Risky Biz News: China faces its first truly mega-leak
In other news: Hackers extort Marriott; the Tel-Aviv Metro hack that wasn't; and OpenSSL and Windows Kerberos bugs.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
When you have a population of more than 1.4 billion people, a data breach of epic proportions is just bound to happen at one point or another, and it's more of a question of time. While something like this has happened in the United States on several occasions, the Chinese government is currently dealing with the first mega leak of its kind and, by far, the largest data breach in the country's history.
While the leak occurred months before, the incident came to light over the weekend, after a threat actor named ChinaDan posted an ad on an underground cybercrime forum, claiming to have obtained the personal data of more than one billion Chinese nationals from a database server that was left exposed online by the Shanghai National Police (SHGA).
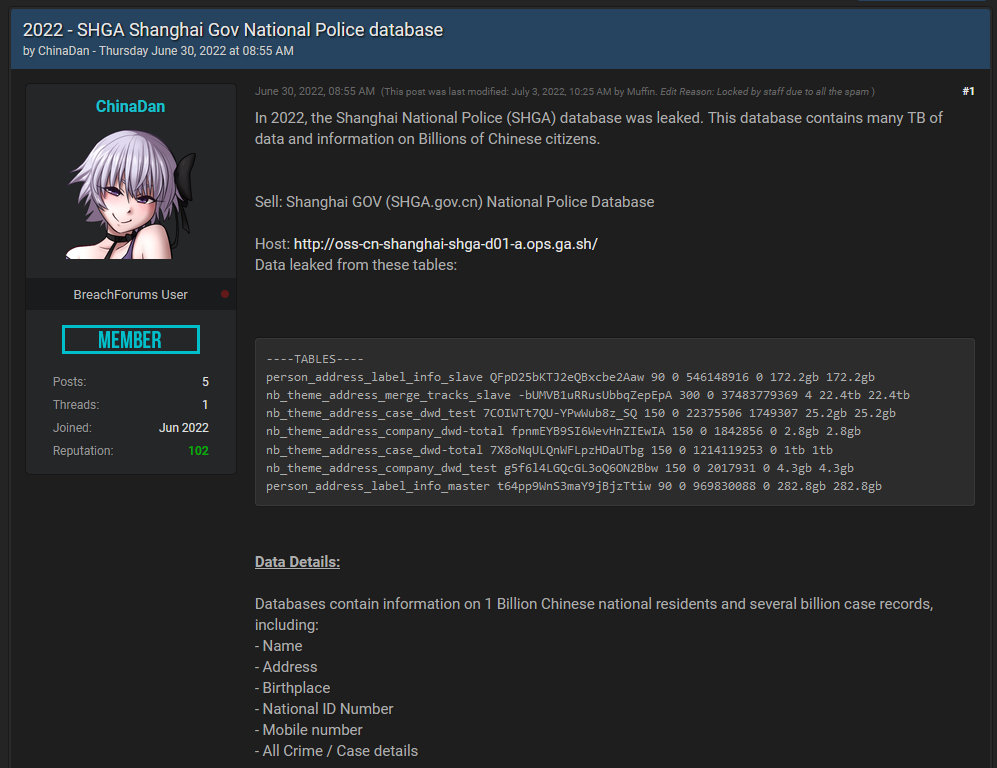
According to a sample released by the threat actor, the data contains details such as names, addresses, national ID numbers, mobile numbers, and police and medical records.
ChinaDan said they are currently looking for buyers for this gigantic data trove, with which they were willing to part ways for the tiny sum of $200,000 worth of Bitcoin.
While previous leaks sold for this price have often turned out to be scams or publicity stunts, reporters from the Wall Street Journal and CNN said they already confirmed the data's authenticity with some of the victims who had information listed in ChinaDan's samples.
And in the old adage that "don't believe anything until Russia China denies it," it didn't take long for an official confirmation of the leak's authenticity to come through—as Chinese authorities began censoring talk on the leak on Chinese social media as soon as news started getting traction on Monday, the Financial Times reported.
But by this point, it may be too late for the Chinese government to curtail discussions on the incident, as several cyber-security firms and researchers have already confirmed that the leak is authentic and that it came from a government source.
The leak also comes at a sensitive time for Beijing, as the government has been churning out rules and legislation on data privacy and data security over the past two years. While the government may have targeted its sprawling and generally-unregulated tech sector, the incident may end up being a seminal moment for its public agencies as well, many of which have leaked similar information before, but on a smaller scale.
Such leaks have been happening in China's corner of the internet for years but have been largely ignored by western security firms and security researchers, many of which have been focused on providing services for western countries and companies, and past China-related leaks have typically never been shared outside local underground hacking forums and got very small coverage in some rogue Chinese IT and security blogs, once in a while.
Breaches and hacks
Marriott security breach: The Marriott hotel chain confirmed on Tuesday a security incident after hackers broke into the company's IT network and stole 20GB of sensitive data, including some documents containing credit card information. DataBreaches.net—which first reported the incident and had been in contact with the hackers—said the threat actor had been trying to extort the hotel chain over the past few weeks, asking for a ransom demand to not disclose the security breach to the public.
Tutu hack: Hackers have leaked the data of millions of users of Tutu.ru, a Russian online portal that can be used to book airplane, train, and bus tickets for national and international travel. Data for tens of millions of users has been leaked, including details such as names, home addresses, phone numbers, emails, passport scans, and even some hashed passwords. Tutu confirmed the breach in a statement to Russian media.
The cyber-attack that wasn't: A Palestinian group of hackers known as Sabareen and Iranian media ran pompous reports on Monday about a cyber-attack that crippled Tel Aviv's metro system. The problem with the reports is that Tel Aviv doesn't have a functional metro system, which is still under construction, so the hackers didn't disrupt anything except some poor construction company's homepage.
Iranian media saying there was a cyberattack on the Tel Aviv Metro. The Tel Aviv Metro does not exist. https://t.co/0B8Q5XFb1b
— Lahav Harkov (@LahavHarkov) 7:31 AM ∙ Jul 4, 2022
Another crypto-heist: DeFi service Crema Finance lost $8.78 million worth of cryptocurrency over the weekend after an attacker exploited a bug in the company's platform. Blockchain security firm OtterSec described the incident as yet another "flash loan" attack that have plagued DeFi platforms for the past two years. In a series of tweets posted on Monday and Tuesday, Crema Finance said its investigation is going well, and they believe they already identified the threat actor's trail, including their Discord account.
New progress: According to the clues provided by our partners, we found the suspect discord account of the hacker that he/she was using during the hacking incident. We're approaching relevant parties to get more information that may help with the detection.
— CremaFinance (@Crema_Finance) 12:07 PM ∙ Jul 4, 2022
Significant progress: By tracing the original gas sources of the hacker’s address, we targeted a suspicious identity that might relate to the hacking incident. New updates will be shared following a further verification.
— CremaFinance (@Crema_Finance) 4:12 AM ∙ Jul 5, 2022
General tech and privacy
EU puts out new big tech rules: The EU passed on Tuesday the Digital Services Act and Digital Markets Act, two pieces of legislation meant to curtail big tech's powers and give more power to end-users. The Digital Services Act is focused on user security, data privacy, and also takes great care to push companies to be more aggressive with content moderation, including cracking down on misinformation campaigns. The Digital Markets Act cracks down on walled gardens—forcing big tech to play nice with smaller companies, such as providing service interoperability.
Chrome zero-day: Google released Chrome v103.0.5060.114 for Windows users to patch an actively exploited zero-day (CVE-2022-2294). The vulnerability was described as a heap buffer overflow in Chrome's WebRTC component and was found by Jan Vojtesek from security firm Avast last Friday.
AirTag abuse: Well, it has happened. A local Japanese gang has apparently put Apple AirTag devices on police cars to track them. [via InfoOps]
Government, politics, and policy
Russian govt on cyber-attacks: The Russian government said that while at the start of the war, cyber-attacks have disrupted the activity of many of its websites, the government and the private sector are getting better at stopping incoming attacks, especially DDoS attacks. [via Oleg Shakirov]
UK MPs call for Dahua and Hikvision ban: A group of 67 MPs has called on the UK government to formally ban the sale and use of Dahua and Hikvision CCTV cameras in the UK. Equipment made by the two companies has been linked to human rights abuses and intensive surveillance in China's Xinjiang region.
NIST quantum-resistant encryption news: US NIST announced on Tuesday that it chose the first set of quantum-resistant encryption algorithms meant to protect sensitive data against an attack from a quantum computer. The four selected algorithms are CRYSTALS-Kyber, CRYSTALS-Dilithium, FALCON, and SPHINCS+, and NIST said they would become part of the agency's post-quantum cryptographic standard, expected to be finalized in the next two years.
Cybercrime and threat intel
GanjaMask: Cannabis ISAO, a security group inside the nascent US cannabis industry, published a report last week on GanjaMask, a threat actor targeting their members. Cannabis ISAO says GanjaMask runs a network of websites posing as fake US-based cannabis stores. The role of these websites is to collect payments and payment card details from customers who place orders through the sites.
Academic research on Gozi: An academic study published earlier this year looked at the internal structure and operations of the Gozi cybercrime cartel.
AstraLocker releases decryption keys: The operators of the AstraLocker ransomware said they are shutting down their operation and have released free decryption keys for all their past victims. The gang told BleepingComputer they are now switching to running a crypto-mining botnet.
Malicious npm libraries: In a report published on Tuesday, ReversingLabs said it found 31 npm libraries that contained obfuscated JavaScript code that would steal web form data. The npm packages had been available on the npm portal for the past two months, and the vast majority were disguised to look like tools meant for manipulating and working with icon images. ReversingLabs said the libraries contained hidden code that would steal any data that users entered inside forms on websites or mobile apps where the malicious libraries would be accidentally included. The attack most likely targeted information entered in password fields and payment forms, data that threat actors could easily monetize.
Luna Moth: Security firm Sygnia has published a report on Luna Moth, a new threat actor that, since March this year, has been engaging in hack-and-extortion attacks. Sygnia said Luna Moth uses spear-phishing to infect victims with a remote access trojan, which it then uses to steal sensitive data that can be used in a future extortion attempt. The company reported that some extortion demands reached "millions of dollars."
XFiles campaign: Threat intelligence company CyberInt said in a report on Sunday that it detected a malware distribution campaign spreading the XFiles infostealer trojan with documents weaponized with the Follina Office zero-day.
Chropex campaign: Broadcom's Symantec team said it detected a rise in attacks distributing Chropex, a browser hijacker targeting macOS platforms that can monitor Safari searches and insert ads in web pages. Symantec said the Choprex group typically uses malvertising campaigns and drive-by downloads to distribute their payload.
New RedAlert ransomware: Security researchers also discovered a new ransomware operation this week. Named RedAlert, according to BleepingComputer, this group has tools that can encrypt Windows and Linux-based VMWare eSXi servers alike.
A look at RedAlert ransomware gang's leak site, titled "Board of shame".
— MalwareHunterTeam (@malwrhunterteam) 6:25 PM ∙ Jul 5, 2022
Currently only 1 victim listed...
Malware technical reports
Hive ransomware: Microsoft has published a technical analysis of the Hive gang's new Rust-based ransomware strain, which the group has been using in attacks since March this year.
APTs and cyber-espionage
VSingle: Japan's CERT team has published a report on new versions of VSingle, a malware strain used by North Korean state-sponsored hackers, targeting both Windows and Linux users. This new report focuses on the updates to the Linux version, which has been updated to include a backup mechanism for obtaining command-and-control server information from GitHub repositories.
Bitter APT: Researchers from German security firm SECUINFRA have published a report on a campaign carried out by the Bitter APT against targets in Bangladesh. The campaign's end goal was to infect victims with the Almond RAT.
Brute Ratel abuse: Palo Alto Networks said it identified a suspected APT29 campaign that abused Brute Ratel, an adversary emulation framework developed by a former Crowdstrike and Mandiant security engineer. The Brute Ratel author said they took actions against the licenses abused in these attacks, which they claim were sold on the black market.
A thoroughly detailed blog on Brute Ratel C4 by Palo Alto. Proper Actions have been taken to against the found licenses which were sold in the Black Market. As for existing customers, #BRc4 v1.1 release will change every aspect of IOC found in the previous releases.
— Paranoid Ninja (Brute Ratel C4) (@NinjaParanoid) 2:57 PM ∙ Jul 5, 2022
Konni targets Russia: Lumen's Black Lotus Labs have published a report on a recent spear-phishing campaign targeting Russian targets that they linked to Konni, a North Korea-based espionage group. The group previously targeted Russian government agencies earlier this year.
We found another #Konni lure written in Russian that was active in the wild last week
— Black Lotus Labs (@BlackLotusLabs) 2:11 PM ∙ Jul 5, 2022
Vulnerabilities and bug bounty
Windows Kerberos bug: James Forshaw of Google's Project Zero has published a technical analysis about a vulnerability that allows remote code execution (CVE-2022-24545) and elevation of privilege (CVE-2022-30165) in the Windows Kerberos service. The vulnerability can be exploited in unpatched systems via CredSSP, a Windows protocol designed to securely forward authentication credentials between a client and a remote server in an internal network/domain.
OpenSSL bug: The OpenSSL project released a security update on Tuesday to fix several security flaws, including a vulnerability that, under certain scenarios, can lead to remote code execution on a small subset of OpenSSL servers.
The OpenSSL security issue will get a lot of press attention.. but the scope is extremely small.
— Kevin Beaumont (@GossiTheDog) 9:44 PM ∙ Jul 5, 2022
It only impacts one (newer) version, and needs a specific configuration and a specific CPU.. and also the code didn't compile properly.
EternalBlue, five years later: Five years after the WannaCry and NotPetya ransomware outbreaks, Jan Kopriva of ISC SANS says that the number of internet-connected systems vulnerable to the EternalBlue exploit has decreased by more than two-thirds.