Risky Biz News: Apple's Lockdown Mode scores first major win against iOS zero-days
In other news: Microsoft overhauls APT naming scheme; Iranian APT goes after US critical infrastructure; RedLine Stealer malware servers temporarily disrupted.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Apple's Lockdown Mode security feature has been confirmed to have blocked the execution of a new iOS 16 zero-day exploit.
According to a new CitizenLab report, the zero-day was developed by Israeli company NSO Group and was used in attacks last fall against members of Mexico's civil society investigating the Mexican Army's extrajudicial killings and disappearances.
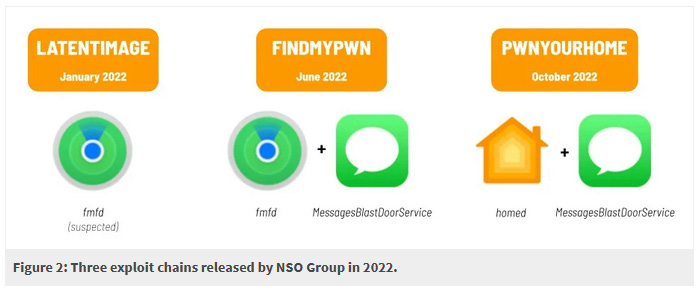
The new exploit is named PwnYourHome and was deployed against both iOS 15 and iOS 16 devices. On iOS 16, where Apple's new Lockdown Mode is available, CitizenLab says targets received real-time warnings when the exploit was executed.
Besides PwnYourHome, CitizenLab says the same campaign also used two other exploits named FindMyPwn and LatentImage. Both of these targeted iOS 15, so Lockdown Mode wasn't available to protect users.
Apple launched Lockdown Mode in the fall of last year for both iOS and macOS.
The company described Lockdown Mode as an "extreme and super-secure protection mode" where iOS and macOS turn off internal services and features that are commonly abused by threat actors.
In a call with Apple before the launch, the company's security team told Risky Business they designed Lockdown Mode specifically to protect high-risk individuals who are regularly targeted with zero-days and advanced spyware.
Following CitizenLab's recent report, we presume the people in Apple's security team have huge grins on their faces right now.
The Lockdown Mode feature is disabled by default. If you think you may be a possible target for advanced high-grade zero-days and spyware, you can see this support page on how to turn it on.
Breaches and hacks
CommScope ransomware attack: CommScope, one of the world's largest manufacturers of networking equipment, has suffered a ransomware attack at the hands of the Vice Society ransomware gang. Data containing the personal information of thousands of employees was published on the gang's dark web portal this week. CommScope confirmed the incident, which allegedly took place at the end of March. [Additional coverage in TechCrunch]
Evide ransomware attack: Evide, a company that provides IT servers to charities and non-profits across the UK, has suffered a ransomware attack. The ransomware gang is believed to have accessed the personal data of some of its customers, including four Irish organizations that deal with victims and survivors of rape and sexual abuse. RTE News reports Evide does not intend to pay the requested ransom demand.
General tech and privacy
DDoS protections for top Apex players: Respawn Entertainment has added DDoS protections to servers hosting games for its top-tier Apex Legends ranks such as "Predator," "Master," and "Diamond." Lobbies hosting games for high-ranked players have been regularly under DDoS attacks, causing games to crash and the top players to lose ranking points.
Open letter to UK government: A group of executives from several E2EE messaging apps, including Signal, WhatsApp, and Threema, signed an open letter asking the reconsider the current form of its Online Safety Bill. The group says that, as currently drafted, the Bill could be used to break end-to-end encryption and open the door to routine, general, and indiscriminate surveillance of personal communications.
"The Bill provides no explicit protection for encryption, and if implemented as written, could empower OFCOM to try to force the proactive scanning of private messages on end-to-end encrypted communication services - nullifying the purpose of end-to-end encryption as a result and compromising the privacy of all users.
In short, the Bill poses an unprecedented threat to the privacy, safety and security of every UK citizen and the people with whom they communicate around the world, while emboldening hostile governments who may seek to draft copy-cat laws."
Major Firefox update: Mozilla has released a new Firefox version that fixes a major bug that was wiping its users' cookie files.
Helicopter crash: An Australian military helicopter crashed because it missed a crucial software update. The world we live in!!!
Government, politics, and policy
CISA SBOM guide: CISA has published a guide on techniques and solutions for sharing SBOM files. CISA says the guide will be able to assist organizations in "choosing suitable SBOM sharing solutions based on the amount of time, resources, subject-matter expertise, effort, and access to tooling that is available to the reader to implement a phase of the SBOM sharing lifecycle."
Predator in Sudan: Greece's main opposition leftist Syriza party has asked the ruling government if it allowed the export of the Predator spyware to Sudan, a country currently on the verge of another civil war.
Hikvision in the Pentagon Leaks: In documents part of the recent Pentagon Leaks, the US intelligence community has described Chinese security camera maker Hikvision as "partnering with Chinese intelligence entities" and actively working to distribute white-labeled equipment to US government agencies in order to create vectors for future breaches. In a response to the BBC, Hikvision denied it was disguising its cameras as white-label brands but did not answer if it was working with Chinese intelligence.
Russian disinformation: In documents part of the recent Pentagon Leaks, the US government seems to be very aware of Russia's ongoing disinformation operations. According to one of the documents, US intelligence officials learned that a Russian government agency boasted about its ability to carry out influence operations, claiming it runs hundreds of thousands of fake online accounts, of which only 1% get detected and banned. According to the Washington Post [non-paywall], the agency bragged about spreading lies about Ukraine's military and spreading fake news about the side effects of vaccines.
"The undated analysis of Russia's effectiveness at boosting propaganda on Twitter, YouTube, TikTok, Telegram and other social media platforms cites activity in late 2022 and was apparently presented to US military leaders in recent months."
Smart cameras come to bite Russians: The Russian government has announced plans to use facial recognition and smart cameras installed across Moscow to identify and track down individuals that are avoiding the Russian army's latest conscription round. Set into motion at the start of the month, this latest draft is the first one where individuals are set to receive their summons via electronic means such as email and SMS.
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
Ryuk money launderer gets light sentence: A Russian national who laundered money for the Ryuk ransomware gang has received a very light sentence from US authorities. According to court documents, Denis Dubnikov was sentenced to time served and will only have to pay a small $2,000 forfeiture. Dubnikov was arrested in the Netherlands and extradited to the US in November 2021. He pleaded guilty this February to laundering more than $400,000 of ransom proceeds for the Ryuk ransomware gang.
RedLine disruption: ESET and GitHub have disrupted the backend panels of the RedLine infostealer. ESET says it identified four GitHub repositories the RedLine malware was using to authenticate operators when logging into backend admin panels. GitHub has taken down the four repositories, which has resulted in cybercrime operators who bought access to the RedLine malware from being unable to access their backends. ESET says this is a temporary disruption and that the RedLine crew will most likely distribute an update to fix the broken authentication mechanism.
Shadow Force group: South Korean security firm AhnLab has published a report analyzing the recent attacks of Shadow Force, a cryptocurrency-mining group that has been active since 2013. The report covers the group's activity between 2020 and 2022, its recent coinminer payloads, and its latest Viticdoor backdoor.
ChatGPT account trade: Threat actors are using brute-force attacks to hack and take over ChatGTP premium accounts. According to security firm Check Point, the accounts are sold in underground markets and are typically bought by other threat actors who want to get around OpenAI's geofencing restrictions and get unlimited access to ChatGPT for malicious purposes. Check Point says the trade in hacked ChatGPT accounts began last December, and they saw an increase in activity and interest in March this year.
New npm malware: Mend researchers have spotted a new malicious npm library that contains a hidden infostealer.
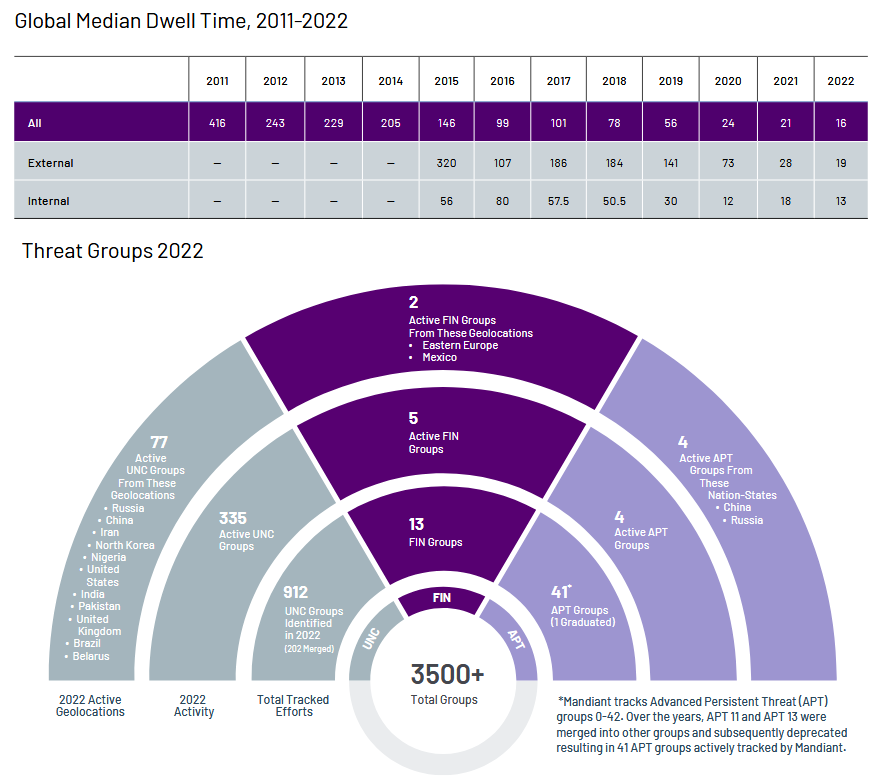
Mandiant M-Trends report: The median dwell time of an attacker inside a compromised network went down to 16 days last year, according to M-Trends 2023, a report compiled by Mandiant from data from its frontline incident response teams. The number has gone down from 21 days in 2021 and down from 416 days in 2011, suggesting companies have gotten better at detecting threat actors inside their networks. Mandiant's dwell time is similar to the 11-day dwell time reported by Secureworks in its own yearly report, published last October. The Mandiant report also covers other topics, such as initial access (with vulnerability exploitation and phishing being top entry points) and top malware families (where Cobalt Strike was king with 15% of all detections).
Old decommissioned routers expose corporate secrets: A study conducted by ESET has found troves of sensitive corporate data on old decommissioned routers sold on the second-hand market.
- 22% contained customer data
- 33% exposed data allowing third-party connections to the network
- 44% had credentials for connecting to other networks as a trusted party
- 89% itemized connection details for specific applications
- 89% contained router-to-router authentication keys
- 100% contained one or more of IPsec/VPN credentials, or hashed root passwords
- 100% had sufficient data to reliably identify the former owner/operator
ANY.RUN Q1 2023 review: According to ANY.RUN's quarterly report, the RedLine infostealer was the most analyzed malware on its platform during Q1 2023.
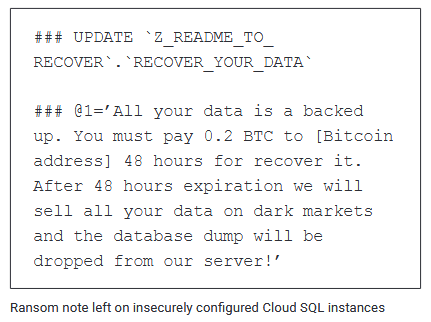
Ransomware hits GCP: Google says that in September of last year, a threat actor compromised a small number of MySQL databases hosted on its cloud service, encrypted data, and then asked for a ransom. Google says the attacks took place because the database servers were misconfigured, likely with weak passwords or no passwords at all. More in the company's Threat Horizons report [PDF].
Malware technical reports
Dark.IoT: QiAnXin researchers say they've spotted a new version of the Dark.IoT botnet. This one appears to be using Pastebin and ClouDNS as part of its C&C system.
DevOpt: Zscaler has discovered a new malware strain named DevOpt. The malware was discovered on a website offering monetary rewards to Russian-speaking visitors. Zscaler says the malware is still in development but already has advanced capabilities to function as a keylogger, stealer, grabber, and clipper.
QBot: Kaspersky says it has seen a "significant increase" in QBot campaigns in early April. The company has a report on QBot's latest tactics.
Raspberry Robin: Check Point researchers have an analysis of the recent evasion and anti-debug tactics used by the Raspberry Robin worm.
PrivateLoader: The ANY.RUN team has a technical breakdown of the PrivateLoader malware strain.
XORStringsNet: OALABS researchers published an analysis of XORStringsNet, an open-source crypter that has been recently adopted by various malware operations.
Aurora Stealer: Morphisec has published research on the Aurora Stealer, a popular Go-based infostealer that's often used by low-grade cybercrime operators. The report covers the new attack delivery chain they are tracking as "in2al5d p3in4er."
LockBit for macOS: Patrick Wardle has a breakdown of LockBit's new macOS ransomware variant. For now, the LockBit's macOS variant is just a test and not that good or any kind of credible threat.
Money Message ransomware: Chinese security researchers with the Anheng Hunting Labs have published a technical analysis of the new Money Message ransomware strain.
BabLock (aka Rorschach) ransomware: Trend Micro has published an analysis of the BabLock (aka Rorschach) ransomware.
Trigona ransomware goes after MSSQL servers: South Korean security firm AhnLab has seen the operators of the Trigona ransomware break into poorly secured MSSQL servers to encrypt files and request ransoms from their victims. AhnSec says the databases used simple passwords and were also compromised by other threat actors with remote access trojans and cryptocurrency miners. The Trigona ransomware launched in June 2022 and is mostly known for accepting payments only via Monero. According to reports from Zscaler and Palo Alto Networks, the group intensified its activity earlier this year.
Sponsor Section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year, in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
APTs and cyber-espionage
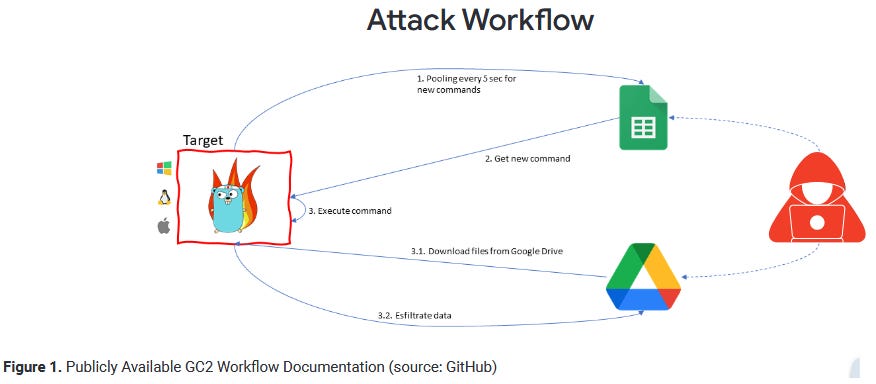
HOODOO disruption: Google says that in October of last year, its security team disrupted a campaign of the HOODOO (APT41) Chinese cyber-espionage group that abused Google services to target a Taiwanese media organization. The final payload in these attacks was an open-source red team tool named "Google Command and Control." The tool is written the Go programming language and is somewhat unique because it retrieves commands to execute on an infected host from an online Google Sheets document and then sends exfiltrated data to a Google Drive account. More in the company's Threat Horizons report [PDF].
APT28: UK and US cybersecurity authorities have linked a series of attacks against Cisco routers in 2021 to APT28, a hacking unit part of Russia's GRU military intelligence agency. The attacks exploited a vulnerability (CVE-2017-6742) in the SNMP interface of Cisco routers to execute code and install a malware strain named Jaguar Tooth [PDF]. US and UK officials say victims included a small number of European and US government institutions and approximately 250 Ukrainian organizations.
Mint Sandstorm: Microsoft says that Iranian state-sponsored hackers have moved from reconnaissance operations to the direct targeting of US critical infrastructure, potentially in support of future destructive operations. The attacks took place between late 2021 to mid-2022 and were carried out by a sub-group of Mint Sandstorm, an Iranian hacking group also known as APT42, Charming Kitten, or Phosphorus, and officially linked to Iran's Islamic Revolutionary Guard Corps. According to Microsoft, compromised entities included seaports, energy companies, transit systems, and a major US utility and gas entity. The attacks consisted of highly-targeted phishing campaigns and the exploitation of recently patched vulnerabilities in common enterprise applications, usually by adopting publicly available PoC exploits as soon as they are released online. Gear exploited in attacks includes the Zoho ManageEngine, IBM Aspera Faspex, and Apache Log4j.
MuddyWater: Group-IB analysts discovered new MuddyWater APT infrastructure while researching the group's recent abuse of SimpleHelp, a legitimate remote access toolkit that the gang has been installing on compromised networks to connect and exfil data. SimpleHelp marks the fourth legitimate remote access toolkit abused by the gang. Over the last few years, MuddyWater has also abused tools like ScreenConnect, RemoteUtilities, and Syncro.
APT36: Uptycs has a report on the Linux malware used by the APT36 (Transparent Tribe) suspected Pakistani cyber-espionage group.
Kimsuky: AhnLab says Kimsuky activity tripled during February 2023.
Attacks linked to Lazarus: South Korea's police agency has linked the attacks against INISAFE Cross Web EX systems to North Korea's Lazarus APT. The attack compromised 210 computers at 60 organizations earlier this year. South Korean officials claim Lazarus wanted to execute a large-scale attack on local organizations.
APT-C-36 (Blind Eagle): Qihoo 360 and ThreatMon have published reports on the recent operations of the APT-C-36 threat actor. The group's main targets are located in Colombia, as well as other South American countries, such as Ecuador and Panama.
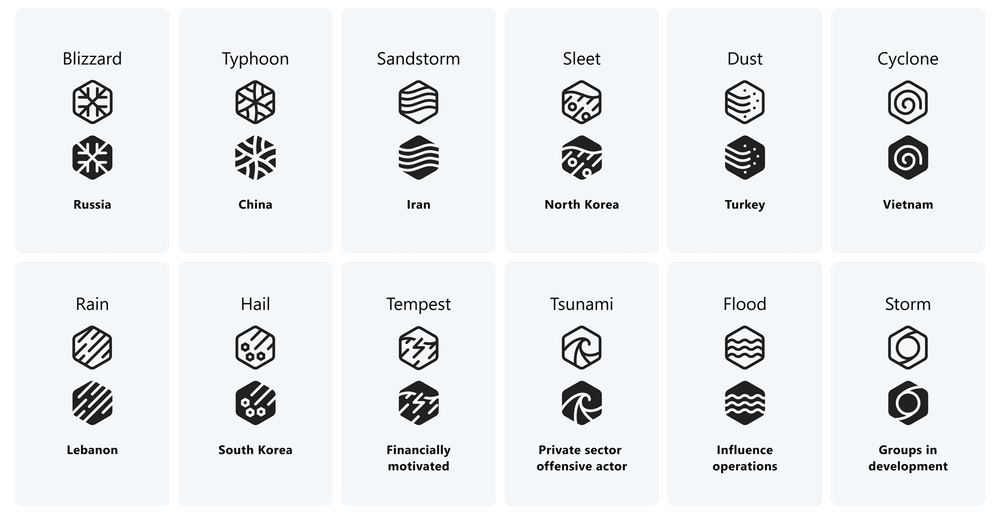
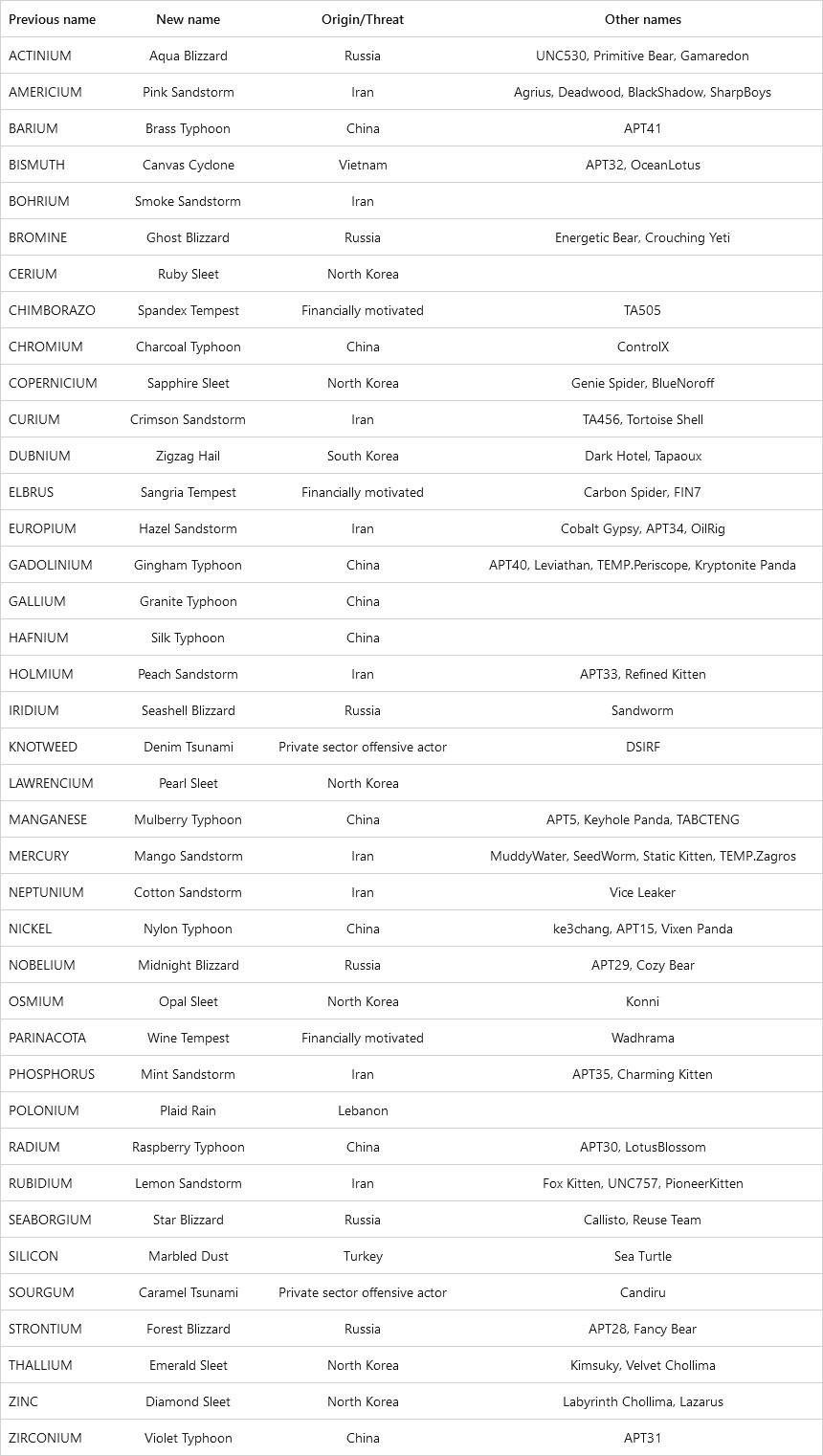
New Microsoft naming scheme: Microsoft's security team has overhauled its threat actor naming scheme. The company has moved away from using chemical elements, trees, and volcanos for the names of state-sponsored actors, surveillance vendors, and cybercrime groups. The move comes after the cybersecurity community has complained that it's hard to find Microsoft's research on a particular threat actor because of the vague names that often result in generic search results on unrelated topics. Microsoft's new naming scheme will now include a combination of a color name and a weather phenomenon for threat actor names. Existing threat actors have all received new names, listed in the table below and on this page.
Vulnerabilities and bug bounty
Security Research Legal Defense Fund: Google and several legal experts have set up a non-profit organization that will provide a legal defense fund for security researchers who are sued or prosecuted for pursuing good-faith security research. The non-profit will not provide direct legal representation to researchers but will provide grants for legal expenses. [Additional coverage in SC Magazine]
Crypto-wallet vulnerability: Blockchain security firm SlowMist says that the WalletConnect feature in many mobile app cryptocurrency wallets can be abused for phishing attacks. Researchers say an attacker can abuse the WalletConnect feature to trigger popups in various areas of an app that can ask users to sign malicious transactions that exfiltrate their funds.
Kerio Mailbox takeover: Security researcher Jokūbas Arsoba has found a simple account takeover vulnerability in KerioConnect mailboxes that can be abused just by sending a malicious file to the desired target.
QueueJumper: Check Point's Haifei Li has published an analysis on QueueJumper (CVE-2023-21554), an RCE vulnerability he discovered in the MSMQ (Microsoft Messaging Queuing) service.
"The CVE-2023-21554 vulnerability allows an attacker to potentially execute code remotely and without authorization by reaching the TCP port 1801. In other words, an attacker could gain control of the process through just one packet to the 1801/tcp port with the exploit, triggering the vulnerability. [...] Surprisingly, we found that more than ~360,000 IPs have the 1801/tcp open to the Internet and are running the MSMQ service."
Infosec industry
Duncan McAlynn: The cybersecurity community mourns the passing of Duncan McAlynn, a 20-year veteran of the infosec industry.
Acquisition news: Cybersecurity firm ZeroFox will acquire threat intel and external attack surface management company LookingGlass for $26 million in stock.
New tool—Spoofy: SeatGeek AppSec engineer Matt Keeley has open-sourced Spoofy, a new tool that checks if a list of domains can be spoofed based on SPF and DMARC records.
New tool—PASTIS: Security firm QuarksLab has open-sourced PASTIS, a new collaborative (ensemble) fuzzing framework.
Tool update—BloodHound: SpecterOps has released v4.3 of the BloodHound red team toolkit.
New open jobs: Amnesty International is looking for two security experts to track spyware companies and spyware attacks against activists and journalists.
OWASP open letter situation: In February this year, a group of OWASP members sent an open letter to their leadership team, asking the organization to change its funding model and governance structure. Immersive Labs' Robert Klentzeris published an analysis of the OWASP's response and analyzed the possibility of a mass exodus of OWASP members to other projects.
"In reality, this response leaves a lot to be desired and in no way has cemented the future direction of OWASP as a foundation. [...] It's likely an exodus is coming, but that's not always a bad thing. And for the wider application security community, this could be the start of a new era with a symbiotic relationship between new and old communities that both flourish in their respective missions. Growth comes from change, and as an interested party, I hope we don't lose this opportunity to make the AppSec space even stronger."




