Risky Biz News: Australia to hack the hackers
In other news: Microsoft blocks domain fronting; Russia sanctions infosec figures; FTX claims $473 million hack (among other things).
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Clare O'Neil, the Minister for Home Affairs of Australia, says the government is setting up "a permanent standing operation" that will "scour the world" and "hunt down the criminal syndicates and gangs who are targeting Australia in cyber attacks and disrupt their efforts."
In an interview with ABC Insiders, O'Neil said this new initiative would be a joint effort comprised of personnel from the Australian Federal Police (AFP) and the Australian Signals Directorate (ASD).
The Australian minister said the task force's first priority would be on ransomware cartels.
The focus on ransomware follows the recent ransomware attack on Australian private insurance provider Medibank. The company says attackers broke into its network, stole internal files—including sensitive personal and healthcare details on 9.7 million Australians—encrypted files, and demanded a ransom. When it refused to pay, the ransomware gang, going by the name of BlogXX, believed to be a spin-off from the infamous REvil ransomware operation, started leaking some of Medibank's patient records—as a form of intimidation and put public pressure on the company to pay the ransom.
One of the group’s first leaks was a file labeled “abortions”.
The group’s activities have been met with outrage and significant political attention from the highest levels of the Australian government.
"This is Australia standing up and punching back. We are not going to sit back while our citizens are treated like this way and allow there to be no consequences for that," O'Neil said.
"This is a new operation, a permanent standing force if 100 of the best most capable cyber experts in this country that will be undertaking this task for the first time. Offensively attacking these people [...] This is not a model of policing where we wait for a crime to be committed and then try to understand who it is and do something to the people who are responsible," O'Neil explained. "We are offensively going to find these people, hunt them down, and debilitate them before they can attack our country."
I have a message for all cybercriminals: Australia is fighting back.
— Clare O'Neil MP (@ClareONeilMP) 12:37 AM ∙ Nov 13, 2022
#Insiders
O'Neil's statement came on the same day that the AFP issued a press release identifying the Medibank hackers as being located "in Russia."
"We believe we know which individuals are responsible but I will not be naming them," said AFP Commissioner Reece Kershaw. "What I will say is that we will be holding talks with Russian law enforcement about these individuals."
After years during which law firms, cyber-insurance providers, and even security firms and law enforcement have closed their eyes during ransomware negotiations and allowed victims to pay ransom demands in order to placate attackers, these criminal cartels have grown their operations and intensified attacks feedings on profits but also on a sense of invincibility.
Cases where law enforcement agencies fought back and hacked the hackers have been very rare so far. Success stories include the DOJ recovering Colonial Pipeline's payment to the Darkside group and US CyberCom and the FBI both hacking REvil's servers following the Kaseya attack. Both Darkside and REvil shut down following these "offensive" operations.
Further to the announcement of the taskforce, O'Neil lauded Medibank's decision not to pay its attackers and suggested the government might look into a law banning ransomware and data extortion payments altogether, which the official hopes will strangle the financial incentive behind most attacks.
I want Australia to be the most cyber-safe country in the world. The payment of ransoms directly undermines that goal.
— Clare O'Neil MP (@ClareONeilMP) 7:12 AM ∙ Nov 7, 2022
Breaches and hacks
FTX claims hack: Cryptocurrency exchange FTX claimed that a hacker stole roughly $473 million worth of crypto assets from its accounts. FTX officials said the incident took place shortly after the company filed for bankruptcy on Friday, prompting the company to move all its funds to offline cold storage wallets. Shortly after this incident, Reuters discovered that another $1 billion (possibly $2 billion) worth of customer assets was also reported missing from the company's books—in what appears to be a separate incident.
DFX Finance crypto-heist: DeFi platform DFX Finance said it lost $4.185 million worth of cryptocurrency assets following an attack on its platform late last week. The company said the incident was identified as a reentrancy attack.
Sobeys ransomware incident: Canadian retail chain Sobeys said it was hit by a ransomware attack over the previous weekend that crippled IT systems across its grocery stores and pharmacies. Self-checkout stations, payroll management, gift card activation systems, and most backend services were all affected, according to public reporting. Despite the huge outage, the company's stores remained open as point-of-sale systems were unaffected and allowed the company to process payments unhindered. The attack was later linked to the Black Basta ransomware operation.
Whoosh breach: Hackers have leaked a data trove containing the personal details of more than 7.2 million users of Whoosh, an electric scooter company active across more than 45 Russian cities. Leaked data includes real names, phone numbers, and parts of their payment card number. [Additional coverage in Positive Technologies SecurityLab]
BAH breach: Intelligence services giant Booz Allen Hamilton disclosed a security breach last week to Montana's OAG, revealing that a former employee illegally downloaded a report containing his colleague's personal data from one of the company's internal SharePoint servers. See breach notification letter here [PDF].
General tech and privacy
Apple sued for ignoring privacy settings: After two app developers found that Apple was collecting data about all its users even if they checked the "disable the sharing of Device Analytics" option in the App Store settings, two class-action lawsuits were filed last week against the tech giant in California and Philadelphia, respectively.
Microsoft blocks domain fronting on Azure: Microsoft has notified customers that it intends to "block any HTTP request that exhibits domain fronting behavior" starting on November 8, 2023. Domain fronting is a technique used to configure servers in a way to allow online services to bypass internet censorship. The technique has been widely used by Telegram to bypass censorship in Russia and Iran. With Microsoft's decision, all three major cloud providers will have blocked domain fronting after both Google and Amazon Web Services blocked domain fronting back in 2018. Microsoft signaled it would crack down on domain fronting back in March 2021, but this week the company imposed a hard cut-off date for all its customers. A copy of the email Microsoft sent users last week is available here or in the image below (via @HackingLZ)
Government, politics, and policy
EU Cyber Defence: The European Commission proposed an action plan last week that would boost the EU's cyber defense capabilities and strengthen coordination and cooperation between civilian and military cyber-security organizations. The document also calls on member states to ensure EU cyber defense interoperability and coherence through common standards and asks the EU to develop "full-spectrum state-of-the-art cyber defense capabilities." For this, the European Commission urges the cultivation of a strong and agile European cyber defense industry and for states to address "a real and alarming cyber skills gap" in its current defense workforce—with the European Cybersecurity Organization (ECSO) estimating that a total of 500 000 professionals are needed now in 2022 to cover all available job openings.
My summary take on the CDP is that, the Commission essentially lost its creative direction and was noticably forced to focus on speed and replication. Case in point, many outlined CDP items are - in the end - NATO capability dublications, with little to no added value.
— Stefan Soesanto (@iiyonite) 1:16 PM ∙ Nov 11, 2022
Switzerland sees main "cyber threat" coming from ransomware: In its annual threat assessment report, the Swiss government said last week that it sees cybercrime, and specifically ransomware, as the main cyber threat to the country's critical infrastructure, as opposed to state-backed APT groups.
"So far, the war in Ukraine has confirmed that in the context of armed conflicts, cyber means are above all used in a support function. They aim to reduce the adversary's military capabilities and damage critical infrastructure. Given international interdependencies, such cyberattacks can also cause collateral damage and therefore indirectly affect Swiss facilities."
Russian sanctions 200 US citizens: The Russian government has sanctioned 200 US citizens for their support of the Ukrainian government. Among the list of sanctioned Americans, who are now forbidden from entering Russia, there are also several infosec figures, such as Dmitri Alperovich, co-founder of Crowdstrike and founder and chairman of the Silverado Policy Accelerator, Chris Krebs, former CISA head and co-founder of the Krebs Stamos Group, and Jen Easterly, CISA's current director.
NSA recommends memory-safe languages: The US National Security Agency issued guidance on Friday, recommending that developers and organizations look into using memory-safe languages when coding new applications as a way to avoid common "poor memory management issues" that could allow threat actors to exploit their software and abuse or steal user data. Examples of memory-safe languages listed in the guidance document include C#, Go, Java, Ruby, Rust, and Swift. Several major tech companies, like Microsoft, Google, and Mozilla, have long promoted the use of Rust as a C and C++ alternative. NVIDIA is also a known case where the company ditched C and C++ for a memory-safe language named SPARK.
Sponsor section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
Cybercrime and threat intel
State of Massachusetts sued: The Massachusetts Law Reform Institute, a nonprofit organization, has sued the state of Massachusetts on behalf of thousands of low-income families who had funds stolen from their food assistance benefits after they used their SNAP debit cards on ATMs compromised with card skimming devices. The goal of the lawsuit was to force the state to reimburse victims of SNAP card skimming, something the US Department of Agriculture (USDA), which funds the food assistance SNAP cards program, does not allow under the current rules, even for victims of obvious cybercrime. [Additional coverage in KrebsOnSecurity]
Sextortion hits a new low: The FBI has reported that a "high rate" of teenage boys are committing suicide after being the targets of sextortion attempts, with some victims taking their lives sometimes within hours of receiving the sextortion message. Even worse, the FBI also reported that in some cases, criminals contacted families and requested payment, threatening to release the deceased's nudes online. [See original Forbes report]
Mastodon abuse: You're not a true social network until someone uses your infrastructure for C2 comms. Mastodon: ✅
Attacks on US midterm elections infrastructure: Internet infrastructure company Cloudflare—which provides free services to state and local governments through the Athenian Project and to political campaigns through the Cloudflare for Campaigns programs—published a summary of what threats the company saw directed at these two projects over the last month and through the US midterm elections. Long story short, while some attacks were detected and mitigated, there was no super major cyber-attack that tried to compromise websites or disturb the US electoral process.
17 scam domains seized: The FBI and the US Postal Inspection Service seized 17 websites that were part of a large-scale fraud operation. The websites posed as recruiting portals for work-at-home jobs, where US citizens were tricked into receiving stolen goods or stolen money and asked to reship the products or funds to another address controlled by the scammers. Officials said the operation had been going on since February 2021 and that hired applicants were paid $20 for each reshipped package.
Malware technical reports
KmsdBot: Akamai's security team said it discovered a new botnet named KmsdBot. The company said this new botnet is written in the Go programming language, spreads by targeting systems that use weak SSH login credentials, and currently focuses on mining the Monero cryptocurrency.
Somnia ransomware: Ukraine's CERT team has released details and IOCs about a new strain of ransomware—named Somnia—deployed in recent attacks against Ukrainian organizations. CERT-UA officials said they linked the malware to a group of Russian hackers known as FRwL (aka Z-Team), which the agency tracks as UAC-0118.
Inlock and Xorist ransomware: Fortinet researchers have published a write-up on two new ransomware variants known as Inlock and Xorist.
Free decrypter: Bitdefender released a free decrypter for the RanHassan ransomware, allowing victims to recover their files without paying the attackers. K7Security Labs has a technical analysis of the RanHassan (also known as DCDcrypt) here.
APTs and cyber-espionage
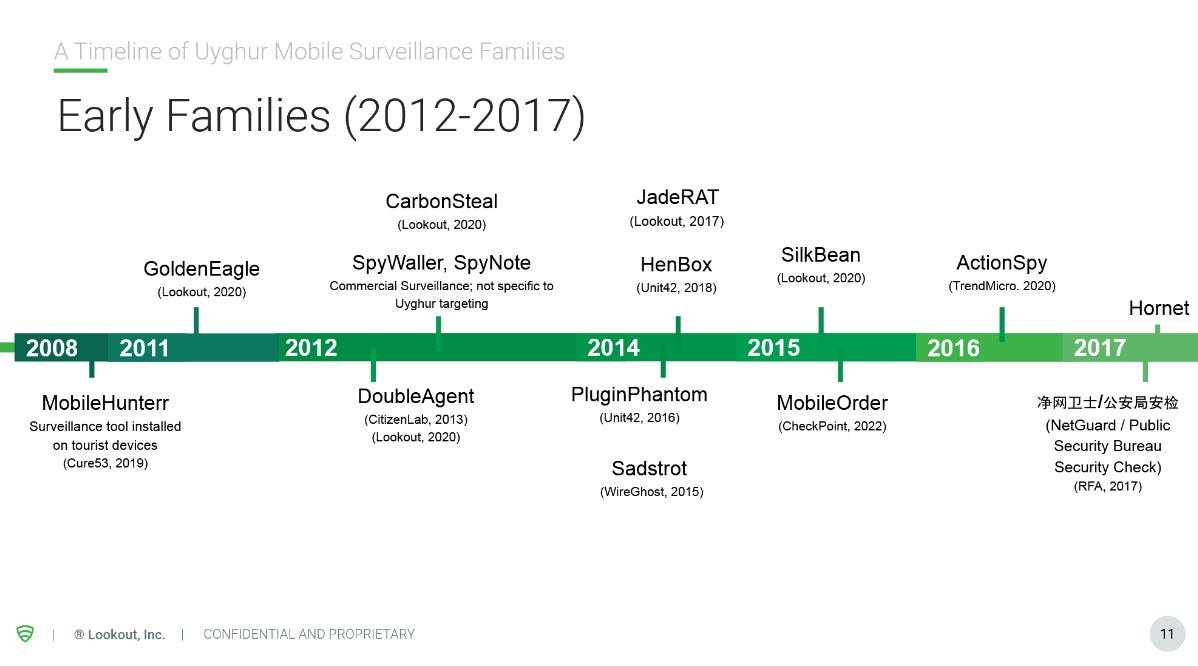
BadBazaar: Security firm Lookout said it identified two suspected Chinese government surveillance operations that targeted its minority groups throughout the past years. The first campaign targeted Uyghurs and other Turkic ethnic minorities in China and abroad using a novel piece of malware known as BadBazaar, while the second campaign used spear-phishing messages on WhatsApp to infect Tibetan activist groups with malware known as Moonshine. Lookout said they linked the first campaign to a group known as APT15 (or Vixen Panda), while evidence suggested the second campaign was carried out by a group known as Poison Carp (or Evil Eye). Extensive previous reporting links both groups to the Chinese government. More in the company's CyberWarCom slides, including some cool timelines.
Vulnerabilities and bug bounty
GitHub private vulnerability reporting: Code-hosting platform GitHub has added a new feature to its service to allow security researchers to report vulnerabilities in public repositories to their respective owners via a private channel. The new feature will allow sensitive security-related reports to be filed to repo owners without having to file a publicly-viewable entry in a repo's Issues Tracker. Instructions on how repo owners can enable this feature are here.
CVE-2022-32895: Trend Micro has published a write-up on CVE-2022-32895, a vulnerability in the macOS PackageKit Framework that can be used by malicious apps to modify protected parts of the file system. The vulnerability is a variation of the older CVE-2019-8561 vulnerability.
"Users who fail to update their operating systems can be vulnerable to root privilege escalation, signature bypassing, and SIP bypassing. It is therefore imperative for users to install all updates to keep their systems secure."
LiteSpeed server vulnerabilities: Palo Alto Networks' Unit42 security team has published details about three vulnerabilities in the LiteSpeed open-source web server. The three bugs include an RCE, a privilege escalation, and a directory traversal issue.
Infosec industry
Infosec's Mastodon: Infosec.exchange has turned out to be the favorite Mastodon instance to where most security researchers have migrated to. As a result of the sudden influx of thousands of new accounts, the team behind the servers is looking for moderators and support staff. Donations are also currently needed and encouraged. More info about the instance can be found on its wiki.
Vitali Kremez fundraiser: A GoFundMe page has been created to help the family of Vitali Kremez, the late CEO of Advanced Intelligence, with funeral costs. Vitali died earlier this month during a scuba diving trip. His company also issued a statement here.
New tool—Canary Hunter: Optiv security researcher Curtis Ringwald open-sourced Canary Hunter, a red-team tool meant to detect canary tokens installed across an organization's network or files.
New tool—Shufflecake: The team at Kudelski Security has open-sourced a new tool named Shufflecake that can be used to "create multiple hidden volumes on a storage device in such a way that it is very difficult, even under forensic inspection, to prove the existence of such volumes." Researchers said they developed this tool for "people whose freedom of expression is threatened by repressive authorities or dangerous criminal organizations," such as activists, whistleblowers, and journalists.




