Risky Biz News: IntrusionTruth was right (again)
In other news: Germany has a major Microsoft Exchange problem; China blocks foreign technology on government networks; and new ZenHammer attack impacts AMD Zen CPUs.

This newsletter is brought to you by Sublime Security, an email security platform that's not a black box. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The governments of Australia, New Zealand, the UK, the US, and the EU have called out China again over its broad, clumsy, and sometimes illegal hacking campaigns.
The push behind this latest round of diplomacy finger-pointing came from the UK and US, the two countries that appear to have seen the brunt of these campaigns.
Western officials are miffed—and deservedly so—about China's targeting and attempts to meddle in their democratic and election processes.
The UK has called out two Chinese hacking campaigns that it considers to have crossed a line. The first is a campaign that targeted and gained access to the email inboxes of UK Parliament members in 2021. The second is a breach of the UK Electoral Commission, following which a Chinese hacking group is believed to have accessed and stolen data from the UK Electoral Register.
The UK made the accusations, and the EU, Australia, and New Zealand joined the British in their finger-pointing.
The US did, too, but also lowered the hammer on one of the two groups—APT31, the group that accessed UK MP inboxes in 2021.
The hammer arrived with a formal indictment, sanctions, and a generous reward.

The indictment named seven Chinese nationals believed to be members of the group.
Sanctions were then levied on two of seven, and a company from the city of Wuhan named Wuhan Xiaoruizhi Science and Technology Company, Limited.
US officials described Wuhan Xiaoruizhi as a contractor and front company for the Hubei provincial branch of China's Ministry of State Security (MSS).
The company has been allegedly conducting operations for the MSS Hubei branch since 2010.
Throughout the years, the group has targeted foreign governments for intelligence collection, has spied on local and foreign political dissidents, and has helped "transfer" intellectual property and trade secrets from foreign companies to China.
According to the DOJ indictment, the MSS used APT31 to hack and spy on foreign diplomats critical of the Chinese government. While the UK had never revealed the size of its 2021 Parliament breach, the US did so in its press release, putting the tally at 43. See the quote below.
The defendants and others in the APT31 Group also sent malicious tracking-link emails to government officials across the world who expressed criticism of the PRC government. For example, in or about 2021, the conspirators targeted the email accounts of various foreign government individuals who were part of the Inter-Parliamentary Alliance on China (IPAC), a group founded in 2020 on the anniversary of the 1989 Tiananmen Square protests whose stated purpose was to counter the threats posed by the Chinese Communist Party to the international order and democratic principles. The targets included every European Union member of IPAC, and 43 United Kingdom parliamentary accounts, most of whom were members of IPAC or had been outspoken on topics relating to the PRC government.
But China hacking EU diplomats is not a crime in the US. It is a crime to hack and steal from US companies in obvious non-espionage campaigns, and hack US diplomats and... wait for it... their families.
"Additionally in some cases, the defendants also targeted victims’ spouses, including the spouses of a high-ranking Department of Justice official, high-ranking White House officials, and multiple U.S. Senators. Targets also included election campaign staff from both major U.S. political parties in advance of the 2020 election."
The DOJ indictment also confirms that APT31 was behind the 2018 hack of the Norwegian government. US officials did not confirm a similar hack of the Finnish Parliament, but Finnish police did it themselves a day later.
"The defendants and the APT31 Group also targeted individual dissidents around the world and other individuals who were perceived as supporting such dissidents. For example, in 2018, after several activists who spearheaded Hong Kong’s Umbrella Movement were nominated for the Nobel Peace Prize, the defendants and the APT31 Group targeted Norwegian government officials and a Norwegian managed service provider. The conspirators also successfully compromised Hong Kong pro-democracy activists and their associates located in Hong Kong, the United States, and other foreign locations with identical malware."
This paints a picture of APT31 being the Chinese government's go-to group when it needed to hack a foreign government. One thing to take out of this is that APT31 received a lot of work, especially on sensitive topics, and appears to have been held in high regard in Chinese intelligence circles.
In response to all of this, the Chinese government has issued its typical "we don't hack, you hack more" reaction.
The indictment is now the fifth time that an exposé from the mysterious IntrusionTruth group reveals the MSS' links to Chinese APTs and (in all cases except one) leads to a DOJ indictment.
- APT3 - believed to operate out of the Guangdong province
- APT10 - Tianjin province
- APT17 - Jinan province (no DOJ indictment)
- APT40 - Hainan province
In five reports in May of last year—1, 2, 3, 4, 5—, IntrusionTruth exposed MSS Hubei's links to Wuhan Xiaoruizh and four of the seven APT31 indicted members.
At this point, the most obvious conclusion is that someone in the DOJ is subscribed to IntrusionTruth's RSS feed—whoever this APT-doxing group may be (infosec or intelligence service members, as the rumor mongers seem to believe).
UPDATE: This piece was updated on April 4 to clarify that the DOJ has not (yet) indicted any APT17 members.
Breaches, hacks, and security incidents
Curio crypto-heist: A threat actor has stolen $16 million worth of assets from the Curio DeFi platform. The attacker exploited a vulnerability in the platform's smart contract to mint and steal new tokens. The vulnerability was described as a permission access logic.
General tech and privacy
Autodesk pulls out of Russia: Following a similar move from Microsoft, Autodesk has also pulled out of Russia. [Additional coverage in RBC]
Atlas VPN shutdown: The Atlas VPN service will cease operations on April 24. All of the company's users will be moved to NordVPN.
MLS shutdown: The Mozilla Foundation is retiring its privacy-friendly geolocation service. Employees say the service saw a decline in accuracy after a lack of funding in recent years. The Mozilla Location Service (MLS) launched in 2013 and operated on operated on GPS data submitted by the community. The service will shut down in phases between March and July this year.
Telegram P2PL: Telegram has announced a new feature named Peer-to-Peer Login, or P2PL. The new feature allows Telegram to use the phone numbers of volunteering users to send one-time passcodes (OTPs) to other Telegram users. The move comes after Twilio raised prices for using its service. [Additional coverage in The Verge]
In-app browsers study: Research published by the Open Web Advocacy highlights the user privacy issues with apps that block users into their custom in-app browsers. [h/t Lukasz Olejnik]
Government, politics, and policy
China blocks foreign technology on government networks: China introduced new guidelines that block the procurement of foreign technologies for government PCs and servers. The guidelines ban the use of Intel and AMD chips, Microsoft Windows, and foreign database servers. The new procurement guidelines were introduced in December of last year. Chinese officials have urged agencies to switch to domestic alternatives. [Additional coverage in CNBC]
Japan cyber defense drills: Japan held its first cyber defense drill at the end of last month. The event was held in Guam in February. Kiribati, the Marshall Islands, Micronesia, Nauru, and Palau also participated in Japan's cybersecurity exercise. [Additional coverage in DarkReading]
Russian bug bounty law: The Russian government is working on a law to legalize and regulate software bug bounty work. It is still in its early phases. [Additional coverage in Ria Novosti]
US sanctions more crypto exchanges: The US Treasury has imposed sanctions on thirteen Russian companies and two individuals for helping the government evade international sanctions using cryptocurrency and virtual currency. (Quote via Under Secretary of the Treasury for Terrorism and Financial Intelligence, Brian E. Nelson)
"Russia is increasingly turning to alternative payment mechanisms to circumvent US sanctions and continue to fund its war against Ukraine. As the Kremlin seeks to leverage entities in the financial technology space, Treasury will continue to expose and disrupt the companies that seek to help sanctioned Russian financial institutions reconnect to the global financial system."
Another call for a US Cyber Force: A US think tank has called for the creation of the US Cyber Force as a separate branch of the US military. The Foundation for Defense of Democracies argues that having separate cyber units in each military branch is an ineffective solution when it comes to recruiting and retaining talent. The Military Cyber Professionals Association was the first one to propose a separate US Cyber Force branch last year. [Additional coverage in DefenseScoop]
CISA SbD alert: CISA has released another one of its Secure-by-Design alerts—this one targeting SQL injection vulnerabilities.
US anti-spyware effort: The US government says it expects to add more countries to its anti-spyware effort within the next six to eight months. [Additional coverage in NextGov]
UK's cyber incident guide for CEOs: The UK's NCSC has published guidance to help CEOs in public and private sector organizations respond and manage a cybersecurity incident.
EU DMA violations: The EU is investigating multiple DMA violations from Apple, Google, and Meta. This includes investigations into how Apple is complying with user choice obligations, Meta's pay-or-consent model, Apple and Google's sabotage of third-party stores, and Alphabet's tendency to self-preference its own services.
German bill on E2EE: The Federal Ministry for Digital and Transport Affairs (BMDV) has drawn up a draft bill that will make end-to-end encryption mandatory for messengers and cloud services in the future.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Josh Kamdjou, co-founder and CEO of Sublime Security. Josh describes how Sublime implemented the concept of attack surface reduction to email security last year, how it works, and what customers are saying about it.

Cybercrime and threat intel
US man fined for spoofed robocalls: A US judge has fined a Montana man $9.9 million for his role in a scheme that flooded Americans with spoofed robocalls.
Fake PyPI campaign: A malware distribution campaign has impacted the Top.gg Discord bot distribution platform after one of its developers installed a malicious Python library. The attack was detected in its early phases before any malicious code could be distributed through Top.gg. Security firm Checkmarx says the incident was part of a larger campaign that began in November 2022. The campaign leveraged fake infrastructure for the PyPI portal, typosquatting, and account takeovers through stolen cookies. Besides Top.gg, the attackers successfully compromised several other individual developers.
Malicious NuGet package: Security firm ReversingLabs has discovered a malicious .NET library on the official NuGet repository. The package contains code to take screenshots of the infected system every minute and upload the data to a remote server. ReversingLabs says the library appears to target developers who work with industrial software from Chinese company Bozhon.
MFA bombing on Apple devices: Brian Krebs looks at a recent trend where threat actors are combining MFA bombing and social engineering to target and lock Apple users out of their accounts and devices.
South Korea warns of DPRK IT workers: The South Korean National Police published an advisory warning companies against North Korean spies posing as local and foreign IT workers.
TA577: Proofpoint has published a report on TA577's latest techniques. The group is a known malspam actor known to deliver payloads like Qbot, IcedID, SystemBC, SmokeLoader, Ursnif, and Cobalt Strike.
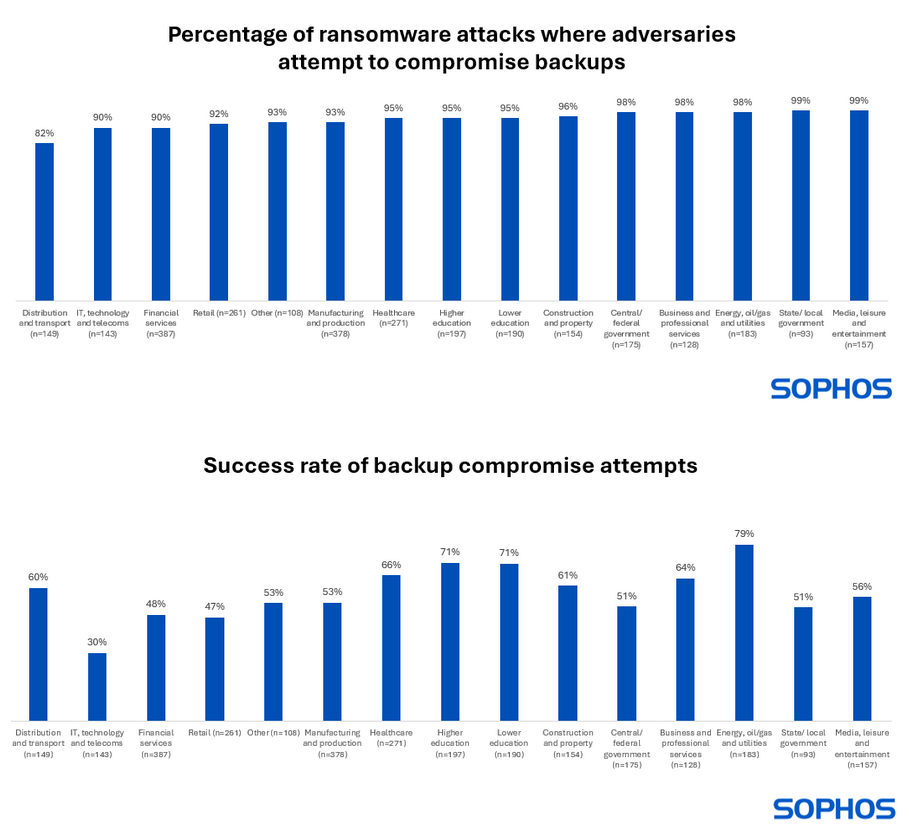
Threat/trend reports: Netskope and Sophos have recently published reports covering infosec industry threats and trends.
Malware technical reports
Latrodectus Loader: Embee Research has published a report on the new Latrodectus malware loader.
New loader: Trustwave SpiderLabs researchers have spotted a new .NET loader in campaigns that were delivering the Agent Tesla infostealer. No name for this one yet.
Raspberry Robin: Per a recent LogPoint report, Raspberry Robin, previously disseminated through USB drives, now employs Discord for distribution.
Snake keylogger: ANY.RUN has published a deep dive into Snake, a .NET-based keylogger.
WhiteSnake Stealer: Sonicwall has published a report on WhiteSnake Stealer, a complex new malware strain that combines keylogger, infostealer, and RAT capabilities.
Mispadu: Morphisec says the Mispadu banking trojan has expanded operations from Latin America and is now targeting banks all over Europe.
Qilin/Agenda ransomware: Trend Micro has published a report looking at
the Agenda ransomware operation, also known as Qilin. The company says that despite rarely making headlines, the ransomware is still extremely active.
Lighter ransomware: The same Sonicwall has also published a report on Lighter, one of those annoying smaller and low-effort ransomware strains.
Tycoon 2FA PhaaS: Sekoia has published details on Tycoon 2FA, a new phishing kit and Phishing-as-a-Service platform that launched in August of last year.
"It mainly aims to harvest Microsoft 365 session cookies to bypass the MFA process during subsequent authentication. Tycoon 2FA became widespread in the months following its release and is currently massively used in numerous phishing campaigns."
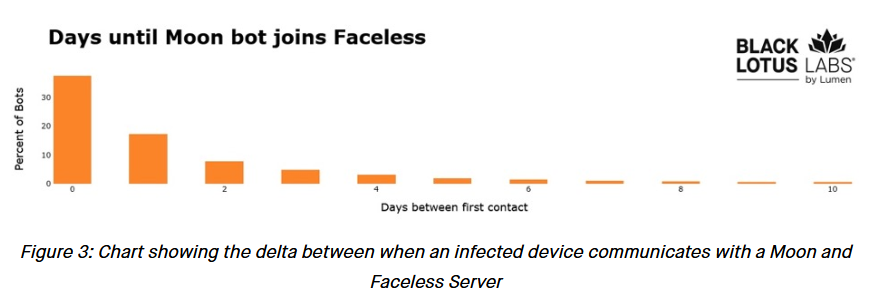
TheMoon: Security researchers from Lumen's Black Lotus Labs have linked a malware botnet known as TheMoon to Faceless, a proxy service advertised in cybercrime forums. Devices infected with TheMoon malware are typically added on Faceless within hours or days. Lumen estimates TheMoon's size at more than 40,000 infected devices. The vast majority of devices are end-of-life SOHO routers and IoT devices.
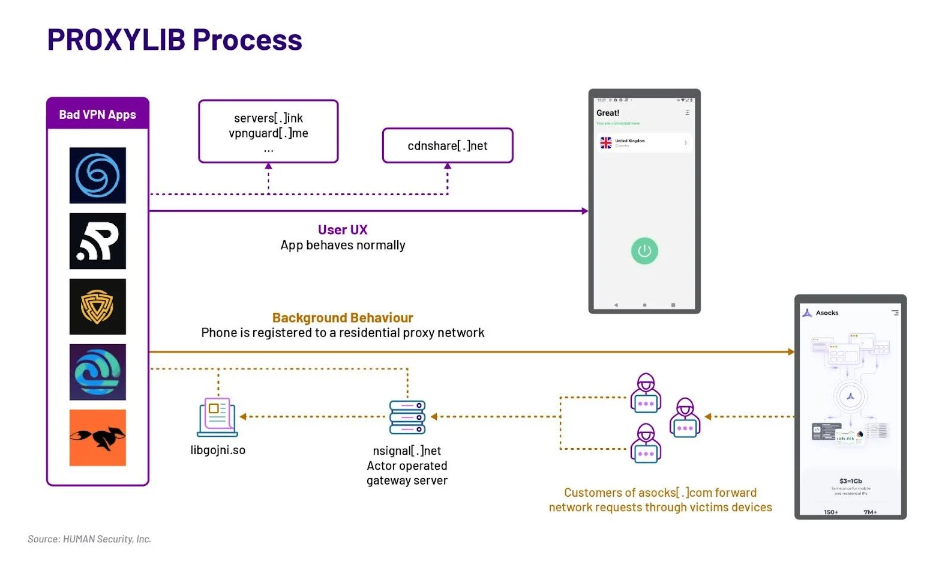
PROXYLIB: Human Security has uncovered a broad malware operation named PROXYLIB. Human Security has uncovered malware in 28 VPN-related apps uploaded on the official Google Play Store. The malware is named PROXYLIB and works by turning infected devices into nodes of a residential proxy network. Human linked the malware to residential proxy service Asocks. After Google took down the malicious apps, Human found the PROXYLIB malware inside an SDK named LumiApps.
Sponsor Section
The latest evolution of PikaBot is using phishing to gain initial access. Learn why it's been effective and how to protect your organization from novel email attacks. Read the full post.
APTs, cyber-espionage, and info-ops
Chinese hacker detained in Canada: Canada has detained a Chinese national living in Winnipeg since 2021. Officials claim Huajie Xu served as a Lieutenant Colonel in China's military and worked as an instructor in a military academy under China's cyber warfare department. Officials believe the man is a spy and are seeking his deportation. [Additional coverage in GlobalNews]
Kimsuky's Endoor and Nikidoor: AhnLab has published a report on Endoor and Nikidoor, two backdoors linked to the Kimsuky APT. The two strains were distributed disguised as installers for official South Korean government software.
PhantomCore: Russian security firm FACCT says a new threat actor named PhantomCore is behind a recent wave of attacks against Russian companies. FACCT says the group started operations in January this year, and its main tool is a remote access trojan named PhantomRAT.
Vulnerabilities, security research, and bug bounty
ShadowRay campaign: Threat actors are exploiting a vulnerability in the Anyscale Ray AI framework to compromise and take over AI servers. The attackers are using a vulnerability disclosed in November of last year that Anyscale has yet to patch. The vulnerability (CVE-2023-48022) allows the threat actors to run code on the server through one of the Ray API endpoints without needing to authenticate. Anyscale disputed the vulnerability last year, claiming the Ray framework was never meant to be used on the internet and didn't need authentication.
BSI warns of Exchange exposure: Germany's cybersecurity agency says that more than 17,000 Microsoft Exchange email servers across the country are vulnerable to one or more critical vulnerabilities. The BSI says that more than 45,000 Exchange servers are exposed on the internet without protection. More than 5,000 of these are running outdated and end-of-support versions. According to Shodan, Germany has the most internet-exposed Exchange servers in the world.
Uniview auth bypass: SSD researchers have published details and a PoC for an auth bypass (CVE-2023-0773) in Uniview IPC2322LB security cameras. The vendor has released fixes here.
Linux PoC: PwningTech's Notselwyn has published a proof-of-concept code for CVE-2024-1086, a LPE in the Linux kernel.
Apple security updates: Apple has published security updates for iOS, macOS, and Safari to fix a vulnerability in the AV1 decoder discovered by Nick Galloway of Google Project Zero.
ZenHammer attack: Academics have developed the first version of the classic RowHammer attack that can work on AMD processors. The new attack is named ZenHammer and was successfully tested on AMD's Zen CPU series. The attack can flip bits inside the CPU memory and modify or corrupt data. AMD has confirmed the attack and published mitigations.
Apple TV jailbreak: The Palera1n team has published the first jailbreak for Apple TV devices. [Additional coverage in iClarified]
Infosec industry
PancakesCon 5 streams: Recorded live streams from the PancakesCon 5 security conference, which took place last week, are available on YouTube [Track 1, Track 2].
New cyber insurance company: Marsh has launched a "group captive" insurance company to provide a more stable company for the unruly and unpredictable cyber insurance field.
New tool—Tracecat: Tracecat, an open-source automation platform for security teams, is now in alpha.
New tool—Bincapz: Security firm Chainguard has open-sourced Bincapz, a tool to analyze binaries and enumerate capabilities, including malicious behavior.

Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at Russia's recent leak of an intercepted German military discussion. From an intelligence point of view, the content of the discussion is only moderately interesting, but Russia decided to leak it in an attempt to influence European attitudes towards providing military aid to Ukraine.




