Risky Biz News: CISA orders federal agencies to secure internet-exposed routers, firewalls, and VPNs
In other news: Indian government denies breach of COVID vaccination platform; Fortinet and VMWare zero-days get patches; and Argentina's securities commission gets ransomed.
This newsletter is brought to you by Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
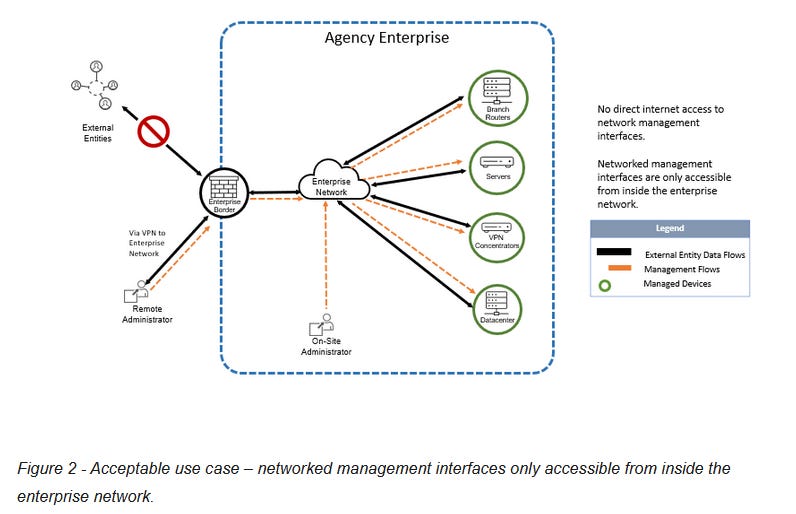
The US Cybersecurity and Infrastructure Security Agency (CISA) has issued a new Binding Operational Directive (BOD) and has ordered federal civilian agencies to limit access from the internet to the management interfaces of networking equipment.
The new BOD 23-02 applies to routers, switches, firewalls, VPN servers, proxies, load balancers, and out-of-band server management interfaces such as the iLo and iDRAC.
It applies to management interfaces hosted on a multitude of protocols, ranging from HTTPS to SSH, SMB, RDP, and others.
Federal agencies have 14 days to take the management interfaces of these devices off the internet and make them accessible only from internal networks.
The BOD applies to all existing devices, new ones that will be added to federal networks going forward, and systems hosted by agencies and/or contractors.
CISA says it plans to scan the networks of federal civilian agencies for devices with exposed management interfaces and then notify administrators to take action. According to a BOD 23-02 implementation guide, agencies should expect notifications from CISA within the next 30 days.
The new BOD 23-02 comes after both cybercrime and state-sponsored groups have repeatedly used network devices to gain an initial foothold inside government systems.
The latest example of this is the Volt Typhoon Chinese cyber-espionage group, which has used a long list of networking equipment to breach several US critical infrastructure organizations. The list included devices from ASUS, Cisco, Draytek, FatPipe, Fortinet, Netgear, and Zyxel and ranged from switches to routers and firewalls.
Breaches and hacks
India denies CoWIN hack: Indian officials have denied that hackers breached CoWIN, the country's official COVID-19 vaccination scheduling platform. Reports in Indian media over the weekend claim that hackers used the stolen CoWIN data to build a Telegram bot that would spew out the personal details of any Indian citizen based on their phone number. Officials claimed the bot was built with data stolen during other hacks and that the CoWIN system was never breached. Indian security firm CloudSEK also confirmed the government's early assessment. The Telegram channel where the alleged CoWIN data was being handed out has also been shut down.
JamaicaEye hack: The Jamaican Ministry of National Security says that hackers have disrupted access to JamaicaEye, a nationwide government CCTV system used for law enforcement investigations. Officials say attackers did not gain access to any of the JamaicaEye video feeds because the website is not connected to the CCTV system's backend. According to messages posted on the ministry's social media accounts, officials were unable to confirm if any data was taken from the website itself.
Sturdy Finance crypto-heist: A threat actor has stolen almost $800,000 from DeFi platform Sturdy Finance. According to blockchain security firms BlockSec and PeckShield, the hacker(s) used a price manipulation exploit. Sturdy Finance confirmed the hack and paused operations while they investigate.
Atomic Wallet hack: Blockchain security Elliptic says that some of the funds stolen by North Korean hackers from Atomic Wallet users are now being laundered through Garantex, a Russian crypto-exchange sanctioned by the US Treasury for... drumroll... helping cybercrime groups launder stolen funds.
Ofcom incident: Britain's communications regulator Ofcom confirmed it is one of the organizations impacted by the recent MOVEit attacks. The regulator says the data of 412 employees was taken, along with several confidential documents on companies it is regulating.
Xplain ransomware attack: The Swiss government has admitted that some "operational data" of the Swiss federal government was stolen in a ransomware attack earlier this month. The attack hit Swiss IT company Xplain, a contractor for several government agencies, including the Swiss Army and some of its police forces. The Play ransomware group took credit for the Xplain attack, leaked 5GB of data on its dark web leak site, and threatened to publish the entire data if there was "no reaction" from the company. Xplain says it did not contact the ransomware gang and will not pay the ransom demand. [Additional coverage in LeTemps]
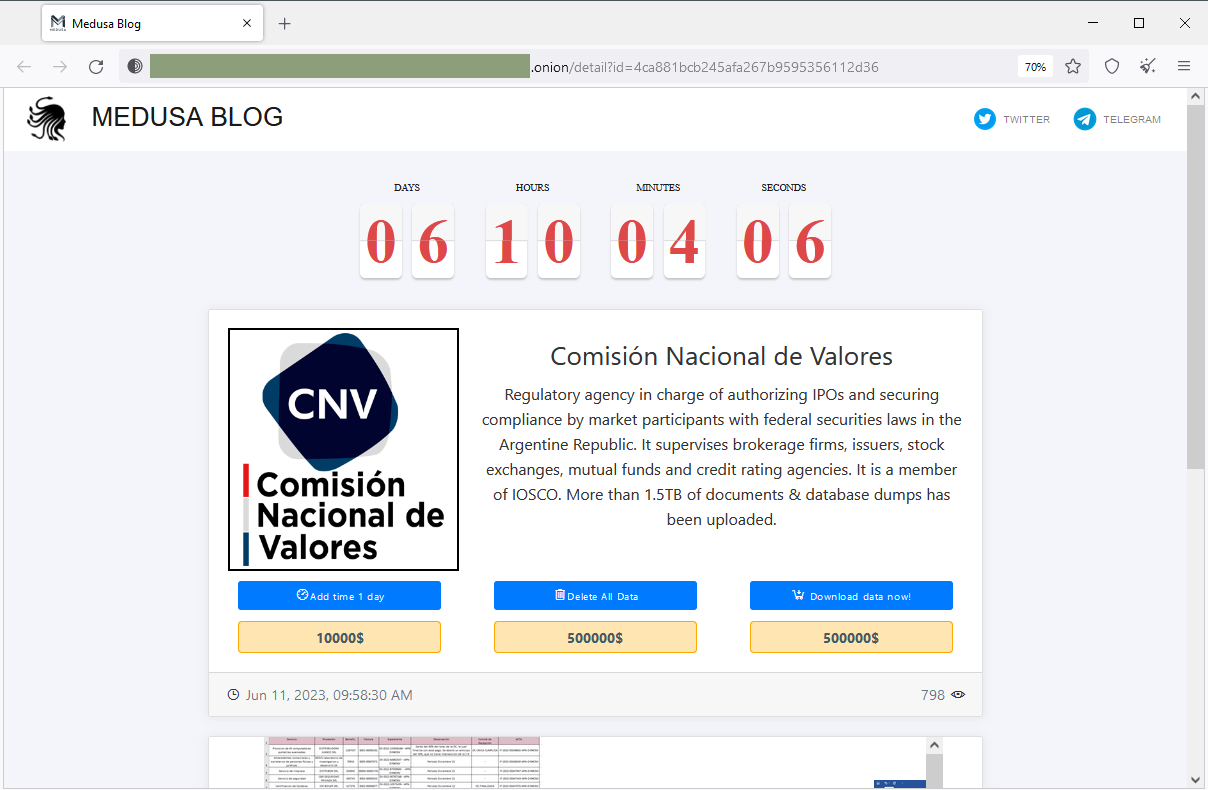
CNV ransomware attack: The Argentinian government says its National Securities Commission (CNV) fell victim to a ransomware attack on June 7, last week. Officials say they have now contained and isolated the compromised systems and have notified law enforcement. The Medusa ransomware group took credit for the attack and claimed to have stolen more than 1.5TB of files from the agency's network. According to local media, the group is demanding a $500,000 ransom to delete the agency's data. The CNV says the files taken by attackers are public information.
General tech and privacy
Spotify fined: The Swedish data protection agency IMY has fined music streaming service Spotify SEK58 million (€5.3 million) for breaking EU's GDPR regulation. The agency says that while Spotify adheres to most GDPR rules, it fails when it comes to informing users what it does with their personal data once it is collected. IMY says the decision to fine Spotify was made in cooperation with data protection authorities from other EU states.
More Edge drama: After earlier this year, users found that Edge was leaking some of their browsing history to a Bing API, users are up in arms again about another Edge feature that is apparently sending the URLs of images they're loading in their browser to Microsoft for "enhancement." The thing is that this isn't the only major privacy with that browser these days, and BornCity has a good summary of all the recent issues.
Government, politics, and policy
France exposes Russian disinfo campaign: The French government has uncovered a sprawling social media disinformation campaign orchestrated by the Russian government and designed to spread false narratives about the war in Ukraine. The campaign consisted of fake news stories published on websites mimicking legitimate news outlets such as Le Figaro, Le Monde, and Le Parisien. The articles pushed narratives that the Ukrainian government and army were associated with neo-Nazis, that Ukrainian refugees were responsible for crimes across Europe, and that sanctions against Russia were damaging European countries more. Links to these articles were amplified using bots on social media networks like Facebook, Twitter, and Telegram. French officials say the stories and narratives were often boosted by the official accounts of Russian embassies and its cultural centers across the world.
"The implication of Russian cultural centres and embassies that have actively participated in spreading content produced by this campaign, including via their institutional accounts on social media, is further proof of the hybrid strategy that Russia is implementing to undermine the conditions for peaceful democratic debate, and therefore damage our democratic institutions.
France condemns these acts, which are not worthy of a permanent member of the United Nations Security Council. No manipulation attempt will dissuade France from supporting Ukraine in the face of Russia's war of aggression."
Russia to confiscate cybercrime profits: Russian President Vladimir Putin has signed a bill into law that will allow law enforcement authorities to more easily confiscate funds and property gained through cybercrime activities. The new law expands the list of cybercrime activities and type of property that can be seized. The law will enter into force ten days after its official publication today. [Additional coverage in Interfax]
Dutch government cyber strategy: The Dutch government has published its official international cyber strategy. The document covers the 2023-2028 period and puts a focus on cooperation to counter both criminal and state-based threats.
Six-months password change policy: The South Korean government is drawing close to removing a rule mandating that passwords for government accounts must be changed every six months. The mandatory password change rule made it on a Top 10 list of worst government regulations compiled by the Prime Minister's Office following a month-long public survey. Officials will hold an online vote to rank the ten rules and then revise laws and regulations based on the final Top 10.
702 renewal: In a bid to get the FISA Section 702 renewed, the FBI has disclosed for the first time how it used the controversial surveillance capability to unmask the attackers behind the Colonial Pipeline attacks in 2021 and Iranian hackers behind a series of ransomware attacks across the US in 2022. [Additional coverage in The Record]
US intelligence agencies buy commercial data: A newly declassified ODNI report confirms for the first time that US intelligence and law enforcement agencies are buying vast amounts of PII from commercial data brokers. The data is collected for intelligence mining purposes and ranges from web browsing data to geolocation information and even vehicle information. The government admits that such information is helpful to their efforts, but also warns the same data could be bought and abused by foreign adversaries. The report noted that while the data is being advertised as "anonymized," when combined with multiple data points, the data can be deanonymized and used to identify both US citizens and foreign nationals. [Additional coverage in TechCrunch]
"The volume and sensitivity of CAI have expanded in recent years mainly due to the advancement of digital technology, including location-tracking and other features of smartphones and other electronic devices, and the advertising-based monetization models that underlie many commercial offerings available on the Internet."
CISA expects destructive Chinese cyberattacks: The US government says it expects Chinese hackers to conduct destructive cyber-attacks against US critical infrastructure in the event of a conflict between the two nations, CISA Director Jen Easterly said during an interview at an Aspen Institute event this week.
"Anybody who's been studying what's been happening under the leadership of President XI, in the event of a conflict, China will almost certainly use aggressive cyber operations to go after our critical infrastructure, to include pipelines and rail lines, to delay military deployment and to induce societal panic. [...] I think is the real threat that we need to be prepared for and, to focus on, and to build resilience against."
Sponsor section
This edition is brought to you by Thinkst Canary. Most companies find out way too late that they've been breached. Thinkst Canary changes this. Deployed and Loved on all seven continents. Deploys in minutes; almost zero admin overhead. It just works!
Cybercrime and threat intel
Bulletproof hoster sentenced: US authorities have sentenced a Romanian national named Mihai Ionut Popescu to three years in prison for operating a bulletproof hosting service. Popescu ran PowerHost, a service that hosted servers for malware operations like Gozi, Zeus, SpyEye, and BlackEnergy. His company also hosted servers that carried out DDoS attacks and distributed email spam. Popescu was detained in Colombia in 2021 after being on the run for nine years after being initially charged by the US in 2012.
Pirated Windows campaign: Russian security firm Dr.Web has documented a campaign using pirated versions of Windows to infect users with a cryptocurrency clipper. So far, the group behind this campaign has already stolen almost $19,000.
MSSQL abuse: A honeypot experiment that ran for more than four months has found that MSSQL databases are far more targeted by threat actors than other DB systems like MySQL, Redis, or MongoDB. Trustwave says it recorded a giant disproportion in the number of attacks, with more than 93% targeting MSSQL servers, while other systems like Oracle, DB2, Cassandra, or Couchbase seeing little to no action.
ZIP domain abuse: Both Cisco Talos and Netskope have summaries on the recent ZIP domain abuse.
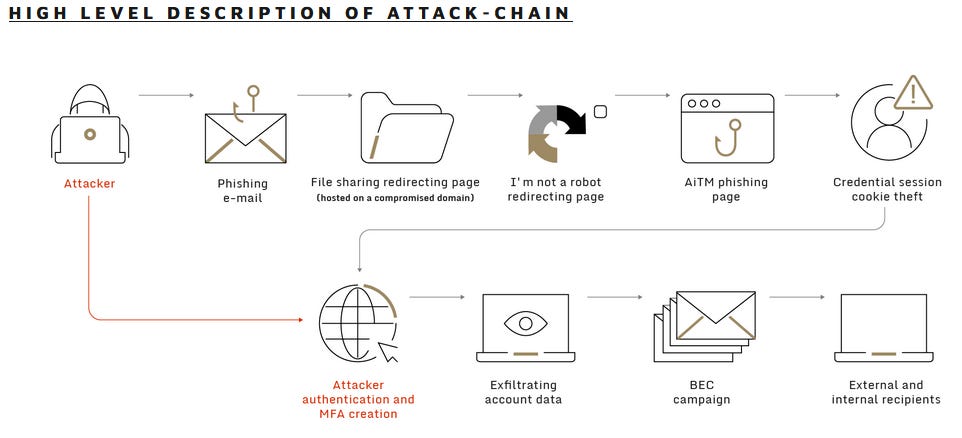
AitM BEC campaign: Sygnia has the lo-down on a BEC campaign that has used AitM phishing techniques to target and breach dozens of companies across the world. Microsoft documented a similar campaign last week, showing the increasing adoption of AitM phishing tools by BEC groups.
8Base ransomware: A ransomware gang that has gone under the radar lately is 8Base. The group started operating in April 2022 and currently lists a whopping 78 victims on its data leak site.
Malware technical reports
PikaBot: Sophos warns about PikaBot, a new malware loader that appeared at the start of the year and has become a solid alternative to Emotet, QakBot, and TrickBot.
GreetingGhoul: Kaspersky has a deep dive into a campaign delivering the DoubleFinger malware loader that then deploys GreetingGhoul, a malware designed to collect credentials linked to cryptocurrency wallet apps.
PowerHarbor: NTT's cybersecurity team has published a report on PowerHarbor, a new malware strain used in recent attacks linked to the SteelClover (BatLoader) cybercrime group. The new malware has been live since the end of May 2023.
CosmicEnergy: ICS security firm Dragos has a technical analysis of the CosmicEnergy ICS red-team tool, which it calls a non-immediate threat.
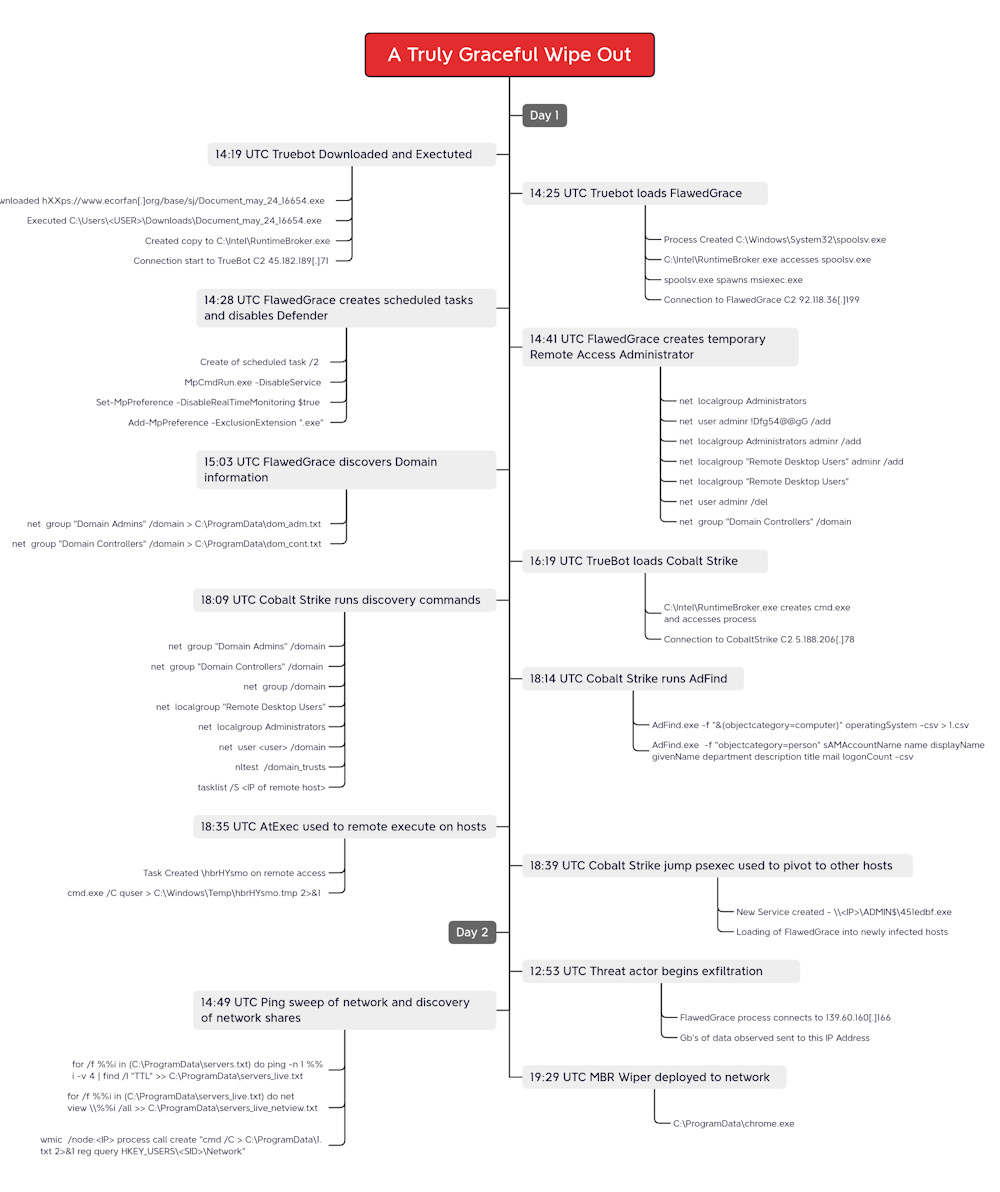
FIN11/Clop wiper campaign: While everyone is focused on FIN11/Clop's MOVEit hacks, the DFIR Report team has published an analysis of one of their older campaigns, where they rented access to systems previously infected with the TrueBot malware, then deployed the FlawedGrace remote access trojan, stolen data from the victim's network, and then deployed an MBR wiper to destroy the target's network.
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
APTs and cyber-espionage
RedEyes: A recent AhnLab report looks at a recent campaign from the RedEyes (APT37, Scarcruft) group targeting North Korean defectors, human rights activists, and university professors.
ChamelGang's ChamelDoH: Stairwell has published an analysis of ChamelDoH, a C++ implant operated by the ChamelGang Chinese cyber-espionage group. The malware stands out because it's designed to communicate with its operators via DNS-over-HTTPS tunnels. At a technical level, the implant is capable of basic remote access operations such as file upload, download, deletion, and execution.
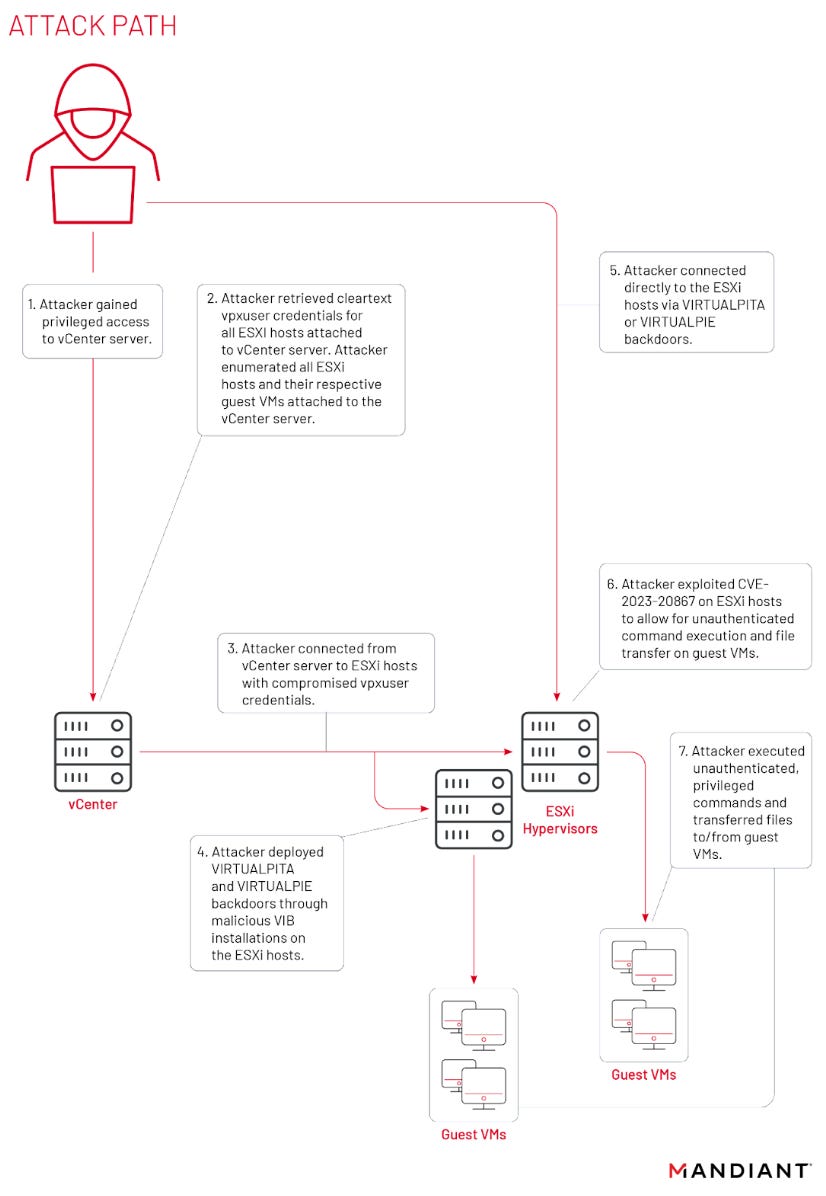
UNC3886 exploits VMWare zero-day: A Chinese cyber-espionage group tracked as UNC3886 has exploited a new VMWare zero-day (CVE-2023-20867) to backdoor and steal data from VMWare guest VMs. The zero-day allowed the group to run malicious commands with elevated privileges, without needing to authenticate, and without leaving traces in VMWare logs. The attacks were discovered by Google's Mandiant division, and VMWare released a fix for the zero-day during the company's monthly Patch Tuesday. Previously, the UNC3886 group also exploited a Fortinet zero-day (CVE-2022-41328) earlier this year and also utilized a novel VMWare persistence technique in attacks at the end of 2022.
Vulnerabilities and bug bounty
MOVEit PoCs go live: Horizon3, Rapid7, and independent security researchers have released proof-of-concept exploits for the recent zero-day used by the Clop cybercrime group to hack MOVEit file-sharing appliances. Go break some eggs. Just don't extort the hens!
Patch Tuesday: Yesterday was also the June 2023 Patch Tuesday. We had security updates being released by Adobe , Chrome, Fortinet, Microsoft, VMWare, Citrix, and SAP. The Android project, Mozilla Firefox, GitLab, Cisco, and Zyxel released security updates last week as well. This month, Microsoft patched 94 vulnerabilities.
Fortinet patches zero-day: Fortinet has patched 21 vulnerabilities as part of its June Patch Tuesday, including a zero-day vulnerability (CVE-2023-27997) that allows attacks to execute code remotely on the company's SSL VPN servers. Fortinet says it learned of the vulnerability from two LEXFO researchers (Charles Fol and Dany Bach), but a later investigation discovered that the same bug was being exploited in the wild as well. The company says the vulnerability "may have been exploited in a limited number of cases" and urged customers to install patches as soon as possible. CISA confirmed exploitation on Tuesday. LEXFO also published a technical breakdown of the bug.
WooCommerce plugin bug: Patchwork has identified a vulnerability (CVE-2023-34000) in the WooCommerce Stripe Gateway plugin that can allow unauthenticated threat actors to view details of orders placed on WooCommerce stores.
VMWare Aria PoC: A proof-of-concept exploit for a VMWare Aria vulnerability (CVE-2023-20887) that was patched last week has now been released online. A technical analysis of the bug is available here.
GitHub bug bounty program: GitHub's Bug Bounty Program has been updated to include clear and accessible criteria for receiving an invitation to the company's more select VIP program. The two conditions are that a researcher submitted two bug reports over the past two years and earned more than $20,000 in bounties on the normal bug bounty platform.
Infosec industry
Upcoming book: Head of Vodafone's Global Cyber Threat Intelligence team Stuart Peck is working on a book on cyber threat intelligence and security analytics. The book is expected towards the end of the year/start of next year.
New tool—eBPFmon: Cybersecurity firm Red Canary has open-sourced a new tool named eBPFmon that can be used to monitor eBPF-based applications for security threats.
New tool—CloudFoxable: Security firm BishopFox has open-sourced a tool named CloudFoxable, an intentionally vulnerable AWS environment created specifically to teach the art of AWS Cloud penetration testing.
New tool—CVExploits: Three security researchers (Youssef Muhammad, Mohammad Hussam Alzeyyat, and Muhammad Salah) have launched CVExploits, a website that aggregates exploits and PoCs for known vulnerabilities.
New tool—Mitre Assistant: Security researcher Carlos Diaz has released an app called Mitre Assistant that pulls and lists all the MITRE ATT&CK techniques employed by a specific threat actor.
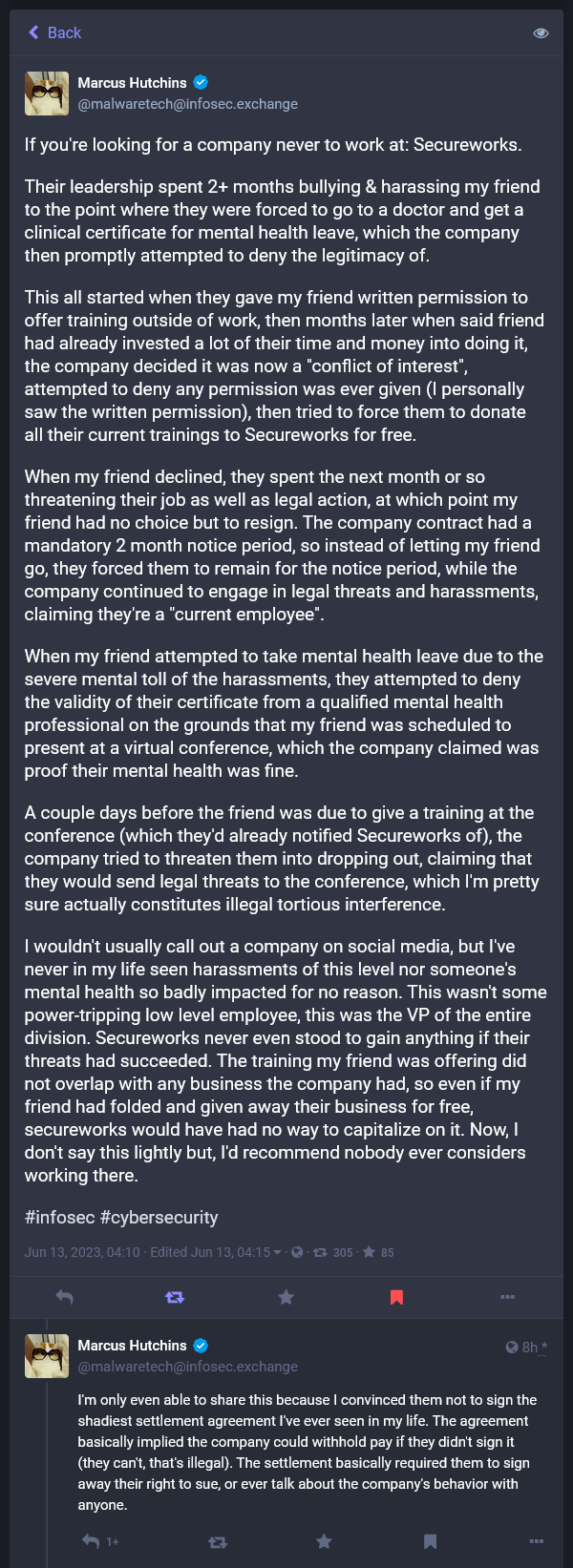
Secureworks WTF: Congratulations to Secureworks for making sure no infosec top talent will ever want to work for them going forward.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the elements that make them think an operation is state-backed.




