Risky Biz News: Apple debuts Lockdown Mode to protect users against high-end spyware
In other news: North Korean hackers linked to Maui ransomware; Russian hacker hits Portuguese hotel in clever hack; and Microsoft rolls back VBA macros block.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
In an unexpected but very welcomed move, Apple announced this week plans to add a new security feature to its iOS and macOS operating systems later this fall. Named Lockdown Mode, this new feature will be available as a new "mode" in a device's settings section.
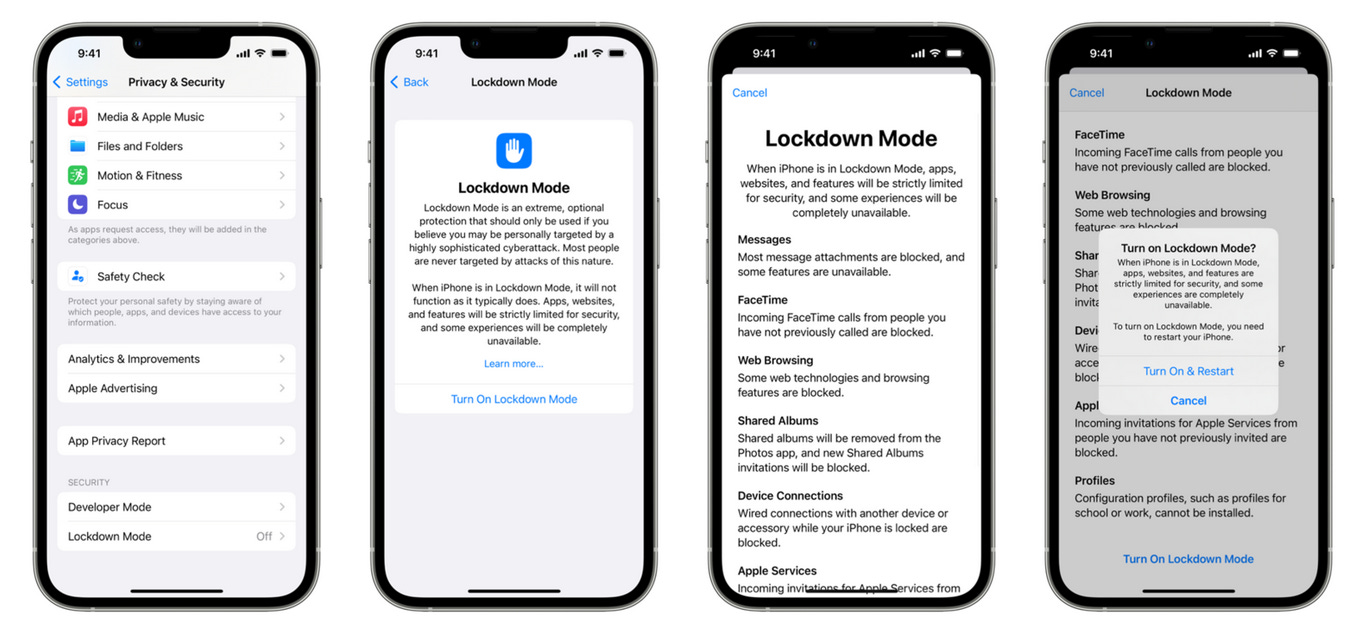
Apple says that once users enable Lockdown Mode, iOS and macOS will be put into what the company describes as an extreme and super-secure protection mode.
What happens under the hood is that iOS and macOS will turn off some of their internal services and features that are commonly abused by threat actors to attack and compromise devices. Apple said that Lockdown Mode would focus on five major areas of concern for the company. This includes:
- Messages: Commonly used for the delivery of zero- or one-click exploits, but once Lockdown Mode is enabled, the Messages app will be put into a state where it would only support text and image-based communications, with no support for URL previews or complex audio and video formats.
- Web browsing: Since many recent actively exploited zero-days against Apple devices are in Safari components, once Lockdown Mode is enabled, Apple said it would disable many of the new and complex web API technologies that have been added in Safari in recent years, but which are not essential to browsing websites. This includes stuff like WebGL, WebAudio, WebRTC, MathML, Picture-in-Picture, and web fonts, among many others.
- Wired connections: But remote attacks aren't the only way to compromise iOS and macOS devices. Apple says that once Lockdown Mode is enabled, all wired connection ports will be disabled and blocked once a device is locked.
- Configuration profiles: A recent technique that has become popular with threat actors has been to trick users into installing malicious OS configuration profiles to secretly add a victim's device to an attacker's network. The idea is that once a device is joined to an attacker's mobile device management (MDM) server, the threat actor can exfiltrate data or install malicious apps on the device. But Apple says that when Lockdown Mode is enabled, a device's MDM service will be disabled, effectively countering and preventing any such attack from working.
- Apple services: Besides remote and physical access attacks, Apple users may also be at risk from social engineering attacks. For this, Apple says that Lockdown Mode comes with a feature that will block unknown individuals from starting calls or conversations via Apple services if the owner has not contacted that person before.
Lockdown Mode is not meant for everyday users
With so many features turned off, Apple devices will effectively be thrown back a decade into the past. It is no exaggeration to state that Lockdown Mode will greatly degrade the user experience on an iPhone, iPad, or macOS device.
However, Apple's security team said they didn't design this feature to be user-friendly. It is effectively a last-resort option for some of its users that are active civil society members, dissidents, politicians, or intelligence and law enforcement employees. These users are the ones who are typically targeted by advanced threat actors, sometimes state-sponsored entities, which have access to high-grade and expensive exploits designed for stealthy attacks.
Apple hopes that Lockdown Mode will be able to protect these users by disabling all the common avenues of attacks that past high-end exploits and spyware developers have used against its devices.
If you're a regular Joe Blow, Lockdown Mode will look cool and interesting for a hot minute, after which it will just get in the way of how you connect with friends and use your device. Turning it on will be overkill, and you'll most likely turn it back off within a few days. However, for people fighting the good fight, Lockdown Mode might end up saving their lives, and we're not exaggerating when we're stating this.
Great to see big tech companies roll out features to protect at-risk people: Google announced the Advanced Protection Program in 2017. Meta announced Facebook Protect in 2018. Apple announced Lockdown Mode in 2022. Very curious about what we'll see next and from whom.
— Runa Sandvik (@runasand) 9:45 PM ∙ Jul 6, 2022
Breaches and hacks
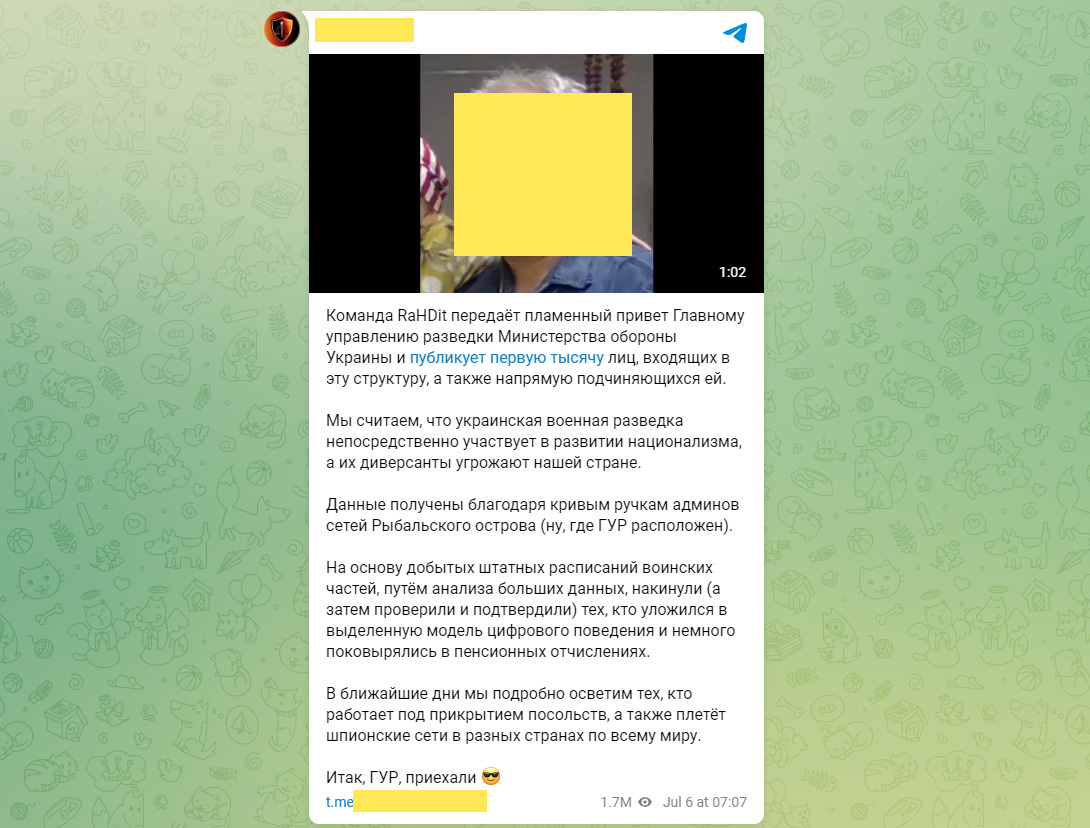
Ukrainian intelligence officers leak: A group of Russian hackers calling themselves RaHDit have published a trove of documents with the alleged identities of thousands of Ukrainian intelligence officers. The leak is currently still unverified, Risky Biz News understands, but the RaHDit crew was also previously linked to Project Nemesis, a project among Russian "hacktivists" that doxxed members of the Ukrainian military.
PFC releases list of affected healthcare orgs: Professional Finance Company (PFC), a US company that provides various financial and payment services to the healthcare sector, has disclosed a security incident that took place in February this year and involved a ransomware attack. The company said the hackers stole data from its systems that belonged to more than 600 of its customers, most of which are US healthcare organizations, such as hospitals and clinics, and the stolen data also included patient details. [Coverage in Becker's Hospital Review]
Hacker steals from Portuguese hotel guests: A hacker has stolen more than half a million euros from the guests of the Marino Boutique Hotel in Lisbon. The hacker broke into the hotel's online booking platform, locked out the hotel's personnel, changed room prices to a derisory €40, and emailed the hotel's former customers this "special offer." During four days between June 12 and June 16, the hotel said the hacker collected payments for thousands of room bookings, which the hotel said would have normally cost around half a million euros. It took the hotel staff four days to regain access to their booking platform, which they initially thought was having a technical issue. The hotel, which is one of the most expensive in Lisbon, said it is considering suing the booking platform for not detecting the hacker's intrusion. CNN Portugal said they found the hacker on one of its Telegram channels, where they bragged about having pulled the same attack against other hotels in many other countries. The hacker identified as Russian and claimed to have made over €20 million from his cybercrime activities. [via @chum1ng0]
How the Ronin hack took place: A reporter from cryptocurrency news site The Block has uncovered the root cause of the Ronin Network hack, which lost $540 million worth of cryptocurrency earlier this year, in March, to North Korean state-sponsored hackers. The Block says the company had its IT network compromised after one of its employees was lured into opening a malicious PDF document received from the hackers, touting a fantastic job offer with a generous compensation package, a scheme for which North Korean hackers are known to excel at.
General tech and privacy
Meta sues scraping company: Meta filed a lawsuit this week against a company named Octopus, a US subsidiary of a Chinese tech company. Facebook said Octopus provided website scraping technology to its customers, including the ability to scrape content from Meta properties such as Facebook and Instagram, including private content that's hidden and requires authentication. In addition, Meta said it also sued a Turkish national named Ekrem Ateş for scraping the data of more than 350,000 Instagram users.
Microsoft rolls back VBA macros ban: After blocking VBA macros in five Office applications earlier this year in February, Microsoft has apparently rolled back the change earlier this week, in what the company described as "feedback received." As expected, the rollback of one of the company's most requested security-related changes launched a whirlwind of complaints and ironies directed at Redmond. Even worse, it appears that Microsoft's change had its desired effects, contributing to a decline in macro-based malware in recent months to the point of extinction. Following Microsoft's change of heart—cybercrime groups, rejoice, I guess! [Coverage in Bleeping Computer]
@campuscodi @sherrod_im Clearly it was working and was a threat to crimeware distro, otherwise the actors wouldnt have been screwing around suddenly with LNK/IMG/ISO/ZIP shenanigans to work around MoTW.
— Cryptolaemus (@Cryptolaemus1) 11:55 PM ∙ Jul 7, 2022
I have no information about this but I can confidently state it will be because it broke some process at a very large customer (probably more than one) and they starting complaining
— Mary Branscombe (@marypcbuk) 12:22 AM ∙ Jul 8, 2022
Government, politics, and policy
Biometrics database speed-run: The Russian Parliament voted this week on a law that will allow it to gather biometrics data from Russian banks into a central database named the Unified Biometric System (EBS). The law effectively allows the government to pilfer this data from banks without the express approval of Russian citizens, and government officials said this would allow the widespread deployment of biometric identification and authentication technologies to as many organizations as possible. Also helps with other "things" beyond paying for goods without payment cards, wink-wink.
Cybercrime and threat intel
Trickbot gang systematically attacks Ukraine: An IBM X-Force report published on Thursday claims that the operators of the Trickbot malware have been "systematically attacking Ukraine since the Russian invasion." IBM notes that Trickbot has conducted at least six different malspam campaigns against Ukrainian users, something they have never done in the past. IBM notes that Trickbot is currently controlled by members of the old Conti ransomware gang, which got into a little bit of trouble earlier this year, having their hacking tools and internal chats leaked online after publicly expressing support for the Russian government.
Russian influence operations: A Recorded Future report published on Thursday has delved into Russia's most recent influence operations, which according to the company, appear to be focused on creating a divide in Western countries around their efforts and support of Ukraine against Russia's invasion.
These information operations almost certainly aim to undermine and divide the Western coalition on Ukraine both directly, by creating or exacerbating divisions between Western coalition countries, and indirectly, by influencing European populations to oppose their governments' support of Ukraine and negative policies toward Russia.
Google Cloud Threat Horizons Report #3: In the third edition [PDF] of its threat and trends report, the Google Cloud security team said that its cloud service continues to see a large number of attacks, with the majority aiming to deploy cryptomining payloads. The most common points of entry for these attacks continue to be brute-force attacks and unpatched software vulnerabilities.
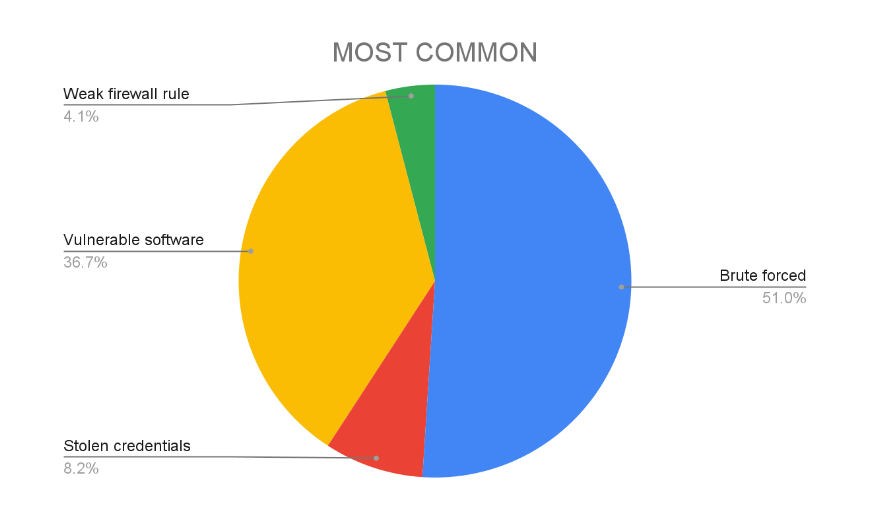
In addition, Google also noted that, in recent months, they've seen a rise in ransomware-like attacks against some of their SQL database infrastructure.
The most common technique observed was where attackers were seen brute forcing SQL databases, cloning a database table into a new table, encrypting the data, and proceeding to drop the original table. Attackers have been observed leaving instructions in the new table that instruct the victim to transfer funds to a specified crypto wallet to recover their data. Similar tactics have been seen around cloud project takeover, with threats to delete data & resources. These attacks were most commonly observed in developer and proof of concept (POC) instances. In many instances, these were targeted due to fewer security controls being placed in non-production environments due to their perceived lower risk.
MySQL servers targeted with AsyncRAT: AhnLab researchers have published a report on a recent series of attacks against MySQL database servers that have been infected with the AsyncRAT remote access trojan. According to the research team, the attacks leverage brute-force attacks and dictionary attacks against the MySQL root admin account as the initial access vector.
Teng Snake: S2W Talon has published a report on Teng Snake, a suspected Chinese threat actor that has been engaging in hacking and data leaks.
Checkmate ransomware: Taiwanese NAS vendor QNAP published a security advisory on Thursday warning its users about a new ransomware strain named Checkmate that has been infecting some of its devices. QNAP said the Checkmate gang uses dictionary attacks against a device's SMB service to break into accounts using weak passwords.
1.2k malicious npm packages: Security firm Checkmarx said it uncovered a cluster of more than 1,200 malicious npm packages that have been uploaded on the npm portal in a short period of time using an automated process by a threat actor the company calls CuteBoi. The company said almost all the packages contain malicious code that runs a coinminer inside apps where the packages are deployed. Checkmarx has set up a dedicated website to track and list recent npm packages linked to the CuteBoi cluster.
Malware technical reports
Maui ransomware: In a joint security advisory published on Wednesday by CISA, the FBI, and the US Treasury, the US government said that North Korean state-sponsored hackers had developed a ransomware strain named Maui. Officials said the Maui ransomware had been used in attacks dating as far back as May 2021, and many of its targets have been US healthcare organizations. Cybersecurity firm Stairwell has also published its own report on this new threat, noting some of the Maui ransomware's advanced features.
ABCsoup: Zimperium has published a report on ABCsoup, a cybercrime operation that builds and distributes malicious browser extensions for Google Chrome, Opera, and Firefox. The extensions mimic the IDs of legitimate add-ons and are typically distributed as Windows executables to bypass security checks found in official extension stores. Zimperium said the gangs has deployed at least 350 extension variants so far.
YourCyanide: CloudSEK has published a report on YourCyanide, a rare ransomware strain that comes with a mail-based worm behavior, previously also covered by Trend Micro here.
Ekipa: The same CloudSEK team also published a report this week on Ekipa, a remote access trojan sold on underground cybercrime forums for $3,000. According to CloudSEK, the RAT comes with a builder and would operate as a Microsoft Word macro or Excel add-on.
OrBit: Intezer published a technical analysis on a new malware strain named OrBit. The malware targets Linux systems and once deployed on a compromised, it can provide threat actors with remote access capabilities over SSH, can harvest credentials, and logs TTY commands. At a technical level, the malware is also of note because once deployed, it infects all processes running on a Linux system, including new ones.
LockBit 3.0: We now have the first technical report on the new version of the LockBit ransomware, also known as LockBit 3.0. Just like Fabian Wosar of Emsisoft pointed out last week, Cluster25 researchers also point out several similarities in the LockBit 3.0 code to the now-defunct Darkside and BlackMatter ransomware strains.
HavanaCrypt: Trend Micro has published an analysis of the HavanaCrypt ransomware, which is currently being distributed hidden in files posing as a Google Chrome browser update.
TrippleCross: A computer science student open-sourced last month a rootkit named TripleCross that abuses the eBPF network package filtering technology in Linux systems after such malware has become popular in recent months.
PINKPANTHER: On the same note, a security researcher also open-sourced this week a Windows kernel exploit named PINKPANTHER that can run shellcode on all recent versions of Windows to replace a process' access token with the SYSTEM token and elevate an attacker's privileges on an infected machine.
APTs and cyber-espionage
Chinese APT targets Russia: SentinelOne has published a report on a recent series of spear-phishing operations that appeared to have been carried out by a Chinese threat group against Russian organizations, including some government targets.
YamaBot: Japan's CERT team has published a technical analysis of YamaBot (also known as Kaos), a malware strain used by North Korean state-sponsored hackers on compromised Linux and Windows systems.
APT campaign uses recent NATO conference as lure: Lab52 has published a report on a suspected APT campaign that used the recently concluded NATO conference in Madrid, Spain, as a lure for its spear-phishing emails.
Vulnerabilities and bug bounty
Apple bug bounty news: Besides announcing Lockdown Mode this week, Apple also said it would also add this new mode to its official bug bounty program. The company plans to reward researchers who find Lockdown Mode bypasses and some vulnerabilities could earn researchers up to $2 million, in what Apple described as "the highest maximum bounty payout in the industry."
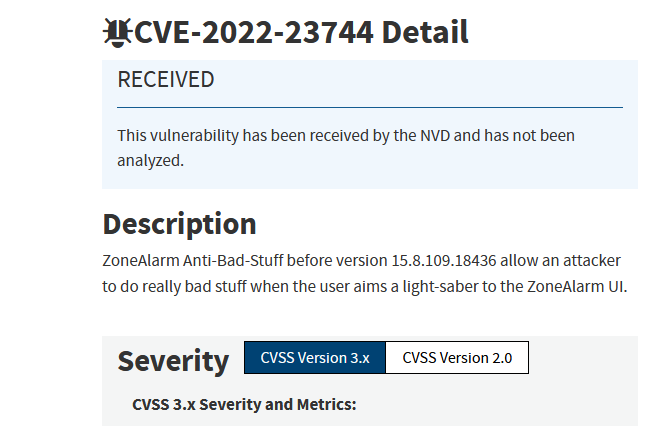
What now?: So... this happened this week.
It's finally happened, we've found the best CVE. H/t @NTKramer 🏆 Definitely Wayback Machine'd this thing for posterity.
— Caitlin Condon (@catc0n) 4:57 PM ∙ Jul 7, 2022
Infosec industry
Group-IB splits: Cybersecurity and threat intelligence firm Group-IB has split its Russian branch from its international operation. The company was originally founded in Russia and moved its headquarters to Singapore. Ilya Sachkov, founder and CEO of Russian security firm Group-IB, was detained in Moscow in September 2021 on treason charges for allegedly sharing data of Russian hackers with international authorities.
Tool release: Security firm SpectreOps has open-sourced a new tool called Koh that can be used to capture Windows account authentication tokens for new logon sessions and reuse them for future attacks. A technical introduction to the tool is also available in a dedicated blog post.




