Risky Biz News: China's Great Firewall can now block Shadowsocks, VMess, and Obfs4
In other news: New GreenMwizi group targets Booking customers; Google offers cheap cybersecurity training courses; new Cactus ransomware gang targets Fortinet VPN appliances.
This newsletter is brought to you by Material Security, the company that provides visibility, defense-in-depth, and security infrastructure for Office 365 and Google Workspace. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
A team of academics specialized in internet censorship systems has confirmed that China's Great Firewall can detect and block fully-encrypted protocols such as Shadowsocks, VMess, and Obfs4.
These protocols are far superior to TLS because all their traffic is encrypted, including handshakes, so there are no portions of data that can leak information about any part of the protocol or traffic destinations—and hence why they're called "fully encrypted protocols."
While there have been reports that Chinese censors have been sparsely blocking some of these protocols as early as 2019, these blocks were your typical whack-a-mole situation. Chinese authorities would actively scan the internet, identify IPs that they believed carried certain protocols and then block traffic to those addresses.
But in a paper published at the end of last month, academics say that China's Great Firewall is now capable of detecting the Shadowsocks, VMess, and Obfs4 protocols in real-time, just by passively looking at what traffic goes in and out of China.
The way China has approached the "problem" was quite simple. Basically, China's Great Firewall is currently in a "deny-all" state for unknown protocols. If censors have encountered a protocol and know they can intercept and filter it, the protocol is allowed to pass. If not, the protocol is blocked. A very crude solution, but as any enterprise admin will tell you, a very efficient one.
"We find that, instead of directly defining what fully encrypted traffic is, the censor applies crude but efficient heuristics to exempt traffic that is unlikely to be fully encrypted traffic; it then blocks the remaining non-exempted traffic.
This new system has been live since as early as November 2021 and works pretty efficiently, as it only blocks around 0.6% of normal Internet traffic as "collateral damage."
The research team says they developed "various circumvention strategies," which they shared with the developers of various popular anti-censorship tools, such as the Shadowsocks project, V2Ray, Outline, Lantern, Psiphon, and Conjure.
"These circumvention strategies have been widely adopted and deployed since January 2022, helping millions of users bypass this new censorship. As of February 2023, all circumvention strategies these tools adopted are reportedly still effective in China."
Breaches and hacks
GRFC fined for data breach: A Russian court has fined the Russian General Radio Frequency Center (GRFC) the whopping sum of $385 (30,000 rubles). The fine is for a November 2022 data breach, when Bielorussian hacktivist group the Cyber Partisans breached the agency's systems, stole sensitive files, and then trashed its internal network. Data stolen during the intrusion was shared with journalists, who published an exposé earlier this year on how the Russian government monitors and censors the Russian internet.
Twitter finally discloses data leak: Twitter is notifying users via email about a data leak the company experienced in its Twitter Circle feature last month. The company says that tweets shared inside private circles were, for a period of time, also visible to outside users. As several users pointed out on the platform, the leak had been active for almost two weeks before Twitter fixed the issue.
NextGen incidents: EHR software maker NextGen has disclosed a credential-stuffing attack that hit its service at the end of March this year. The incident comes two months after the company was also hit by the AlphV ransomware gang. According to a breach notification it filed with US authorities, the credential-stuffing attack impacted more than one million customer accounts.
Sherrif's Department pays ransom: The San Bernardino County Sheriff's Department has paid a $1.1 million ransom to a ransomware gang that encrypted its network last month. According to the Epoch Times, the county paid $511,852 of the sum, while the rest was covered by its cyber insurer. Compared to past ransomware payments, that's quite the sum for such a small Sherrif's department.
Smashing Pumpkins extortion: Smashing Pumpkins lead singer Billy Corgan paid hackers a ransom to prevent the leak of nine songs from the band's latest album ATUM. Corgan says the hack took place around six months ago, last year, while the album was going through mixing and mastering. The artist says he paid the ransom out of his own pocket and then notified the FBI, which eventually tracked down and arrested the hacker. Corgan says the hacker obtained the files from a person who was also handling content for other artists but declined to name the individual.
Scam site leak: A company that scams US citizens with fake USPS jobs has leaked the personal information of more than 900,000 of its past victims. According to KrebsOnSecurity, the data appears to have leaked from US Job Services, a company based in Lawrenceville, Georgia.
IoM Energy snafu: The main energy provider for the Isle of Man has had an embarrassing data leak after it sent all this month's customer invoices to one single person. The emails contained sensitive data such as names, addresses, and client IDs for other Isle of Man Energy customers. The company says it informed authorities of the incident, and the customer who received the emails has since deleted them. [Additional coverage in Three.fm]
Panama Papers documentary: Alex Winter's 100-minute documentary on the Panama Papers leak is now available to stream for free via the Documentary+ platform.
DEUS Finance crypto-heist: DeFi platform DEUS Finance lost $6 million worth of crypto-assets after a threat actor exploited a vulnerability in one of its smart contracts. DEUS promised not to press charges against the attacker if they returned 80% of the stolen funds—with the attacker being allowed to keep 20% as a "bug bounty" reward. The company said it will reimburse the stolen funds and publish a post-mortem of the attack.
General tech and privacy
TikTok tracked FT journalist: TikTok has confirmed it tracked the movements of Financial Times reporter Cristina Criddle in order to discover if she was meeting with TikTok employees and identify her sources. Criddle didn't have an account in her name and says TikTok tracked the account she made for her cat. She is the fourth known reporter that TikTok admitted to having spied on. Previously, the company confirmed it tracked Emily Baker-White, Katharine Schwab, and Richard Nieva, three Forbes journalists that were working at the time for BuzzFeed News. The four incidents were discovered as part of an internal TikTok security audit. [See FT coverage / non-paywall]
Binance warns customers of Google Authenticator: Binance is warning customers who use the Google Authenticator app as their MFA solution that their accounts may be vulnerable to attacks. The warning comes a week after Google announced that the Authenticator app would be able to save backup codes to Google accounts. Binance says that following this change, if a threat actor gains access to a victim's Google account, they would also be able to retrieve Binance one-time codes from the Authenticator app backups and access and steal Binance funds.
New WhatsApp feature: Meta engineers are working on a new feature that will allow users to mute incoming calls from unknown numbers. The feature is currently under testing in WhatsApp's beta versions.
Mozilla launches Mastodon instance: The Mozilla team has launched its official Mastodon server. The instance is live at mozilla.social, currently in beta, and new users have to sign up via a waiting list.
Opera One: Opera unveiled last month Opera One, a reimaged and redesigned version of its browser, which the company says is planned to replace its current flagship browser. The browser's main addition is "tab islands," aka tab groups.
Azure AD CBA mobile support: Microsoft Azure Active Directory (Azure AD) Certificate-Based Authentication (CBA) now supports authenticating mobile devices, such as Android and iOS smartphones, via YubiKey devices.
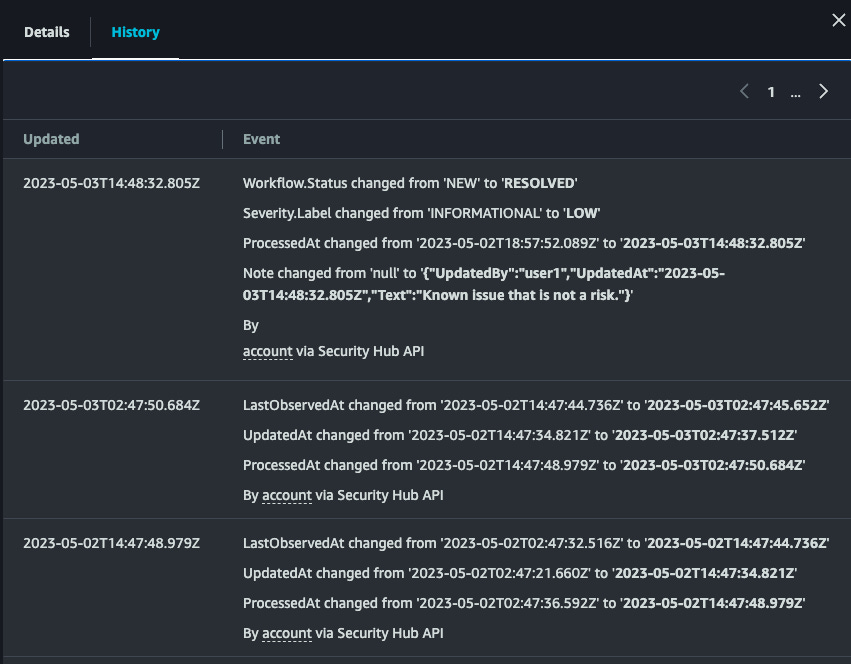
AWS history feature: AWS has added a "Finding History" feature to allow security teams to track historical changes made to a security issue found on their infrastructure.
"To try out this new feature, open the Security Hub console, select a finding, and choose the History tab. There you will see a chronological list of changes that have been made to the finding. The transparency of the finding history helps you quickly assess the status of the finding, understand actions already taken, and take the necessary actions to mitigate risk."
Government, politics, and policy
New York crypto-legislation: New York Attorney General Letitia James submitted a bill last week that would introduce a slew of regulations for cryptocurrency platforms active in the state. If approved, James says the bill will introduce the strongest and most comprehensive set of regulations on cryptocurrency companies across any US state. Among the bill's most interesting points are mandatory know-your-customer (KYC) provisions for cryptocurrency platforms and a ban on cryptocurrency exchanges from issuing and trading in their own tokens. Cryptocurrency companies would also be banned from using terms like "stablecoins" unless such digital assets are backed 1:1 with US currency. The bill also mandates that crypto exchanges reimburse customers who were victims of fraud, the same rules that have been active in the banking sector for years.
RTF anniversary: On the two-year anniversary of its launch, the Ransomware Task Force says its efforts to get governments and the private sector to act against ransomware attacks are finally coming to fruition. The non-profit says that 92% of the 48 recommendations the organization made in 2021 have seen some action, with more than half seeing significant progress, "including through legislation and policy adoption." More in the organization's overview report and press conference (embedded below). [Additional coverage in Decipher]
Sponsor Section
Material Security co-founder Ryan Noon demos Material Security's email security solution to Risky Business podcast host Patrick Gray.
Cybercrime and threat intel
Dutch hacker detained: Dutch police detained a 25-year-old man from the city of Purmerend for hacking a Dutch company from Haarlem and attempting to extort the company for €50,000 with the threat of leaking the data of hundreds of thousands of its customers.
Cyberstalker and extortionist sentenced: A Texas man was sentenced to five years in prison for a relentless one-year-long cyberstalking and extortion campaign that targeted a female victim and her family. Authorities say Jordy Julian Alvarez threatened to release a female victim's compromising photos and videos online and ruin her reputation unless she provided him with new explicit videos. Alvarez did not only send threats to the victim but also targeted her father, brother, and grandmother. When the victim did not comply, Alvarez also made death threats against her and her family.
New npm malware: Eight new malicious npm packages were spotted last week. Check out GitHub's security advisory portal for more details.
New Katyushabit ransomware: A new ransomware strain has been spotted in the wild since mid-April. Named Katyushabit, besides showing a ransom demand, the group also includes an "ad" in its ransom note, offering to pay individuals up to 40% of a future ransom if they provide access to a company's network, such as RDP, VPN, or corporate email credentials.
New Cactus ransomware: Kroll security researchers have spotted a new ransomware group named Cactus that exploits vulnerabilities in Fortinet VPN appliances to gain access and then encrypt corporate networks. The ransomware has been active since March this year, and one of its tricks has been to encrypt its own ransomware binary to avoid detection when first infecting a victim. Kroll says they've seen the gang steal files from the networks they breach, but they have not seen the gang run a leak site on the dark web, like most ransomware gangs today.
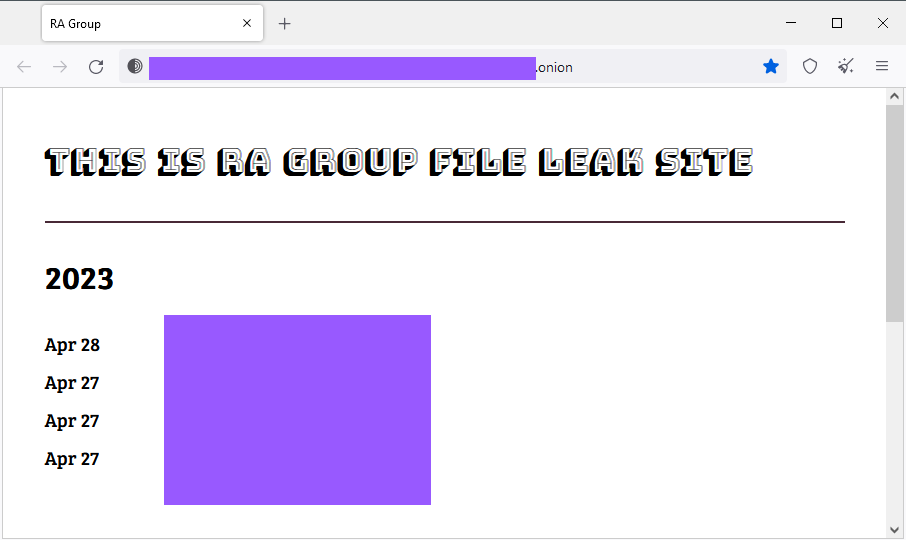
New RA Group ransomware: Security researcher MalwareHunterTeam has discovered a new ransomware gang named RA Group. The malware was coded on top of the leaked Babuk ransomware source code, and the gang also runs a data leak site on the dark web.
Netskope cloud threats report: Cybersecurity firm Netskop says that 5 out of every 1000 enterprise users attempted to download malware in the first quarter of the year. Of these malware payloads, 55% were hosted on popular cloud hosting services. [Report/PDF]
SmokeLoader campaign: CERT-UA says UAC-0006, a financially-motivated threat actor, is targeting Ukrainian organizations with malspam emails that infect victims with the SmokeLoader malware.
Guildma technique: SANS ISC researcher Renato Marinho has a breakdown of a new technique used by the Guildma banking trojan to bypass security solutions and abuse the BITSAdmin utility.
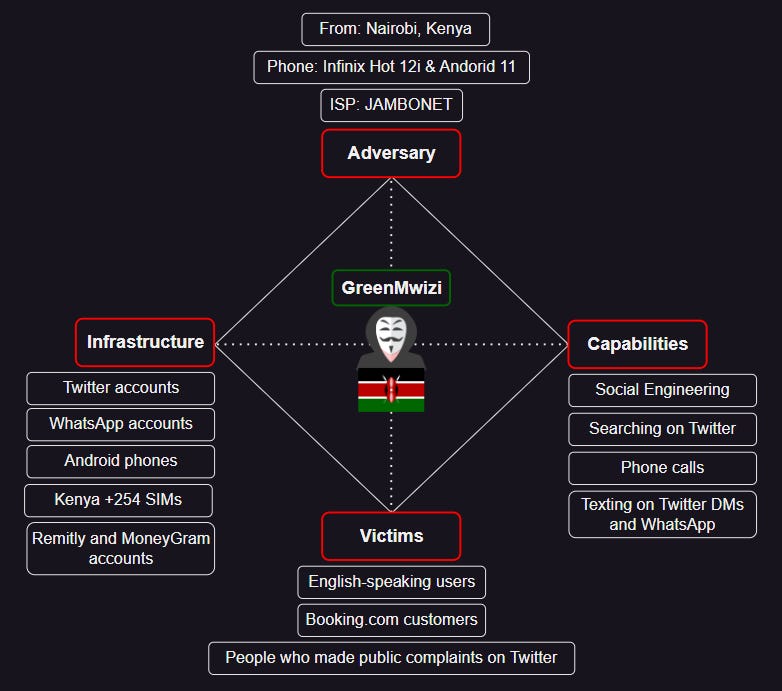
New GreenMwizi group: Equinix security researcher William Thomas has discovered a new threat actor named GreenMwizi that is conducting social engineering scams using Twitter. Thomas says the group uses a dozen fake Booking.com Twitter accounts to reply to users who make public complaints about the company's services. The group's main aim is to socially engineer users over WhatsApp into sending funds to its members via Remitly, an international money transfer service. Thomas says he interacted with the gang and traced several of its phone numbers and IP addresses. Based on his findings, the researcher believes the gang operates out of Kenya.
"This type of activity is extremely common on Twitter. Users should always do their due diligence if they respond to an "official" account replying to them. Ever since Elon Musk decided to remove the blue verification icon from many official Twitter accounts, this issue has been exacerbated. Organizations whose users rely on Twitter to communicate with them should be proactively monitoring for these types of scammers to prevent them from being victimized. Now more so than ever, since Elon Musk's Twitter is failing to respond to the bot issues such as this themselves."
Malware technical reports
DeathNote: Synack researcher Mayank Malik published a breakdown of the DeathNote infostealer. Not to be confused with the Lazarus Group's DeathNote campaign.
IcedID: Elastic's security team published a report on unpacking and analyzing IcedID malware samples (PAN has one out too). The team also released tools to decrypt and analyze IcedID samples.
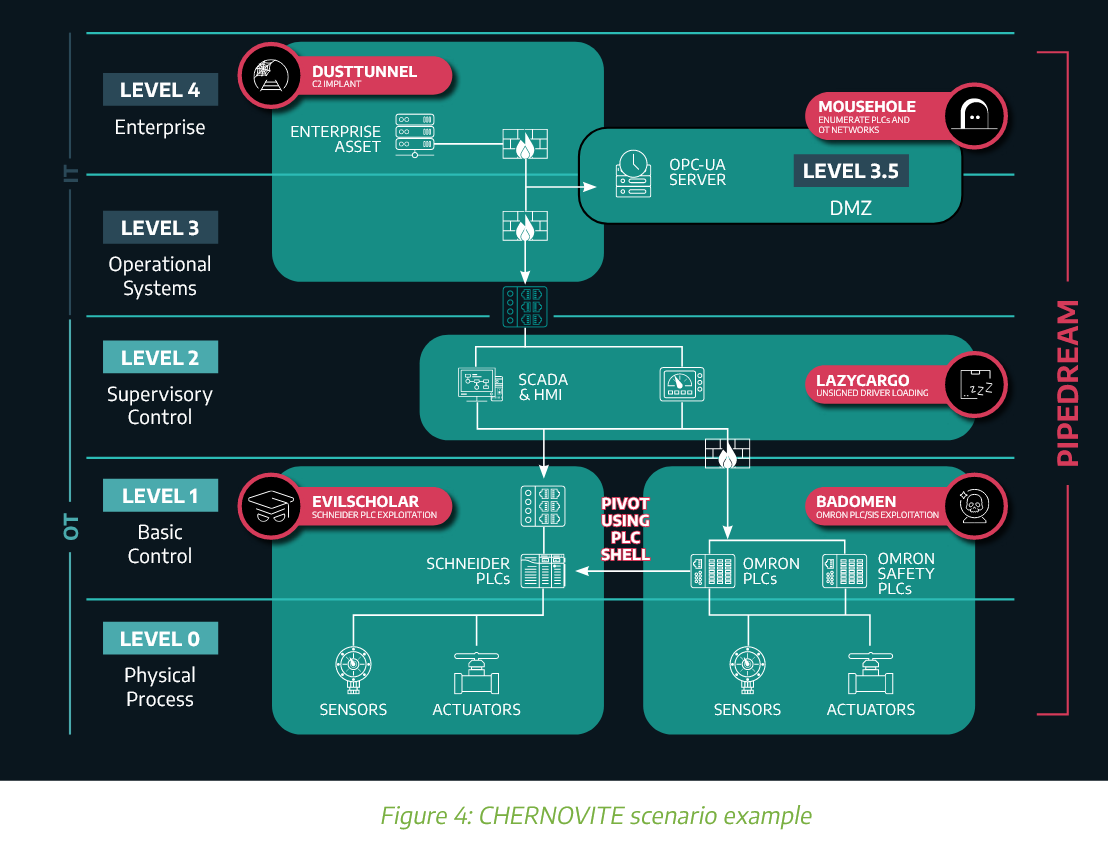
MOUSEHOLE: Dragos has published a technical analysis of MOUSEHOLE, one of the five modules of PIPEDREAM, an ICS malware framework developed by the Chernovite group. The malware was discovered last year, and the MOUSEHOLE module is used for gaining access and interacting with OPC UA servers, typically found on ICS/SCADA equipment. Dragos says MOUSEHOLE can scan networks for the presence of OPC UA servers, perform brute-force attacks and infiltrate the server, read its "structure" and "atributes," and set various security settings such as security mode, policies, certificates, and private keys.
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
APTs and cyber-espionage
Iranian groups and PaperCut: Microsoft's security team says it is seeing three Iranian APT groups launching attacks against PaperCut print management servers. The first attacks were carried out by a financially-motivated group it tracks as Lace Tempest (DEV-0950). Since then, Microsoft says that Iranian cyber-espionage groups have also started exploiting the same bug in order to gain access to corporate and government networks. This includes the likes of Mint Sandstorm (PHOSPHORUS, APT35, Charming Kitten) and Mango Sandstorm (MERCURY, MuddyWater), groups associated with the country's Islamic Revolutionary Guard Corps (IRGC) and Ministry of Intelligence and Security (MOIS).
(Cyber)-war in Ukraine Q1 2023: According to a report from the CyberPeace Institute, in the first quarter of the year, there were 360 cyber-incidents related to the Russo-Ukrainian war that targeted Ukrainian entities, 241 incidents that targeted Russian organizations, and 936 against other countries. Of the latter category, Poland took the brunt of the attacks, with 173 recorded incidents. The vast majority of these incidents, regardless of their targets, were DDoS attacks—typically carried out by various pro-Kremlin and pro-Ukraine hacktivist groups.
Vulnerabilities and bug bounty
TikTok vulnerability: Imperva security researchers have discovered a vulnerability that could be used to monitor a user's activity on both mobile and desktop devices. TikTok has fixed the issue.
OpenAI vulnerability: Cybersecurity firm Checkmarx has identified a vulnerability in the OpenAI platform that could have been used to gain access to unlimited credit and allow threat actors to perform any amount of ChatGPT queries they wanted. The issue was discovered and reported to OpenAI last December, and the company fixed the bug at the start of March 2023. Checkmarx says the issue resided in the company's account validation process, which they were able to bypass "using Unicode encoding on certain non-ASCII bytes" and register multiple accounts using the same user details.
Linux vulnerability: Trustwave researchers published a report on CVE-2023-29383, a vulnerability in the Linux chfn (change finger) utility. The vulnerability can be used to fake an edit to the /etc/psswd file.
Windows Graphics vulnerability: Trellix researchers have published details on CVE-2022-37985, a vulnerability they discovered in the Windows Graphics component last year and which Microsoft patched in October.
Videostream vulnerability: Google software engineer Dan Revah has discovered an LPE vulnerability (CVE-2023-25394) in Videostream, a user-friendly wireless application designed to stream videos, music, and images to Google Chromecast devices.
Dependabot vulnerability: Giraffe Security has discovered a dependency confusion vulnerability in GitHub's Dependabot service
"To fix the issue, GitHub removed the Git dependency to NPM public registry source conversion functionality from Dependabot. They rewarded me a bounty of $2500 for finding the issue."
Cookie handling bugs: Security researcher Ankur Sundara has discovered that four web frameworks are incorrectly handling cookie files opening the doors for various attacks and leaks. Vulnerable frameworks include Jetty, TomCat, Undertow, and Zope.
Infosec industry
Google Cybersecurity Certificate: Google has added a cybersecurity training course to Google Career Certificates, a program that provides affordable training to job seekers. Named the Google Cybersecurity Certificate, the course will cost from $150 to $300. Google says more than 150,000 people have graduated via its Google Career Certificates program in the US since 2018.
New tool—rules_oci: Google has open-sourced a new tool named rules_oci that can help developers quickly build test (OCI-compatible) containers. The containers are compatible with Bazel, a Google build and testing toolkit.
DEF CON AI Village: At this year's DEF CON AI Village, several of the world's largest AI companies will have their AI systems prodded by the world's best security researchers. Participating companies include Anthropic, Google, Hugging Face, Microsoft, NVIDIA, OpenAI, and Stability AI. Security researchers will analyze if AI systems developed by these companies follow guidelines described in the AI Bill of Rights and the AI Risk Management Framework, two guidelines published last week by the Biden Administration as part of a push for "responsible AI innovation."




