Risky Biz News: Canada's tax revenue agency tries to ToS itself out of hacking liability
In other news: DoppelPaymer ransomware gang members identified; Germany ponders Huawei & ZTE 5G ban; Israel blames Iran for recent ransomware attack.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Today's newsletter intro was written by Tanya Janca, CEO and Founder of We Hack Purple.
The Canada Revenue Agency (CRA), the tax department of Canada, recently updated its terms and conditions to force taxpayers to agree that CRA is not liable if their personal information is stolen while using the My Account online service portal—which, ironically, all Canadians must use when doing their taxes and/or running their business.
The CRA's terms of use assert the agency is not liable because they have "taken all reasonable steps to ensure the security of this Web site".
Excerpt from the CRA terms statement:
"10. The Canada Revenue Agency has taken all reasonable steps to ensure the security of this Web site. We have used sophisticated encryption technology and incorporated other procedures to protect your personal information at all times. However, the Internet is a public network and there is the remote possibility of data security violations. In the event of such occurrences, the Canada Revenue Agency is not responsible for any damages you may experience as a result."
Unfortunately, that is not true. After reviewing the HTTP responses from the CRA My Account login page, it's clear the agency has not configured even some of the most basic security features. For example, security protections for their cookies are not configured, nor are all the recommended security headers used.
Not only is that not "all reasonable steps," but the CRA is missing the very basics for securing online web applications.
The terms of use also state that users are not allowed to use "any script, robot, spider, Web crawler, screen scraper, automated query program or other automated device or any manual process to monitor or copy the content contained in any online services."
Looking at the HTTP response headers using web browser developer tools doesn't breach the terms of services, but the CRA must be well aware that internet users perform scans like this all the time.
And it's not the legitimate My Account users who are likely to be the culprits. Unfortunately for Canadians, threat actors don't read terms of use pages.
A statement like this doesn't protect anyone, except CRA, from being held responsible for failing to properly secure Canadian citizens' personal data.
The changes to the terms of service may be the result of numerous data breaches (see below) that have already occurred at the CRA (see below), as well as the result of a class action lawsuit filed against the agency last August.
- August 2020 - Statement from the Office of the Chief Information Officer of the Government of Canada on recent credential stuffing attacks
- September 2020 - Update from the Office of the Chief Information Officer of the Government of Canada on recent cyber attacks
- August 2020 - CRA shuts down online services after thousands of accounts breached in cyberattacks
- March 2021 - CRA locking 800K Canadian taxpayers out of accounts
The CRA offloading its responsibility for securing citizens' data via a benign ToS update is a worrisome development from the government agency that should be safeguarding their data in the first place.
The data that CRA holds on every single Canadian is more than enough to help threat actors steal their identity or decide who might be worth robbing or blackmailing.
If threat actors identify particular vulnerabilities in the CRA website, they could also erase or modify taxpayers' data, creating infinitely more terrifying scenarios.
Nation states, criminal organizations, and even political rivals would be very interested in obtaining the data that the CRA is entrusted with holding on behalf of the citizens of Canada.
You can view the CRA's new terms of use here.
Attempts to get the CRA to address its web security posture have been met with silence.
Update: they did not respond. I have sent physical letters and emails.
— Tanya Janca (@shehackspurple) 6:16 AM ∙ Mar 5, 2023
Breaches and hacks
Acer confirms hack: Taiwanese hardware vendor Acer has confirmed a security breach after a hacker began selling more than 160GB of data they stole from one of the company's servers. According to the seller, an individual going by the name of Kernelware, the stolen data includes details about the Acer BIOS, confidential presentations, product documentation, ROM, and other binary files. Acer says the files originated from a server for repair technicians.
Facebook's LLaMA leak: LLaMA (Large Language Model Meta AI), a collection of large language models developed internally at Meta, was leaked on 4chan last week, marking the first time when a major tech company's proprietary AI model has leaked in full. Prior to the leak, Meta, Facebook's parent company, had provided access to the LLaMA model to select researchers from the AI community. While the leaker hid their identity using the "llamanon" 4chan username, AnalyticsIndiaMag notes that the LLaMA torrent file contained a unique identifier that would, theoretically, allow Meta to track down who received and leaked the files. Motherboard reported that Meta did not deny or confirm the leak, nor has it taken any steps to have the torrent removed.
LaunchZone crypto-heist: The LaunchZone cryptocurrency portal announced this week a compensation plan for users who lost funds in a hack that took place at the end of February. At the time, the company lost $700,000 following an exploit against one of its contracts that drained around 80% of the funds from its liquidity pools.
Another DDoS attack hits Mastodon: Mastodon.social, today's largest Mastodon server, was hit by a massive DDoS attack on Monday, just as Twitter was dealing with a major outage after shooting itself in the foot. According to Jorge A. Caballero, major Mastodon instances getting DDoSed following major Twitter tech snafus is a thing these days. Caballero has an analysis of the attack in this Mastodon thread.
General tech and privacy
Sony's attack on Quad9: Sony Music has sued DNS provider Quad9 and is asking the court to force Quad9 to block DNS resolutions to domains that Sony believes are infringing on their copyrighted material.
"If Sony wins and Quad9 is forced to block access to the site, other companies can use this precedent to block sites they don't like, for example, for commercial or political motives."
Naming and shaming: In some weird gaming news, Battlestate Games, the Russian gaming company behind the hugely successful Escape from Tarkov exfil shooter, has decided that instead of silently banning cheaters, it will name and shame them instead. Since the end of February, the company has been publishing spreadsheets with the in-game nicknames of players it caught cheating. So far, the company has named and shamed more than 6,700 players. [More in TechCrunch]
Brave blocks Google SSO: Starting with v1.51, the Brave browser will put any Google SSO (Google Sign-In) requests under a permission prompt. Brave says that blocking Google SSO will improve user privacy by blocking Google from using the feature to track users.
Government, politics, and policy
Irony is dead: Zhou Hongyi, co-founder, chairman, and CEO of Qihoo 360, as well as a political advisor for the Chinese government, says in a China Daily interview that "cyberattacks launched by hackers backed by foreign governments have become the biggest threat to China's cybersecurity."
US officials warn of growing Chinese influence ops: US government officials say that China is amplifying its information operations on social media networks to a level that now rivals Russia, although less sophisticated.
"US officials and outside experts cite recent examples of China-linked actors generating false news reports with artificial intelligence and posting large volumes of denigrating social media posts. While many of the discovered efforts are amateurish, experts think they signal an apparent willingness from Beijing to try more influence campaigns as part of a broader embrace of covert operations, according to two people familiar with the matter who spoke on condition of anonymity to discuss sensitive intelligence."
Incoming German Huawei ban: The German government is planning to ban the use of Huawei and ZTE equipment from its national 5G telecommunications network, according to reports in German media. German officials cited fears that Huawei and ZTE equipment could be used for Chinese espionage or sabotage. Previously, the German government gave the go-ahead for Chinese equipment to be used for its 5G network, but the recent Russian invasion of Ukraine and Russia's attempt to blackmail Germany from aiding Ukraine through its NordStream natural gas pipeline led to a major change of thinking in Berlin. According to German media, telcos that previously installed 5G technology from the two vendors may be forced to rip and replace the equipment.
Israel blames Iran for ransomware attack: Israel has blamed Iranian hackers for a ransomware attack that crippled the IT network of the Technion research university last month. Officials with the Israel National Cyber Directorate say that a cyber-espionage group named MuddyWater breached the university and deployed a ransomware strain named DarkBit on its network. In February 2022, the US government formally linked the MuddyWater group to Iran's Ministry of Intelligence and Security.
Russia wants to ban IM and push-noty spam: FAS, Russia's anti-monopoly watchdog, has put forward legislation to ban the distribution of ads via instant messengers and push notifications without a user's explicit consent. According to TelecomDaily, the proposed law would eliminate the legal uncertainty around where IM and push notifications should be classified in terms of communications technologies and if previous consumer protection laws apply.
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy demonstrates the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
DoppelPaymer ransomware gang crackdown: Europol, the Dutch, German, and Ukrainian police have cracked down this week on core members of the DoppelPaymer ransomware gang. Two suspects were questioned in Germany and Ukraine, while German authorities issued international arrest warrants for three other suspects, Igor Olegovich Turashev, Igor Garshin, and Irina Zemlianikina, all three "with connections to Russia" and considered "core members" of the DoppelPaymer gang. The DoppelPaymer crew started operations in 2019 as a spin-off project from the BitPaymer, a ransomware strain created by the infamous EvilCorp cybercrime cartel. The ransomware got on everyone's radar after an attack on the Duesseldorf University Hospital was believed to have indirectly caused the first ransomware-linked death of a patient, who had to be redirected to a nearby hospital 30km away. Since then, the DoppelPaymer gang tried to rebrand as the Grief ransomware service, but the intensity of attacks and payments fell after the EvilCorp was sanctioned by the US Treasury, and victims began avoiding paying ransoms to gangs even remotely connected to EvilCorp in an attempt to avoid breaking international sanctions. The gang is believed to have carried out more than 600 intrusions and earned more than €40 million from ransom payments.

New ransomware strains: Equinix's William Thomas has spotted two new ransomware strains—named Mario ESXI and DarkAngelSteam, both based on the leaked source code of the now-defunct Babuk ransomware. According to Thomas, both appear to be rebrands of the ransomware that hit ADATA last year and the DarkAngels strain spotted by Uptycs. The DarkAngels gang has been recently linked to an incident at Andrade Gutierrez, a major Brazilian construction conglomerate that operates across 11 countries. On top of this, Fortinet has spotted two new ransomware strains named Sirattacker and ALC, while Broadcom has spotted attacks with a new ransomware strain CMLocker.
Another low for ransomware gangs: The ALPHV (BlackCat) ransomware gang has published photos of topless female breast cancer patients as part of its extortion of Lehigh Valley Health Network, a Pennsylvania-based healthcare network.
AresLoader: Flashpoint covers AresLoader, a new malware loader currently advertised on Russian-speaking cybercrime forums.
Malicious Chrome extension: Google has removed "Get cookies.txt" from the official Chrome Web Store. The extension allowed users to export the content of their cookie files in the old Netscape browser cookie format and had almost 160,000 users before it was removed from the Web Store. Issues around the extension were brought to light in early January when a Reddit user discovered that the extension was tracking users by collecting user and browsing data and uploading it to a remote server. The extension was removed this week after a subsequent report over the weekend found that the extension was also stealing users' cookie files, which could have allowed the extension's author to hijack user accounts.
DFIR year in review: The DFIR Report team has published its year-in-review report for 2022. According to the infosec collab group, phishing remained the top initial entry vector last year, accounting for 69% of all tracked cases. In terms of preferred persistence methods, the creation of scheduled tasks and the creation of local administrative accounts were the most commonly observed techniques. For lateral movement, threat actors preferred RDP and SMB shares, both accounting for 41% each. More stats in the report.
Malware technical reports
Nexus C2 infra: Security researcher Rohit Bansal has identified the command and control infrastructure of a new Android banking trojan named Nexus. The malware is currently being advertised for sale on Telegram cybercrime channels.
Android banking trojans: And since we're on the topic of Android banking trojans, Equinix's William Thomas has a spreadsheet of all the Android banking trojan strains in case you need to keep track of them.
Second debunk: Over the past weekend, Łukasz Siewierski, an Android malware reverse engineer at Google, published a debunk of a paper from a US security researcher named Jonathan Scott in which Scott claimed that Citizen's Lab research on the use of NSO Group spyware by Moroccan authorities was wrong. Now, Runa Sandvik of GranittHQ, has published a second debunk of the same Scott paper, calling out several inaccuracies.
Remcos RAT campaign: SentinelOne has a report out on a DBatLoader campaign dropping Remcos RAT on the systems of Eastern European organizations and enterprises.
Brute Ratel analysis: Security researcher Boymoder RE has published an analysis of Brute Ratel, a red-team tool very popular these days with APTs and cybercrimz.
“Brute Ratel is a so-called "red team" malware created by some Twitter malware developer who claims to be an ex-EDR engineer. Right now, it is most known for being abused by various ransomware gangs and the author lying about that despite extensive proof otherwise. The reverse engineering project was instigated by these reports of abuse by RaaS. More specifically, abuse by Blackcat / ALPHV affiliates were reported by Sophos in private circles on July 1st 2022.”
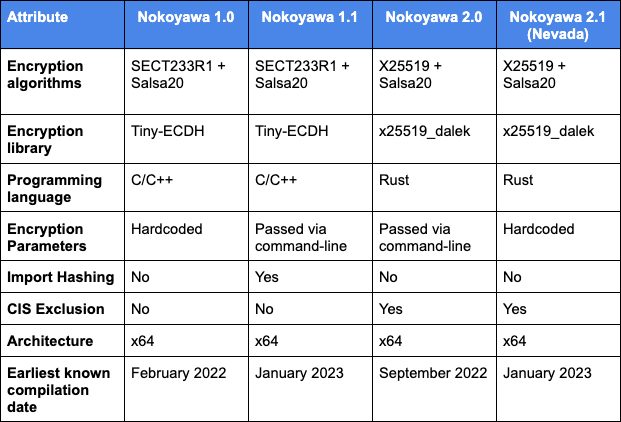
Nevada and Nokoyawa connections: Earlier this year, reports from several cybersecurity firms shed light on a new Ransomware-as-a-Service operation named Nevada that launched in December of 2022. Nevada operators claimed their ransomware could encrypt Windows, Linux, and ESXi-based systems and gained a lot of attention by allowing their affiliates to keep as much as 90% from successful extortions. However, in a report published this week, Zscaler says it analyzed Nevada's code and found numerous clues and similarities to suggest that Nevada is just a new version (v2.1) of the older Nokoyawa ransomware, and a possible attempt from the older gang to rebrand, a common tactic used by many groups to muddle their tracks and confuse security researchers and law enforcement investigations.
SYS01stealer: Morphisec researchers are tracking a new infostealer strain named SYS01stealer. The malware was first spotted in attacks in November of last year. Morphisec says its operators use Google ads and fake Facebook profiles that promote things like games, adult content, and cracked software in order to trick victims into infecting themselves. SYS01stealer is designed to steal login data, cookies, and is specifically looking for information about Facebook business accounts.
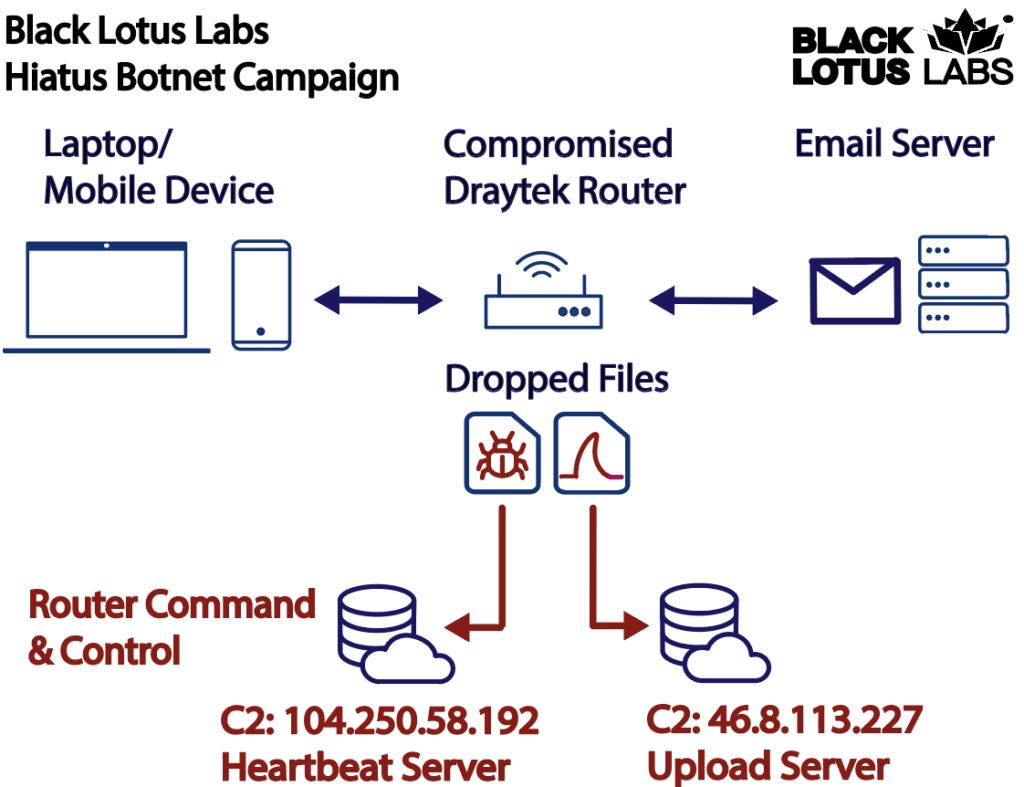
HiatusRAT: Lumen's Black Lotus Labs has identified a new campaign that targets business-grade routers in order to convert them into proxies that relay malicious traffic. Lumen says the campaign has been underway since at least July 2022, compromised 100 routers so far, and most of the infected devices are end-of-life DrayTek Vigor 2960 and 3900 models. Once a device is compromised, Lumen says the attacker installs a never-before-seen remote access trojan named HiatusRAT, through which the attackers control the router and convert it into a SOCKS5 proxy. In addition, the attacker also installs a version of the tcpdump utility through which they monitor email and file-transfer traffic originating from the router's internal network.
Sponsor Section
RunZero is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
APTs and cyber-espionage
Kimsuky tactics: Kaspersky's Seongsu Park has a report on various tactics used by Kimsuky, a North Korean APT group.
APT-C-56 (Transparent Tribe): Cybersecurity firms ESET and Qihoo 360 have published reports on Tuesday about ongoing cyber-espionage campaigns carried out by a suspected Pakistan-based threat actor they are tracking as Transparent Tribe and APT-C-56. ESET says it saw the group target Indian and Pakistani citizens with a version of the Android CapraRAT backdoor that was hidden inside two chat apps called MeetsApp and MeetUp. On the other hand, Qihoo 360's report covers two of the group's newer tools, namely the RlmRat Android remote access trojan and the Poseidon framework for targeting Linux systems.
Sharp Panda: Check Point has posted an update on recent attacks carried out by Sharp Panda, a suspected Chinese APT group. The company previously covered the group in 2021. Check Point says it has seen the group deploy new versions of the SoulSearcher loader, which eventually loads the Soul modular framework.
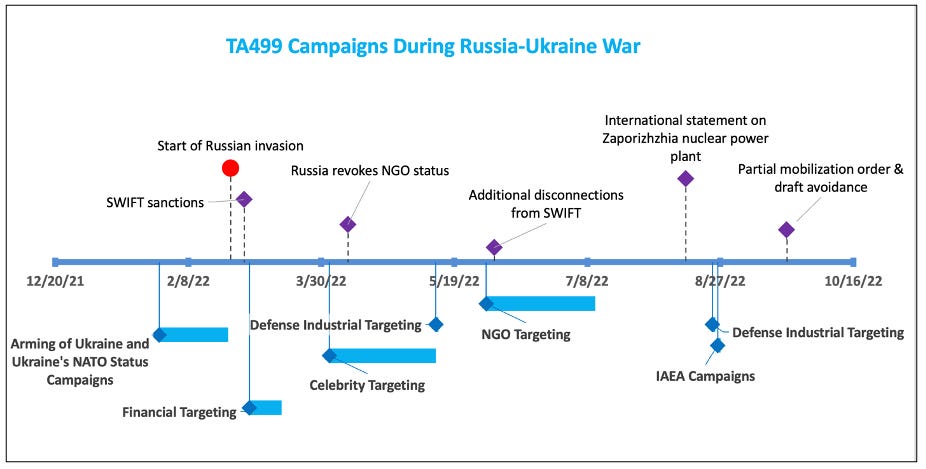
TA499: Proofpoint says that as part of a weird propaganda effort, a Russian threat actor it is tracking as TA499 has spent the past year contacting high-profile politicians, celebrities, and famous CEOs. Proofpoint says the group's main task appears to be to lure unsuspecting victims into phone or video calls discussing controversial topics related to their support of Ukraine. These videos are then edited to discredit the subject and their support for Ukraine and uploaded on YouTube and RuTube. Proofpoint believes the campaign is part of a Russian internal propaganda effort to support its invasion of Ukraine and denigrate critics of Vladimir Putin. Researchers say that in most of the group's operations, TA499 uses email to reach out to victims, typically posing as embassy employees, Ukrainian government officials, and members of Alexey Navalny's staff.
"Conversations with TA499 typically begin serious and allow the target to voluntarily say as much information as possible. Once the target begins asking questions, the actor mirrors the target's replies to keep the conversation going. Some of the 2021 videos with the threat actor have the Leonid Volkov impersonator asking for financial support and appear to encourage the target into voicing particular obligations and efforts in tandem with the Russian opposition led by Navalny. Once the target makes a statement on the matter, the video devolves into antics, attempting to catch the target in embarrassing comments or acts. The recordings are then edited for emphasis and placed on YouTube and Twitter for Russian and English-speaking audiences."
Vulnerabilities and bug bounty
Android security updates: ...for March 2023 are out!
Word RCE PoC: Security researcher Joshua J. Drake has published a write-up and PoC for CVE-2023-21716, a remote code execution bug in Microsoft Word. The bug was patched in last month's Patch Tuesday.
Polynonce attack: Researchers from Kudelski Security have discovered a novel attack on the ECDSA cryptographic algorithm. Named Polynonce, the attack can be used to extract the original signing key from ECDSA signatures generated with weak pseudo-random number generators (PRNGs). The researchers proved their attack by recovering private keys for hundreds Bitcoin addresses that used weak PRNGs. They also say the attack can be used to recover signing keys for Ethereum wallets but also TLS certificates.
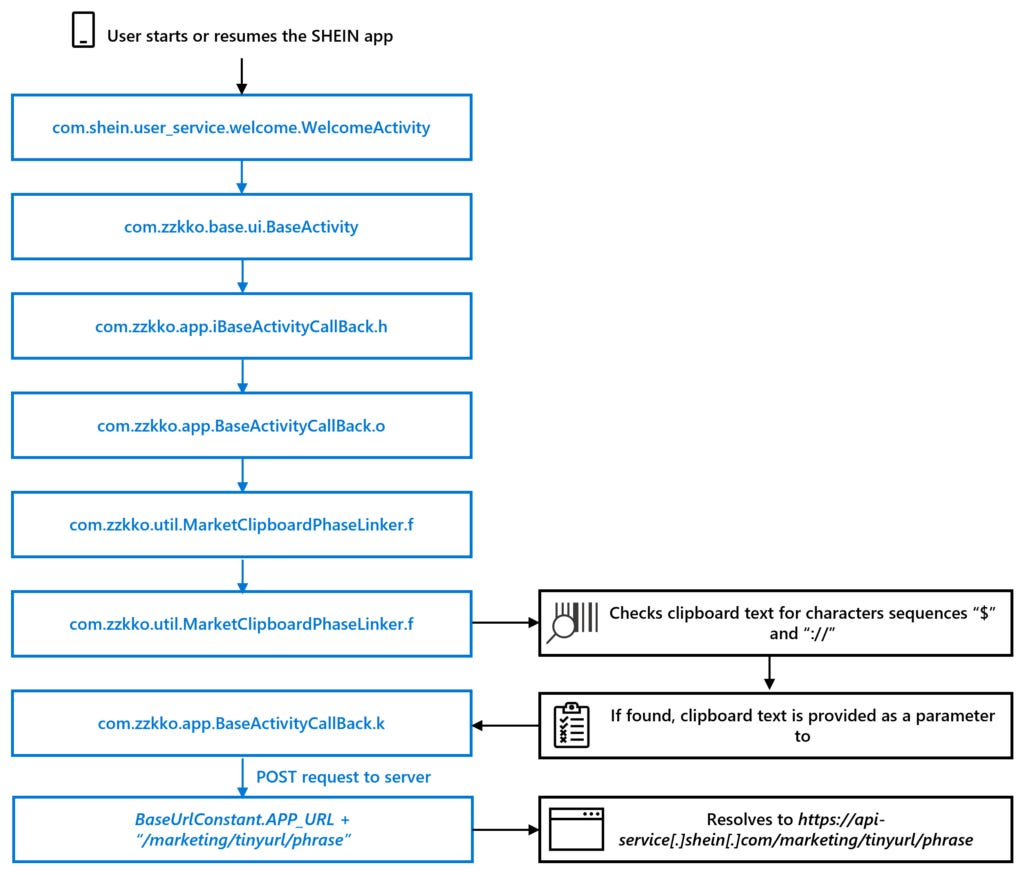
Clipboard data exfiltration: Microsoft's security team discovered that the official Android app for SHEIN, one of the world's largest fashion retailers, contained a hidden behavior that would "periodically read the contents of the Android device clipboard and, if a particular pattern was present, sent the contents of the clipboard to a remote server." According to Microsoft, any clipboard content that appeared to be an URL or contained the dollar sign ($) would be sent to one of SHEIN's API servers. Microsoft says it notified Google of the app's malicious behavior, and Google worked with SHEIN to have the clipboard data collection feature removed from the app in May of last year.
Infosec industry
Municipal CISO challenges: Infosec journalist and the author of the Metacurity newsletter Cynthia Brumfield has a column out on the challenges that municipal CISOs across the US are facing in light of the rising number of cyberattacks. These include more sophisticated threats, increasing regulations, and the constant lack of funding.
Blockchain security newsletter: Time to recommend another good cybersecurity newsletter. This time it's Fairyproof's newsletter, which tracks hacks and cybersecurity-related developments across the blockchain and cryptocurrency community.
Tool update: Fortra, formerly HelpSystems, has released Cobalt Strike 4.8. Defenders might wanna take a look and prepare for a hurtin'.
Layoffs: Dozens from Microsoft's security teams have had their positions "eliminated" as part of the tech giant's recent layoffs.