Risky Biz News: Backdoor found in 92k D-Link NAS devices
In other news: New Ahoi attack impacts cloud VMs; Chinese info-ops adopt AI; Palau falls to ransomware attack.

This newsletter is brought to you by GreyNoise. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

A security researcher going online by the pseudonym of NetSecFish (NetworkSecurityFish) has discovered a backdoor in D-Link network-attached storage (NAS) devices.
D-Link has declined to patch the issue as all the devices reached End-of-Service four years ago, in June 2020.
The list of affected products includes NAS models DNS-320L, DNS-325, DNS-327L, and DNS-340L.
According to NetSecFish, more than 92,000 devices are currently connected to the internet and ripe for exploitation.
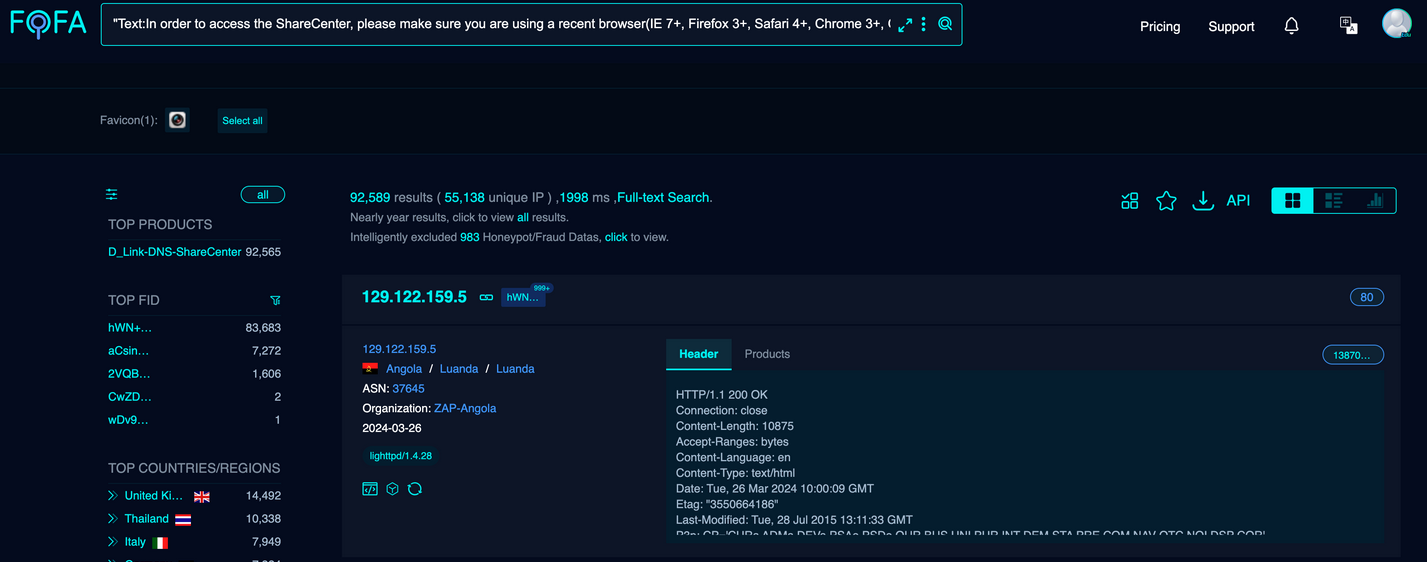
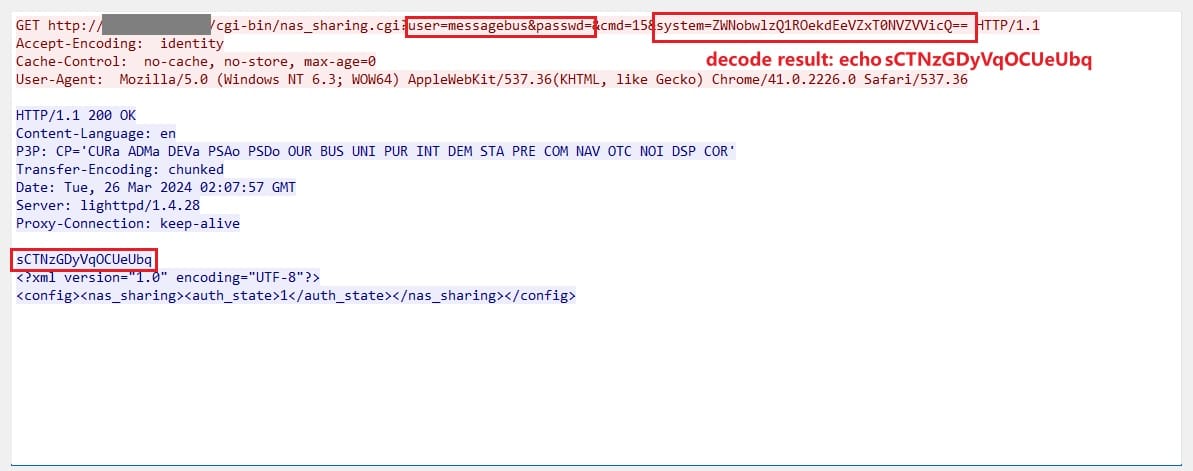
The devices are actually impacted by not one but two issues. The first is the backdoor (tracked as CVE-2024-3272), and the second is a command injection vulnerability (tracked as CVE-2024-3273).
The backdoor is a set of hardcoded credentials that can be fed to the "nas_sharing.cgi" server interface and authenticate on the device.
user=messagebus
passwd=(empty field)
The second vulnerability can be exploited via the same interface to allow an attacker to run commands on the NAS operating system via the "system" parameter, allowing for quick one-line exploits that compromise the device with one network request.
Since the product has been EoS for four years and D-Link has declined to release new firmware for such old hardware, the researcher has published both details and a proof-of-concept exploit on their GitHub account.
Despite being EoS for four years, the high number of available systems still online will most likely attract loads of attention from botnet herders.
Breaches, hacks, and security incidents
Acuity breach: Virginia-based tech consulting firm Acuity has confirmed a security breach after a threat actor stole data from its GitHub repositories. The admission comes days after a hacker named IntelBroker posted some of the company's data on an underground hacking forum. The threat actor claimed it stole classified data from US military and intelligence agencies. Acuity says the GitHub repos contained only "dated and non-sensitive information."
Palau ransomware attack: The Palau government has fallen victim to a ransomware attack that encrypted files and crippled IT systems. Officials reported finding two ransom notes. The first was from the more well-known Lockbit gang, and the second was from a smaller group called Dragonforce. The latter group formally claimed the attack over the weekend. The incident marked the second time the small Pacific island nation dealt with a ransomware attack. The previous attack was in 2019. [Additional coverage in The Record]
University of Winnipeg incident: The University of Winnipeg in Canada fell victim to a cyberattack at the end of March. Officials say hackers stole the personal details of past and current staff and students. Besides personal details, the data also includes bank account information for some of its staff. The incident knocked out network access and forced the institution to cancel classes. Officials have not said if it was a ransomware attack.
General tech and privacy
Jpegli: Google has open-sourced Jpegli, a new JPEG coding library. The library is backward-compatible while adding a 35% compression ratio improvement at high-quality compression settings.
Notepad++ asks for help: The developers of the Notepad++ text editor have asked users to help report a new website impersonating its brand and ranking high in search results.
New Microsoft driver: Microsoft added a secret driver via the February update for Windows 10 and Windows 11 that prevents users from changing their default browser. The driver is called UserChoice and prevents editing of the registry key associated with default browser registry keys. It's unclear if this is a bug or if the driver is working as intended.
Ivanti CEO open letter: Ivanti CEO Jeff Abbott has published an open letter promising an overhaul of its software and security practices after its products have been the target of multiple state and financially-motivated threat actors over the past years.
Matrix asks for public funding of FOSS projects: The Matrix.org Foundation is urging governments to fund more open-source projects. The organization's call comes in the aftermath of the XZ Utils incident from last month. Matrix developers are asking for funding that is not contractually tied to new feature development. The Matrix team is, instead, requesting that governments fund basic code security and maintenance operations.
"This funding should NOT be tied to specific feature development, but simply funding the core maintenance of the infrastructure - paying for the maintainers (and/or letting them or their umbrella org hire trusted ones!) to ensure the core project remains healthy and secure. Otherwise, the pressure just rises on the core project to chase feature development at the expense of maintenance (making maintenance harder) - or, worse, to be pushed away from open source into building proprietary solutions or crippling the open source by moving valuable features into side proprietary products."
Government, politics, and policy
ENISA CRA report: The EU's cybersecurity agency ENISA has published a report on how companies can become compliant with the EU's new Cyber Resilience Act.
Cyber Storm IX: CISA will host the ninth edition of its Cyber Storm defensive cyber exercise. The exercise will host more than 2,000 participants and will simulate the response to a large-scale cyber incident on critical infrastructure. [Additional coverage in FederalNewsNetwork]
CISA joins MVSP: CISA has joined the Minimum Viable Secure Product, an industry group working on minimum security baselines for enterprise-ready products and services. The MVSP launched in November of last year. Some of the MVSP's biggest members include Google, Netflix, Okta, and Slack.
Czechia warns of Russian hacks on railways: Czech officials have warned that Russian hackers are trying to sabotage railway systems across Europe using DDoS attacks and by hacking into their signaling systems. The warning comes as Russia has been jamming GPS signals across Northern Europe from its Kaliningrad exclave. [Additional coverage in the Kyiv Independent]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with GreyNoise founder Andrew Morris about last year's vulnerability exploitation trends, how the company's AI system works, and Catalin makes a fool of himself because he can't pronounce 'abnormalities.'

Cybercrime and threat intel
PrivNote crypto-phishing: Infosec reporter Brian Krebs has uncovered a network of phishing sites mimicking the PrivNote secure note-sharing service. The sites contained malicious code that swapped cryptocurrency addresses shared in notes with an attacker-controlled address. Krebs says the operation was incredibly profitable. Just one of the malicious sites hijacked $18,000 worth of cryptocurrency over just five days.
Manipulaters: DomainTools and (the same) Brian Krebs have published new reporting on the Manipulaters, an old cybercrime group known for selling phishing kits and spamming services.
GhostBusters: Threat intel analyst g0njxa has published a profile of GhostBusters. Also known as MMM, a traffer team known for working with infostealer gangs.
AI-themed lures: Bitdefender has spotted a malvertising campaign active on social media sites that push users to websites offering malware-infested generative AI tools. Crooks impersonated tools from the likes of Midjourney, Sora AI, DALL-E 3, Evoto, ChatGPT 5, and others.
New npm malware: Twenty-one malicious npm packages were discovered last week. Check out GitHub's security advisory portal for additional details.
Threat/trend reports: Elastic, Qrator Labs, RiskRecon, Sonicwall, and VISA have recently published reports covering infosec industry threats and trends.
Malware technical reports
Byakugan: Fortinet has published a report on the Byakugan malware, first documented by AhnLab here.
RisePro: ThreatMon has published a (gated) report on RisePro, one of the recent infostealer strains that are gaining popularity with various threat actors.
JSOutProx: Security firm Resecurity has spotted a new version of the JSOutProx malware framework. According to VISA's security team [PDF], the malware was used in attacks against banks and other financial institutions across APAC and MENA. The malware is coded in JavaScript and .NET. It is a highly modular backdoor used for remote access into compromised systems. The malware's first version was seen in the wild in 2019 and has been linked to a group known as Solar Spider.
Raspberry Robin: Security firm Harfang has published a technical deep dive into Raspberry Robin's new anti-emulation technique—inspired by a 2018 Black Hat talk [PDF].
Sponsor Section
GreyNoise founder Andrew Morris demonstrates how people use the GreyNoise sensor network.
APTs, cyber-espionage, and info-ops
MuddyWater DarkBeatC2: DeepInstict has published a report on DarkBeatC2, a previously unreported C2 framework used by the MuddyWater Iranian cyber-espionage group.
Russian disinfo: FOIA requests obtained by Bloomberg paint a grim picture on how the DoD and Biden administration have miserably failed to counter Russian disinformation campaigns after the Ukraine invasion. That propaganda was so good that there are now Republican lawmakers parroting it inside closed-door House meetings. YOLO!
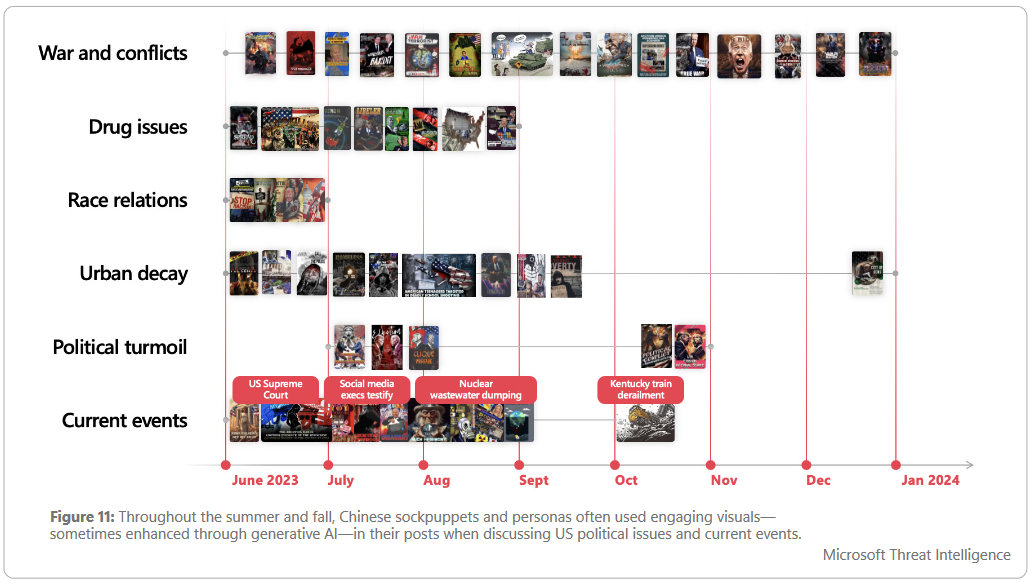
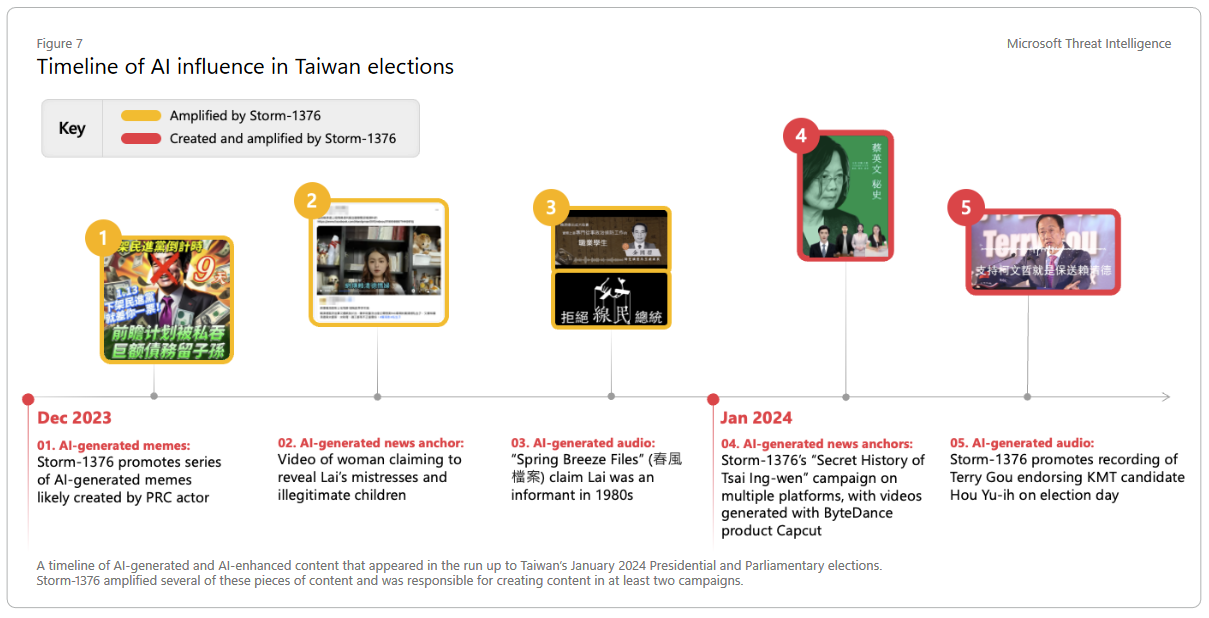
Chinese info-ops love AI: Chinese threat actors are increasingly adopting generative AI technologies for influence operations. The most active threat actor is tracked as Storm-1376 or Spamouflage. Microsoft says the group used AI-generated images and text translated into more than 30 languages in an attempt to influence public opinion. The group ran campaigns targeting the US, Taiwan, and Pacific islands. The vast majority of the campaigns ran on Twitter. [More about threat actors trends in SE Asia in Microsoft's report/PDF]
Vulnerabilities, security research, and bug bounty
Jasmin ransomware exploit: Security researcher Evan Ikeda has published details and a PoC for a vulnerability in the control panel of the Jasmin ransomware operation. Ikeda says the bug can be used to "deanonymize panel operators and dump decryption keys." The vulnerability is tracked as CVE-2024-30851, and Ikeda described it as a pre-auth path traversal vulnerability.
Chaos RAT RCE: The same Ikeda has also found an XSS+RCE combo vuln (CVE-2024-30850) that can be used to take over command-and-control servers for Chaos RAT. It's funny how both issues received CVE identifiers.
Brocade RCE: Broadcom has published a fix for an RCE vulnerability in Brocade Fabric OS. This is the firmware that runs on the company's Brocade network switches. [h/t Simon Tsui]
GOG bugs: Anvil Secure has published a write-up on two bugs (DoS+LPE) they found in CD Projekt Red's GOG gaming platform.
V8 Sandbox in the Google VRP: Google has included the V8 Sandbox component in its official Vulnerabilities Rewards Program (VRP). Security researchers can stand to earn bug bounties of up to $5,000 for vulnerabilities that can bypass the component. The V8 Sandbox is a Google Chrome component that isolates JavaScript code inside its own sandbox. Google began developing the V8 Sandbox in 2021 after learning that a large number of dangerous bugs were targeting the Chrome V8 JavaScript engine.
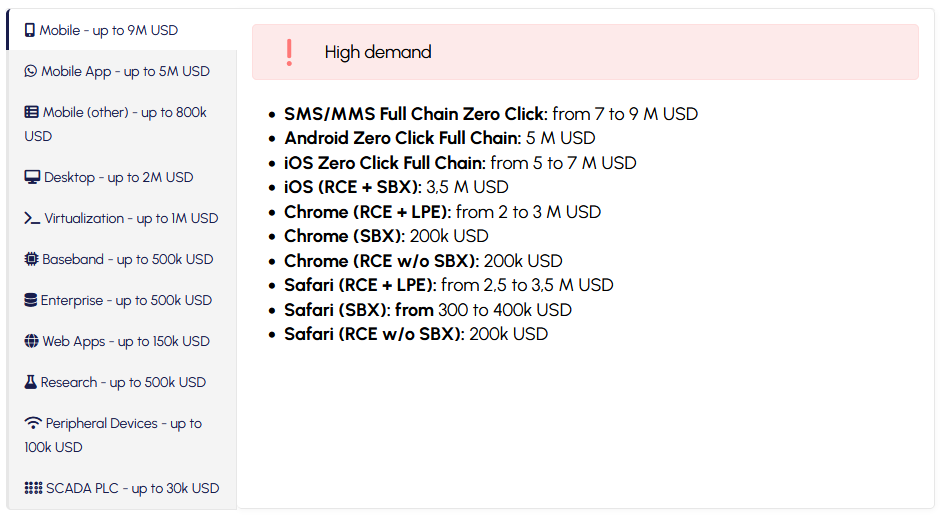
Zero-day prices: Vulnerability acquisition platform Crowdfense is willing to pay millions of US dollars for zero-click exploits in iOS, Android, and secure messaging apps. The company is offering up to $9 million for zero-click exploits that work via SMS or MMS and up to $7 million for iPhone zero-days. It is also offering up to $5 million for Android zero-days, and for zero-click exploits in Signal and WhatsApp. The company launched years before but had gone dormant for months. It restructured operations and re-launched its program with new prices at the end of March. [Additional coverage in TechCrunch]
ConnectSecure exposure: More than 16,500 ConnectSecure VPNs are currently exposed online and vulnerable to a recent RCE tracked as CVE-2024-21894. Ivanti patched the bug at the start of the month. The vast majority of vulnerable systems are located in the US, per the Shadowserver Foundation.
Hugging Face fixes: Hugging Face has rolled out fixes to address a vulnerability in its AI-as-a-Service platform. The issue could have allowed threat actors to upload malicious AI models that backdoored Hugging Face's platform and stole customer data. Cloud security firm Wiz discovered the issue, which exploited a flaw in the Hugging Face Inference API.
Ahoi attack: A team of academics has discovered a new attack that can break the confidentiality of trusted execution environments (TEEs) used by cloud service providers. The new Ahoi attacks affect AMD SEV-SNP and Intel TDX, two TEEs used by cloud providers to host confidential virtual machines (CVMs). The attacks exploit the notification system between the hypervisor and the guest OS. A successful attack can allow threat actors to access data stored in the memories of other cloud users working with the same hardware.
Infosec industry
New tool—CspReconGo: Arcanum Infosec's Jason Haddix has released CspReconGo, a tool that automates the extraction and analysis of domains from Content Security Policy (CSP) headers and JavaScript files.
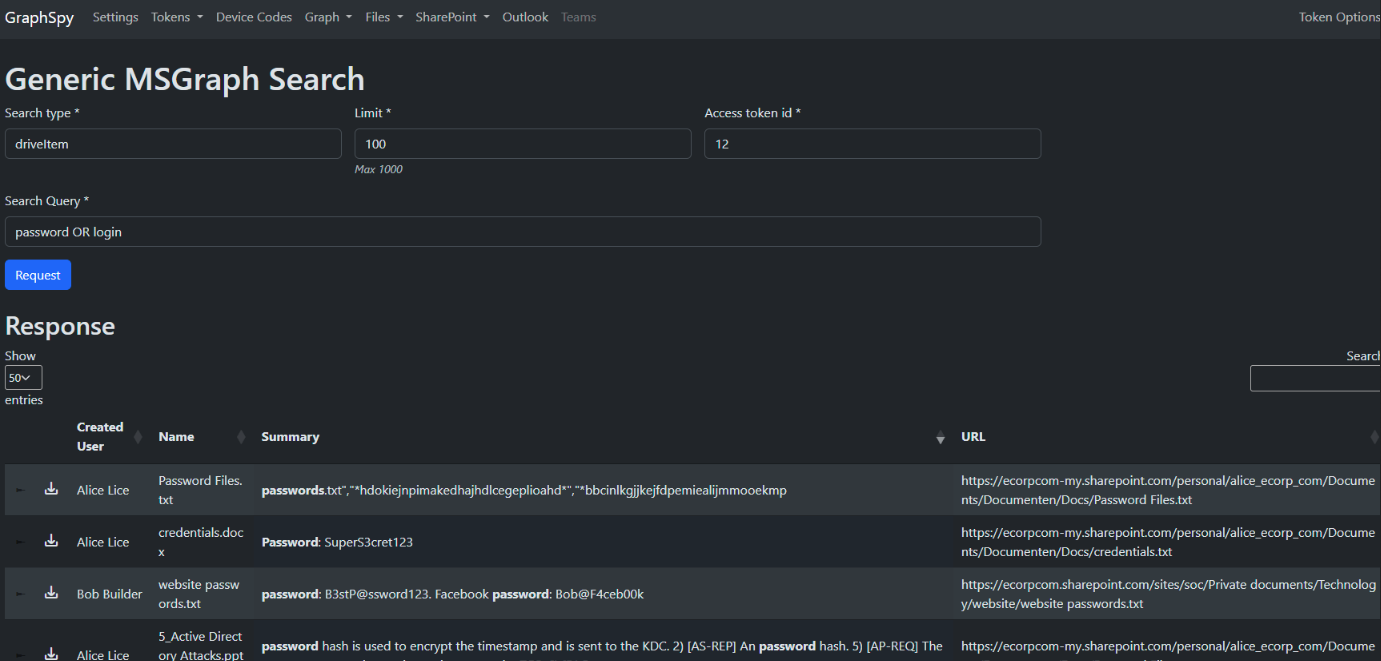
New tool—GraphSpy: Spotit security researcher Keanu Nys has open-sourced a new red-team and pen-testing tool for Azure AD and Office 365 environments. Named GraphSpy, the tool comes with a browser GUI.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at how states have very different views about manipulating the information environment aka "information warfare."




