Risky Biz News: BreachForums shuts down for good fearing law enforcement compromise
In other news: Kremlin staff told to dump their iPhones; Greece spied on Meta employee; cybersecurity spending to reach $219 billion this year.

This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
BreachForums, an underground cybercrime forum that made a reputation for being the go-to place for buying and selling hacked personal data, is officially no more.
The site has closed down on its own, but the decision to shutter all operations for good comes after a very turbulent four days.
Last Friday, the FBI detained the forum's main administrator—a New York man named Conor Brian Fitzpatrick, aka Pompompurin—after the personal data of US lawmakers and their staff was posted for sale on the site.
On the same day, an individual named Baphomet took over the forum. In a message posted on the site, Baphomet promised at the time to move the forum to new infrastructure in order to protect the identities of its users from any potential law enforcement seizure.
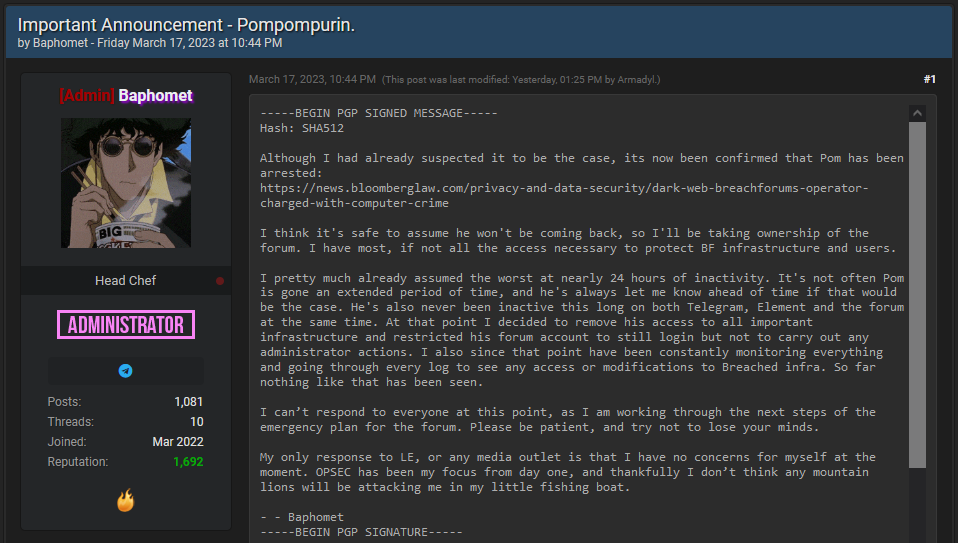
Both the clear web and dark web versions of BreachForums went down on Monday, and it was initially believed the downtime was most likely caused by Baphomet's attempts to move the site to new servers.
This was, however, not the case. In a follow-up message posted on Tuesday, Baphomet said BreachForums would shut down for good because the site "is not safe anymore."
Baphomet says that while migrating the site, they found evidence that "the glowies" (aka government agents) gained access to Pompompurin's machine and had accessed some CDN servers that were part of the BreachForums backend.
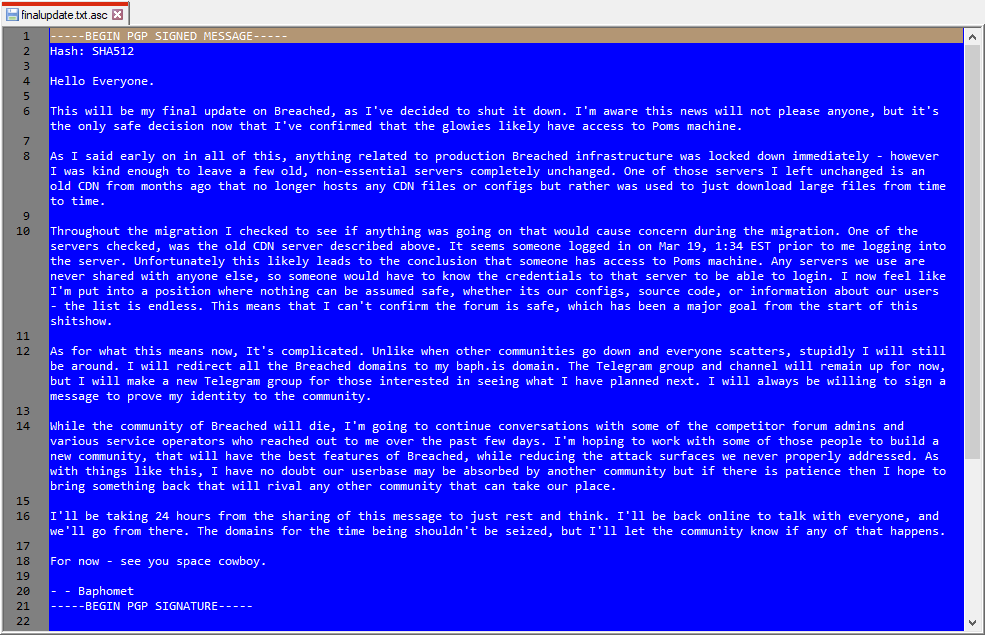

Baphomet's explanation for the decision to shut down BreachForums is most likely accurate, as law enforcement officials have most likely seized computer equipment from Pompompurin's house during the arrest.
However, the downfall of BreachForums does not mean the end of the hacked data trading ecosystem, which has previously survived multiple similar takedowns.
BreachForums itself is a reincarnation of another forum named RaidForum, which was seized and taken down by EU and US law enforcement in April last year. In fact, BreachForums is an almost pixel-perfect clone of the original RaidForums, which is why it became so popular so quickly, ensuring most RaidForum users migrated over.
While Baphomet touted possible plans for a new platform where the BreachForums userbase can migrate, they expect the community to split and get absorbed by other existing cybercrime platforms.
Recorded Future CTI researcher Alexander Leslie shares Baphomet's assessment.
"Most of the low-tier stuff — combolists, leads, log dumps, etc. — will probably be redirected to other English-language forums. Think Cracked, Nulled, etc. The initial access, database leak, and ransomware communities will likely go to XSS and Exploit," Leslie wrote in a long thread on the aftermath of BreachForums' demise.
"The threat landscape will continue to evolve, despite the closure of BreachForums," he added.
Breaches and hacks
Ferrari extortion: Sports car maker Ferrari says a hacker recently contacted its Italian branch and demanded a ransom payment in regard to certain customer contact details they appear to have obtained. The company says it contacted law enforcement and will not pay the ransom as a matter of policy. A source with knowledge of the incident told DataBreaches.net this is a new incident and not related to a ransomware attack carried out by the RansomExx gang in October of last year.
Latitude hack: Australian financial services company Latitude says the personal information of almost 330,000 customers was stolen in a security breach. The company says the breach took place after a threat actor obtained a Latitude employee's login credentials, which they used to log into its network and steal data stored on the network of two service providers. Stolen information includes identification documents, with the bulk being copies of customer driver's licenses. [Company update #1/PDF and #2/PDF]
Euler hack linked to NK: Blockchain analysis company Chainalysis says it spotted $175,000 (100 ETH) from the Euler Finance hack move to an address that previously received funds stolen from the Axie Infinity Ronin Bridge incident, a hack formally linked to North Korea's Lazarus hacking group. Despite the discovery, Chainalysis says it was not ready to link the Euler exploit to Lazarus operators, as this could be a "misdirection by another hacking group" and because only a very tiny portion of the $197 million stolen funds was transferred there.
Bitcoin ATMs hacked (again): Panama-based company General Bytes says that a threat actor discovered a zero-day vulnerability in its Crypto Application Server (CAS), a cloud and on-premise solution for running Bitcoin ATMs. The company says the attacker used the zero-day to steal funds stored in Bitcoin ATMs across the world, including from its cloud service, where it hosts ATMs for customers. The losses are estimated in the realm of millions of US dollars, according to a list of addresses where funds were exfiltrated. General Bytes released security updates to patch the zero-day. It also announced it was shutting down its cloud service because it was "theoretically (and practically) impossible to secure" it from "bad actors." This incident is the second time the company's ATMs were compromised after a similar wave of hacks last August.
Wagner Leaks: A consortium of investigative journalists have published an analysis of the Wagner Leaks, a collection of files that a group of unknown hackers has stolen from a consortium of companies owned by Russian oligarch Yevgeny Prigozhin. The leaks, compiled after hackers spent months inside the compromised networks, include details about the personnel and IT infrastructure of companies like the Wagner Group private military corps, the Internet Research Agency (aka the Lakhta Project) troll factory, and the Concord group of consulting companies. The leaked files include salary structures, recruiting documents, job tasking, lists of Telegram channels operated by the companies, hardware and software inventories, the structure of internal software networks, web hosting details, and more. [Reports are available in both English and Russian]

General tech and privacy
Edge is getting a built-in cryptocurrency wallet: Microsoft is testing a cryptocurrency wallet inside its Edge web browser. A similar feature is included in other browsers like Brave and Opera.
PfP discontinued: The PfP (Pain-free Passwords) password manager has been discontinued after seven years.
Java 20 is out: The OpenJDK project has released v20 of the Java SE Platform.
BBC bans TikTok: If TikTok getting banned on government devices across the western world wasn't bad enough, now even the BBC is telling staff to remove the app from work phones. Ouch!
Government, politics, and policy
Russian presidential staff to dump iPhones: The Kremlin's security team has instructed presidential staff to dump their iPhones by April 1. Kommersant reports that employees were told to get an Android device, either from a Chinese vendor or one running Rostelecom's Aurora OS. Kremlin officials cited security considerations for their decision, claiming iPhones were "more susceptible to hacking and espionage by Western experts compared to other smartphones."
Greece spied on Meta employee: Greece's national intelligence agency is believed to have hacked the mobile phone of a Meta employee as part of a year-long wiretapping operation. According to the New York Times, the target was Artemis Seaford, a dual Greek and US citizen who worked from 2020 to the end of 2022 on Meta's security and trust team. Seaford says she first found out about the spying after a Greek newspaper published last November a list of names that were allegedly targeted with spyware by the Greek government. Seaford took her phone to researchers at Citizen Lab, who confirmed the device was infected with the Predator spyware around September 2021.
CADS: This FederalNewsNetwork report looks at CADS, CISA's new security platform that's currently planned to replace its EINSTEIN system.
IAM security guide: CISA and the NSA have published a best practices guide [PDF] for securing Identity and Access Management (IAM) systems.

Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
Phishing gang detained in RO&NL: Two Dutch nationals were detained in Romania, and another one was detained in the Dutch city of Enschede on charges of digital fraud. Dutch police say the group stole more than €1 million from more than 1,000 victims by phishing bank accounts. A fourth suspect was also questioned in Romania in relation to the scheme.
Malicious NuGet packages: JFrog security researchers have identified 13 malicious .NET libraries available through the official NuGet portal. The libraries leveraged a technique called typosquatting, trying to pass as legitimate packages. JFrog says the libraries contained code that would run a Powershell script to download and install a malicious executable and steal cryptocurrency wallet information. While most of the libraries had only a few tens of installations, a package named Coinbase.Core was downloaded more than 120,000 times.
Adobe ColdFusion exploitation: Rapid7 reports active exploitation of Adobe ColdFusion servers in "multiple customer environments." Some of the attacks took place as early as January 2023, and evidence suggests the attackers installed web shells on the compromised servers. Rapid7 did not link any of the attacks to a specific vulnerability CVE. There is a high chance the attacks were carried out with CVE-2023-26360, a ColdFusion vulnerability that Adobe patched last week and described as a zero-day.
Google removes Pinduoduo apps: Google has removed the official app of the Pinduoduo Chinese e-commerce giant from the official Play Store. All the company's apps were flagged as malware, and users who installed them received a warning via the Play Store app. The suspension comes after earlier this month, Chinese security researchers found malicious code inside the apps designed to exploit vulnerabilities, elevate privileges, modify system settings, adjust permissions, and even track users. Prior to being delisted, the app was downloaded more than 24 million times and had more than 11 million monthly active users.
Facebook phishing campaign: SilentPush has a report on a recent phishing campaign spreading via Facebook DMs.
Mid-sized business report: Huntress has released a report [PDF] detailing the state of cybersecurity in mid-sized businesses across the US and Canada. Below are some findings summarized:
- 61% of mid-sized businesses don't have a security team.
- 47% don't have an incident response plan.
- 27% have no cyber insurance coverage.
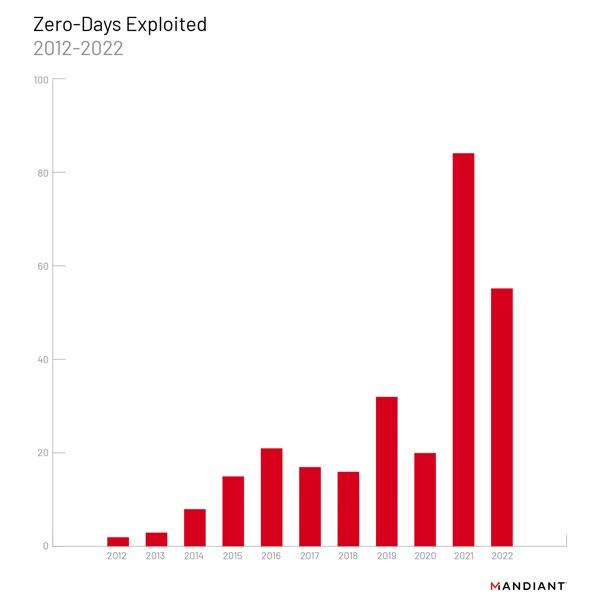
2022 zero-day report: Mandiant published its yearly report on zero-day exploitation. Below are some findings summarized:
- Mandiant says 55 zero-days were exploited last year.
- Chinese state-sponsored cyber espionage groups exploited more zero-days than other cyber espionage actors in 2022.
- Four zero-days were linked to financially-motivated threat actors.
- Three of these were used by ransomware gangs.
- Products from Microsoft, Google, and Apple made up the majority of zero-day vulnerabilities in 2022.
Malware technical reports
NAPLISTENER: Elastic's security team has a report out on NAPLISTENER, a network implant that works as an HTTP listener written in C#. Elastic says the malware was developed and is being used by a threat actor it tracks as REF2924, the group behind the SIESTAGRAPH malware they spotted last December.
Mispadu: Security firm Metabase Q reports on a recent campaign carried out with the Mispadu banking trojan that has targeted Latin America and appears to have collected more than 90,000 credentials from infected hosts.
ALC ransomware: CyFirma researchers have analyzed a recently spotted ransomware strain named ALC and concluded this was only a screen-locker and not a file encrypter.
Sponsor Section
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. The company has recently launched a new type of canary token that looks like an Azure login token and warns companies whenever a threat actor tries to use them.
APTs and cyber-espionage
Lazarus FudModule: IBM's X-Force team has a technical report on the Lazarus FudModule, a toolkit used by the group to impair the visibility of security tools in the malware arsenal's operations.
Kimsuky security advisory: The intelligence services of Germany and South Korea have published a joint advisory on tactics used by the Kimsuky APT to spread malicious Chrome extensions and Android applications.
Armageddon: ThreatMon researchers have published a technical report of the Armageddon (Gamaredon) APT's infostealer.
SideCopy: QiAnXin has a report on the SideCopy APT's attacks on the Indian Ministry of Defense.
"The SideCopy group mainly copies the TTPs of the Sidewinder APT group for attacks. It has come to public eye in recent years, and its attack methods and weapon code are relatively immature compared to other threat groups in the same region, with most of its tools using open source code and tools available on the internet."
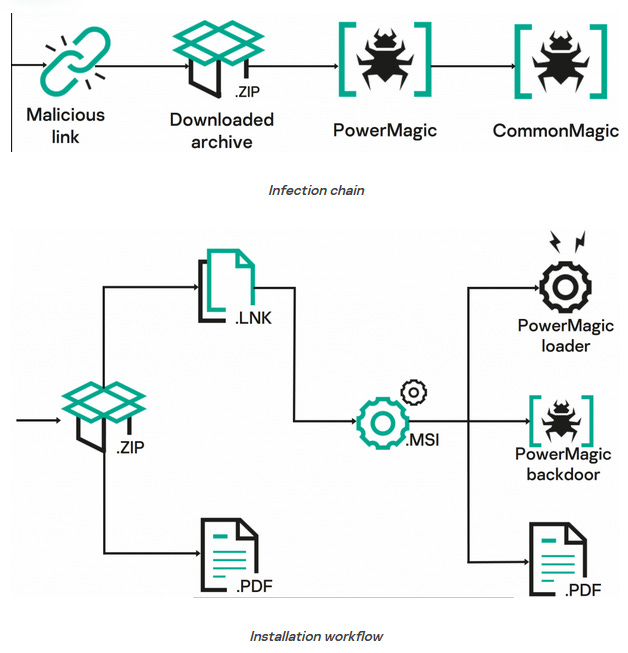
CommonMagic: Kaspersky says it identified a new APT group they are calling CommonMagic, operating in the area of Russo-Ukrainian conflict. The group has been active since at least October 2022 and appears to have targeted government, agriculture, and transportation organizations located in the Donetsk, Luhansk, and Crimea regions. Kaspersky says victims get infected via spear-phishing emails containing links to boobytrapped ZIP archives. These files install the PowerMagic backdoor, which is then used to deploy a previously unseen malware framework named CommonMagic, which gave the group's name.
Vulnerabilities and bug bounty
Zoom bug bounty program: Video conferencing service Zoom says it paid out more than $3.9 million to hundreds of security researchers via its bug bounty program in FY2022/23. In total, the company says it has awarded over $7 million since the program began in 2019.
Jenkins update: The Jenkins project has security updates out for 15 plugins.
Parallels Desktop Toolgate vulnerability: Researchers with ImpalaLabs have discovered a directory traversal vulnerability (CVE-2023-27326) in Toolgate, a component of the Parallels Desktop virtualization software.
"An attacker can leverage this vulnerability to write arbitrary files and execute code in the context of the current user on the host system."
Red Pill attack: ZenGo security researchers have found a new technique named the Red Pill attack that allows malicious smart contracts to detect when blockchain security solutions run "simulated transactions" and hide their malicious behavior. ZenGo says it found six cryptocurrency wallet providers vulnerable to Red Pill attacks. The list includes Coinbase, Rabby Wallet, Pocket Universe, Fire, and Blowfish, all of which have released patches.
aCropalypse comes to Windows: aCropalypse, the vulnerability that can recover cropped or redacted screenshots taken on Android Pixel smartphones, also impacts Windows devices. According to the team of researchers who discovered the original bug, the Snipping Tool on Windows 11 and the Snip & Sketch tool on Windows 10 also produce screenshots that are vulnerable to the aCropalypse bug, allowing threat actors to fully or partially recover the unredacted version of the original screenshot.
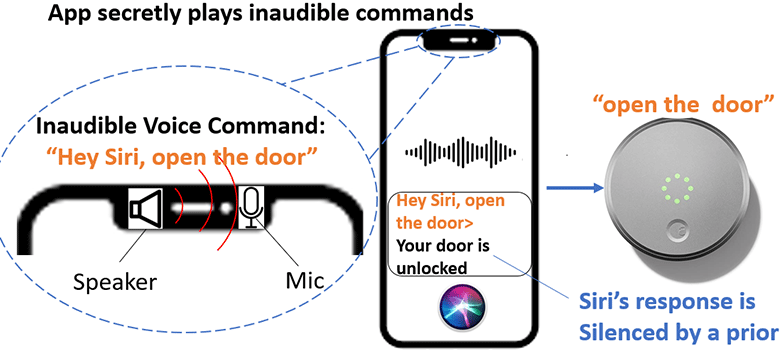
NUIT attack: Academics say they developed an attack method named NUIT (Near-Ultrasound Inaudible Trojan) that uses inaudible sounds embedded in regular audio and video files to send malicious commands to voice assistants. The researchers say the attack works on smart voice assistants such as Siri, Google Assistant, Alexa, Amazon Echo, and Microsoft Cortana.
Infosec industry
New tool—Badsecrets: Black Lantern Security has open-sourced Badsecrets, a Python library that can check for cryptographic secrets leaked across various web development frameworks. Currently supports stuff like Flask, Django, RoR, Symfony, and more.
New tool—Black Angel: Polish security researcher Ksawery "XaFF" Czapczyński has open-sourced Black Angel, an x64 kernel rootkit for Windows 10 and 11.
Kelly Lum: The cybersecurity industry mourns the passing of Kelly "Aloria" Lum, a member of the infosec community for two decades.
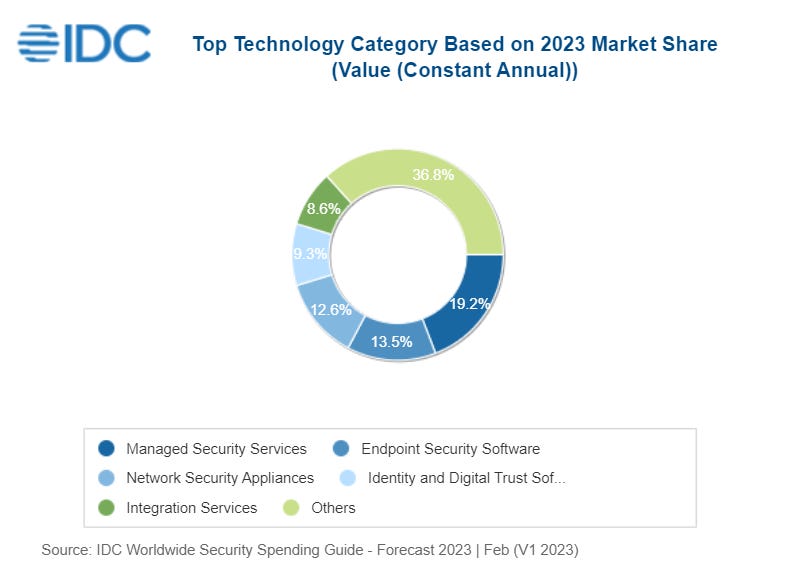
Cybersecurity spending: Worldwide spending on security solutions and services is forecast to be $219 billion in 2023, an increase of 12.1% compared to 2022, according to a prognosis from the International Data Corporation (IDC). Banking, Discrete Manufacturing, Professional Services, and the Federal/Central Government verticals are expected to account for more than a third of all security spending in 2023. Cybersecurity spending overall is expected to surpass the $300 billion yearly mark by 2026.