Risky Biz News: Chinese APT targeted White House reporters ahead of Jan. 6 insurrection
In other news: Vault7 leaker found guilty at retrial; DoT is coming to Windows; and Iran puts the entire country in Safe Search mode.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
In the days preceding the January 6 attack on the US Capitol, Chinese state-sponsored hackers changed the targets of their email phishing campaigns to go after US political and national security reporters, security firm Proofpoint said in a report published on Thursday.
The company linked the campaign to a group it calls TA412, also known as Zirconium and APT31, and described the attacks as "a very abrupt shift in targeting."
The sudden change in targeting from TA412, which typically goes after diplomatic targets, suggests the group may have anticipated the turmoil surrounding the transfer of power in the US government, picking up on hints and threats left online on forums and social media by Trump supporters.
And Proofpoint said that TA412 didn't go just after any natsec reporters but specifically focused on "Washington DC and White House correspondents," the journalists who would have had their finger on the pulse of that day's events.
Proofpoint only saw the phishing campaign and was not able to tell if any were successful, but said that TA412 returned to target reporters later in the year, but this time the ones covering cybersecurity, surveillance, and privacy issues with a focus on China.
TA412 also carried out a third campaign against US media organizations in February this year, and this time they targeted the newsrooms reporting on political topics, with the group most likely trying to gather information shared by US officials with reporters on the US' possible involvement in the rising tensions between Russia and Ukraine, tensions that eventually blew over later that month, when Russia invaded Ukraine.
But Proofpoint said that Chinese hackers weren't the only ones engaging in campaigns against reporters and media organizations over the past year and a half. For example, Proofpoint said that North Korean hackers also targeted reporters who wrote articles criticizing the country's leader, while Iranian and Turkish threat groups tried to compromise the social media accounts of numerous reporters and newsrooms.
All in all, Proofpoint argues that the recent attacks highlight the risks facing journalists and other members of the news media, who are more attractive targets for cyberspies since they might not always benefit from the same training and IT resources that government officials might receive, and would be easier to compromise. Once compromised, reporter accounts can then be pilfered for information on sources and past interactions with government officials, or they can be used to launch new attacks against officials or sources, taking advantage of existing trust relationships.
Breaches and hacks
CIA Vault7 leak: Joshua Schulte, the former CIA employee who leaked the Vault7 files to Wikileaks, was found guilty on all counts following a retrial. Schulte, who represented himself, claimed to the end that he was made a scapegoat by US authorities, even if extensive and multiple reports portrayed him as hot-headed, ego-centrical, and self-entitled. A sentencing date was not set as Schulte is also on trial for child pornography possession and transport charges in a separate case.
OPM breach settlement: Victims of the 2014 and 2015 OPM data breaches are expected to receive about $700 each, while victims who can prove extensive damage are eligible for $10,000. The decision comes after several class-action lawsuits against the US government were consolidated last month into one case, which was settled for $63 million, per The Record.
Bandai Namco confirms ransomware attack: Bandai Namco, the Japanese gaming company behind the hit-game Elden Ring, confirmed this week that they were hacked. The company's admission comes after the AlphV ransomware gang listed the company on its leak site earlier this week.
LendingTree breach: Online lending company LendingTree formally disclosed a security breach almost a month after a threat actor dumped the details of more than 200,000 of its users on an underground cybercrime forum. Leaked details included customer names, physical addresses, phone numbers, emails, IP addresses, credit scores, and various loan application details. In a letter filed with the California OAG, the company said the breach occurred because of a vulnerability on its website that has now been patched. LendingTree is currently facing a class-action lawsuit following the breach.
General tech and privacy
Another Clearview AI fine: After being fined more than £7.5 million ($9.4 million) in the UK and another €20 million ($20 million) in Italy, facial recognition company Clearview AI received the third fine in Europe, another €20 million ($20 million) from Greek authorities.
Microsoft Salus is now open source: Microsoft has officially open-sourced this week its Salus app, an internal tool that the company has used for the past months to generate software bill of materials (SBOM) for its internal projects. SBOM files are lists of libraries used inside a software application. They allow companies to track if an app uses third-party code and are incredibly useful when a vulnerability in these third-party libraries is disclosed, as it allows the company to easily identify which of its own apps are also impacted.
DoT comes to Windows: Support for the DoT (DNS-over-TLS) protocol is now available for Windows Insiders users, Microsoft said this week.
QWACs are bad, mkay: Mozilla has launched a public campaign to raise awareness of the EU's terrible plan to force browser vendors to support Qualified Website Authentication Certificates (QWACs), a new type of digital certificate. Mozilla, academics, and security experts say that QWACs are similar to Extended Validation certificates that browser makers have stopped supporting because of their lack of actual security benefits. But more importantly, Mozilla says that an EU regulatory body should not be telling browser makers what technical solutions to support, especially since their idea is actually a step back for user security and only a money-grab for certificate authorities (CAs).
Government, politics, and policy
Russia looking to impose fines for data breaches: The Russian government is working on a law that will impose turnover-based fines on companies that suffer data breaches that expose personal user information, according to a report from the Russian Legal Information Agency. Currently, legal entities face fines of 500,000 rubles (~$8,500) for the leak of personal data, but if the new proposed bill passes, fines will be calculated as a percentage of a company's revenue.
First DHS Cyber Safety Review Board report: In its first-ever report published on Thursday, the DHS Cyber Safety Review Board concluded that the Log4j vulnerability disclosed last year would pose issues to US organizations for years to come. To deal with this problem, the board issued 19 recommendations o deal with the issues, such as the implementation of software bill of materials (SOBM) schemes and increasing investment in open-source programs, many of which are the core of many government and private sector networks. [Additional coverage in The Record and in Dmitri Alperovitch's Twitter thread below]
I am very proud of this inaugural report from Cyber Safety Review Board (CSRB) on the #Log4j incident. Grateful for the leadership of our Board Chair @DHS_Policy and Deputy Chair @argvee. Here are the most important highlights from my perspective 🧵
— Dmitri Alperovitch (@DAlperovitch) 1:29 PM ∙ Jul 14, 2022
US senators propose crackdown on shady VPNs: Two Democrat senators have asked the FTC to look into the deceptive practices of VPN companies. The two want the FTC to look at how VPN companies use false or misleading claims about user anonymity in their ads, the sale of user traffic data to third parties, and if the companies disclose when they share user data with law enforcement agencies.
Iran puts the entire country in Safe Search mode: Several Iranian users reported on Wednesday that Iranian internet service providers started replying to DNS queries for the main Google.com domain with the Lock SafeSearch URL of forcesafesearch.google.com. This is a known feature of the Google search engine that's usually employed in controlled corporate environments, where companies prevent users from searching for inappropriate content. Apparently, this is also the second time the Iranian government has done this.
This is the second time Iran has done something like this to Google Search, using features meant for schools to impose country level censorship. https://t.co/8zvIkzqFFO
— cda (@CDA) 2:33 PM ∙ Jul 13, 2022
Cybercrime and threat intel
KillNet: Intel471 has a report out on the operations of pro-Russian hacktivist group KillNet and its recruitment, tactics, techniques, and procedures.
GhostSec: On the same note, CyberInt published a report on GhostSec, a hacktivist group founded back in 2015, which joined the "Russo-Ukrainian hacktivist war" on the side of Ukraine.
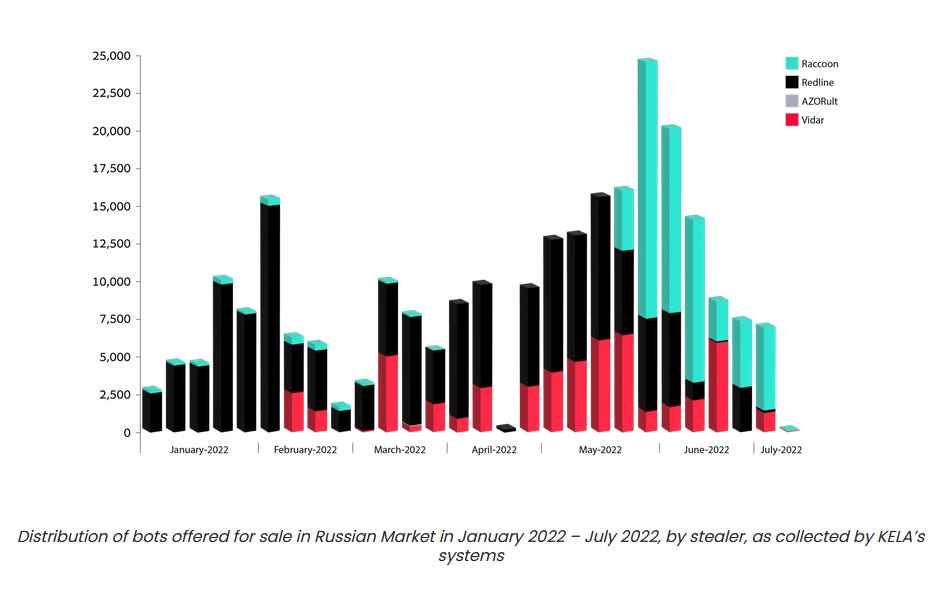
Infostealer market overview: Threat intel company KELA has published an overview of the current underground market for infostealer malware and its top players, like Redline, Racoon, AZORult, Mars, BlackGuard, META, Arkei, Vidar, Ginzo, Eternity, 7.62mm, Inno, TigersTeam, and the Aurora Project.
Unity merges with adware maker: Apparently, Unity for Games decided to merge with a company accused of spreading adware.
Wait what, Unity is merging with the company best known for its malware delivery system, so popular that it has its own entries in VirusTotal, was blacklisted on Windows by MS, and was used to spread fake flash installers through the Equifax site?! What??
— shana 😋 (andreia gaita) (@sh4na) 2:04 PM ∙ Jul 13, 2022
WPBakery attacks: WordPress security firm Wordfence reported on Wednesday seeing a sudden spike in attacks targeting a vulnerability (CVE-2021-24284) in Kaswara Modern WPBakery Page Builder Addons, a page builder plugin for WordPress sites from WP developer WPBakery. The vulnerability, which did not receive a patch, can be used to upload malicious PHP files to an affected website, leading to code execution and complete site takeover.
Mantis DDoS botnet: Cloudflare said that a botnet named Mantis was responsible for the record-breaking DDoS attack that hit its servers last month. Cloudflare says the Mantis botnet is an evolution of the older Meris botnet, but unlike its predecessor, Mantis can infect a wider range of devices, and not just MikroTik routers. The company estimated the current size of the Mantis botnet at only 5,000 bots, meaning the botnet can pack a strong punch even from a small base, hence the reason they named the botnet after the Mantis shrimp, which can also generate a lot of power from their tiny frame to spear their prey.
New Autolycos malware: Evina security researcher Maxime Ingrao discovered this week eight applications uploaded on the official Google Play Store that contained a new Android malware strain named Autolycos. Ingrao said the apps were downloaded more than 3 million times and that Autolycos' main purpose was to secretly subscribe infected users to various premium services and generate a profit for the threat actor through an affiliate kickback scheme. According to Evina, the malware family originated in South Africa and is now proliferating in Nigeria.
A new family of malware dubbed Autolycos has been identified by Evina's malware experts.
— Evina (@EvinaTech) 12:57 PM ∙ Jul 13, 2022
The malware family originated in South Africa and is now proliferating in Nigeria.
bit.ly/3nWRR0G
North Korean hackers linked to H0lyGh0st ransomware: Microsoft said that it found evidence to link the operators of the H0lyGh0st (HolyGhost) ransomware to a group of North Korean hackers it tracks as DEV-0530, and which may be connected to a larger group known as the Andariel APT (PLUTONIUM, DarkSeoul). Microsoft said it saw the group deploy its payload on the networks of small businesses in multiple countries since June 2021. This is not the first time that North Korean hackers have been linked to ransomware operations after they've also been linked to strains like WannaCry, VHD, Tflower, BEAF, PXJ, ZZZZ, CHiCHi, and Maui.
From the website of the HolyGhost ransomware gang:
— Catalin Cimpanu (@campuscodi) 8:39 AM ∙ Jan 13, 2022
"We help poor and starving people if we earn money" 🤨
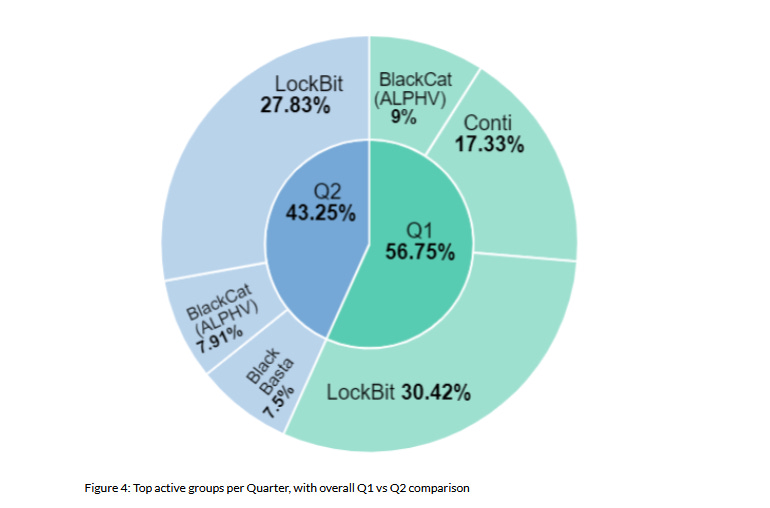
Lockbit dominates Q2 2022: According to reports from both CyebrInt and Digital Shadows, the Lockbit gang was the most active ransomware group in Q2 2022.
Vice Society group: Sekoia's threat intel team has published a report on Vice Society, a cybercrime group that deploys ransomware created by other groups (such as Zeppelin and HelloKitty) but uses its own leak site to extort victims. Sekoia said that based on its analysis, it believes the group's members are "English native speakers."
BlueSky ransomware: CloudSEK researchers have published some initial details and IOCs on the new BlueSky ransomware, first spotted this year in May and believed to be connected to the former Conti gang. CloudSEK also said it believes to have tracked down the ransomware's operator to someone located in Krasnodar, Russia.
Use of cryptocurrency mixers rose in 2022: Blockchain tracking company Chainalysis said that cryptocurrency mixing services saw a huge spike in usage this year as cybercrime and nation-state groups have extensively used them to launder ill-gotten funds.
Illicit addresses account for 23% of funds sent to mixers so far in 2022, up from 12% in 2021.
CERT-FR MISP feed: The CERT France team has released a free public MISP feed with indicators of compromise (IOC) labeled TLP:WHITE for free distribution.
Malware technical reports
Qakbot evolves: Security researchers from Zscaler said in a report this week that the rising number of infections seen in recent months from the Qakbot (QBot, QuackBot, Pinkslipbot) botnet can be traced back to the deployment of several new evasion detection techniques. This includes the use of ZIP files to hide their payloads, new code obfuscation methods, and the use of unknown file extensions (OCX, ooccxx, dat, or gyp) to deliver payloads.
Backdoorit & Caligula: The Avast team published a report on the Backdoorit RAT and the Caligula IRC DDoS bot, both malware strains written in the Go programming language.
Mysterious campaign: Trellix has a report out on a threat actor malspam campaign targeting government agencies of Afghanistan, India, Italy, Poland, and the US since 2021. The final payload in these attacks is either AysncRAT or LimeRAT. According to clues left by the attacker, Trellix believes the threat actor may be from South Africa.
APTs and cyber-espionage
Confucius APT: Chinese infosec firm Antiy Group has published a report on a recent campaign of the Confucius APT that targeted Pakistani government and military institutions. Past reporting has found links between Confucius and Patchwork, a well-known Indian threat actor. Some insights from one of Trend Micro's APT experts.
Nice report (in Chinese) on recent Confucius #APT campaigns targeting Pakistan gov and military. They still use the malware that we blogged about last year, only the lures changed. Some interesting links with the Sidewinder threat actor are also disclosed mp.weixin.qq.com/s/n6XQAGtNEXfP…
— Daniel Lunghi (@thehellu) 12:12 PM ∙ Jul 13, 2022
Sidewinder compromises Pakistani Air Force: On a similar note, Check Point said it had "evidence suggesting that Pakistan Air Force's Headquarters was a victim of a successful attack conducted by Sidewinder, a suspected India-based APT group." The compromise allegedly took place in May 2022, according to the security firm.
Transparent Tribe: Now, in direct opposition, Cisco Talos also published a report on recent attacks carried out by Transparent Tribe, a Pakistani APT that has been targeting Indian educational institutions, showing that these two countries continue to hack each other with no respite.
Vulnerabilities and bug bounty
macOS sandbox vulnerability: After releasing its own security updates on Patch Tuesday, Microsoft also took great care to disclose a vulnerability in Apple's macOS that could be exploited to escape the App Sandbox service and run malicious code on a system. While the bug (CVE-2022-26706) was fixed in May, Microsoft's team published a technical report on it yesterday.
70+ Lenovo laptop models impacted by UEFI firmware bugs: ESET security researcher Martin Smolar has discovered three buffer overflow vulnerabilities in the UEFI firmware of Lenovo Notebook devices. The vulnerabilities allow threat actors to hijack the boot sequence and take over the device's OS. More than 70 Lenovo models are impacted, and the Chinese vendor released patches this week.
#ESETresearch discovered and reported to the manufacturer three buffer overflow vulnerabilities in UEFI firmware of several #Lenovo Notebook devices, affecting more than 70 various models including several ThinkBook models. @smolar_m 1/6
— ESET research (@ESETresearch) 10:29 AM ∙ Jul 13, 2022
New browser side-channel attack: A team of academics from the New Jersey Institute of Technology published details this week about a new deanonymization attack that targets web browsers and can disclose past sites a user has visited. The gist of the research is that a threat actor who manages to lure a victim to a malicious site can link their IP address with details such as usernames or emails used on popular websites the victims are currently still logged in. The research team said the attack works because the researchers pull data from the user's CPU cache and not the browser cache, and by doing so, they are bypassing many browser-level isolation mechanisms, including cross-origin resource policies (CORP), cross-origin opener policies (COOP), and SameSite cookie attributes. The NJIT team said they tested the attack on both desktop and mobile browsers running on various CPU microarchitectures (Intel, Apple M1, Qualcomm CPUs), operating systems (Windows, macOS, Android), different browser engines (Chrome, Safari, Firefox, Tor Browser), and with multiple services (Google, Twitter, LinkedIn, TitTok, Facebook, Instagram, Reddit).
RCE in Blitz.js: SonarSource researchers published a write-up for CVE-2022-23631, a prototype pollution vulnerability in the Blitz.js JavaScript framework that can lead to remote code execution.
Decade in vulnerabilities: A Trustwave report looks at the top 10 worst vulnerabilities from the last decade, including stuff like BlueKeep, Heatbleed, EternalBlue, and others.
Honda to redesign cars to address Rolling PWN: Japanese carmaker Honda said it plans to redesign the key fob technology in its new vehicles to address a recently-discovered vulnerability known as Rolling PWN. Disclosed last week, the vulnerability can be used to unlock and start the engines of all Honda cars made since 2012.
Infosec industry
ATT&CKcon 3.0: The recorded presentations from the ATT&CKcon 3.0 security conference are now available online.
New tool: German security firm RedTeam Pentesting has open-sourced and released Pretender, a cross-platform tool for executing machine-in-the-middle (MitM) attacks inside Windows networks.
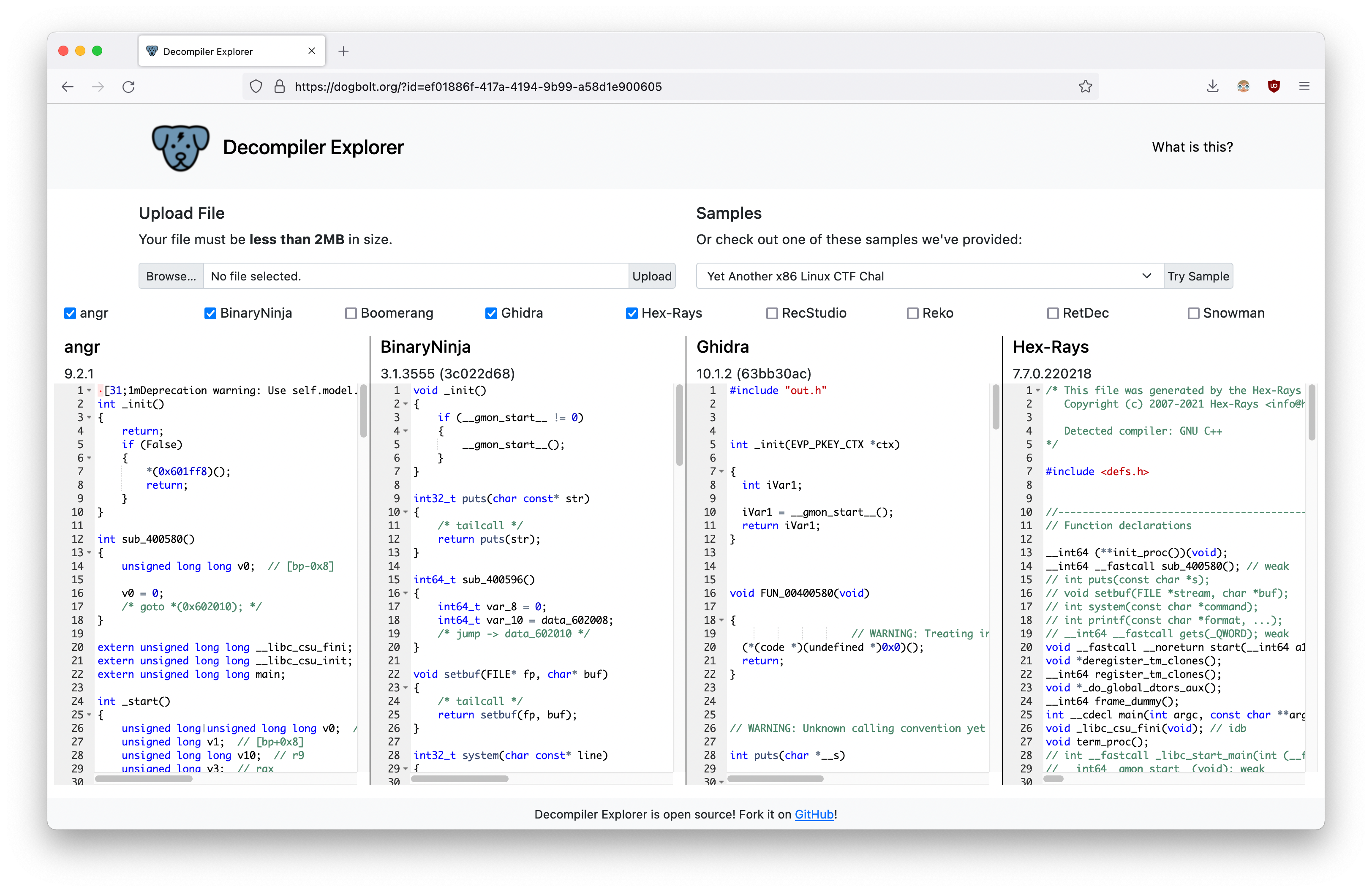
Web tool launch: BinaryNinja launched this week Decompiler Explorer, a web service that lets you compare the output of different decompilers on small executables.