Risky Biz News: Almost 9 million Android phones sold pre-infected with malware
In other news: Cyber-attack cripples Suzuki's motorbike and scooter production; Apple bans employees from using ChatGPT; PyPI suspends new accounts and uploads following surge of malicious packages.
This newsletter is brought to you by Thinkst. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
A cybercrime operation tracked as the Lemon Group has planted malware inside the firmware of almost nine million Android devices sold across the world over the past half-decade.
The group's malware has been found in the OEM firmware images of multiple brands of low-cost Android smartphones.
Trend Micro, which has been tracking the group for years, says it was unable to discover how exactly this was done, but the company suspects the group may be working with insiders at various smartphone factories.
The Lemon Group's malware is known as Guerrilla, and it is typically hidden inside Zygote, one of the first processes that starts after the Android OS boots.
The malware has one primary function—to download other plugins at the behest of Lemon Group operators.
Trend Micro says it spotted Guerilla plugins that can show fullscreen ads when users open particular apps and send spam messages via Facebook and WhatsApp.
Other plugins can install or uninstall apps, turn infected devices into proxies and relay network traffic, or intercept SMS messages.
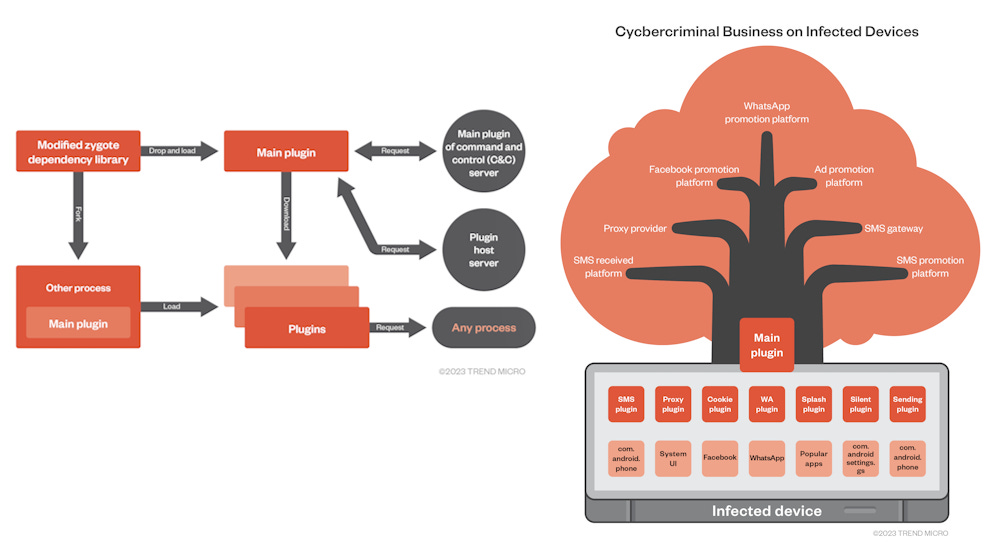
Trend Micro says it linked the Lemon Group to several real-world companies that leverage the infected devices to generate a profit.
This includes a data analytics company, a residential IP proxy service, and a service through which botnets and other threat actors can verify online accounts using the phone numbers of Guerrilla-compromised devices.
While the malware has been spotted only on Android smartphones so far, Trend Micro says the Lemon Group looks to be branching out to the IoT ecosystem, such as smart TVs, TV boxes, smart displays, and even children's watches.
Trend Micro's research was also presented in full at the Black Hat Asia 2023 security conference held in Singapore in early May 2023, so keep an eye on YouTube for a possible recording of the presentation.
In the meantime, the company's research also highlights the lack of security guardrails and best practices in the Android OEM ecosystem and the dangers of buying a low-cost device from a no-name vendor.
Reports on the Guerilla malware have been available online since 2018, yet the Lemon Group has continued to operate undisturbed and unabated.
The problem of pre-installed Android malware doesn't go away just by shining a light on vendors with bad security. The best example of this is the case of Allwinner Android-based TV boxes. Malware was found pre-installed on Allwinner devices earlier this year, and the devices are still on sale on online stores like Amazon. Still infected.
Breaches and hacks
Suzuki cyber-attack: A cyber-attack on Suzuki's India plant has halted the production of motorbikes and scooters for more than a week. The incident took place on May 10 and is having a serious impact on Sukuki's business since the manufacturing facility in India provides almost half of the company's global vehicle output. Suzuki estimates to have lost production of over 20,000 units since the shutdown. [Additional coverage in Autocar India]
Swaprum crypto-heist: The operators of the Swaprum DeFi platform have been accused of using a backdoor function to steal more than $3 million of customer-deposited crypto assets before shutting down their project and disappearing. Commonly referred to as a "rug pull," the incident took place just weeks after the company's code was audited by blockchain security firm CertiK. CertiK told Decrypt that as an auditor, there's no guarantee customers make recommended changes.
Cyber insurance lawsuit: A North Carolina radiology group is suing its cyber insurance provider after its coverage lapsed two days before it was hit by a ransomware attack. Raleigh Radiology Associates sued the Arthur J. Gallagher insurance company last month, alleging the agency didn't notify it that its policy expired. The radiology group claims it submitted all the needed paperwork to have the insurance renewed but found out it wasn't only when it tried to file a claim related to the ransomware attack. The healthcare provider is seeking more than $1 million in recovery and lost revenue in costs related to the attack they feel the insurer should have covered. [Additional coverage in The Wall Street Journal]
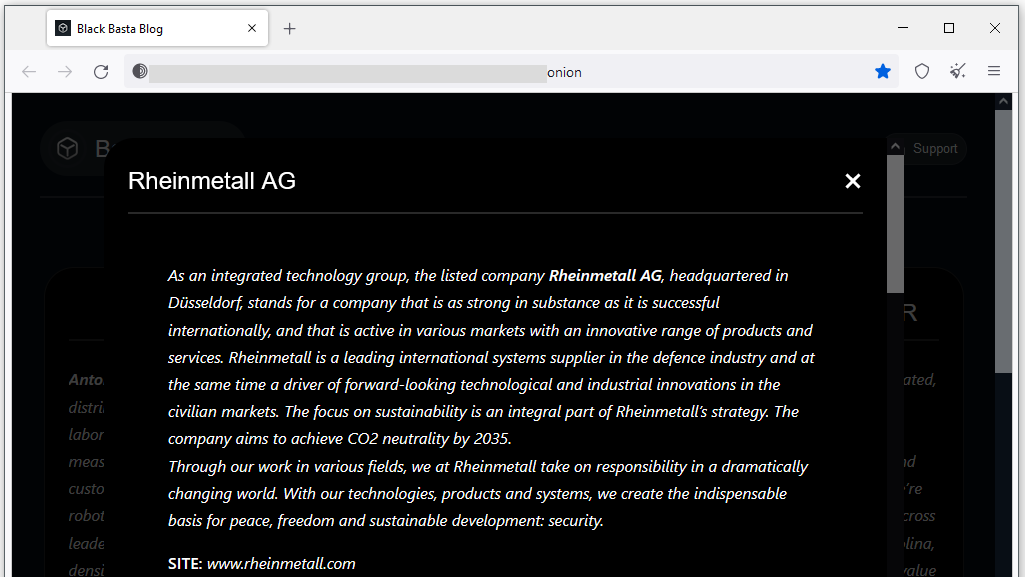
Rheinmetall claim: The Black Basta ransomware gang has listed Rheinmetall AG on their leak site. The German company is one of the world's largest weapons manufacturers and has recently announced plans to build tanks at a Ukroboronprom plant in Ukraine. The gang shared screenshots of a small number of documents perpetrating to have been stolen from the company's network. Rheinmetall has not confirmed the incident.
General tech and privacy
Apple bans ChatGPT internally: Apple has banned employees from using ChatGPT, Bard, or other similar Large Language Models (LLMs). The company is concerned that workers could accidentally upload and leak confidential data to rival companies. An accidental leak of proprietary information happened at Samsung's semiconductor division in late March, when employees shared internal procedures and code meant to identify defective chips with ChatGPT. Samsung banned the use of ChatGPT internally as a result. [Additional coverage in AppleInsider]
App Store Transparency Report: Apple has published the first-ever version of the App Store Transparency Report [PDF]—which appears to be the raw numbers behind this press release we featured in one of our past editions.
ASUS update borks routers: Taiwanese equipment vendor ASUS has confirmed that an error in a server configuration file has caused many of its routers to lose internet connectivity following a firmware upgrade. The botched configuration file was linked to the company's AiProtection, a feature that scans traffic for malicious URLs. The company has published instructions on how device owners can fix the issue on affected routers and upgrade the device with new and working firmware. On a similar note, HP is also in the midst of fixing its own bad firmware incident after a recent update borked HP Office Jet printers worldwide. And completing the treble in bad infrastructure management is Japanese tech giant Fujitsu, which issued an apology for its own gaffe as well. The company admitted that its MICJET customer servicing platform, installed in many Japanese municipalities, showed and issued wrong documents to users across the country.
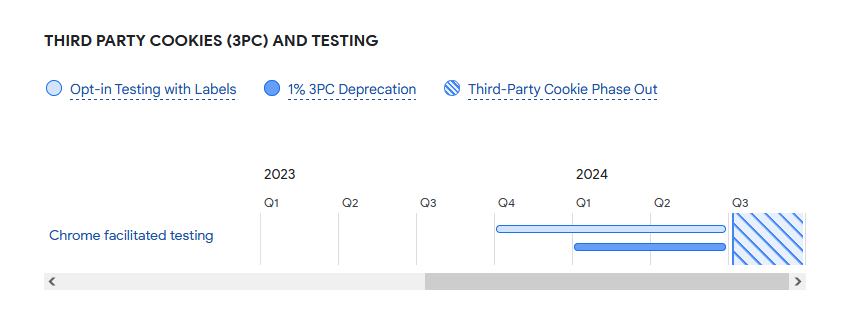
Privacy Sandbox rollout: Google will start rolling out its new Privacy Sandbox technology in the third quarter of this year, with the formal release of Chrome 115. The Privacy Sandbox is a collection of APIs that Google is making available in Chrome to online advertisers so they can deliver ads without collecting vast quantities of personal information about users and without tracking their movements across the web via third-party cookies. Google says that as part of the rollout, it will also remove support for third-party cookies from Chrome next year. Third-party cookies will be removed from 1% of the Chrome userbase in Q1 2024 and for all Chrome users by Q3.
Government, politics, and policy
China bars Micron chips: The Chinese government has barred critical infrastructure organizations from purchasing Micron chips. The Cyberspace Administration of China says the US chipmaker's products failed a security review. CAC announced it was going to review Micron chips for security flaws at the end of March, shortly after the US and its allies imposed trade controls to prevent the flow of advanced chips to the Chinese market.
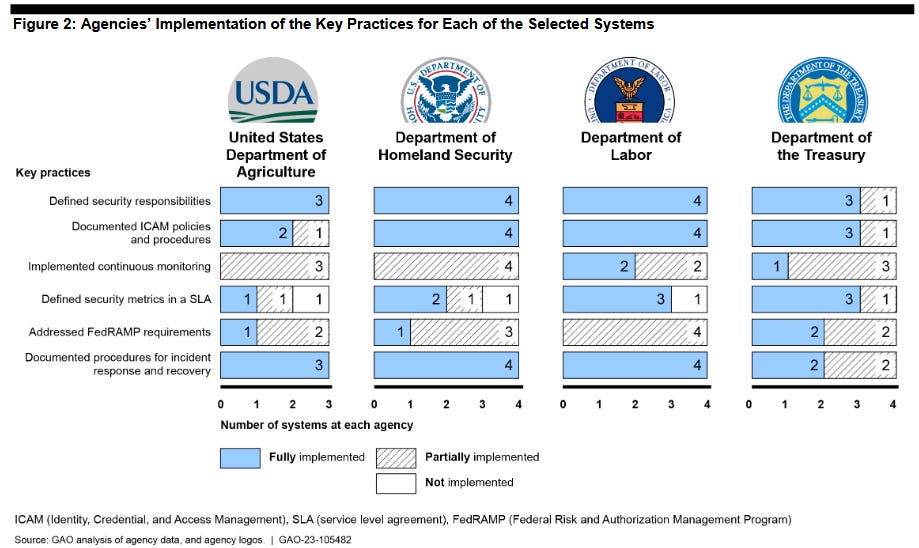
GAO cloud security report: A report by the US Government Accountability Office has found that the departments of Agriculture, Homeland Security, Labor, and Treasury are lagging in implementing crucial cloud security practices. GAO says it randomly selected the four agencies to see how federal agencies have been securing their cloud infrastructure across six key cloud security practices. GAO made 35 recommendations to the four agencies.
FISA misuse: The FBI improperly searched the personal communications of Americans more than 300,000 times between 2020 and early 2021, according to newly declassified documents released by the Senate Intel Committee. The inappropriate searches occurred under the Foreign Intelligence Surveillance Act (FISA), currently up for renewal in the US Congress. The documents reveal the FBI used the massive trove of communications data gathered using FISA powers to search for information on participants who attended the George Floyd protests and the January 6 storming of the US Capitol. The FBI also searched the names of more than 19,000 donors to political campaigns for plausible connections to foreign governments. [Additional coverage in The Record]
FTC to expand HBNR: The US Federal Trade Commission has proposed changes to the Health Breach Notification Rule (HBNR) in an effort to clarify the law's language. The changes specifically target companies that collect health data via mobile health apps, fitness trackers, and other direct-to-consumer health technologies. Under the new rules, app makers will have to get a user's permission before they share their data, and they'll also have to notify their users, the FTC, and the general public when they suffer a data breach. The proposed FTC changes to the language of the HGNR come after several cases of health apps accidentally or intentionally sharing health data with online advertisers.
DoD zero trust: David McKeown, the DOD's deputy chief information officer, says the Defense Department is on track to implement its zero trust cybersecurity framework by fiscal year 2027 as planned.
Utah security audit: Utah's Office of the Legislative Auditor General has published an audit [PDF] of the state's cybersecurity posture.
Sponsor section
This edition is brought to you by Thinkst Canary. Most companies find out way too late that they've been breached. Thinkst Canary changes this. Deployed and Loved on all seven continents. Thinkst Canary. Deploys in minutes; almost zero admin overhead. It just works!
Cybercrime and threat intel
Mexico charges govt officials in Pegasus probe: Mexico's Attorney General has charged four former government officials as part of an investigation into the country's purchase of the Pegasus spyware in 2014. Charges were announced against Tomás Zerón (former head of Mexico's Criminal Investigation Agency), Vidal Díazleal (former chief of Mexico's Federal Ministerial Police), and Judith Araceli Gómez Molano and Rigoberto García Campos, two former senior law enforcement officials. The Attorney General says the former officials "illegally acquired" access to the Pegasus spyware for 460 million pesos ($26 million). The four are charged with embezzlement, fraud, abuse of power, and criminal association. According to local media, Zerón is currently living in Israel, and authorities are already seeking his extradition in a separate case.
Golden Chickens: eSentire has updated an August 2022 report where the company claimed to have identified the person behind the Golden Chickens Malware-as-a-Service (MaaS) as "badbullzvenom," a Moldavian national living in Canada. In a new report published last week, eSentire says they identified the second person behind the Golden Chickens service, a hacker going by the name of "Jack," currently living in Bucharest, Romania. The security firm says it notified authorities and also attached a "high confidence" rating to its latest attribution report.
DataBox arraigned in court: A Dutch hacker was arraigned in an Amsterdam court last week and formally charged by Dutch officials. Twenty-five-year-old Erkan S. was accused of selling hacked data on the now-defunct RaidForum, where he operated under the pseudonym of DataBox. Officials say the suspect sold the data of more than 9 million Austrians he stole from a tax filing service, the medical information of 4.4 million Colombians, and the user database of e-commerce giant Lazada. In total, he advertised at least 16 databases, which he sold for a few thousand euros each. He also stands accused of laundering more than €700,000 in cryptocurrency. Dutch prosecutors are seeking a four-year prison sentence. [Additional coverage in AD.nl / English coverage in DataBreaches.net]
FIN7 returns: Microsoft's security team says the FIN7 cybercrime group has come out of a long period of inactivity and is currently attacking and breaching organizations to deploy a version of the Clop ransomware. Microsoft notes the attacks are the gang's first ransomware campaign since late 2021. In a report at the time, Microsoft said that a FIN7 subgroup named Elbrus had created and ran the now-defunct Darkside and BlackMatter RaaS operations. Before that, FIN7 members worked as affiliates for the REvil and Maze operations. Last year, SentinelOne said it found evidence of a FIN7 member working with the BlackBasta ransomware.
Taiwan activity: Trellix saw a rise in malicious emails targeting Taiwan. This includes not just regular APT operations but also cybercrime activity. Malware spotted distributed to Taiwanese users includes PlugX, Kryptik, Zmutzy, and Formbook.
BEC on the loose: In the fourth edition of its Cyber Signals report, Microsoft says it saw a 38% increase in CaaS (Cybercrime-as-a-Service) providers targeting business email operations between 2019 and 2022.
"While threat actors use phishing-as-a-service like Evil Proxy, Naked Pages, and Caffeine to deploy phishing campaigns and obtain compromised credentials, BulletProftLink offers a decentralized gateway design, which includes Internet Computer public blockchain nodes to host phishing and BEC sites, creating an even more sophisticated decentralized web offering that's much harder to disrupt."
VCaaS overview: Threat intel giant Recorded Future has published an overview of the major Voice-Cloning-as-a-Service offerings available on the underground cybercrime ecosystem. Popular solutions include custom-built tools advertised via Telegram channels but also the abuse of legitimate tools like ElevenLabs' Prime Voice AI service.
Phone Link spouseware abuse warning: Mobile security firm Certo warns iOS users to be careful about Microsoft's Phone Link app being installed on their devices. The app has been available for years and has allowed Android users to sync their data to their Windows 10 and Windows 11 computers. Certo says that since April 2023, the app can also sync data from iOS devices as well, which opens the door to being abused to spy on unwitting victims.
WordPress exploitation: Sucuri has detected more than 1,600 WordPress sites that have been hacked using a recently disclosed vulnerability (CVE-2023-32243) in the Essential Addons for Elementor plugin. More than one million WordPress sites are using the plugin, which is currently seeing heavy exploitation. Sucuri says the attacks appear to be carried out by the same gang behind Balada, an active WordPress malware campaign that has been active since 2017.
KEV update: CISA has updated its KEV database with three new vulnerabilities that are currently being actively exploited. Two of them are old Cisco bugs from 2004 and 2016, respectively. The third is a Samsung kernel vulnerability (CVE-2023-21492) that Google's TAG team detected exploited in the wild against users of the Samsung Internet Browser in December 2022. At the time, Google said the attacks targeted UAE residents and were carried out using the Heliconia Framework, a hacking platform developed by Spanish commercial spyware vendor Variston.
PyPI suspends creation of new accounts and packages: The Python Foundation has suspended new user registrations and new package uploads on the official Python Package Index, also known as PyPI. The organization's security team says PyPI saw another wave of malicious packages being uploaded on the platform over the last week. PyPI staff says the incident occurred while some of its members were on leave, and current personnel was quickly overwhelmed by the large number of reports and malicious packages they had to remove. Existing users can still access and update their projects.
New npm malware: Nine new malicious npm packages were spotted last week. Check out GitHub's security advisory portal for more details.
Malware technical reports
Ransomware in Russia: FACCT (formerly Group-IB's Russian division) has a technical analysis on LokiLocker and DarkBit, two ransomware strains that have been spotted attacking Russian companies. Both LokiLocker and DarkBit have been previously linked to Iranian groups operating with state backing.
Minas: Kaspersky's GReAT has discovered a new strain of malware that was used in an attack in June 2022. Named Minas, the malware's primary purpose appears to be cryptocurrency mining.
AMOS: K7 Computing published a report on AMOS, a macOS infostealer, also known as the Amotic macOS Stealer.
Amadey Bot: Embee researchers have identified 12 command and control servers for the Amadey Bot malware via Censys and Shodan.
Laplas: Embee researchers have identified 27 command and control servers for the Laplas clipper via Censys and Shodan.
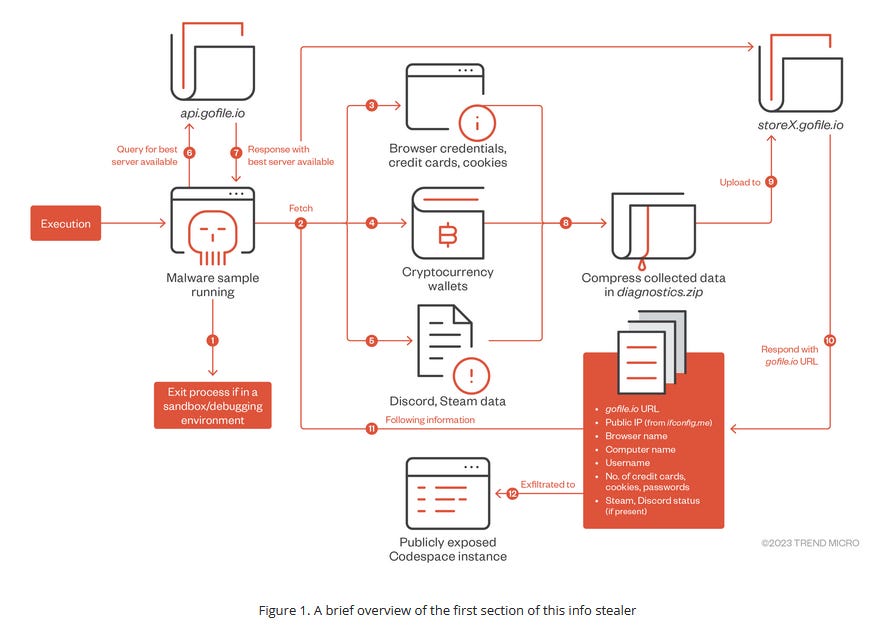
Rust-based infostealers: Trend Micro has a breakdown of a Rust-based infostealer that abuses GitHub's Codespaces feature to community cate with its C2 and exfil data.
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
APTs and cyber-espionage
CloudWizard APT: Kaspersky researchers found evidence to connect a recently discovered APT group named CloudWizard (previously BadMagic) to an older 2016 cyber-espionage campaign known as Operation Groundbait [PDF]. At the time, ESET concluded that "the attackers most likely operate from within Ukraine." Kaspersky didn't conclusively link CloudWizard to Ukraine but pointed out that the group targeted both pro-Ukraine and pro-Kremlin entities located in the Donetsk, Luhansk, and Crimea regions.
ScarCruft: Qihoo 360 has a report on recent APT-C-28 (ScarCruft) activity deploying the RokRat malware.
Blind Eagle & Hagga Group connections: Chinese security firm QiAnXin has published a report highlighting possible connections between the Blind Eagle and Hagga Group threat actors. Based on a previous Yoroi 2020 report, QiAnXin believes Blind Eagle operators may be renting access to Hagga Group's hacking services.
Vulnerabilities and bug bounty
KeePass vulnerability: A security researcher has published proof-of-concept code that can allow attackers to extract the master password of a KeePass password manager in clear text. KeePass has confirmed the vulnerability (CVE-2023-32784) and promised a fix in version 2.54, expected to be released in early June. The researcher says that once a fix is out, users should also change their master password and delete various KeePass artifacts such as OS crash dumps, OS hibernation files, pagefile/swapfile, and others. KeePassX is not vulnerable.
Zyxel PoC: Rapid7 has published a detailed write-up and PoC for CVE-2023-28771, an unauthenticated command injection bug in the WAN interface of Zyxel network devices. Zyxel released patches last month.
Pimcore vulnerability: SonarSource researchers have discovered a vulnerability (CVE-2023-28438) in the Pimcore CMS. The bug is a combination between a path traversal and an SQL injection.
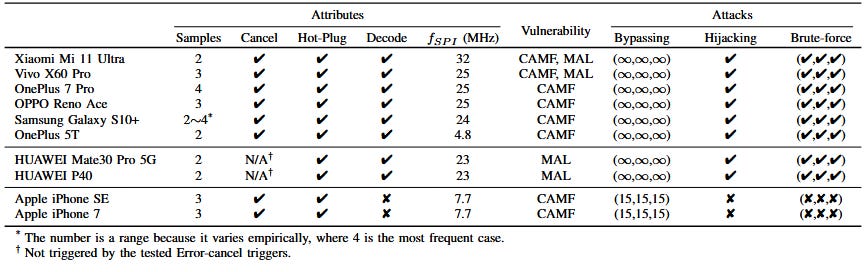
BrutePrint: A team of academics has published details about BrutePrint, an experimental technique that can be used to brute-force fingerprint authentication on some modern smartphones. The researchers claim their BrutePrint toolkit uses two zero-day vulnerabilities in the smartphone fingerprint authentication (SFA) framework to bypass smartphone security features such as rate limits and finger liveness detection. They claim the BrutePrint toolkit brute-forced fingerprints on eight of the ten tested smartphones, such as Samsung, Xiaomi, OnePlus, Huawei, Vivo, but not the iPhone (see table below).
Android lockscreen bypass: Security researcher Jose Rodriguez has discovered a way to abuse the Google Maps driving mode to bypass the Android lockscreen on Samsung and Xiaomi devices.
Infosec industry
KSG layoffs: The Krebs Stamos Group has laid off six people. Founded in 2021, the firm had less than 20 employees before this round of layoffs, according to TechCrunch.
CircleCityCon: The organizers of the CircleCityCon security conference have announced that this year's edition, to be held in late June, will be held in a virtual format after they failed to raise the necessary funds. This edition will also be the conference's last.
PHDays 12 videos: Talks from PHDays 12, Russia's largest cybersecurity conference, which took place last week, are available on YouTube.
CloudNativeSecurityCon 2023 videos: Talks from the CloudNativeSecurityCon 2023, which took place in February, are now available on YouTube.
Mod call: /r/netsec is looking for a mod.




