Risky Biz News: Black Basta group spam-bombs victims and then calls to help
In other news: Another Europol data breach; Google fixes a Chrome zero-day; US Navy to build a unified cyber defense network.

This newsletter is brought to you by Okta. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Breaches, hacks, and security incidents
Another Europol breach: Europol has taken its EPE (Europol Platform for Experts) platform offline in the aftermath of a security breach. The agency started an investigation into the breach hours after a threat actor listed alleged Europol classified documents on a hacking forum. The data was leaked by a hacker named IntelBroker. The same individual previously claimed to have breached the US ICE, the US DOD, HPE, and security firm Zscaler. This marks Europol's second data breach after a first incident in March of last year. [Additional coverage in BleepingComputer]
Christie's hack: The Christie's auction house shut down its website last week in the aftermath of a cyberattack. The attack took place ahead of a week of major auctions expected to bring in around $840 million in sales. The company's website was supposed to allow remote customers to place bids for desired items. Christie's officials didn't share any details and described the incident as a "technology security issue." [Additional coverage in Artnet]
Ohio Lottery ransomware attack: The Ohio Lottery says the personal data of almost 540,000 customers was stolen in a ransomware attack last December. A ransomware group named DragonForce took credit for the incident. The group leaked more than 94GB of files in late January after the Ohio Lottery refused to pay the ransom.
UK news site hacks: A UK newsgroup says it removed a "Russian" story from its site in what looks to be another case where Russian hackers breached a news org to plant fake stories. [h/t Metacurity]
General tech and privacy
Firefox Bounce Tracking Protection: Mozilla is adding a new privacy feature named Bounce Tracking Protection to its Firefox web browser. Bounce tracking is a new tracking technique that became popular after major browsers started phasing out third-party cookies. It works by redirecting users through intermediary URLs before allowing them to access a desired site. Bounce Tracking Protection will try to detect these redirects and only take users to their final destination. The new feature is currently being tested in Firefox Nightly versions.
TikTok structure: A Rest of World investigation has found that despite claiming to have international leadership, TikTok's key decisions are still being made by its Chinese execs.
"Experts say close ties between TikTok and ByteDance call into question whether TikTok could be considered a separate entity, making a potential sale unfeasible."
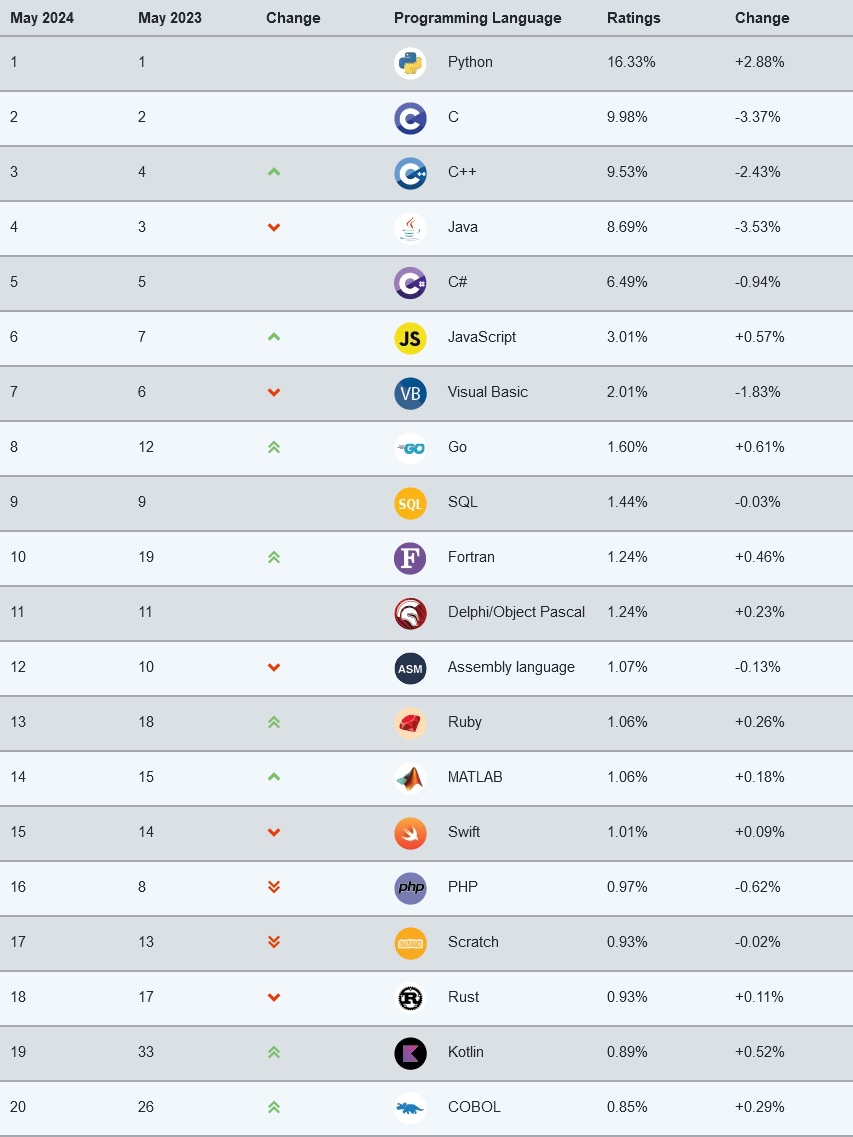
TIOBE index: Dear Lord, almighty! Both Fortran and COBOL are back in the TIOBE index of most programming languages.
Government, politics, and policy
Project Fortress: The US Treasury Department is warning with the country's largest banks to help improve their cybersecurity posture part of an initiative named Project Fortress. The project's main aim is to avoid a catastrophic cyberattack that cripples large parts of the US economy. [Additional coverage in CNN]
Microsoft House hearing: The House Homeland Security Committee intends to subpoena Microsoft President Brad Smith to testify about the company's latest security failings. [Additional coverage in CyberScoop]
US Navy SHARKCAGE: The US government has awarded Accenture a $789-million contract to build a unified cybersecurity platform for the US Navy. The platform will be named SHARKCAGE and will allow the Navy to better defend its networks. Accenture will have to design, build, install, and provide logistics and assessment for the platform. The contract runs for five years with an option to renew for another five. [Additional coverage in The Defense Post]
Sponsor section
In this Risky Business News sponsored interview, Adam Boileau talks to Okta's Cassio Sampaio about how cloud-native applications can move authorisation into a centralised model. This brings real benefits for consistency, control and auditing in distributed applications, beyond just the authentication part Okta is normally known for.

Cybercrime and threat intel
Smart home wall pad hacker sentenced: South Korean authorities have sentenced a former security expert to four years in prison. The individual hacked wall pads, secretly recorded footage from people's homes, and sold intimate videos online. Authorities say the individual hacked over 400,000 wall pads installed across 638 apartment complexes. Police discovered over 200 videos and over 400,000 images on his PC after they arrested the suspect in December 2022. [Additional coverage in Donga]
Crypto-scammers detained: Europol has arrested six Austrians suspected of orchestrating an initial coin offering scam. Officials claim the group pretended to operate an online trading company, issued a cryptocurrency token, and then ran away with its customers' money. The six were arrested in Cyprus last week. The alleged scam took place in late 2017, early 2018. Officials didn't share the name of their platform.
Hacker-for-hire suspect set free: British authorities have fumbled the arrest of a suspected Israeli man who acted as a hacker-for-hire for a US PR company. Authorities arrested Amit Forlit at the London airport earlier this month but failed to arraign him in court in due time. Reuters reports that Forlit was set free last week, and his current whereabouts are unknown.
Black Basta social engineering: The Black Basta ransomware gang is using a new social engineering tactic as a way to gain a foothold inside corporate networks. According to security firm Rapid7, Black Basta operators are flooding the email inboxes of employees of a targeted company. The group calls affected employees posing as their IT help desk and offering assistance. The campaign has been taking place since last month and its end goal has been to install remote access software on the targeted networks. Rapid7 says Black Basta uses the software to collect credentials and move laterally inside a victim's network.
"In all observed cases, the spam was significant enough to overwhelm the email protection solutions in place and arrived in the user’s inbox. Rapid7 determined many of the emails themselves were not malicious, but rather consisted of newsletter sign-up confirmation emails from numerous legitimate organizations across the world."
US Coast Guard phishing lures: The US Coast Guard has published a security advisory [PDF] about a spear-phishing campaign abusing the agency's name as lures.
FIN7 campaign: eSentire looks at a recent FIN7 malvertising campaign distributing malicious MSIX installers. A report on the same campaign is also available via Rewscel.
Monday.com updates: Project management platform Monday.com has removed its "Share Update" feature after threat actors abused it in phishing attacks. [Additional coverage in BleepingComputer]
Threat/trend reports: CyFirma, Intel471, and ThreatDown (Malwarebytes) have recently published reports covering infosec industry threats and trends.
Malicious Minecraft mod: Members of the Minecraft open-source mod portal Modrinth have discovered malware in a mod named Windows Borderless. The malware can collect passwords from web browsers and other popular apps. Modrinth says that around 372 users downloaded the mod, and at least one user had a Discord account hacked. The mod allows Minecraft to run in Windows borderless mode and is usually popular with streamers or users who leave the game running in the background.
New npm malware: Twenty-eight malicious npm packages were discovered last week. Check out GitHub's security advisory portal for additional details.
PyPI malware: DevSecOps company Phylum has found a malicious Python library that mimicked the more popular Requests library but deployed a malicious Go backdoor on victim systems via the library's logo image.

Malware technical reports
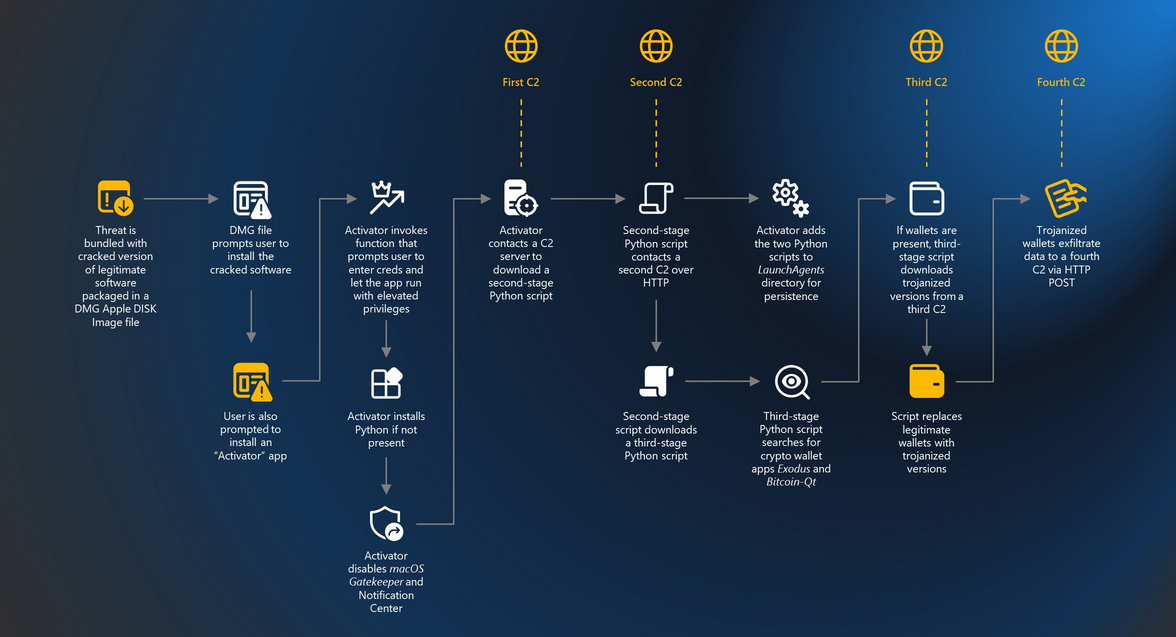
Activator: The Activator macOS malware gang ramped up operations in March this year in a campaign that is still active today. The malware works by replacing legitimate versions of the Exodus and Bitcoin-Qt cryptocurrency wallets with malicious ones that steal a user's funds. According to Microsoft's security team, the malware is distributed via cracked versions of legitimate macOS apps. Once installed, Activator turns off the macOS Gatekeeper and then disables the macOS Notification Center to hide its presence on infected systems.
Cuckoo: SentinelOne looks at a new macOS infostealer named Cuckoo. A report on the same malware is available via Kandji.
"The actors behind the Cuckoo Stealer campaign have clearly invested some resources into developing a novel infostealer rather than buying any of the ready-made offerings currently circulating in various Telegram channels and darknet forums. This, along with the rising numbers of samples we have observed since initial reporting of this threat, suggests that we will likely see further variants of this malware in the future."
Lumma Stealer: Cyber-Forensics has published an analysis of the Lumma Stealer infostealer.
XZ backdoor: Knownsec 404 researchers have published another analysis on the XZ backdoor.
Black Basta ransomware: According to a joint security advisory from US government agencies, the Black Basta ransomware gang has hit organizations in 12 of the US' 16 critical infrastructure sectors.
Rhysida ransomware: Barracuda's security team has posted a report on the Rhysida ransomware gang and its operations.
Wormhole ransomware: Qihoo 360 researchers have spotted attacks on Chinese end-users with the Wormhole ransomware. Users are typically asked to pay a ransom of 0.04 bitcoin ($2,500).
HiddenShovel: Antiy researchers have discovered a new crypto-mining botnet named HiddenShovel. The malware was first seen in November 2023 and targets Windows systems.
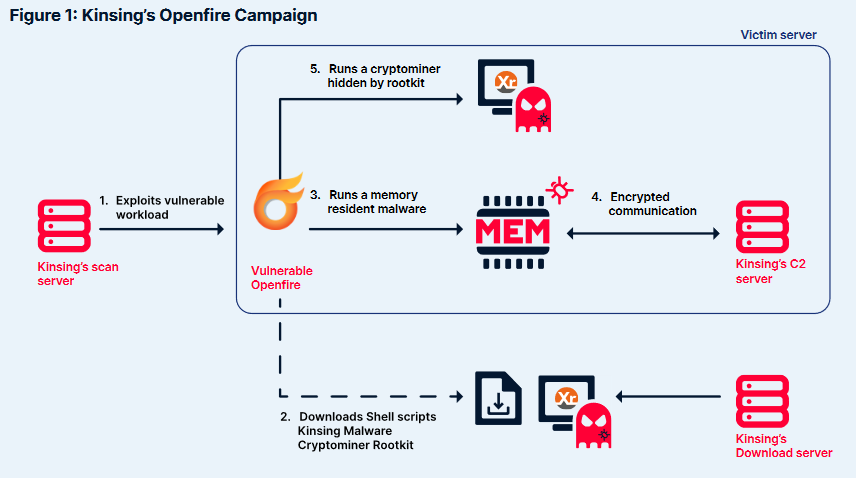
Kinsing: A botnet named Kinsing is exploiting vulnerabilities in over 75 different applications to breach systems and deploy a cryptominer. 90% of the targets are open-source applications. According to Aqua Security, the botnet has been active since 2019 and receives updates almost on a weekly basis.
Sponsor Section
Brett Winterford and Harish Chakravarthy demonstrate to Risky Biz host Patrick Gray how Okta can be used for passwordless authentication. These phishing-resistant authentication flows—even if they are not rolled out to all users—can also be used as a high-quality signal of phishing attempts that can be used to trigger automated follow-on actions.
APTs, cyber-espionage, and info-ops
MuddyWater: Iranian APT group MuddyWater is increasingly adopting residential proxy IPs to hide its operations. Security firm Obsidian says the group relies on residential proxies when accessing previously phished accounts. Operators will employ a residential IP from a victim's local area to bypass enterprise geofenced access policies and access the account without triggering security alerts.
Lazarus (APT-Q-1): Chinese security firm QiAnXin has a report on a recent Lazarus (APT-Q-1) campaign targeting blockchain industry experts on LinkedIn, Upwork, and Braintrust with malicious ZIP files.
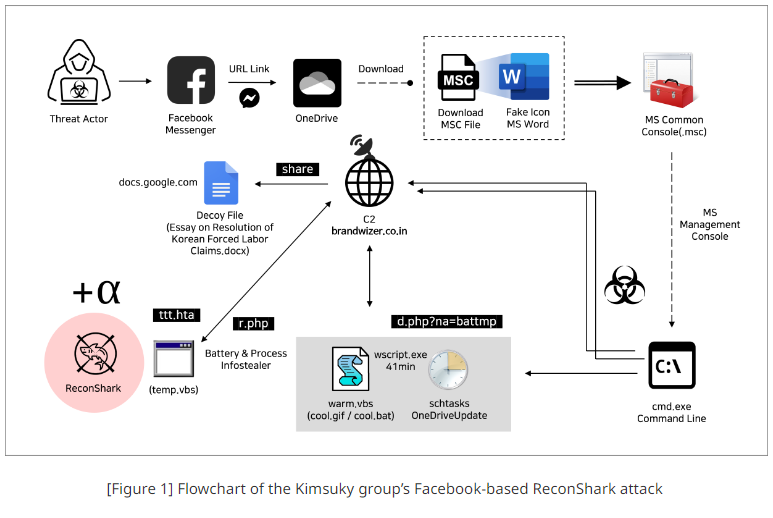
Kimsuky: South Korean security firm Genians says North Korean APT group Kimsuky is targeting users in Japan and South Korea using Facebook Messenger messages. Victims are sent malicious files, with the final payload being the ReconShark malware.
Vulnerabilities, security research, and bug bounty
Chrome zero-day: Google has released an update for its Chrome browser to fix a zero-day (CVE-2024-4671) exploited in the wild. The zero-day is a vulnerability in Chrome's Visuals component, a collection of libraries for interacting with the GPU. This is the fifth Chrome zero-day patched this year.
Cinterion vulnerabilities: Kaspersky researchers have found critical vulnerabilities in Cinterion cellular modems. The vulnerabilities allow threat actors to take over modems using a malicious SMS message. Telit Cinterion cellular modems are typically embedded in industrial and IoT equipment to allow remote management. Telit released firmware updates for all bugs at the end of last year.
NextJS SSRF bug: Security firm Assetnote has found an SSRF vulnerability in the NextJS JavaScript framework. The framework is one of today's most popular tools for building one-page web apps, static sites, and CMS platforms. The vulnerability (CVE-2024-34351) allows threat actors to have a NextJS server make requests to other services, and return the output.
PDF.js vulnerability: Mozilla has fixed a bug (CVE-2024-4367) in the PDF.js web-based PDF viewer that could have allowed threat actors to execute malicious code via the app's font loader.
Arcserve exploitation: Threat actors are exploiting three vulnerabilities in the Arcserve Unified Data Protection (UDP) backup and disaster recovery server to gain access to victim networks. Attacks were detected in the wild by the UK's National Health System. The NHS says attacks started after a cybersecurity firm published proof-of-concept exploit code online. [h/t Screaming Goat]
Veeam security updates: Backup software maker Veeam has released a security patch to fix a vulnerability in its Service Provider Console (VSPC) server.
PressHammer: Academics have put together RowHammer and RowPress [PDF] to create a new RAM attack called PressHammer [PDF].
Infosec industry
New tool—HelloJackHunter: Security researcher Andy Gill has open-sourced HelloJackHunter, a tool for DLL hijacking via WinSxS binaries.
New tool—HoneyTrail: Security researcher Adan Álvarez has open-sourced HoneyTrail, a tool to deploy customized honeyservices on AWS and trigger alerts for unauthorized access.
UniCon 2024: Talks from Scythe's UniCon 2024 security conference, which took place in early April, are available on YouTube.
RSA 2024: Talks from the RSA 2024 security conference, which took place last week, are available on YouTube. SecurityWeek has a summary of all the RSA press releases and announcements from the conference's four days—1, 2, 3, 4.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at how different types of secrecy-obsessed organizations learn.




