Risky Biz News: China blocks several protocols used to bypass the Great Firewall
In other news: Ferrari denies ransomware attack; White House asks for advice on cybersecurity workforce shortage; and new Maggie malware goes after MSSQL servers.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The operators of China's Great Firewall have rolled out an update this week that has blocked several protocols that have been recently utilized by Chinese citizens to bypass the country's internet censorship system.
GFW Report, a project that tracks changes in China's Great Firewall, said that protocols like trojan, Xray, V2Ray TLS+Websocket, VLESS, and gRPC have all stopped working on Monday.
All are TLS-based protocols used for tunneling internet traffic via port 443 or any other custom port.
"More than 100 users reported that at least one of their TLS-based censorship circumvention servers had been blocked," GFW Report noted on Tuesday.
"The blocking is done by blocking the specific port that the circumvention services listen on. When the user change the blocked port to a non-blocked port and keep using the circumvention tools, the entire IP addresses may get blocked," they added.
"While most of the users report their port 443 got blocked, a few users reported that their non-443 port on which circumvention services listen got blocked as well."
Researchers believe the blocking is currently being done via the TLS fingerprints of those tools and protocols and that using something like uTLS could let developers change their fingerprints and avoid the block.
The good news is that some circumvention tools are still working; although the number is slowly dwindling.
It looks like #China is now blocking multiple TLS-based circumvention tools. naiveproxy, which uses the Chrome stack, seems ok.
— Vinicius Fortuna (he/him) (@vinifortuna) 1:30 PM ∙ Oct 4, 2022
This doesn't affect Outline, which uses Shadowsocks and is not TLS-based.
The move to block these popular GFW circumvention tools comes two days after the Chinese government also blocked access to 1,147 Google domains. This includes both DNS and SNI-based blocks, in China's greatest crackdown on Google services to date.
Breaches and hacks
Telstra breach: Two weeks after Australian telco Optus disclosed a data breach, its main rival Telstra also disclosed a similar incident. However, as the company explained in a breach notification posted on its website, the incident is far smaller than the Optus breach and only involved the personal data of employees the company had back in 2017.
You may have heard about a data breach involving Telstra employee details. Here are the key facts:
— Telstra (@Telstra) 3:05 AM ∙ Oct 4, 2022
👉 This wasn't a breach of any Telstra system
👉 No customer account info was included
👉 The data includes first/last names and employee email addresses
👉 The data is from 2017
Suspected ADATA breach: The operators of the RandomHouse data extortion group claimed on early Wednesday to have breached Taiwanese hardware vendor ADATA. If confirmed, this would mark the second time the company gets hacked after suffering a ransomware attack by the RagnarLocker gang last year.
Ferrari hack: Earlier this week, on Monday, the RansomExx ransomware group claimed to have breached Italian carmaker Ferrari and leaked almost 7GB of data from the company's servers. But in a statement provided to local media, Ferrari said they haven't detected any breach or ransomware attack on their network. The company said it's still investigating the incident and that there was no disruption to its business following this particular incident—which to most security experts is starting to look like a breach of one of the carmaker's contractors; an incident that was most likely misrepresented by the attackers for increased media coverage.
The RansomExx group has leaked today 7GB of files from fancy-pants way-too-expensive carmaker Ferrari
— Catalin Cimpanu (@campuscodi) 11:01 AM ∙ Oct 3, 2022
You can look at the leaked data as much as you want, none of it will explain the abysmally bad decisions the company's F1 team has been making this year 🤣
General tech and privacy
New Arm security features: Chipmaker Arm announced a slew of new security features for its CPUs, such as support for shadow stacks via the "Guarded Control Stack (GCS)" feature, translated tables permissions hardening, and support for multiple memory encryption contexts.
Azure Firewall Basic hits public preview: Azure Firewall Basic, a stripped-down and cheaper version of the Azure Firewall service specifically designed for SMBs, has now entered public preview.
PS5 jailbreak: The PlayStation 5 has been jailbroken to allow users to install custom packages. An exploit is available on GitHub, and this marks the first major PS5 hack since its launch back in 2020. [Additional coverage in Glitched and Wololo]
It's... beautiful.
— Lance McDonald (@manfightdragon) 2:57 AM ∙ Oct 3, 2022
The PlayStation 5 has been jailbroken.
Government, politics, and policy
US-UK partnership on CLOUD Act: A collaboration agreement between the US and the UK entered into effect on Monday, extending the provisions of the CLOUD Act in both countries. Passed into law by Congress in 2018, the Clarifying Lawful Overseas Use of Data, also known as the CLOUD Act, allows law enforcement agencies access to customer data stored on the servers of US-based cloud hosting providers for the purpose of ongoing criminal investigations and on the basis of a warrant or subpoena. The joint US-UK CLOUD Act agreement allows agencies in both countries to request access to data located on servers in each others' territories for criminal investigations, albeit agencies will be able to request the data of their own citizens only. The UK collaboration comes after the US also entered into a similar CLOUD Act agreement with Australia in December 2021. [Additional coverage in NextGov]
New CISA BOD: The US Cybersecurity and Infrastructure Security Agency issued a new Binding Operational Directive (BOD 23-01) on Monday and mandated that all federal civilian agencies scan their networks in order to discover all their assets, including vulnerable systems that will need to be patched. Agencies must report their findings to CISA within six months, by April 3, 2023, so CISA would have a better understanding of the nation's cyber resilience and needed defensive actions. [Additional coverage in Cyberscoop]
Cyber activity unlikely to impact elections: In a joint public service announcement on Tuesday, the FBI and CISA said that "any attempts by cyber actors to compromise election infrastructure are unlikely to result in large-scale disruptions or prevent voting," similarly to how it had no impact on previous elections.
"Any attempts tracked by FBI and CISA have remained localized and were blocked or successfully mitigated with minimal or no disruption to election processes."
Cybersecurity workforce: The White House and the Office of the National Cyber Director (ONCD) are requesting advice on how the government should handle the current cybersecurity workforce shortage, currently estimated at around 700,000 empty jobs. The Biden administration said it's looking for recommendations "as to how the Federal government can further lead, assist, or encourage other key stakeholders in government, industry, non-profits, and academia to advance progress in cyber training, education, or workforce development—including ways that expand diversity, equity, inclusion, and accessibility."
Sponsor section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
Cybercrime and threat intel
BEC money laundered sentenced: A US judge sentenced a Georgia man to 25 years in prison this week for laundering more than $9.5 million on behalf of cybercrime gangs. The man, named Elvis Eghosa Ogiekpolor, set up at least 50 bank accounts through which he received stolen funds from romance and business email compromise (BEC) scams.
Netwalker affiliate sentenced in the US: In addition, after receiving a seven-year prison sentence in Canada, Sebastien Vachon-Desjardins, a Canadian national who worked as an affiliate for the Netwalker ransomware operation, received an additional 20 years in prison in the US.
OnionPoison: Kaspersky researchers said they identified a campaign that distributed spyware-laced versions of the Tor Browsers via a popular Chinese YouTube channel. Named OnionPoison, the spyware collected data such as browsing history, social networking account IDsm and Wi-Fi network identifiers, but did not bother to collect more sensitive information such as user passwords, cookies, or wallet information.
OTP bypass bots: CloudSEK researchers said they detected cybercriminals advertising a new automated service called Apollo that can bypass one-time passcode (OTP) protections on online accounts. While several bots like these exist already, such as the Generaly OTP Bot, this one is particularly intriguing because it can also spoof calls on behalf of any company using Google Voice to trick victims into giving away their OTP code.
Attack Manager: In addition, the same CloudSEK team said they spotted a new DDoS-for-hire service called AttackManager, also advertised on several underground cybercrime forums. The service appears to have been set up in August and has yet to garner any substantial following.
Water Labbu: In a very interesting report from Trend Micro, the company's researchers said they uncovered a new threat actor they named Water Labbu that hacks into vulnerable cryptocurrency scam sites to replace the scammers' wallet addresses with their own, effectively stealing from other thieves.
Malicious PyPI package: Snyk said they discovered a new malicious PyPI library named Raw-Tool that, during its installation, executes unknown binary files and reaches out to a suspicious domain.
Nigerian BEC magic: We know that Nigerian BEC groups are superstitious and often ask for help from shamans, but this is something else altogether.
Are your #scams not working as well as you would like? You might be washing with the wrong soap. Apparently you can buy "cashout soap" and wash with it and then you will have a much better time stealing money. Who knew?
— GarWarner (@GarWarner) 6:49 PM ∙ Oct 3, 2022
#NigerianMagic #BlessTheScammers ???
New BlackByte ransomware tactic: The Sophos research team published a technical report on Tuesday describing a new technique employed by the BlackByte ransomware. Researchers say the group now abuses a vulnerability in the Rtcore64.sys driver to remove kernel callbacks for EDR software and limit their visibility. Rtcore64.sys is a component of MSI Afterburner, an MSI app for overclocking graphics cards.
Chinese ransomware group: In a report published on Tuesday, security firm Sygnia said it linked the Cheerscrypt and Night Sky ransomware strains to Emperor Dragonfly, a China-based threat actor.
"Emperor Dragonfly – also known as DEV-0401, and BRONZE STARLIGHT – is a Chinese ransomware group that started operating in mid-2021. Unlike other ransomware groups, Emperor Dragonfly does not operate in an affiliate model and refrain from purchasing initial access from other threat actors. Instead, they manage all stages of the attack lifecycle on their own. The group often rebrand their ransomware payloads, which helps them stay under the radar and avoid sanctions – as they have the appearance of being several, smaller ransomware groups."
NRA hacktivists: KyivPost has a profile on the National Republican Army (NRA), a hacktivist group that claims to be made up of Russian citizens looking the overthrow the Putin Government, a-la the Cyber Partisans group in Belarus. The group's latest action includes ransoming Unisoftware, a software service provider for Russia's Federal Tax Service, the Russian Ministry of Finance, and the Central Bank of Russia.
Secureworks threat landscape: Secureworks published on Tuesday its report on the 2022 threat landscape. Among the report's findings:
- Dwell time for ransomware gangs has gone down to 11 days this year, from 22 days last year.
- The loader landscape is evolving, and there's evidence of close collaboration between the groups operating different loaders. There is also a shift towards lightweight, disposable loaders in place of complex botnets like TrickBot or Emotet.
- Compromise of unpatched internet-facing infrastructure has overtaken credentials-based attacks as the primary initial attack vector (IAV) and was the start for 52% of ransomware incidents over the past year.
- Accelerated use of Infostealers as a means of enabling ransomware operations
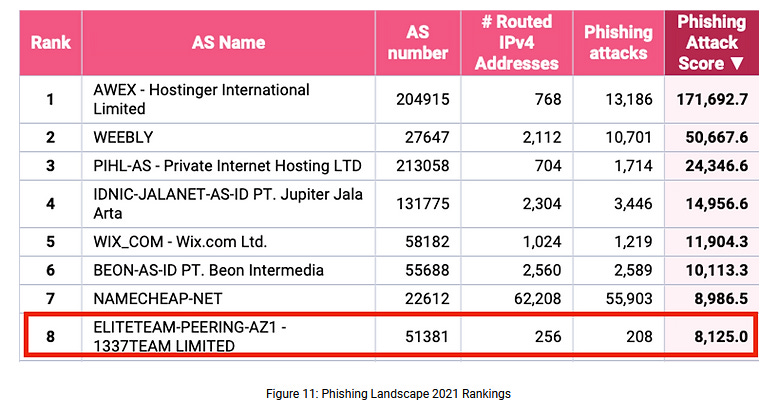
ELITETEAM: The excellent researchers from Team Cymru published a report last week on the infrastructure of ELITETEAM, a bulletproof hosting provider registered in Seychelles that has historically hosted quite a large number of malicious campaigns. Team Cymru reported that the hosting provider seems to run on different clusters, each dedicated to various operations, like hosting traffic distribution systems (TDS), banking trojans, ransomware, and crypto-mining botnets.
All the data and information we have researched points to ELITETEAM being Russian / Russian-speaking, operating behind a shell organization in Seychelles. We have reason to believe that Datahouse, RU is connected to ELITETEAM and worthy of further investigation.
Malware technical reports
Bumblebee: Since this spring, Bumblebee has been one of the most active malware strains, and several security firms have covered it in reports (IBM X-Force, Fox-IT, Proofpoint, Sekoia, Cybereason, Symantec, OALABS). Here's Check Point report on it.
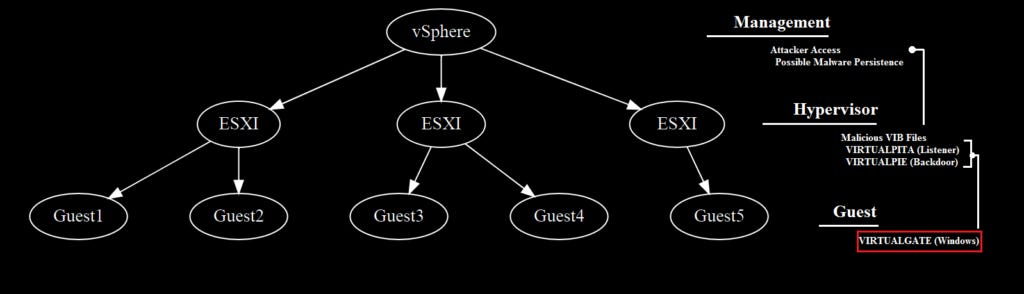
VirtualGate: Researchers from Norfolk Security have additional analysis on VirtualGate, a malware strain used by a Chinese threat actor to backdoor guest Windows operating systems running on top of VMWare ESXi hypervisors. The malware was first detailed in a Mandiant report last week, along with VirtualPie and VirtualPita, two pieces of malware deployed at the hypervisor level, through which VirtualGate is deployed.
MafiaWare666 ransomware: Avast released a free decrypter for the MafiaWare666 ransomware to allow victims to recover their files without paying a ransom.
MedusaLocker: CloudSEK researchers have a technical report out on the MedusaLocker ransomware, the same on which CISA also published a malware report back in June.
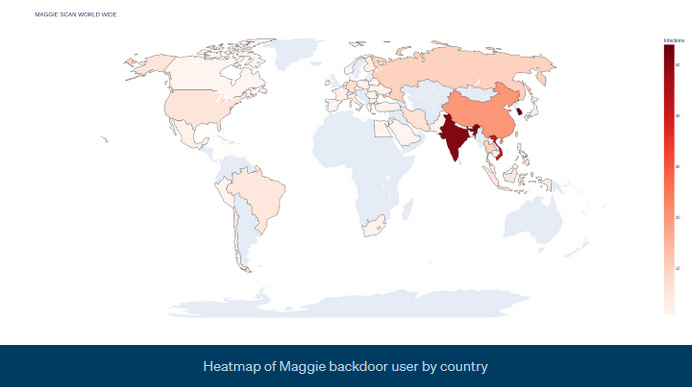
Maggie backdoor: German security firm DCSO said it found a new backdoor malware strain named Maggie that's been infecting MSSQL databases across the internet. Besides providing attackers access to the compromised servers, Maggie can also be used as a proxy to relay malicious traffic and launch brute-force attacks against other MSSQL systems. According to DCSO, the vast majority of infected servers are located in South Korea, India, Vietnam, and China.
APTs and cyber-espionage
DeftTorero: Kaspersky researchers have published a report on DeftTorero (aka Lebanese Cedar, Volatile Cedar), an advanced persistent threat group that was initially spotted in 2015 but about which very few have been reported in recent years. Kaspersky's research covers DefttTorero attacks that took place between late 2019 and mid-2021, during which the company's experts say the group abandoned their old malware strains and shifted to fileless/LOLBINS techniques and the use of publicly-available offensive tools.
"Based on our telemetry, the indicators of the intrusions we assessed between late 2019 and mid-2021 are similar to the usual DeftTorero victimology, with a clear focus on Middle Eastern countries such as Egypt, Jordan, Kuwait, Lebanon, Saudi Arabia, Turkey and the United Arab Emirates. The targeted web servers occasionally host multiple websites belonging to different industry verticals such as Corporate, Education, Government, Military, Media, and Telcos. This presents the threat actor with the opportunity to pivot to other victims of interest."
Earth Aughisky: Trend Micro has published an overview report on how the malware portfolio of the Earth Aughisky (Taidoor) APT has changed over the years.
"Our research paper, "The Rise of Earth Aughisky: Tracking the Campaigns Taidoor Started," lists all the malware attributed to the group, the connections of these malware families and tools with other APT groups, and the latest updates in illicit activities potentially connected to real-world changes."
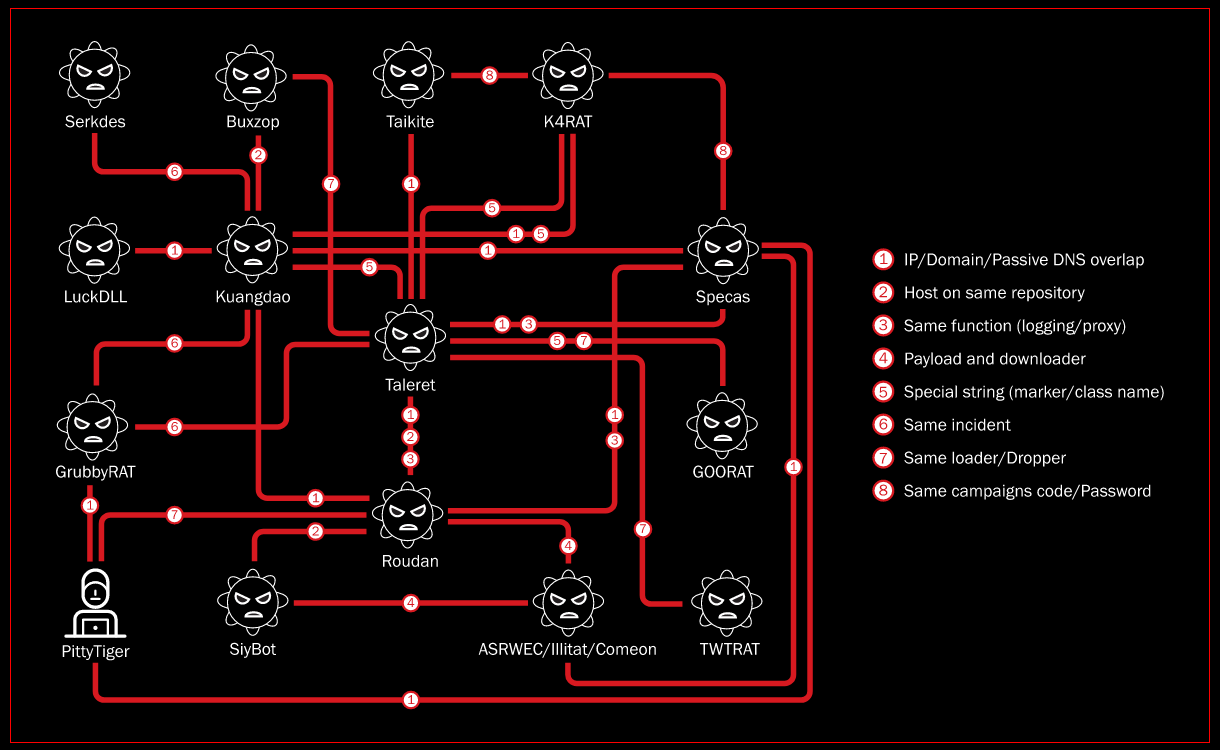
NSA, CISA, FBI advisory: The NSA, CISA, and the FBI issued a joint security advisory on Tuesday, warning about APT attacks against US Defense Industrial Base organizations. The advisory specifically mentioned the attacker's propensity to use an open-source tool named Impacket to gain an initial foothold inside orgs and the use of a private tool called CovalentStealer to exfiltrate data from the victim's systems. Impacket, in particular, is a very popular tool with attackers and was ranked #1 in Red Canary's threat landscape report in June as one of the most widely and most commonly detected tools that month. More from Katie Nickels, Director of Intelligence at Red Canary:
"Adversaries favor Impacket because it allows them to conduct various actions like retrieving credentials, issuing commands, moving laterally, and delivering additional malware onto systems. The good news is that Impacket can be detected with endpoint and network visibility. However, while Impacket is fairly easy to detect, it can be challenging to determine if the activity is malicious or benign without additional context and understanding of what is normal in an environment. Approximately one third of the Impacket detections we saw in 2021 were from confirmed testing. If an organization's infosec team detects a malicious instance of Impacket, they should consider isolating the endpoint because there may be an active adversary in their environment. By detecting the use of Impacket early in an intrusion, defenders have a good chance at stopping that intrusion and preventing exfiltration of sensitive data."
TA453 attack: Researchers from CyFirma have published a breakdown of a social engineering attack carried out by the Iranian group TA453.
APT naming schemes: Security researcher Arkbird has put together a list with all the APT naming schemes used by various infosec entities, from CERTs to security firms.
Vulnerabilities and bug bounty
Packagist vulnerability: SonarSource researchers said they found a vulnerability in Packagist, the repository for the PHP Composer package installer, which could have allowed them to hijack the service's backend and mount supply chain attacks against the service's users. SonarSource said Packagist fixed the reported vulnerability "within hours" after their report.
Ranger stored passwords in plaintext: A now-patched version of Rancher, an open source Kubernetes management tool, stored sensitive values in plaintext, a pair of software developers have discovered. Exploitation could have enabled attackers to gain privileged access to various Rancher-owned Kubernetes objects, The Daily Swig reported.
Drupal security updates: ...are out and are here.
Infosec industry
Hacking Google series: The six episodes of the Hacking Google series are available in this YouTube playlist. They cover the five major Google security teams and the Project Aurora hack that led to their creation.
NSA internship: The US NSA has listed summer internship positions for next year if you're interested.
It's never too early to make summer plans!
— Rob Joyce (@NSA_CSDirector) 6:58 PM ∙ Sep 8, 2022
@NSACyber 2023 Summer Internships are open:
#CompSci - 1191813
#Cybersecurity - 1191816
#Engineering - 1191817
Apply at:
intelligencecareers.gov/nsa
Use the numbers above - find your passion. Hurry, applications close on Halloween!
New tool—Dissect: Researchers from NCC's Fox-IT team have open-sourced a new project called Dissect, a modular Python framework for enterprise-scale incident response and investigations.
New tool—Freeze: Cybersecurity firm Optiv open-sourced last week a new project called Freeze that can be used to bypass EDR solutions.
EvilGoPhish update: The EvilGoPhish phishing toolkit has been updated to support Twilio-based SMS-based phishing campaigns. Hooray for the red-teamers and cybercrime gangs, I guess!
MITRE ATT&CK update: The MITRE ATT&CK framework has been updated with support for Campaigns.
Sysmon 14.1 is out: Complete with a new feature named FileBlockShredding that prevents wiping tools from corrupting and deleting files. The feature was announced last month at the LABScon security conference as a way to protect Ukrainian systems against Russian data wipers.
The new Sysmon I showed off at @labscon_io last week with file-shred blocking is out, as well as a Coreinfo update that reports CPU-CPU latency:
— Mark Russinovich (@markrussinovich) 9:32 PM ∙ Sep 29, 2022
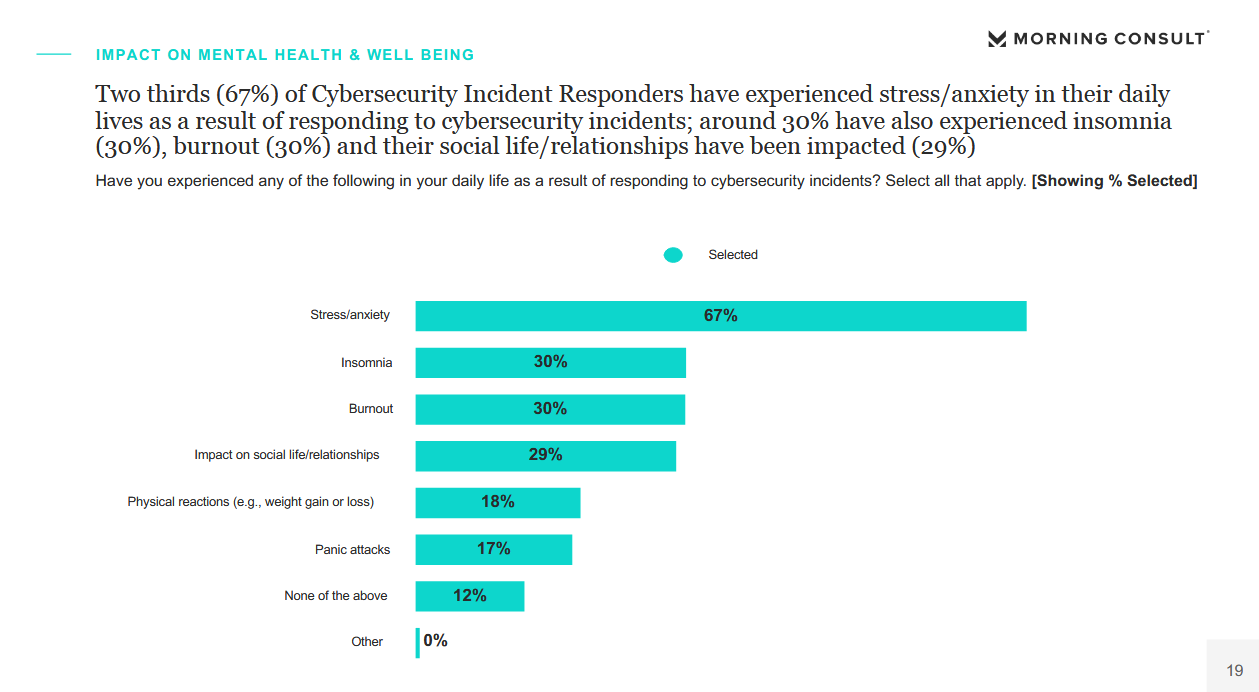
Stressed out: A survey conducted by IBM of more than 1,100 IR teams found that two-thirds of incident responders are "experiencing stress or anxiety in their daily lives" due to the high demands of their cybersecurity engagements, including dealing with two or more intrusions at the same time. Respondents also cited experiencing insomnia, burnout, and impact on their social life or personal relationships as some of the side-effects of their demanding jobs. See full results and charts here.