Risky Biz News: Bitcoin ATMs hacked
In other news: VIASAT hack impacted French emergency services; LockBit gang gets DDOSed; and Tox sees usage as C&C channel.
This newsletter is brought to you by Airlock Digital, Proofpoint, RunZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
In news that you never heard before—Bitcoin ATMs have been getting hacked across the world after a mysterious threat actor discovered a zero-day vulnerability in the ATM's web-based admin management panel.
The attacks, which appear to have been taking place since the start of the month, have been targeting Bitcoin ATMs managed via Crypto Application Server (CAS), a cloud-based system from Panama-based company General Bytes.
In a security alert published on Friday, the company said the attackers scanned the internet to identify CAS servers and then accessed a left-over URL from the CAS installation process. This URL allowed them to re-register the admin panel's default admin user using their own credentials; access they later used to change ATM settings so every time a user would send money to an ATM to be picked up using an in-person transaction, the funds would be automatically redirected to the attacker's wallets.
General Bytes said all CAS servers released over the past two years are vulnerable (since CAS version 20201208). The company said it released patches that should address the vulnerability exploited in the attacks.
According to BleepingComputer, there were 18 General Bytes CAS servers still exposed online last week, but more are believed to be hidden behind firewalls since the attacks were first reported.
General Bytes said the attacks against its ATMs started three days after it added a "Help Ukraine" feature to its machines earlier this month.

Breaches and hacks
Airplane Accelerates leak: CyberNews says it found 626GB of customer data in an unsecured Elasticsearch server belonging to Airplane Accelerates, a free VPN service advertised to Chinese users. The data contained a staggering of 5.7 billion entries, including user IDs, what IP addresses users were connecting to and from, domain names, and timestamps, the news outlet reported.
Failed crypto-heist: Cryptocurrency bridge project Celer said it successfully fended off a cyber-attack after a threat actor attempted a DNS hijacking account against its frontend infrastructure.
❤️100% users who revoked phishing contract approvals are compensated, 98% loss is recovered!
— CelerNetwork (@CelerNetwork) 12:58 PM ∙ Aug 19, 2022
🦾Funds in cBridge smart contracts was never affected
👀Active frontend and DNS integrity checks are added to prevent similar attempts
📢Missing refunds? Please revoke approvals first.
General tech and privacy
Warning about in-app browsers: Privacy expert Felix Krause has published two write-ups over the past week warning about the dangers of using a mobile app's built-in browser as compared to standalone browsers. In a first report, Krause said he found that the Facebook and Instagram in-app browsers were tracking users on all the sites they visited, while in a second, he said he found key-logging code in TikTok's in-app browser, although he did not find any evidence that it was being actively used.
Government, politics, and policy
VIASAT hack impact in France: According to the minutes of a closed-doors meeting held by Stéphane Bouillon, Secretary General of Defense and National Security for the French Parliament's National Assembly, the Russian hack of the VIASAT satellite internet network had "affected" French ambulance (phone number: 15) and firefighting (phone number: 18) emergency services. The extent of the impact was not detailed. (h/t @SwitHak)
DOD browsing history purchases: The National Defense Authorization Act, a bill passed by the US House in July, which authorizes Department of Defense (DOD) activities and expenses for fiscal year 2023, also includes a clause that will require the DOD to disclose any purchases of smartphone or web browsing data if such purchases target American citizens, according to Gizmodo. The bill still needs to pass the US Senate. The initiative comes after Congress also began looking into similar purchases made by US law enforcement agencies as well, as officials seem to want to crack down on the use of such data, or at least get some visibility into how agencies are using such data, which until now has been used outside of most oversight mechanisms.
NSO CEO steps down: Shalev Hulio, the CEO of embattled spyware maker NSO Group, will step down from his role, the company announced on Sunday. According to Reuters, COO Yaron Shohat will be appointed to oversee a reorganization of the company before a successor is named. This marks the second time that Hulio resigned as NSO CEO after he also resigned in October 2021 but was forced to come back after his replacements left shortly after being brought on board. The company is also rumored to be preparing to sack around 100 employees as well.
Russia looking at more misbehaving companies: Roskomnadzor said it is looking at companies like TikTok, Telegram, Zoom, Discord, and Pinterest after the companies refused to remove "prohibited" content, most likely in relation to Russia's invasion of Ukraine. Since its invasion of Ukraine, Russia has slowly cracked down on the Tor Project, VPN providers, Facebook sites, Twitter, Twitch, and many others.
Russia may compensate victims who had their data leaked: The Russian Ministry of Digital Development is considering an initiative to provide some sort of financial compensation to Russian citizens who had their data leaked online. Kommersant reports that the funds for these payments may come from the companies who leaked the data; in the form of fines the ministry might impose.
Sponsor section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year where they show off Nexus People Risk Explorer, the company’s product for mitigating insider threats:
Cybercrime and threat intel
LockBit gets DDOSed: After the LockBit ransomware gang took credit for the ransomware attack against security firm Entrust, the gang's servers have been flooded by DDOS attacks with messages of "DELETE_ENTRUSTCOM_[REDACTED]" — referencing that LockBit operators should delete the Entrust entry and its data from their leak site.
Lockbit: "We're being DDoS'd because of the Entrust hack"
— vx-underground (@vxunderground) 8:02 AM ∙ Aug 21, 2022
vx-underground: "How do you know it's because of the Entrust breach?"
Lockbit:
Desorden Group: In a report last week, CyberInt said they'd seen the Desorden Group list several Thai entities as victims of their intrusions. Desorden is a threat actor that was first spotted last year and which operates by breaching organizations, stealing their data, and trying to extort a ransom payment from victims.
Pitraix botnet: An unknown developer has open-sourced a new Go-based P2P botnet named Pitraix that works via Tor and can self-modify with every new infection. Add your detections, folks!
Cryptominers on npm and PyPI: Sonatype researchers have found another batch of malicious packages uploaded on the npm and PyPI portals. This time, they found more than 200 libraries, all configured to install cryptominers on infected hosts. These findings come after several similar incidents were reported last week [1, 2, 3, 4, 5].
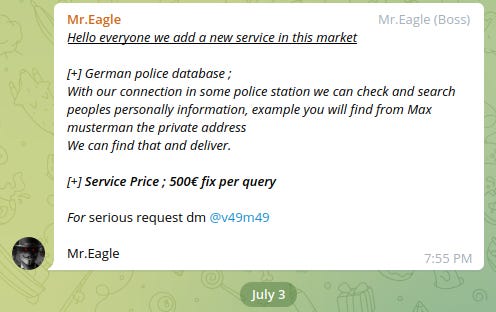
Attacks on LEAs: In a report published on Friday, Resecurity said it observed multiple dark web marketplaces where cybercriminals have sold accounts and credentials belonging to police officers of various foreign countries (emails, VPNs, SSO, etc.).
New FBI PIN alert: The FBI published a new private industry notification (PIN) on Thursday, warning US organizations of the use of proxy servers to carry out credential stuffing attacks. As a way to counter these threats, the FBI recommends using MFA on vulnerable accounts and educating users about the dangers of reusing passwords. More here [PDF].
New exploited vulns added to KEV: CISA has added seven new vulnerabilities to KEV, its database of actively exploited security flaws. These include bugs in SAP, PAN-OS, Apple, Microsoft, and Chrome.
Tox as a C&C mechanism: Researchers from cloud security firm Uptycs said they have begun seeing the Tox P2P serverless instant messaging system used as a command and control mechanism for some cryptomining operations.
New domain-fronting technique: The team behind Shell.Systems have published a report on a new domain-fronting technique abused in the wild to hide malicious traffic. The technique relies on abusing the services of tyk.io, a cloud-native API management platform used by a lot of applications worldwide to manage their API calls via the cloud. According to Vitali Kremez, CEO of AdvIntel, many former members of the Conti ransomware group are currently abusing this technique.
⚡️Timely report on the latest Cobalt Strike domain fronting technique leveraging tyk[.]io.
— Vitali Kremez (@VK_Intel) 8:27 PM ∙ Aug 19, 2022
Many ex-Conti groups leverage this domain fronting technique for Cobalt Strike beacon resolver/traffic.
Watch out for tyk[.]io traffic.
Malware technical reports
Grandoreiro: Zscaler researchers have a report out on recent Grandeiro campaigns targeting Spain and Mexico, with email phishing campaigns hitting multiple industry verticals.
Astaroth: In a similar write-up, ISC SANS researchers have documented a malspam campaign pushing the Astaroth (Guildama) trojan to Brazilian targets.
LockBit 3.0: NCC Group researchers have a report out going through the steps of an intrusion and ransomware attack carried out with the LockBit 3.0 ransomware strain.
ATMZOW: Group-IB researchers have published a report on cybercrime group ATMZOW and its JavaScript-based malware that they typically install on compromised sites. Following recent attacks that took place in May this year, researchers believe ATMZOW might be connected to the Hancitor group.
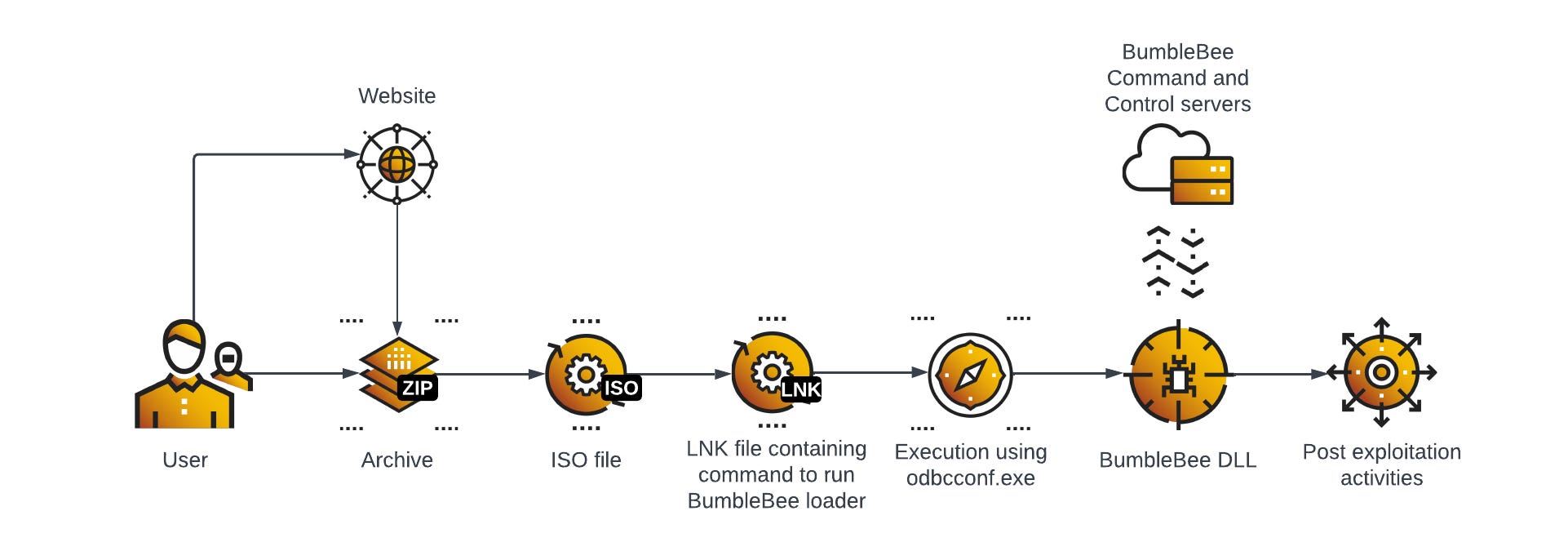
Bumblebee: The Bumblebee is a pretty common threat these days, and we've had reports on it from almost all major vendors. Cybereason has one on it too.
APTs and cyber-espionage
Kasablanka: Qihoo 360 researchers have published a report on new campaigns carried out by the Kasablanka threat actor targeting Bangladesh. Cisco Talos researchers believe this group is based in Morocco, which is why it is referred to as "Kasablanka." InfinitumIT, a Turkish cybersecurity firm, has also covered this APT's attacks, and the company identified one of the victims as Yakın Doğu Üniversitesi, a university in the Turkey part of Cyprus.
MurenShark: NSFOCUS researchers have published a report on MurenShark, a new APT group based in the Middle East whose main target appears to be Turkey. Malware linked to the group includes NiceRender, a malicious Word document builder, UniversalDonut, a malware loader, and LetMeOut, a backdoor trojan.
Vulnerabilities and bug bounty
DirtyCred: Northwestern student Zhenpeng Lin presented details at the BlackHat security conference on DirtyCred, a Linux kernel exploitation concept that can swap unprivileged kernel credentials with privileged ones.
This Thursday @BlackHatEvents , I will be presenting our research on a kernel exploitation method named #DirtyCred. With DirtyCred, you could write an #DirtyPipe liked exploit that works on different kernels and ARCHs without code changes. Check it out tinyurl.com/DirtyCred
— Zhenpeng Lin (@Markak_) 7:49 PM ∙ Aug 7, 2022
Interesting Firefox vulnerability: The ZDI team has finally published a detailed write-up on CVE-2022-1802, a vulnerability first exploited during the Pwn2Own 2022 hacking contest that took place earlier this year in May in Vancouver, Canada. The vulnerability is unique because it targeted the Firefox renderer and, more specifically, inside a component written in a memory-safe language like JavaScript.
Amazon Ring bug: Checkmarx researchers have published details about a vulnerability in the Android app of Amazon Ring cameras that could have been used to expose users' camera recordings. Amazon has fixed the issue, per the security firm.
SSH fingerprinting study: An academic study conducted by researchers from the Technical University of Berlin details a new way of fingerprinting SSH servers using SSFP entries inside DNS records. Researchers say that approximately one in 10,000 domains have an SSHFP entry but that more than half of them are deployed without using DNSSEC, drastically reducing security benefits.
Infosec industry
Thoma Bravo's potential Darktrace acquisition: Shares of cybersecurity artificial intelligence specialist Darktrace are soaring after the company confirmed it's in talks with private equity firm Thoma Bravo about a potential takeover, CRN reported.
CISO guide on doing IR: Tarah Wheeler and friends have published a guide for private organizations and state and local governments on how to answer and investigate major cybersecurity incidents.
New tool—BBOT: Black Lantern Security has open-sourced BBOT, an OSINT automation framework for hackers. BBOT, which is available on GitHub, comes with support for subdomain enumeration, port scanning, web screenshots, vulnerability scanning, and more.
New tool—HijackLibs: Dutch security researcher Wietze Beukema launched during the DEF CON 30 security conference a new project called HijackLibs, a web portal to list and keep a record of all publicly-disclosed DLL hijacking techniques.
Today I'm launching #HijackLibs, an open-source, community-driven project tracking DLL Hijacking opportunities in in Windows
— Wietze (@Wietze) 8:15 PM ∙ Aug 14, 2022
🌍 LIVE on hijacklibs.net 👈
🆕 Currently comprising over 350 unique DLLs that can be targeted
🤝 Contribute via github.com/wietze/hijackl…
New tool—WFH: IBM X-Force researcher Chris Spehn has released an update for his Windows Feature Hunter (WFH) script, a tool that can identify DLL and COM hijacking opportunities in Windows features. This new update was inspired by techniques used by the Dridex malware and expanded the original WFH tool's capabilities by more than ten times.
Today I'm releasing WFH Dridex, another approach to automatically identify and validate DLL sideloading opportunities inspired by the Dridex loader. I also submitted a pull request to @Wietze's HijackLibs project with 507 entries from C:\Windows\System32.
— Chris Spehn (@ConsciousHacker) 4:59 PM ∙ Aug 17, 2022
github.com/ConsciousHacke…




