known for the trading of personal data and compromised accounts.
Killnet analysis: Threat intel outfit Flashpoint has an analysis of Killnet, one of Russia's most active hacktivist groups.
TA558: Similarly, Proofpoint also has released a report on the activities of TA558, a financially motivated small crime threat actor targeting hospitality, hotel, and travel organizations since at least 2018.
TA558's targeting focus is mainly on Portuguese and Spanish speakers, typically located in the Latin America region, with additional targeting observed in Western Europe and North America. TA558 increased operational tempo in 2022 to a higher average than previously observed.
Attacks on OpenCart stores: Web security firm Trunc said it spotted a threat actor attacking OpenCart sites with more than 900 SQL injection variations.
New DDoS record: Google said it blocked a record HTTPS-based DDoS attack that hit a whopping 46 million requests per second, 76% more than the previous 26 million RPS attack mitigated by Cloudflare in June. Google did not disclose the target of this attack but said that it believes the attack was carried out with the help of the Meris botnet.
To give a sense of the scale of the attack, that is like receiving all the daily requests to Wikipedia (one of the top 10 trafficked websites in the world) in just 10 seconds.
Cryptominers getting more stealthy: Microsoft reported on Thursday that cryptomining malware strains have become more stealthy as they adopted living-off-the-land binaries (LOLBins) to evade security software, leading to a dip in detections since the start of the year.
VT advice: The VirusTotal team published a how-to on hunting for malicious Office documents uploaded on its platform that may contain code to exploit the Follina Office zero-day.
GitHub incident: Arnica, a company specializing in software supply chain security, published a breakdown of an incident that took place earlier this month when a threat actor flooded GitHub with more than 35,000 backdoored projects.
Google Translate abuse: A Certitude report published earlier this month describes how email spammers and phishing operators have been using Google Translate's URL to bypass domain blacklists for email security gateways and deliver malware and phishing links to users.
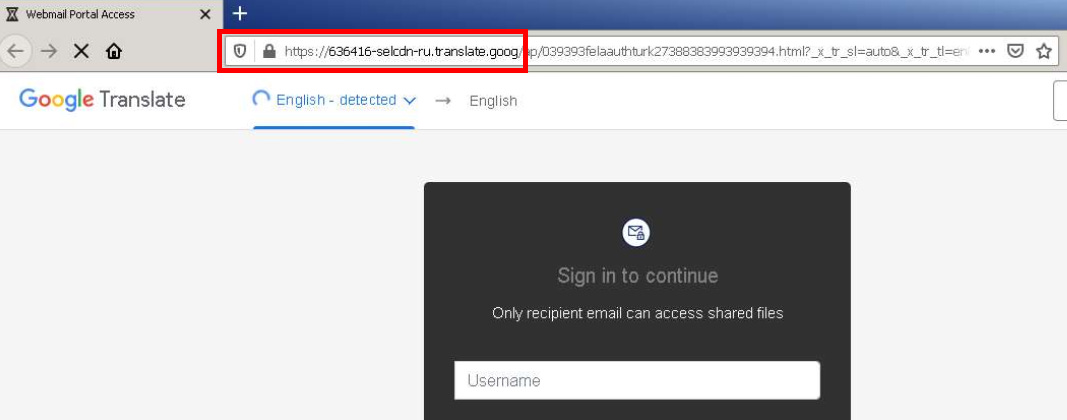
BEC hard truths: Cofense's BEC expert Ronnie Tokazowski has a basic breakdown of the BEC and romance scams landscape, along with some of its darker side, such as voodoo magic rituals and even some of the murder-as-sacrifice that some groups practice. Yes, you read that right: murder-as-sacrifice.
Malware technical reports
Bumblebee: IBM X-Force said in a report published on Thursday that it "uncovered evidence that suggests Bumblebee malware, which first appeared in the wild last year, was likely developed directly from source code associated with the Ramnit banking trojan."
This newly discovered connection is particularly interesting as campaign activity has so far linked Bumblebee to affiliates of the threat group ITG23 (aka the Trickbot/Conti group), who are not known to have had a previous connection with Ramnit.
DarkTortilla: Secureworks published a report on DarkTortilla, a complex and highly configurable .NET-based crypter that has been active since at least August 2015 and used to hide payloads for recent threats, such as AgentTesla, AsyncRat, NanoCore, and RedLine.
Adware on the Play Store: Bitdefender said it identified 35 applications that have snuck into the Play Store. The apps are configured to show intrusive ads to users and appear to have been downloaded more than two million times.
AdSearch adware: Red Canary says that an activity cluster it tracks as AdSearch rocketed to the #1 spot in its Top 10 Threats list in July. The group uses malvertising to trick Windows into downloading an ISO file. The final payload is a browser hijacker that modifies browser settings and redirects users to ad websites, similar to another threat the company tracks as ChromeLoader.
AsyncRAT: Qualys researchers have published an analysis of the command & control mechanism used by the AsyncRAT malware.
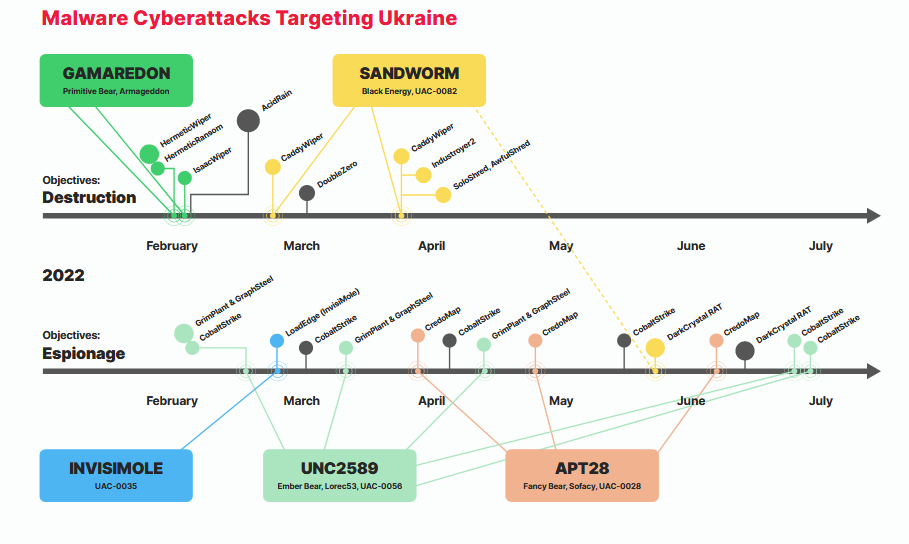
Ukraine war malware: Cybersecurity firm Trustwave published Wednesday a report on the malware strains deployed during Russia's invasion of Ukraine.
APTs and cyber-espionage
UNC3890: Mandiant said on Wednesday that it has been tracking an Iran-based threat actor (codenamed UNC3890) that has been targeting Israeli shipping, government, energy, and healthcare organizations via social engineering lures and watering hole attacks.
Mandiant assesses with moderate confidence that UNC3890 conducts espionage and intelligence collection activity to support multiple Iranian interests and operations. [...] While we believe this actor is focused on intelligence collection, the collected data may be leveraged to support various activities, from hack-and-leak, to enabling kinetic warfare attacks like those that have plagued the shipping industry in recent years.
APT41: Group-IB has a report out on recent campaigns of Chinese espionage group APT41. Some of the most interesting findings are that the group appears to have a preference for breaching orgs via SQL injection flaws in public-facing web apps, are big fans of the Cobalt Strike framework, and have working hours and days, from Monday to Friday, between 10 AM and 7 PM (UTC+8).
APT29: Mandiant put out a report on Thursday detailing the newest techniques used by Russian espionage group APT29 to hack and mess with Microsoft 365 accounts.
Vulnerabilities and bug bounty
Chrome zero-day: Google released a new Chrome browser version on Wednesday to address an actively exploited zero-day. The vulnerability is tracked as CVE-2022-2856 and has been described as insufficient validation of untrusted input in Chrome's Intents component, a deep-linking replacement mechanism.
Apple zero-days: Apple released emergency security patches on Wednesday for macOS and iOS to patch two actively exploited zero-days (CVE-2022-32893 and CVE-2022-32894).
Ruby gem installation research: Snyk's Liran Tal published some interesting research on Wednesday, showing how the Ruby gem installation process allows package maintainers to execute arbitrary code during the install time of their dependencies.
This is a powerful attack surface that can be used in conjunction with the lockfile injection attack of a Ruby application, and also more generally in the space of supply chain security in the Ruby ecosystem. Unfortunately, unlike the npm package manager, which includes a --ignore-script command line flag, Ruby's own gem CLI does not allow for opting out of the native C extension compilation process during install time, leaving users vulnerable to third-party package maintainers ability to execute arbitrary code.
CVE-2022-30211: Nettitude published a write-up on CVE-2022-30211, a vulnerability in the Microsoft implementation of the L2TP VPN protocol.
CVE-2022-29805: White Oak Security published a write-up on CVE-2022-29805, a Java deserialization vulnerability that can result in unauthenticated remote code execution on Fishbowl Inventory, an inventory management software toolkit widely used by large corporations and US government agencies.
Other Microsoft vulnerability write-ups: A similar report is also available for CVE-2022-22025, CVE-2022-22040, and CVE-2022-30209, several critical vulnerabilities in Microsoft's IIS server found by famed security researcher Orange Tsai.
RPA vulnerabilities: CyberArk researchers have found a set of vulnerabilities in robotic process automation (RPA) tools (aka software robots, aka super-complex scripts) made by software company Blue Prism. Vulnerabilities include a master encryption key leak, SQL injection, and insecure deserialization.
SpaceX bug rewards: SpaceX says it will pay up to $25,000 to researchers who find vulnerabilities and manage to hack its satellite internet network, Starlink.
Infosec industry
Tool updates: This week, Sysmon 14.0 and Cobalt Strike 4.7 were released. The biggest change in Cobalt Strike is a new clipboard stealer module and support for SOCK5 proxy servers. Also, this 🎉:
We've had a lot of feedback over the last few months that Cobalt Strike is being aggressively fingerprinted, and this is making it difficult to bypass AV and EDR tools.
On the Sysmon side:
Sysmon now impedes executables, based on the file header from being written to the filesystem according to the filtering criteria. This can be a very powerful feature into blocking certain programs writing malicious files to disk.
SANS Ransomware Summit videos: Talks from the SANS Ransomware Summit 2022 security conference, which took place in July, are now available on YouTube.
DEF CON lawsuit: Security researcher Christopher Hadnagy has sued Jeff Moss, the organizer of the DEF CON hacking conference, for "malicious, willful, and intentional and/or reckless conduct" after he was banned from attending the conference. Court documents are here, courtesy of Steve Ragan.
Further in the thread, it is claimed that Hadnagy and Social-Engineer LLC were "devastated" by the COC ban and "cancel culture"
— Steve Ragan (@SteveD3) 10:27 PM ∙ Aug 17, 2022
"As a result, Plaintiffs have suffered, and continue to suffer, detrimental
harm to their reputations and business relationships"
Twitter is hiring: See tweet below.
Hey folks! If you don’t know me, I’m the CISO of @Twitter – I run the information security, privacy engineering, and IT teams.
— Lea Kissner (@LeaKissner) 7:45 PM ∙ Aug 18, 2022
We’ve got a bunch of roles open across infosec, privacy eng + legal, and IT. Come help Twitter build great things which respect our users! 🧵




