Risky Biz News: Apple to encrypt iCloud backups, support third-party security keys
In other news: Iranian data wiper hits diamond industry; security firm blames hack on rival security firm; CISA Director faces ethics complaint.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Apple users got an early holiday gift from the company, which announced on Wednesday that it was adding three new security features to its services.
None of the features are neither new or groundbreaking, but they're something that privacy and security professionals have been asking Apple to roll out for years.
The first feature is named iMessage Contact Key Verification, and this works by showing alerts inside encrypted iMessage conversations whenever a new device is added to a participant's account. Apple hopes the feature will alert users whenever a threat actor gains access to an Apple account and tries to surreptitiously spy on ongoing conversations.
The second is named Security Keys for Apple ID, and just like its name implies, Apple will now allow you to use hardware-based security keys to secure Apple ID accounts. This is genuinely good news, as hardware security keys are considered one of the most secure forms of 2FA today. The other good news—Apple says that 95% of its Apple ID users have a form of 2FA enabled, which puts the company in the same rarified air of 2FA adoption, right next to Google.
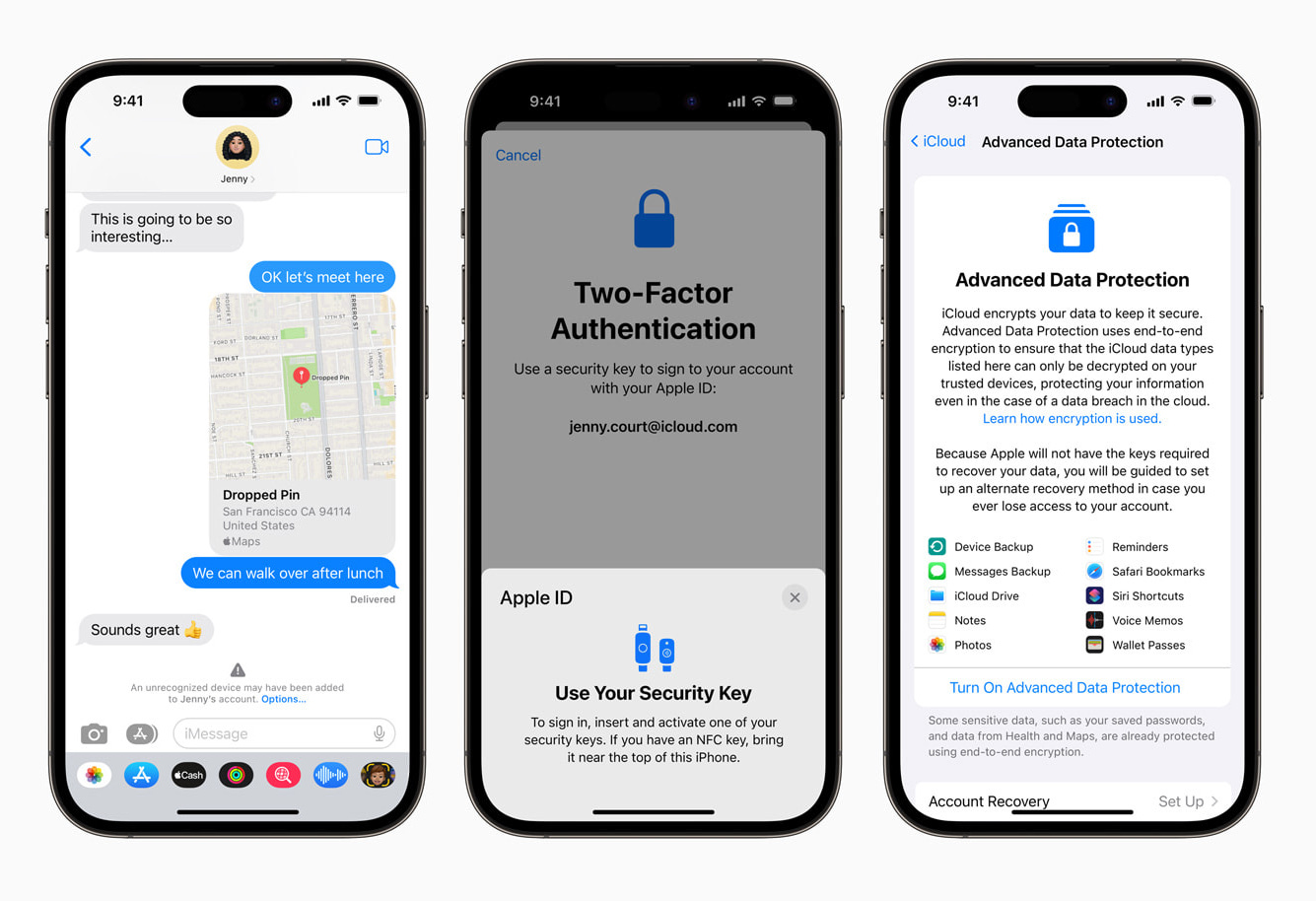
Finally, the third and most positively welcomed feature is Advanced Data Protection for iCloud, which lets users encrypt their iCloud data, including iCloud Backup, Photos, Notes, and others. According to an Apple documentation page, 23 different iCloud data categories can be encrypted.
The feature is also opt-in, so users will have to manually enable it.
Furthermore, Advanced Data Protection for iCloud uses an end-to-end encryption (E2EE) scheme, meaning there's a chance that if you lose access to your devices, you may lose all your encrypted backups and their respective data.
This new feature, in particular, is bound to generate the most drama out of the three. Why? Because Apple won't be able to access or decrypt this data anymore, which puts the company on a direct and fast-tracked collision line with law enforcement agencies all over the world. Will it cause problems for the company? We don't know, but Meta, which rolled out encrypted backups for WhatsApp more than a year ago, doesn't seem to have had any major tussles with law enforcement on the topic so far.
Until now, iCloud data has been "one court order away" from law enforcement investigations, as Albert Fox Cahn, Executive Director of the Surveillance Technology Oversight Project, said in a statement on Wednesday.
The FBI has already expressed its displeasure with Apple's announcement.
Fox Cahn also points out that leaving the feature as opt-in will leave most users' data still available for abuse, especially to oppressive and autocratic regimes. On the other hand, the feature can also cause some catastrophic data losses if turned on without a user's knowledge—so Apple most definitely made the right decision here.
Further, as one user points out in a HackerNews comment, this is also huge news for Apple users, as it shows that the company is willing to sacrifice some of its ad business interests for their privacy and security.
"BUT, perhaps the BIGGEST news here is that Apple is making a backup statement to what they've been saying for years and what they've recently gotten negative attention on: They don't want your data. They're not Goodle/FB/Amazon. They're giving you 2TB+ of space and you can encrypt it to the point that you'll lose your data and they don't care -- they don't want to mine your data, they don't want to know what you store on there, the don't care to scan your pictures with AI 20 different ways, they don't want to monetize it, etc, etc., just pay them money for their service and transactionally they give you [the] only thing that you want in return -- [a] reliable, secure, private service."
According to Apple, Advanced Data Protection for iCloud will be available for beta testers starting this week and for US users by the end of the year. The feature, along with the other two, will be available to worldwide users in early 2023.
Overall, this is very good news for Apple users. Cryptographer and Johns Hopkins University professor Matthew Green, one of Apple's biggest critics, called the news a "big deal." If Apple managed to impress Green, we'll count it as a win.
In the meantime, we're gonna be patiently waiting for the first real-world contact between Apple's Advanced Data Protection for iCloud and Australia's Assistance and Access Act 2018 law.
Breaches and hacks
Turkey charges journalist over their own data breach: The Turkish government has filed charges against İbrahim Haskoloğlu, a local journalist who discovered a breach of a government portal. Haskoloğlu was previously detained in April earlier this year after he tweeted redacted photos of the ID cards of several Turkish political figures, including President Recep Tayyip Erdoğan. Haskoloğlu said he received the data from a hacking group that claimed to have breached Turkey's e-government portal. He said he published the photos after the government refused to admit the incident. Earlier this week, Haskoloğlu said he was charged with disseminating personal data on social media and that authorities have yet to launch an investigation into their own breach.
Sequoia One data breach: Sequoia, one of the largest HR and payroll companies in the US, is currently notifying customers about a security breach after a threat actor gained access to one of its cloud storage servers. The breach took place in September, and Sequoia said the server was storing a wide array of customer personal information, such as names, home addresses, Social Security numbers, healthcare information, and wage and employment details. The company did not reveal the number of impacted customers but did say that the hackers lurked in its network for two weeks before being discovered. [See Wired's coverage]
Medibank shutdown: Australian health insurer Medibank said it plans to shut down all branches, websites, and mobile apps over the weekend for a general overhaul of its IT systems. The company is set to deploy new cybersecurity measures as part of "Operation Safeguard," a series of IT and cybersecurity upgrades it announced last month after a catastrophic hack that exposed the personal details of more than 9.7 million Australians. [Additional coverage in the Sydney Morning Herald]
Antwerp hit by ransomware: The computer network of Antwerp, Belgium's largest city, is currently offline since Monday after a ransomware attack hit Digipolis, the city's IT provider. City officials said that numerous government reservation and appointment systems are offline, along with the city's email servers.
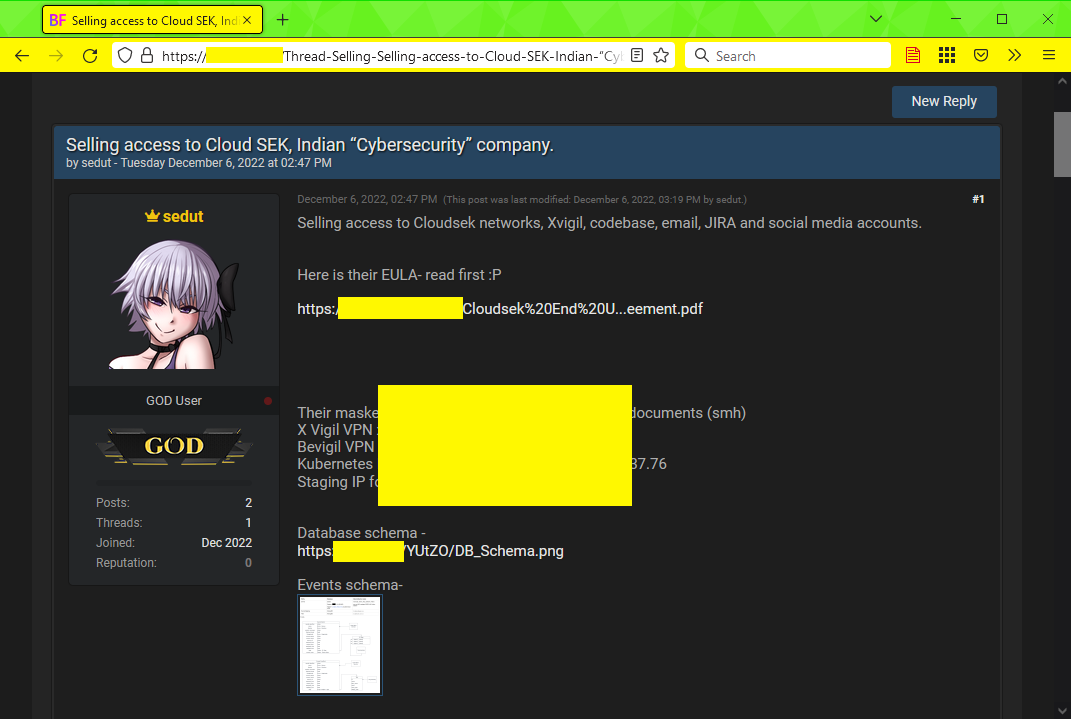
CloudSEK discloses security breach: Indian cybersecurity firm CloudSEK says that a threat actor has gained access to the JIRA account of one of its employees. The account was allegedly used to access CloudSEK internal systems that were storing information on bug reports, customer details, and dark web monitoring. CloudSEK said it learned of the breach after some of its data was put up for sale on Breached—an underground cybercrime forum for selling hacked data. While the data was put up for sale under an account named "sedut," CloudSEK believes the intrusion was carried out by a rival cybersecurity company, but did not elaborate further.
General tech and privacy
Telegram to let users sign up without a SIM card: Secure instant messaging service Telegram says it will allow users to sign up for accounts without a real phone number or a SIM card. The company says it recently added support for Fragment, a platform that allows users to buy anonymous phone numbers using cryptocurrency.
npm 2FA adoption: GitHub says that starting with November 1, last month, they began enrolling the maintainers of high-impact packages into mandatory 2FA for their accounts. GitHub says high-impact packages account for 93% of npm's monthly traffic, hence their desire to enforce 2FA for these projects.
Tor Browser 12.0: The Tor Project has released v12 of the Tor Browser, which now comes with full support for Apple-made CPUs.
E2EE Twitter DMs: End-to-end encrypted messages aren't coming to Twitter any time soon, after all. Something, something, about Musk having a decade-long history of promising but never delivering. From Forbes:
"But, according to new trust and safety lead Ella Irwin, there are no immediate plans to roll out encrypted messages in Twitter DMs. Indeed, there's no guarantee it will ever be deployed, she told Forbes in an interview from Twitter's San Francisco HQ on Tuesday."
Government, politics, and policy
Tech vendors advise against SBOM deployment: The Information Technology Industry Council (ITI), an industry group consisting of the world's largest tech and software companies, has asked the US government to "discourage" agencies from adopting Software Bills of Material (SBOM) as a mandatory requirement for government contracts until the standard matures and both vendors and agencies can better understand how to use it. The request, made in an open letter [PDF] published last month, comes after the White House issued a memorandum [PDF] earlier this year mandating that all new government software purchases come with an SBOM. [Additional coverage in SecurityWeek]
Texas bans TikTok: Texas Governor Greg Abbott has banned the use of the TikTok mobile application on devices of state employees. Texas becomes the fourth Republican-led state to ban TikTok on employee devices after Maryland, South Carolina, and South Dakota. In addition, Indiana's Attorney General Todd Rokita sued TikTok in two separate lawsuits, accusing the company of deceiving users that their data was protected from the Chinese government and for exposing Indiana children to adult content. [Press coverage in ZDNet]
Taiwan bans TikTok too: The Taiwan government banned TikTok from the devices of government employees. Officials said the app is a "harmful product against national information security."
CISA Director faces ethics complaint: CISA Director Jen Easterly has been hit by an ethics complaint for a series of tweets that praised a recent book published by Wired reporter Andy Greenberg. Politico first spotted that the tweet might be an ethics violation last week. Easterly deleted the tweet after the news outlet's inquiry. The case seems pretty thin, though, as Easterly's tweets were published around the book's launch when most of the cybersecurity community was mass-prasing the book and don’t appear to have been anything more than a compliment.
2023 NDAA summary: Cyberscoop's Suzanne Smalley has a summary of the 2023 National Defense Authorization Act, which this year contains significant spending increases for US Cyber Command and multiple cybersecurity-related updates.
- More CYBERCOM hunt forward missions
- Creates an assistant secretary of cyber policy at the DOD
- Codifies a new cybersecurity bureau at the State Department
- Reforms the FedRAMP cybersecurity authorization program
- New rules for how intelligence agencies can use spyware
Sponsor section
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. The company launched a new product called Sensitive Command Canarytoken, a simple canary token that sends an alert every time any command you choose as "sensitive" or "malicious" is executed on your host.
Cybercrime and threat intel
POS hacker arrested: The FBI has arrested an Arizona man named Foster Cooley in connection to a scheme to hack into a salon company's point-of-sale provider and steal over $430,000 worth of credit card payments from its customers. The incident took place in May this year and was discovered two weeks later after the company noticed the missing funds.
New spyware vendor: Politico Europe has a profile on Altrnativ, a French company that allegedly sells spyware and surveillance tools to at least six African countries. The most interesting part of the piece is that one of the Altrnativ founders is the former CEO of Qwant, a privacy-first search engine that at one time was the default search provider of the Brave browser. That's quite the sudden career turn.
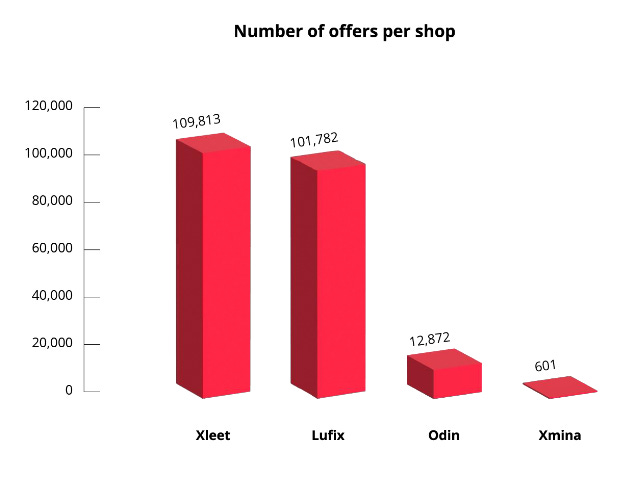
Webmail shops: Threat intelligence firm KELA has a report [PDF] out on the IAB market selling access to corporate webmail services. The company specifically covers Xleet, the largest criminal shop selling access to webmail accounts, but also other smaller shops such as Xleet, Odin, Lufix, and Xmina. The most popular listings are for Office 365 accounts, and most shops also sell other types of accounts as well.
CryptosLabs group: Group-IB researchers have identified a new cybercrime operation named CryptosLabs that, since 2018, has operated a network of more than 300 scam websites posing as fin-tech and cryptocurrency trading platforms. Group-IB says the group used search engine ads and social media posts to trick French-speaking users across Europe into investing more than €480 million in these websites, thinking they would get to trade in stocks and crypto assets. But researchers say that once users put money into their accounts, the crooks either asked for more or ignored their customers before shutting down platforms and moving to a new domain. Group-IB said it named this group CryptosLabs after the kit they used to automate the deployment of the fake trading portals, which typically mimicked 40 popular banking, fin-tech, and crypto brands.
Malicious PyPI package: A malicious Python package named pywz was identified on the official PyPI portal.
New npm malware: Eleven new malicious npm packages were discovered on the npm portal. Check out GitHub's security advisory portal for details.
Hybrid malware campaign: Mobile security firm ThreatFabric said it discovered what it calls a "hybrid malware campaign" where a threat actor was combining and deploying both Android and Windows-based banking trojans in order to maximize their profits. Banking trojans spotted included the likes of Ermac, Laplas, Erbium, and Aurora.
SMS scams target India: Zscaler has a breakdown of a wave of SMS scam texts that are trying to convince Indian users to install malicious e-banking apps.
WordPress hacking campaign: Sucuri researchers have a breakdown of a malicious campaign that appears to have compromised more than 170 WordPress sites and altered their plugin code to redirect incoming traffic to websites that aggressively request permission to send push notifications—which they are most likely using to push spam and malware.
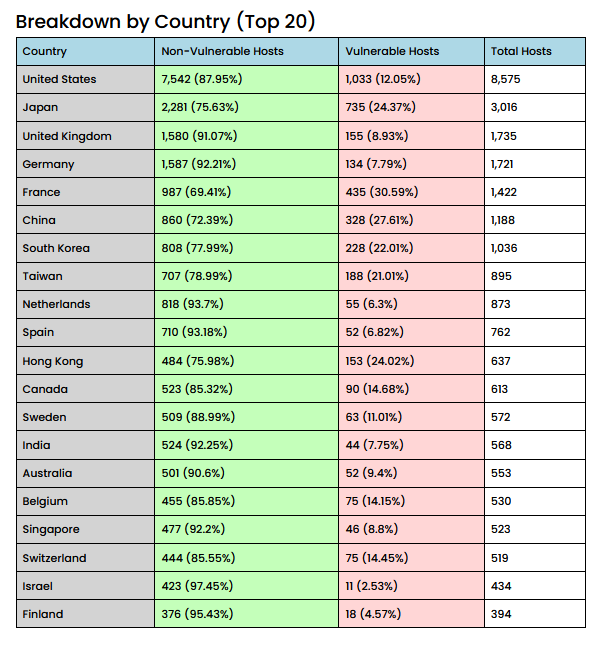
4.4k Pulse Secure VPNs still unpatched: Researchers with Censys say that 4,460 of 30,266 Pulse Secure VPN servers currently connected to the internet are vulnerable to one or more security bugs, leaving the networks they protect exposed to attacks. The number represents almost 15% of all Pulse Secure servers currently connected online. Pulse Secure VPNs have been known to be targeted by various threat actors, including APTs and ransomware gangs.
Malware technical reports
WSzero botnet: Qihoo's Netlab division says it spotted a new DDoS botnet named WSzero. Written in the Go programming language, Netlab said the botnet appeared and grew to a considerable size over the last four weeks. Researchers say the botnet is currently using a collection of n-day vulnerabilities and Telnet brute-force to take over unsecured devices and has already been used to launch DDoS attacks by its operator(s).
Babuk ransomware: Morphisec researchers identified a new variation of the (previously leaked) Babuk ransomware that was deployed in an attack in the wild. Their report on this version is here.
APTs and cyber-espionage
Agrius APT wiper: ESET says that an Iranian APT group they track as Agrius has compromised the network of an Israeli company that produces software for the diamond industry and used one of its software suites to execute a supply chain attack and deploy data-wiping malware to companies across the world. ESET said the wiper, which they named Fantasy, appears to be a modified version of a previous wiper named Apostle that the group used in 2020 and 2021 in previous destructive operations against Israeli companies.
APT37: Google TAG security team has revealed that an Internet Explorer zero-day that Microsoft patched last month was actually used by North Korean hackers to target users in South Korea. Google linked the attacks to a group known as APT37 (ScarCruft), known for targeting North Korean defectors and South Korean policy-makers, journalists, and human rights activists. The group also has a history of using IE zero-days before.
Operation EvilPlane: EST Security researchers have published a report called Operation EvilPlane that describes a recent spear-phishing operation targeting South Korean users and carried out by Konni, a North Korean cyber-espionage group.
DeathStalker (Evilnum): Kaspersky's GReAT team has a report on a new version of the Janicab malware, which the DeathStalker (Evilnum) APT has deployed in attacks against legal and financial entities in the Middle East throughout 2020 and 2021.
Vulnerabilities and bug bounty
Jenkins plugin vulnerabilities: The Jenkins project has published a security advisory warning about vulnerabilities in seven plugins, including the official Google Login plugin, one of the project's most popular modules.
Cisco CDP zero-day: Cisco says that a proof-of-concept exploit has been published for a zero-day vulnerability in the Cisco Discovery Protocol. The company said the vulnerability can allow remote unauthenticated attackers to run malicious code on affected devices. Currently, the vulnerability has been confirmed to impact Cisco IP phones running the 7800 and 8800 firmware series. No security updates or workarounds are currently available, but if they will, more information will be available on this page.
WAF bypass: Claroty's Team82 has discovered a generic technique that can bypass web application firewalls (WAFs) from major providers such as Palo Alto Networks, AWS, Cloudflare, F5, and Imperva. Researchers say the technique involves appending JSON syntax to SQL injection payloads that a WAF is unable to parse, and the technique worked because most WAF products lack support for JSON payloads.
CVE-2022-42703: Google's Project Zero team has a technical write-up on CVE-2022-42703, a UAF vulnerability in the Linux kernel that was patched in September.
Infosec industry
Security firms aiding Ukraine: Kim Zetter has a piece on how cybersecurity companies helping to defend Ukraine against Russian cyberattacks during the current war could be considered direct participants in the hostilities and open themselves to attack. This includes companies like Microsoft, Amazon, Mandiant, Cisco, ESET, and Recorded Future.
Deloitte acquires Makros: Service provider Deloitte has acquired Chilean cybersecurity firm Makros.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




