Risky Biz News: Citrix and Fortinet patch zero-days exploited in APT and ransomware campaigns
In other news: Xnspy spyware exposes its developers; Uber discloses new breach; Greece raids Predator spyware maker; 2022's last Patch Tuesday is here.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Citrix and Fortinet, two of today's largest providers of enterprise networking equipment, have released security updates to patch two zero-day vulnerabilities that were exploited in the wild against their devices.
The Fortinet zero-day (CVE-2022-42475) is an unauthenticated RCE that impacts the FortiOS operating system that runs on the company's SSL-VPN devices.
According to reports, the vulnerability was being exploited to gain access to corporate networks and then deploy ransomware. Sadly, we couldn't get anyone to spill the beans on which ransomware gang was behind this.
This zero-day was first spotted exploited in the wild by French security firm Olympe last week, and Fortinet deserves some credit for patching it over the weekend in just three days.
Similarly, the Citrix zero-day (CVE-2022-27518) is also an unauthenticated RCE as well. It impacts the company's ADC and Gateway devices, and the exploitation was spotted by none other than the US National Security Agency.
In a security advisory [PDF], the NSA said it saw the APT5 (UNC2630, MANGANESE) Chinese cyber-espionage group leveraging the Citrix zero-day but did not elaborate on targeting.
In a rare and very surprising step, the NSA released IOCs from its investigations and asked the cybersecurity industry to share additional insights they have or find related to this zero-day's exploitation "in order to enhance understanding of this activity and so that it can be used to improve the overall security posture of the Defense Industrial Base, DoD, and USG."
In addition, yesterday was also the December Patch Tuesday. This month, we had security updates released by Adobe, Android, Apple, Microsoft, Mozilla, SAP, VMware, and others.
Microsoft fixed 72 security flaws this month, including a zero-day tracked as CVE-2022-44698 that was used by threat actors to bypass Microsoft's SmartScreen and Mark-of-the-Web technologies using standalone JavaScript files.
The OS maker also issued a general security advisory regarding recent incidents where drivers certified by Microsoft's Windows Hardware Developer Program were used in malicious intrusions to deploy malware that appeared to come from drivers signed by Microsoft.
"We were notified of this activity by SentinelOne, Mandiant, and Sophos on October 19, 2022, and subsequently performed an investigation into this activity. This investigation revealed that several developer accounts for the Microsoft Partner Center were engaged in submitting malicious drivers to obtain a Microsoft signature. A new attempt at submitting a malicious driver for signing on September 29, 2022, led to the suspension of the sellers' accounts in early October."
Notable, the Hive and Cuba ransomware strains were deployed using drivers "signed by Microsoft" in some attacks, according to reports from SentinelOne and Sophos. Mandiant also has a report out on these attacks but does not mention ransomware being deployed, linking all malicious activity to a financially-motivated group it tracks as UNC3944.
Oh... and the Apple security updates also fix a WebKit zero-day (CVE-2022-42856) that was used in targeted against iOS users. So don't forget to update your iPhones this week.
Breaches and hacks
Uber hacked data leaked online: The details of more than 77,000 Uber employees, along with source code, and credentials for some of the company's internet IT network, have been leaked online on an underground cybercrime forum over the weekend. Uber confirmed the authenticity of the leaked files in a statement sent to BleepingComputer. The company blamed the leak on a breach at Teqtivity, one of its IT service providers. Teqtivity formally disclosed the breach a day later, on Thursday. Other companies that use their services may also have had their data stolen as well. This marks Uber's second breach this year after the company was hacked by the Lapsus$ gang in September.
ITTF leak: The International Table Tennis Federation (ITTF) has leaked the passports and vaccination certificates of hundreds of professional table tennis players. The leak was caused by an improperly configured cloud hosting service and the data was exposed for more than three years. The Dutch reporters who found the leak said they notified the ITTF several times this year before the federation finally intervened to secure the leaky server. [Original report via RTL Nieuws; English coverage via InsideTheGames]
California DoF ransomware attack: The California Department of Finance confirmed on Monday that it suffered a security breach, hours after the LockBit ransomware gang listed the agency as a victim on its dark web leak site. No data has been leaked yet, and the agency has been given until Christmas Eve to pay to avoid having more than 500GB of files published online.

General tech and privacy
Twitter’s failed attempt to block bot farms: After Elon Musk, Twitter's controversial CEO, bragged on social media that he had a surprise for all the bot farms, Twitter managed to spectacularly shoot itself in the foot on Monday when the company blocked entire IP address blocks for around 30 mobile carriers across Asia. According to Platformer, this included the primary telecom providers in India and Russia, as well as the second-largest telecom in Indonesia. However, the block was short-lived, as Twitter had to revert its decision a few hours later after telcos and users complained all over Asia about not being able to access the service—go figure! The social network also officially dissolved its Trust and Safety Board as well on Monday, as, let's face it, it was getting in the way of Musk's attempts to influence US politics at this point.
Manipulated academic imagery: Dr. Neal Krawetz has an interesting write-up on the practice of forging and editing images in academic studies and how these can be spotted.
Vivaldi gets Mastodon support: Vivaldi browser version 5.6, released last week, now comes with a Mastodon widget.
More Pushwoosh findings: Pushwoosh, the Russian software company whose code was recently removed from many US government apps earlier this year, claimed after a Reuters exposé that it stopped using code from its Russian developers after Russia's invasion of Ukraine. However, Margin Research, a DARPA contractor, said that after analyzing the company's GitHub history, they found this claim to be false, as many code contributions were made in the Russian GMT+7 timezone.
Government, politics, and policy
Intellexa raids in Greece: Greek authorities have raided the homes of several individuals connected to Intellexa, a Greek-Cypriot conglomerate that's behind the Predator spyware. According to the Greek newspaper Kathimerini, the raids are related to suspicions the company might have exported its surveillance tool to two African countries without receiving an official export license and approval from the Athens government. One of these two countries is believed to be Sudan—a connection that was exposed via a Haaretz report earlier this month. According to previous reports, Intellexa previously received a license to export its Predator spyware to Madagascar. The same spyware was also used inside Greece to spy on opposition parties, prosecutors, and journalists, in incidents that have drawn the ire of EU officials.
Jesuit priest framed in India: Digital forensics company Arsenal Consulting said they found evidence that a hacker broke into the computer of Father Stan Swamy, an 84-year-old Jesuit priest, and planted incriminating evidence. The Indian government detained and sentenced Father Swamy on terrorism-related charges. He spent eight months in prison before passing away in July 2021. The case is among of dozen similar incidents where activists and academics have been framed and sentenced to jail in India after criticizing the Indian government. Several of these incidents have been tied to Indian police forces.
Dutch government warnings: The Dutch government said it sent out more than 5,200 warnings to Dutch companies since the summer of 2021 about security vulnerabilities in their IT networks. Officials said that around 76% of these warnings were for sensitive systems being accessible via the internet. The other warnings covered malware infections, leaked credentials, or unpatched systems.
NSA guidance: The US National Security Agency published four documents last week that contain guidance meant to help vendors and government agencies protect microelectronic components from malicious influence.
Sponsor section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
Cybercrime and threat intel
Xnspy stalkerware: Xnspy, a company that advertises itself as a way to catch "a cheating spouse/partner," has misconfigured some of its online infrastructure and leaked data collected from more than 60,000 Android and iOS devices where its spying apps were installed. The data was found by two security researchers, who presented their findings at the BSides London security conference last week. The data mostly contained iCloud backups, but also more than 10,000 iCloud email addresses and passwords and 6,600 authentication tokens that anyone could abuse to take over iCloud accounts if they discovered Xnspy's exposed servers. TechCrunch reported that the leaky servers helped it identify the app's maker as Konext, a small development startup in Lahore, Pakistan. Following the report, Kaspersky's Costin Raiu has shared a list of domains that can be used to detect or block Xnspy spyware operations on a local or enterprise network.
Malicious IIS modules: Microsoft has a good report for defenders on how they can detect and protect against malicious IIS modules, which are often planted by threat actors on hacked IIS servers to hide backdoors and web shells.
Kerberos attacks: On the same note, PAN's Unit42 has a guide on all the new variations of Kerberos attacks that have been discovered in recent months.
New npm malware: Ten new malicious npm packages spotted. Check out GitHub's security advisory portal for details.
Black Basta profile: If you're looking for a threat actor profile on the Black Basta gang, InQuest has put out one this week.
Malware technical reports
Empire C2 Framework: Qualys researchers have published a deep dive into Empire, an open-source post-exploitation framework that has been seeing adoption by malware operators in recent years. Threat actors seen using Empire include Turla, Leviathan, Wizard Spider (Conti/TrickBot), and many more. According to Qualys, although Empire has support for Linux, the vast majority of malware samples they found that used it had targeted Windows systems.
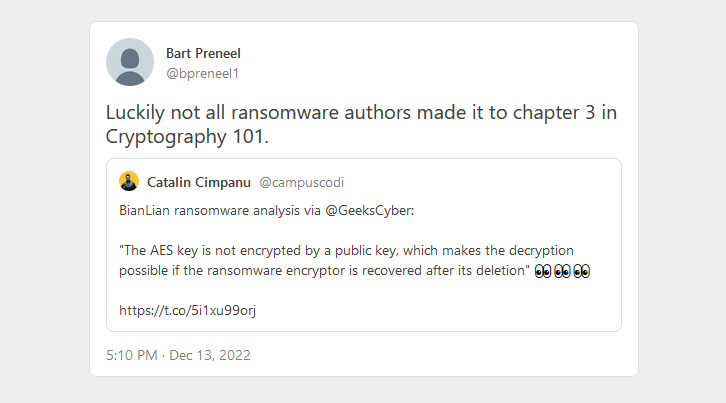
BianLian ransomware: SecurityScorecard's Vlad Pasca has a technical analysis of the BianLian ransomware. One of Pasca's main discoveries is that there might be a way to recover encrypted files if DFIR teams can recover the original BianLian encrypter. Other BianLian technical reports are also available via BlackBerry and Redacted.
"The same key is used to encrypt all files, which is unusual for most ransomware families. The AES key is not encrypted by a public key, which makes the decryption possible if the ransomware encryptor is recovered after its deletion."
Azov wiper: Check Point has a technical breakdown of Azov, a data wiper that was deployed in the wild in September and November. The malware was delivered on systems previously infected with the SmokeLoader malware, tried to frame known security researchers as its authors, and according to Check Point, was "an egregious false flag meant to incite anger at Ukraine and troll victims."
CHAOS RAT: Trend Micro also has a report on a new Go-based malware strain named CHAOS RAT, used in recent crypto-mining attacks against Linux servers. The malware appears to have been open-sourced on GitHub.
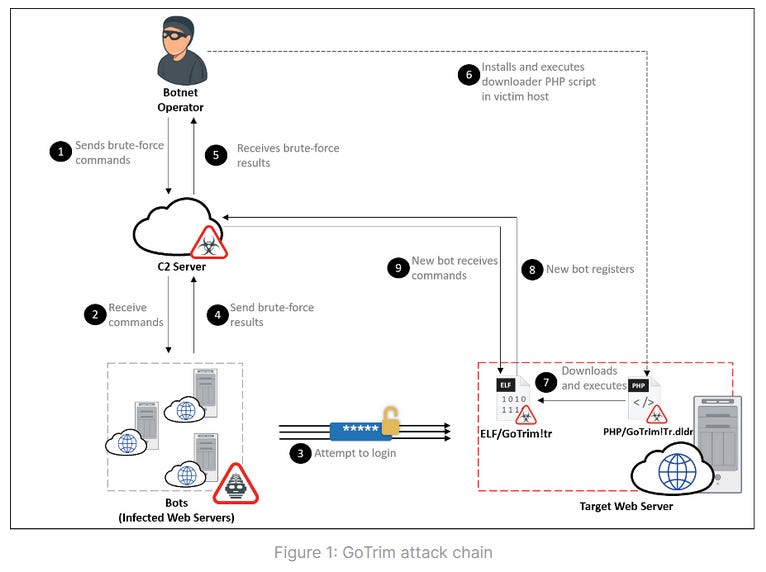
GoTrim botnet: Fortinet said it recently linked a Go-based CMS scanner and brute-forcing tool to a new botnet named GoTrim. According to the company, this new botnet appears to have been created around September 2022 and is mostly comprised of hacked WordPress sites, although evidence suggests GoTrim can also infect Joomla, OpenCart, and DataLife-based websites as well.
APTs and cyber-espionage
Thallium/Kimsuky APT: Members of the Thallium (Kimsuky) North Korean cyber-espionage group have been impersonating think tank members to reach out to political and foreign affairs analysts in order to ask for feedback and commission papers on various North Korean policy topics. Experts believe the hacking group is trying to assess how various governments, both in the West and across Asia, might respond to various North Korean actions. [See original Reuters report]
Influence operations targeting the US far-right: A joint report by Graphika and the Stanford Internet Observatory has found a network of Russian troll farm accounts on right-wing social networks Gab, Gettr, Parler, and Truth Social. The accounts pushed divisive topics related to allegations of voter fraud in the 2020 US presidential election, voter fraud in the 2022 midterms, and attempts to undermine public support for Ukraine following Russia's invasion.
"Based on the technical, behavioral, and content indicators detailed in this report, we assess with high confidence that this activity is linked to the actors behind the Newsroom for American and European Based Citizens (NAEBC), a fake right-wing news outlet that targeted US audiences ahead of the 2020 presidential election. NAEBC has been attributed by Meta to individuals associated with past activity of Russia's Internet Research Agency (IRA), an assessment reportedly shared by US law enforcement."
Vulnerabilities and bug bounty
AWS ECR vulnerability: Cybersecurity firm Lightspin has discovered a vulnerability in the AWS Elastic Container Register Public (ECR Public) that allows an attacker to delete, update, and create ECR Public images, layers, and tags in registries and repositories that belong to other AWS accounts. The Amazon ECR Public Gallery is a public portal that lists all public repositories hosted on the Amazon ECR Public service. Amazon has rolled out patches during the December Patch Tuesday.
Lenovo bugs still unpatched: Binarly researchers say that even if Lenovo released patches for two BIOS Secure Boot bypass vulnerabilities (CVE-2022-3430 and CVE-2022-3431) last month, the fixes are incomplete, and Lenovo notebooks are still open to attack.
Infosec industry
New tool—OSV-Scanner: Google has open-sourced a new tool called OSV-Scanner that can find known vulnerabilities affecting a project's dependencies. The scanner uses the OSV database to scan for vulnerabilities across various programming environments and dependency systems.
New tool—Alert on Public Repos: Security firm PerimeterX has open-sourced a new tool called "Alert on Public Repos" that will alert GitHub organizations when one of their team members creates a repository in their personal account. The idea here is to alert admins about possible cases where a team member has accidentally put a work-related repo into their personal public account.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




