Risky Biz News: AMI Platform Key leak undermines Secure Boot on 800+ PC models
In other news: Google fixes email validation bypass; new threat actor goes after Selenium testing servers; CrowdStrike says 97% BSODed systems have recovered.

This newsletter is brought to you by no-code automation platform Tines. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The Secure Boot system on more than 800 motherboard models across 10 different vendors is basically useless now after an extremely sensitive cryptographic key was accidentally leaked online last year.
The key was leaked via a now-removed GitHub repository in 2023 and discovered earlier this year by firmware security firm Binarly.
It allegedly came from an (unnamed) Original Device Manufacturer (ODM), which in turn received it from American Megatrends International (AMI), a company known for developing BIOS/UEFI products.
Binarly named the entire event PKfail because the leaked key was a Platform Key (PK), one of the most important cryptographic keys that can reside on a computer.
Platform Keys are used to verify the trust between the underlying hardware and the firmware that runs on them. A Platform Key is also used to verify all the other sensitive cryptographic keys on a system during Secure Boot, such as what firmware and drivers are allowed to run when a device and the OS boot.
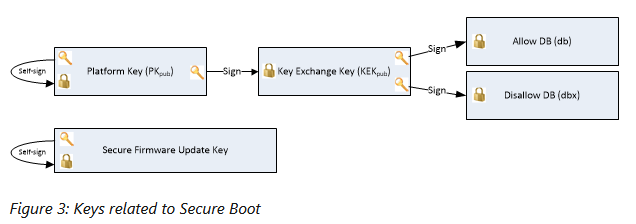
Companies that make BIOS/UEFI firmware, such as AMI, Insyde, or IBM, typically include a "test" or "dummy" Platform Key inside the firmware they provide to OEMs and ODMs—aka the actual hardware vendors.
These vendors are supposed to swap the PK with their own, typically on a per-product or per-model version, and then keep that key as safe as humanly possible.
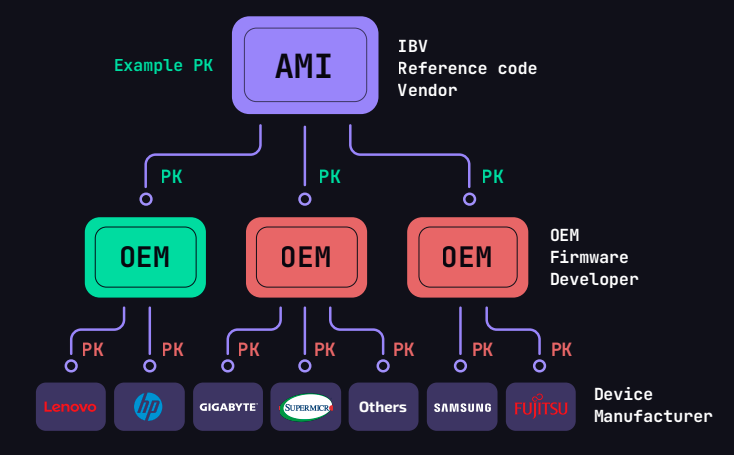
But according to Binarly, things didn't happen like this at all. Instead, the leaked AMI PK was one of those test PKs that never got changed and made its way into more than 800 motherboard models, used for all sorts of things, from data center servers to gaming laptops.
Now, all of these devices are susceptible to having Secure Boot bypassed. Binarly says threat actors can use the leaked Platform Key to develop and sign rootkits that pass as legitimate firmware or kernel drivers.
The security firm says that while the key leaked in 2023, it was one of the test dummy keys that AMI was shipping since as early as May 2012.
Right now, ten vendors are known to have shipped products with the leaked Platform Key. They include Acer, Aopen, Dell, Formelife, Fujitsu, Gigabyte, HP, Intel, Lenovo, and Supermicro.
At the time of writing, there are 813 models running the leaked dummy Platform Key, but the list will most likely grow as more security firms and OEMs/ODMs scan their firmware in the coming days.
Either way, the entire discovery is a security disaster. It basically negates the ability to have Secure Boot running properly on a large chunk of the PC population, re-opening the door to sneaky rootkit attacks of the early 2000s.
Breaches, hacks, and security incidents
Columbus cyberattack: The city of Columbus in Ohio says it's working to restore IT systems in the aftermath of a security breach that took place last week. Officials say the outage impacts resident-facing IT services and may take some time to restore. Columbus is the capital of Ohio and the 14th-largest city in the US, with almost 1 million residents. The incident is suspected to be another ransomware attack. [Additional coverage in The Record]
Israeli athletes PII leak: A hacker group has leaked the personal information of Israeli athletes competing in the Paris Olympic Games. The data contained names, login credentials, military status, and blood test results. A pro-Palestinian group named Zeus published the data in a Telegram channel ahead of the Olympic Games opening ceremony. [Additional coverage in The Times of Israel]
Gemini breach: Cryptocurrency exchange Gemini has disclosed a data leak after one of its banking partners suffered a security breach. Gemini says a threat actor gained access to one of the bank's internal collaboration tools. The exchange believes the intruder may have had access to transactional data between June 3 and June 7 this year. This includes names as well as bank account numbers and routing numbers.
TestRail breach: Atlassian is apparently silently notifying some customers about a suspected breach at TestRail.
Supposed ATM cyber attack in Russia: The Kyiv Post ran an article last week about Ukraine carrying out a major cyber-attack that crippled ATM across Russia for the past week. After looking into this and speaking to several people in both Russia and Ukraine, the Post seems to be overhyping some DDoS attacks that targeted Russian banks last week. For a major ATM outage that prevented Russians from withdrawing money, Russians didn't seem to have complained online at all last week—which is not how outages work.
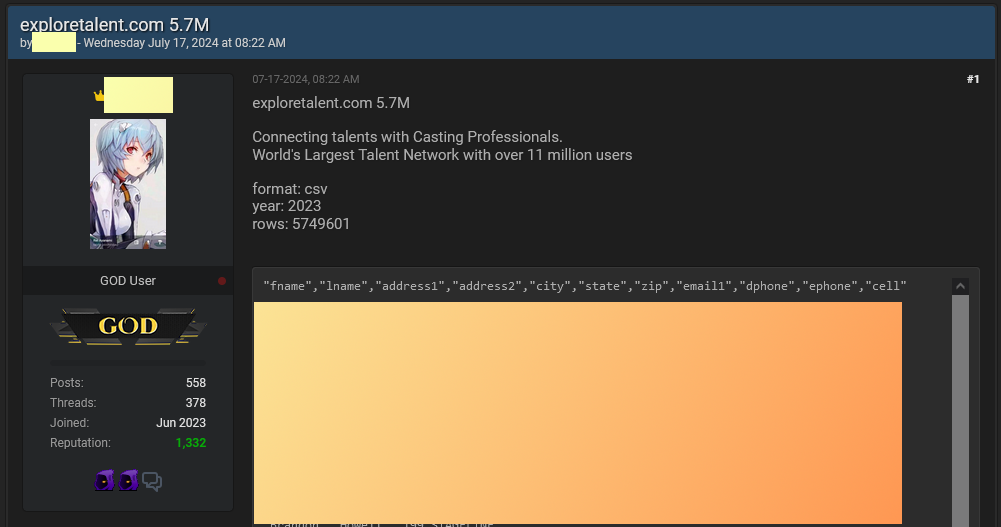
Explore Talent leak: A threat actor has leaked the details of 5.7 million users who registered on acting and modeling job-searching site Explore Talent. The data allegedly comes from a security breach that took place last year. The leak allegedly covers more than half of the site's 11 million registered users. The data includes full names, full addresses, email addresses, and phone numbers.
General tech and privacy
CrowdStrike outage update: CrowdStrike CEO George Kurtz says the company has recovered 97% of Windows systems impacted by a recent IT outage. The exec credited the quick turnaround to the development of a new automatic recovery technique. In the meantime, Microsoft has published its own technical deep dive into the CrowdStrike outage. The OS maker has confirmed that the BSOD screen was caused by a read out-of-bounds access violation in the CrowdStrike kernel driver.
Node joins the dark side: Node.js has added experimental support for running TypeScript files.
Car data sold for pennies: Two US senators have urged the FTC to investigate car makers for violations of consumer privacy laws. Senators Ron Wyden and Edward J. Markey say car makers have used deceptive techniques known as "dark patterns" to trick drivers into sharing car data. The data was sold to insurance companies that used it to increase rates for drivers based on how they drove, even if they had not caused any accidents. Wyden and Markey say some automakers showed a complete lack of respect for their customers' privacy, selling their driving history for mere pennies. For example, Hyundai sold car data for 61 cents per car, while Honda sold it for 26 cents per car. All of this while their buyers had insurance rates hiked based on arbitrary and unimportant data like braking behavior.
Twitter privacy violation: Social media company Twitter has forcibly enabled a feature for all its users that gives the company the right to use all their data to train the Grok AI. Twitter took the action without any formal warning, which may be a major privacy violation in several countries around the globe. The feature can be disabled, but only from Twitter's web interface.
Some outages: Google had an outage last week that prevented users from using the Chrome password manager. An outage also impacted Apple's iCloud Private Relay email anonymity service.
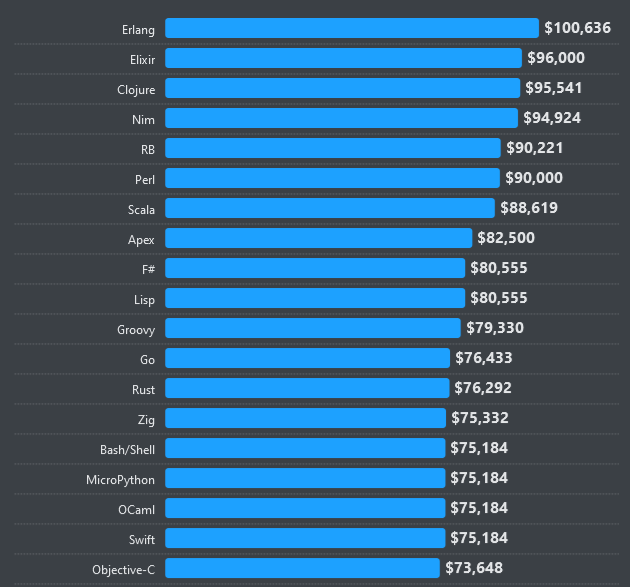
Programming trends: The annual StackOverflow developer survey for 2024 is out, and Erlang has retained its top spot as one of the best-paying jobs in the industry, with the best median salary out there.
Government, politics, and policy
Spyware in the EU: The European Commission has told member states in a private document to curb their spyware operations after a wave of Pegasus and Candiru incidents. The Commission has also told governments that "national security" also can't be used as a universal excuse. The document comes as the EU PEGA commission has found rampant abuse in some countries such as Poland, Greece, and Hungary. [Additional coverage in Politico Pro]
Venezuela elections: The Maduro government is blocking access to Wikipedia ahead of the country's elections. It's weird, but they've apparently done it before.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Thomas Kinsella, co-founder and Chief Customer Officer of Tines about figuring out what AI is really good for and taking advantage of it in automating workflows.

Cybercrime and threat intel
Nigerian scammer sentenced: A US judge has sentenced a Nigerian man to 12 years and 7 months in prison for his role in a cyber scam campaign. Officials say 42-year-old Bamidele Omotosho bought stolen credentials from the former xDedic marketplace and used them to gain access to remote systems. One of Omotosho's victims was the Employees Retirement System of Texas, from where he diverted retirement payments. US prosecutors say Omotosho and his co-conspirators stole more than $2 million.
Threat/trend reports: MTS RED, NBIP, Red Alert, and TRM Labs have recently published reports covering infosec industry threats and trends.
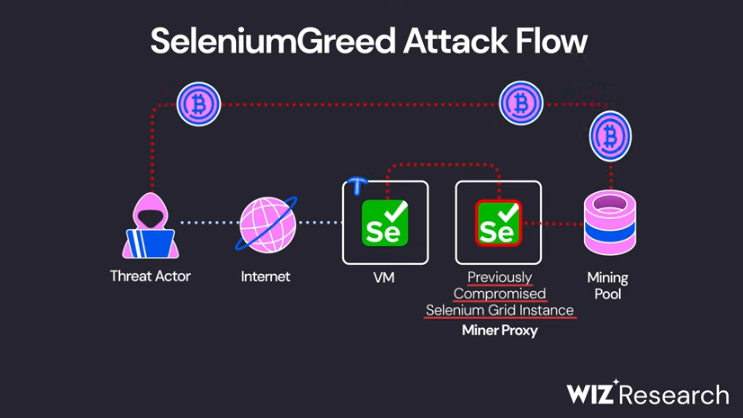
SeleniumGreed: A new threat actor named SeleniumGreed is abusing Selenium software testing servers to gain access to underlying cloud infrastructure. The attack targets Selenium Grid, a server-based version of the Selenium software that can allow developers to run tests in parallel across multiple machines. Cloud security firm Wiz says the threat actor is abusing the Selenium WebDriver API to interface and run commands on the underlying servers to install cryptocurrency miners. Wiz says the attacks are possible because Selenium Grid ships the API with authentication disabled by default. There are currently more than 17,000 Selenium Grid servers that appear to run unprotected APIs online.
GXC Team: Security firm Group-IB says that a threat actor named the GXC Team has become one of the largest players on the Spanish-speaking cybercrime scene. The group launched in January 2023 and is known for selling phishing kits, Android malware, and AI-powered scam tools. The group's services primarily target Spanish-speaking users with a focus on phishing Spanish banks and governmental bodies. Group-IB says GXC members are also involved in the sale of stolen credentials and are also providing on-demand coding for other groups.
TA558: Russian security firm FACCT says that a financially motivated threat actor tracked as TA558 is behind phishing attacks that have targeted companies across Russia and Belarus.
FaCai: Chinese security firm Anheng Hunting Labs has published a report looking at a local cybercrime group named FaCai that has been targeting the internal Chinese market with malicious MSC files. Anheng says the malicious files seem to have been inspired by past DPRK APT operations.
Malicious CrowdStrike domains: Akamai and Infoblox look at more than 180+ newly created malicious domains that appear to have been created to phish CrowdStrike customers using lures related to the company's recent outage.
V3B PhaaS: PulseDive takes a look at V3B, a Phishing-as-a-Service platform that launched in March 2023 and primarily targets European banks.
New npm malware: Eighteen malicious npm packages were discovered last week. Check out GitHub's security advisory portal for additional details.
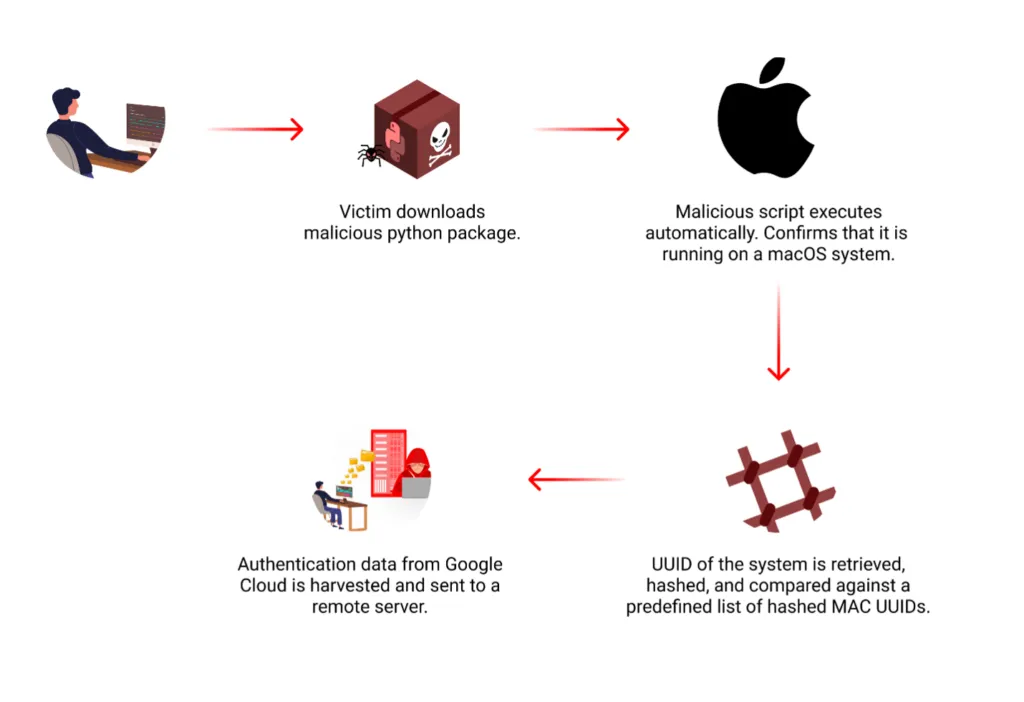
New PyPI malware: DevSecOps company Checkmarx has found a malicious PyPI package that contained malicious code designed to infect macOS systems and steal Google Cloud Platform credentials. Named "lr-utils-lib," the package has been live for almost a month. Checkmarx says the package was uploaded from an account made to look like a tech CEO.
Malware technical reports
XehookStealer: IoT search engine Censys says it found 11 servers hosting command-and-control servers for the XehookStealer Malware-as-a-Service. The company says it found the servers while investigating issues with detections for the older Agniane Stealer service. Censys says the new Xehook appears to have been created by the same coder due to overlapping code. Many of the Xehook and Agniane C2 were also hosted on the same servers. This marks another case where malware lineages can be tracked due to poor OpSec and shared code.
Kematian Stealer: ThreatMon looks at a new infostealer named Kematian Stealer that is available as a free tool on GitHub and has been recently seen in the wild.
RansomHub ransomware: Lab52 researchers have published IOCs and technical details from recent RansomHub ransomware incidents.
Medusa ransomware: Threat intel firm DarkAtlas says it gained access to one of the Rclone data exfil servers used by the Medusa ransomware group.
Sponsor Section
In this demo, Tines CEO and co-founder Eoin Hinchy demonstrates the Tines no-code automation platform to RiskyBiz host Patrick Gray.
APTs, cyber-espionage, and info-ops
UAC-0102: Ukraine CERT says that a threat actor tracked as UAC-0102 is behind a wave of phishing attacks targeting Ukrainian email provider UKR.NET. Russian espionage group APT28 has been targeting UKR.NET users since the start of Russia's invasion. It was extremely active early last year. Ukraine CERT says the recent campaign used HTML files placed inside ZIP files.
XDSpy: Russian security firm FACCT has published a report on new attacks from APT group XDSpy. The campaign took place this month and targeted Russian companies with malicious RAR archives. The final payload was the XDSpy.DSDownloader.
APT-C-09: Qihoo 360 has published a report on APT-C-09, a supposed Indian APT group also known as Patchwork. The report covers recent attacks against Pakistani targets with Go-based malware.
SideWinder new infrastructure: BlackBerry's security team says it found new infrastructure believed to be linked to Indian cyber-espionage group SideWinder. Clues in the infrastructure's setup suggest the group is targeting ports and maritime facilities located in the Mediterranean Sea and the Indian Ocean. BlackBerry believes the campaign is focused on espionage and intelligence gathering, and not any destructive attacks.
Doppelganger activity: French security firm Harfang has published an analysis of the recent infrastructure and contents of influence operations linked to the Russian Doppelganger info-ops group. A new development is the use of black hat SEO to promote links to some of their fake news sites and their articles.
Vulnerabilities, security research, and bug bounty
Google EV bypass: Google has fixed a security flaw that allowed threat actors to register Workspace accounts on domains they did not own. The bug resided in the Workspace platform email verification process. Attackers abused the bug to sign up to Workspace domains with unrelated email addresses. The attackers then abused the "Sign In with Google" feature to access accounts associated with that domain on third-party services. According to Brian Krebs, the bug has been exploited since June. Google says it detected abuse on a "few thousand" Workspace accounts.
New AES-GEM cipher: Trail of Bits cryptographer Scott Arciszewski has developed and released a new TLS 1.3 cipher named AES-GEM, or Advanced Encryption Standard with Galois Extended Mode. The new cipher is meant to replace AES-GCM, which has been deemed insecure for several years. Arciszewski says AES-GEM improves the security of GCM in every dimension with minimal performance overhead. The new cipher is still in development and will need to pass the IETF standardization process.
Fast-charging vulnerability: A team of academics has identified vulnerabilities in fast-charging systems used for modern electric vehicles. Researchers say the Southwest Research Institute say they gained access to network keys from the PLC layer of fast-charging technologies. The keys can allow threat actors to eavesdrop on traffic between EVs and charging equipment and potentially mount more powerful attacks.
Softaculous Webuzo vulnerabilities: Exodus Intelligence has found three major vulnerabilities in Softaculous installers running on Webuzo hosting panels. The issues include an authentication bypass, a command injection vulnerability in the FTP management functionality, and a command injection in the password reset functionality. The first vulnerability can be exploited by remote anonymous attackers and can allow a full server compromise.
New Thread-Name technique: Check Point security researcher Aleksandra "Hasherezade" Doniec has developed a new process injection technique named Thread-Name, named so because it abuses the Thread Name API.
Infosec industry
Nothing in this edition.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss whether the rise of cloud computing has been a boon or a curse for cyber espionage agencies.
In this podcast, Tom Uren and Patrick Gray discuss the wild story of a Chinese illegal gambling operation that involves human trafficking, shell companies, money laundering, hundreds of thousands of websites, and sponsorship of European football teams.
This Soap Box edition of the show is with Mike Wiacek, the CEO and Founder of Stairwell. Stairwell is a platform that creates something similar to an NDR, but for file analysis instead of network traffic. The idea is you get a copy of every unique file in your environment to the Stairwell platform, via a file forwarding agent. You get an inventory that lists where these files exist in your environment, at what times, and from there, you can start doing analysis.




