Risky Biz News: Authorities take down Warzone RAT gang
In other news: New Ivanti bug exploited in the wild; a Fortinet zero-day; and Canada bans Flipper Zero devices.

This newsletter is brought to you by Proofpoint. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

An international law enforcement operation has led to the capture of two individuals believed to have created and operated Warzone RAT, a Malware-as-a-Service operation that has been running since at least 2019.
Authorities have detained Daniel Meli, a 27-year-old from Malta, and Prince Onyeoziri Odinakachi, a 33-year-old from Nigeria.
Meli allegedly created and sold the Warzone RAT through its official website at warzone.ws. Odinakachi allegedly worked as a customer support, providing help to the malware's buyers.
Officials say Meli has been allegedly involved in the malware underground since at least 2012 and also created and sold Pegasus RAT, a precursor of the Warzone RAT.
The two suspects were charged in the US in December of last year, and both were detained on the same day, on February 7, last week.
On the same day, the FBI, working together with law enforcement from several countries, also seized the gang's official website and servers that hosted Warzone RAT backend infrastructure.
US officials are now working to have the two extradited so they can face charges for their alleged crimes in the US. Meli has already consented to his extradition to the US, according to Malta Today.
The FBI also put up a website where victims who were infected with the Warzone RAT can file complaints against the two and their accomplices.
Also known as Ave_Maria, the Warzone remote access trojan was nothing particularly special in the world of malware. It contained all the features you'd expect in a remote access trojan and was in the mid-range pricing scheme of similar tools. If you'd like to know more, the Malpedia database has a collection of reports on the malware itself or the campaigns it was used in.

Breaches, hacks, and security incidents
PlayDapp crypto-heist: Blockchain gaming platform PlayDapp has suffered a cybersecurity breach and lost an estimated $31 million worth of assets. The incident took place on Friday after an attacker gained access to the platform's backend infrastructure. According to blockchain security firm Cyvers, the attacker allegedly added their own address to the PlayDapp backend and minted new tokens that they immediately transferred to new wallets. [Additional coverage BeInCrypto]
Korneuburg ransomware attack: Funerals were canceled last week in the city of Korneuburg, Austria, after a ransomware attack hit the local municipality's network. Officials said the ransomware crippled all of its IT systems, and they couldn't issue death certificates. Locals also couldn't pay bills or taxes. [Additional coverage in Noen]
SouthState Bank hack: In an SEC filing, American bank SouthState disclosed that it suffered a cybersecurity incident on February 6, 2024.
Hyundai ransomware: Hyundai's Europe branch got hit by the Black Basta ransomware gang. [Additional coverage in BleepingComputer]
Wurk leak: Colorado PR firm Wurk leaked the personal details of 2.5 million users via a misconfigured MongoDB database. [Additional coverage in CyberNews]
Juniper leak: Juniper's customer support portal leaked customer data due to a recent upgrade. The issue has now been fixed, per the company. [Additional coverage in KrebsOnSecurity]
Extra Kyivstar hack details: Russian military hackers tried to destroy the software on mobile base transceiver stations during their attack on Kyivstar, Ukraine's largest telco. The attack took place in December of last year when the same hackers also wiped thousands of the company's servers. Kyivstar CEO Oleksandr Komarov says the hackers targeted more than 100,000 of its base stations. Komarov says that if this second part of their attack had succeeded, the telco would have been down for months instead of days. [Additional coverage in The Record]
General tech and privacy
Huawei raided in France: French authorities raided Huawei's French offices this week on "suspicion of improper behaviour" during an ongoing investigation by France's financial prosecution service (PNF). [Additional coverage in Le Monde]
Grammarly layoffs: Online writing assistant company Grammarly has laid off 230 of its estimated 1,000 workforce.
New Mozilla CEO: Mozilla has named Laura Chambers as its new CEO. Chambers previously served as a Mozilla board member for the past three years. She takes over the position from Mitchell Baker, who served as CEO since 2020. Baker leaves after mounting backlash over her huge salary, which doubled since she took over while the Firefox browser lost massive market share.
DT BGP update: Deutsche Telekom will drop BGP routes that do not pass RPKI validation. The German telco expects to implement this new filtering rule during the first quarter of the year. The company was not clear if it plans to drop BGP routes from companies that don't RPKI sign their routes at all.
Clearview AI: Facial recognition company Clearview AI has continued to collect millions of images of Australian citizens even if the company was told to stop by the country's privacy regulator. The company's disregard for the Office of the Australian Information Commissioner's decision comes as the Australian Federal Police has continued to contract its services for crime-solving efforts.
Government, politics, and policy
FTC makes AI-generated robocalls illegal: The Federal Communications Commission has voted to make the use of AI-generated voice in robocalls illegal. Unsolicited robocalls are already illegal in the US. The new ruling gives US prosecutors new legal avenues to go after robocallers just for using AI-generated voices. The agency says robocalls using cloned voices have escalated over the past years. Scammers have used AI technology to clone the voices of family members, celebrities, and politicians to defraud users.
FTC US fraud numbers: Americans lost more than $10 billion to fraud in 2023. The US Federal Trade Commission says this is the first time fraud losses surpassed the $10 billion mark since it began tracking the stats. Investment fraud and imposter fraud accounted for most losses, with $4.6 billion and $2.7 billion, respectively.
AISIC: The US government has launched the AI Safety Institute Consortium (AISIC), a consortium of public and private sector entities dedicated to the safe development of AI technologies. More than 200 organizations have signed up to AISIC. Founding members include Microsoft, Google, Meta, OpenAI, Apple, Amazon, and Nvidia.
Ukraine Cyber Diplomat post: Ukrainian officials are considering creating a post of "cyber diplomat" to represent the country's interests in cyberspace. [Additional coverage in Kyiv Post]
Russia goes after bloggers: The Russian government is creating a blacklist of Russian bloggers who are active on YouTube but not on Russian social networks. Officials said the list is meant to encourage bloggers to move to domestic platforms. They also claimed Russians active on foreign "extremist" platforms are either trying to hide their income or conducting enemy activities. [Additional coverage in TASS]
Surveillance in Tibet: Chinese authorities are forcing Tibet residents to install an app named "National Anti-Fraud Centre" on their smartphones. The app has the ability to access call and SMS logs, read browser histories, and see what other apps are installed on a device. Pro-Tibet privacy groups say that the app could be used as a surveillance system to spy on China's Tibetan population. A similar system with government-mandated mobile apps is also used to track the Uyghur minority in China's Xinjiang province. [Addition coverage in Turquoise Roof and Tibet Watch's joint reports]
Canada bans Flipper Zero: The Canadian government has banned the importation, sale, and use of electronic devices that can be used to intercept wireless signals and steal cars. The ban applies to devices like the Flipper Zero, a tool developed for radio and pen-testing enthusiasts. Flipper Zero was the only device listed by name in the Canadian government's press release. Multiple tutorials are available online showing how the device can be used to unlock cars. There are no confirmed cases of the device being used in proven car thefts. [Additional coverage in PCMag]
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Proofpoint Senior Threat Researcher Greg Lesnewich. Greg explains how a North Korean group is using DMARC spoofing in its efforts to gather strategic intelligence.

Cybercrime and threat intel
New npm malware: Seventeen malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
January crypto-thefts: According to blockchain tracking service ScamSniffer, threat actors are believed to have stolen roughly $55 million worth of crypto assets through phishing in the month of January alone.
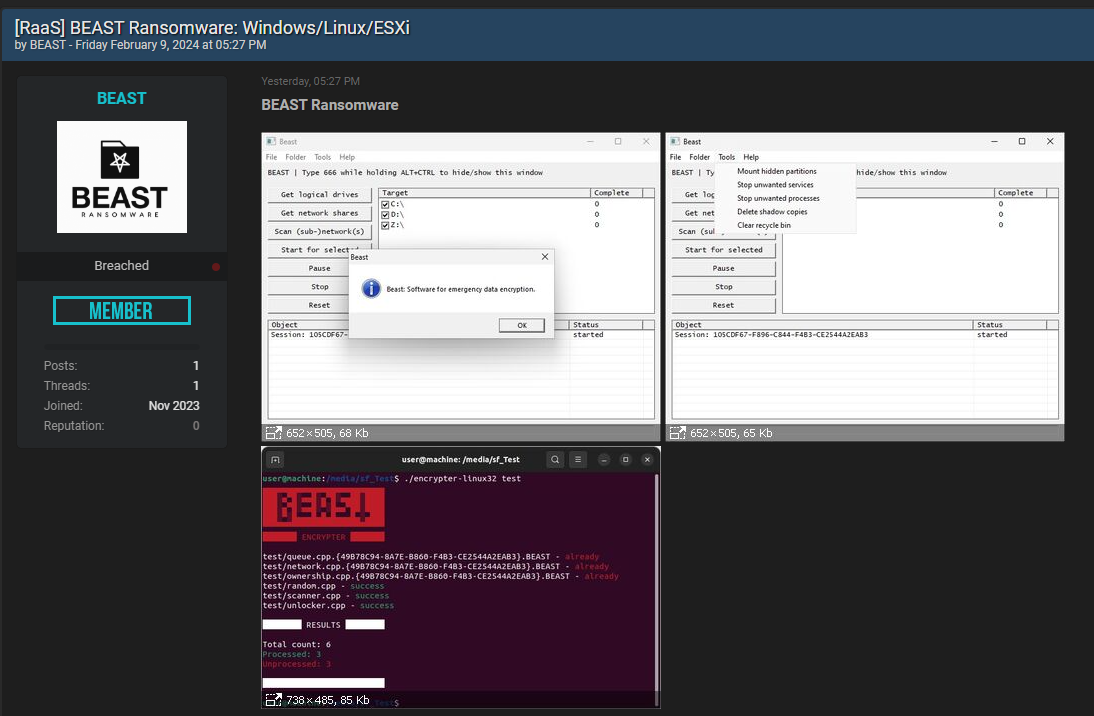
New Beast RaaS: A threat actor is advertising a new Ransomware-as-a-Service platform named Beast on underground hacking forums. [h/t Chum1ng0]
Malware technical reports
RustDoor: Bitdefender researchers have found a new macOS backdoor written in the Rust programming language. Named RustDoor, the malware appears to share some infrastructure overlap with the AlphV ransomware operation, although there's no evidence to suggest the malware was coded or is operated by the gang.
Sponsor Section
Ryan Kalember shows Risky Business host Patrick Gray Proofpoint's Sigma platform. Sigma is a data loss prevention and insider threat detection tool that crunches data from different sources and presents a unified view.
APTs, cyber-espionage, and info-ops
Midnight Blizzard Microsoft hack: Cloud security firm Wiz published an analysis of how the Midnight Blizzard Russian APT breached Microsoft's infrastructure. A similar report is also available from SpecterOps.
Sticky Werewolf: Russian security firm looks at a Sticky Werewolf campaign targeting Belarusian companies with the Ozone RAT.
ShadowPad infrastructure: Hunt.io researchers have identified 16 new servers hosting new ShadowPad infrastructure.
Vulnerabilities, security research, and bug bounty
New Ivanti bug exploited in the wild: Threat actors are exploiting a new vulnerability in Ivanti Connect Secure VPN appliances. Tracked as CVE-2024-22024, the vulnerability allows an attacker to access certain restricted resources without authentication. Attacks began hours after Ivanti patched the bug and after watchTowr Labs published details about the vulnerability. Proof-of-concept code is already available on GitHub. It is the fourth exploited bug in Ivanti Pulse Secure devices over the past month. The first three Ivanti bugs were linked to Chinese espionage campaigns. watchTowr researchers say the bug appears to have been introduced in recent versions of the software while Ivanti was trying to patch the first bugs.
Fortinet zero-day: Fortinet has released a security update for its FortiOS operating system to patch a vulnerability exploited in the wild. Tracked as CVE-2024-21762, the vulnerability is in the SSL VPN component. It is a pre-auth RCE that can be exploited using specially crafted HTTP requests. Fortinet says the vulnerability can be exploited even if the device's web management interface is disabled. Customers are advised to take down VPN appliances or disable the VPN component until patches are applied. The zero-day is one of four patches the company released on Friday.
Fortinet n-day exploitation: Fortinet looks at recent attacks targeting n-day vulnerabilities in its own products, namely CVE-2022-42475 and CVE-2023-27997.
ExpressVPN fixes DNS leak: ExpressVPN has deployed a fix to its Windows VPN client that was leaking DNS lookups in certain configurations. The company says leaks were occurring when customers were using the client's split tunneling feature. ExpressVPN credited CNET reporter Attila Tomaschek with discovering the issue.
Windows Sudo bugs: Google security researcher James Forshaw has disclosed several logical bugs in the Sudo for Windows utility that Microsoft announced just two days earlier.
Empire C2 flaw: BC Security has urged Empire C2 Framework users to update to v5.9.3 as soon as possible to fix a security flaw. The bug was discovered by ACE Responders. The company promised a technical blog and PoC, both to be published on its blog on February 15.
Exploits on GitHub: Security firm Prion has studied the prevalence of exploit code published on GitHub repositories between 2018 and 2023. Some of the main stats they compiled are below.
- Total number of exploit repos: 11068
- Year with most exploits: 2023, with 2804 repos
- Month with most exploits: December 2021 (Log4shell month)
Infosec industry
New tool—CTI.FYI: If you're looking for the latest entries published on ransomware leak sites, you can follow the CTI.FYI Mastodon and Bluesky accounts. A similar Mastodon account for this is Ransomlook.
New tool—LolCerts: WithSecure has put together a GitHub repo named LolCerts that tracks code signing certificates known to have been leaked or stolen, then abused by threat actors.
New tool—LoFP: Elastic's Justin Ibarra has launched a new project named LoFP (Living off the False Positive), a collection of the most common false positives. More details in this blog.
Election security: GreyNoise is looking for help in setting up honeypots that mimic voting machines and other election system software.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about what up-and-coming countries should expect from a Cyber Command and whether they should invest in it.





