Risky Biz News: Albania-Iran cyber drama far from over
In other news: Another Predator victim found in Greece; Kaseya ransomware suspect pleads guilty; and Dutch phisher continues phishing from prison cell.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Two days after the Albanian government severed diplomatic ties with Iran, accusing the Tehran regime of using its hackers to cripple the IT networks of several of its government agencies on July 15, Albania has been hit by another major cyberattack, and officials are once again pointing the finger at Iran.
The attack took place on Friday, September 9, and hit TIMS (Total Information Management System), an IT platform belonging to Albania's Ministry of Interior used to keep track of people entering and leaving the country.
Six border crossing points were impacted and experienced border crossing stoppages and delays for at least two days until the TIMS platform was restored, according to a series of tweets from Albania's Minister of the Interior, Bledi Chuchi.
This included five land crossings with Greece, Kosovo, and Montenegro at Hani i Hoti, Kapshtica, Muriqan, Morinë, and Kakavijë, but also the border crossing point at the Rinas Airport near Tirana, Albania's capital.
Ministry officials blamed the attack on "the same hand" that hit Albania's IT network in July, an attribution that was also backed up by the White House a few hours later.
The United States condemns the September 9th cyberattack against our NATO Ally, Albania. This malicious activity against Albania follows the July 15 cyberattack conducted by the Government of Iran. The U.S. government is supporting Albania’s efforts to mitigate and recover.
— National Security Council (@WHNSC) 2:05 AM ∙ Sep 11, 2022
The second attack not only comes after Albania cut diplomatic ties with Iran and expunged its embassy officials from the country but also after NATO and its individual members also issued stern statements condemning Iran's actions as a violation of international cyber norms since the attack also impacted civilian infrastructure.
The stern statements were also followed on Friday by economic sanctions imposed by the US Treasury against Iran's Ministry of Intelligence and Security (MOIS) and its leader Esmail Khatib, Iran's minister of intelligence, who US officials said ordered the operation.
In a statement published on Twitter, Iran's Mission to the EU accused NATO and its members of hypocrisy because they remained silent when Iran was the victim of cyberattacks against its infrastructure and nuclear facilities (most likely referring to the Predatory Sparrow and Stuxnet attacks). In addition, Iran accused NATO of harboring terrorists, referring to Albania hosting members of MEK, an Iranian political opposition party that was moved to a camp in Albania at the request of the US government after the Tehran regime proclaimed it a terrorist organization and started hunting and imprisoning its members. As Mandiant and Microsoft explained in their reports, Albania hosting MEK members was the main reason Iran carried out its July attack.
PRESS RELEASE of the Embassy of the Islamic Republic of Iran in Brussels on the Statement by the North Atlantic Council date 08 September 2022.
— IranMissionEU (@IranmissionEU) 12:33 PM ∙ Sep 9, 2022
@NATO #Iran #NATO #Press_Release
With new attacks taking place, even in the aftermath of the worse political response and fallout related to a cyber-attack, this story is far from over, and we're expecting more cyber drama.
Breaches and hacks
Crypto-heist #1: The New Free DAO (NFD) token lost 99% of its value after a threat actor used a flash loan attack to steal more than $1.25 million worth of crypto from the platform. According to blockchain security firm CertiK, the hacker appears to be the same attacker who also hit DeFi platform Neorder four months ago.
Crypto-heist #2: The operators of the Gera cryptocurrency suspended operations last week after a hacker gained control over the platform's smart contract after developers leaked the private key. According to the Gera team, the attacker minted $1.5 million worth of crypto, which they later transferred to their own Ethereum address. The platform has not yet resumed operations.
Dear GERA holders,
— Gera Coin (@GeraCoin) 3:43 PM ∙ Sep 7, 2022
It has come to our attention that the GERA token’s security has been compromised due to a private key leak. Hackers transferred ownership of the GERA token’s smart contract deployer to another address: “0x510E4d61663bE6a24D600AaF90F892dd8c8C61dC”.
Samsung sued over its breach: Samsung is facing a class-action lawsuit over its July 2022 security breach, which the company disclosed just days before.
Ransomware attack knocks down Kentucky ISP: A ransomware attack knocked out Bardstown Connect, a Kentucky-based internet service provider, for 18 hours on September 2, during the extended Labor Day weekend. Roughly 13,000 locals had their internet connectivity disrupted during the incident, the ISP said.
OT hacks in Israel: Security firm Otorio has published a blog post looking at claims made by hacktivist group GhostSec that they hacked and took control over 55 Berghof PLC devices in Israel. The company appears to confirm the group's claims but says the hackers didn't seem to realize what they've done and the capabilities they had access to.
The fact that the HMI probably wasn't accessed, nor manipulated by GhostSec, and the hackers were not exploiting the Modbus interface, shows an unfamiliarity with the OT domain. To the best of our knowledge, GhostSec hadn't brought critical damage to the affected systems, but only sought to draw attention to the hacktivist group and its activities.
Crimean TV stations hacked (again): Pro-Ukrainian hacktivists hacked on Friday Russian TV networks in Crimea to broadcast a public address by Ukrainian President Volodymyr Zelensky. In addition, the hackers also included details for the population to act in case of a Ukrainian military attack to return the region to Ukraine's control. This marks the second time Ukrainian hackers defaced Russian TV stations in Crimea after a similar incident on August 20. Four days later, on Ukraine's independence day, Ukrainian hackers also hacked IP security cameras across Crimea to play Ukrainian patriotic songs as well.
Ukraine has hacked Russian TV networks in Crimea
— Jay in Kyiv (@JayinKyiv) 10:59 AM ∙ Sep 9, 2022
General tech and privacy
White House tech upheaval: The White House published six principles last week that it plans to use in future legislation to reform tech policies across the US. This includes reforms aimed at competition among tech companies, algorithmic discrimination, transparency around algorithms, online privacy, safety on social platforms, and changes to Section 230.
HTTPS-Only expands: After the main Tor Browser (for desktop) removed the HTTPS Everywhere extension and enabled the HTTPS-Only mode by default for its users, this change has also started rolling out for Tor Browser for Android users since last week.
Government, politics, and policy
CIRCIA open consultation period: CISA has asked members of the private industry to provide feedback on the upcoming Cyber Incident Reporting for Critical Infrastructure Act, or CIRCIA. Approved and signed into law in March by President Biden, CIRCIA will be formally published in the Federal Register on Monday, September 12, after which the public has 60 days to file feedback. CISA said this feedback is important in its efforts to implement the legislation into practice. CIRCIA contains mandatory rules for reporting cyber incidents and ransom payments.
👉Excited about this! Cyber incident reporting will be a game changer for the cyber defender community & we need your feedback to create a process that works. cisa.gov/CIRCIA go.dhs.gov/Z4h
— Jen🛡Easterly (@CISAJen) 2:51 PM ∙ Sep 9, 2022
public-inspection.federalregister.gov/2022-19551.pdf
Warning about the upcoming Dutch intelligence law: Bert Hubert, a member of TIB, a government board that checks the legality and approves communications interception warrants for the Dutch intelligence and security services, resigned last week. In a blog post explaining his decision, Hubert cited upcoming changes that will most likely be approved to the country's intelligence laws. Under these changes, the TIB will lose its approval power and will only be able to review interception warrants after the fact, which Hubert views as a red flag since TIB flagged several cases of abuse last year that targeted journalists and several cases of broad warrants that intercept bulk traffic over entire global internet cables.
Another Predator victim emerges in Greece: Meanwhile, the spyware scandal in Greece has gotten even hotter. Last week on Friday, Greek reporters from DocumentNews said they discovered a third high-profile victim that was targeted with Predator, a high-grade spyware strain developed by North Macedonian company Cytrox. The victim is Christos Spirtzis, a member of the Greek Parliament on behalf of Syriza, the largest opposition party in Greece. The previous two victims were Nikos Androulakis, a member of the EU Parliament and the president of Greece's second-largest opposition party (PASOK), and Thanasis Koukakis, a local finance journalist who was investigating government corruption.
Τα δύο μηνύματα που έλαβε ο Χρήστος Σπίρτζης από #Predator
— Eliza Triantafillou (@e_triantafillou) 8:46 AM ∙ Sep 9, 2022
Όπως και στην περίπτωση του @nasoskook και του Νίκου Ανδρουλάκη, το ένα λινκ είναι παραλλαγή του μπλογκ edolio5. Το άλλο της Εφημερίδας Συντακτών.
Westlessness: An academic paper takes a look at the rising influence of the Global South in the global cyber governance model with countries such as China, Singapore, and South Korea, and regions like ASEAN and Latin America attempting to shape cyber-norms according to their own views, instead of relying on the rules set by the Global North (US&EU).
Sponsor section
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. Last week, the company launched a new product called Sensitive Command Canarytoken, a simple canary token that sends an alert every time any command you choose as "sensitive" or "malicious" is executed on your host.
Cybercrime and threat intel
Phishing from prison: Dutch authorities said on Friday that they sentenced a 23-year-old from the city of Groningen to 44 months in prison for running a phishing operation from his jail cell. Authorities said that while the suspect was executing a previous 42-month prison sentence for a previous phishing operation, he continued to run campaigns to defraud users from jail with the help of at least four smartphones that were smuggled into the prison. Authorities said they also charged a second man, a 22-year-old from Hoogezand, who worked to maintain phishing panels for the suspect while he was in jail, and a third suspect is also on trial on similar charges.
Kaseya suspect pleads guilty: Yaroslav Vasinskyi, the Ukrainian national charged with executing the ransomware attack against Kaseya, has decided to plead guilty in a notice filed with the court. (via Jeff Stone)
Crypto-fraud in India: Indian law enforcement issued a warning on Friday about a cybercrime group operating fake crypto-trading websites and instant loan lending apps that steal funds from their customers. Officials said the gang has currently stolen more than Rs 4,200 crore ($525,000) from victims this year and that based on current evidence, the gang seems to be working together with other suspects based in China.
Crypto-fraud in Romania: Similarly, Romanian law enforcement raided two penthouses in Bucharest and detained three suspects. According to a joint investigation with the UK's NCA, the suspects would contact victims of cryptocurrency fraud and defraud them again by posing as financial fraud recovery organizations and asking for a fee to recover the initial losses.
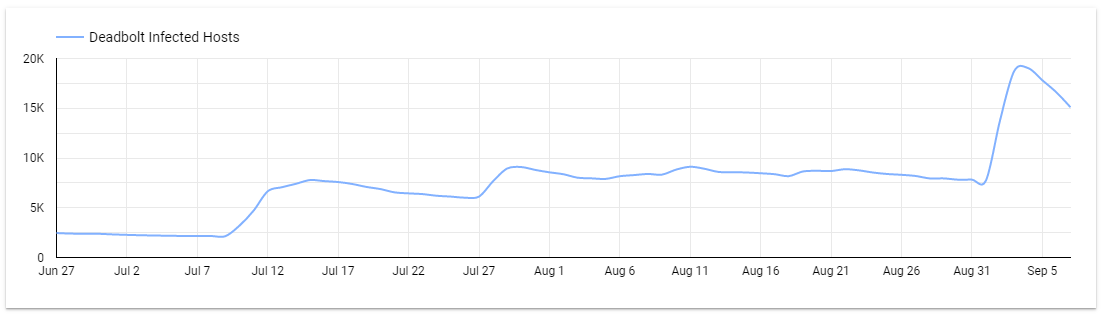
Deadbolt infections explode: According to data compiled by IoT search engine Censys, the number of QNAP NAS devices infected by the Deadbolt ransomware has spiked from 2,144 on July 9 to 19,029 on September 4. The spike comes after the Deadbolt gang exploited a zero-day vulnerability in the Photo Station app installed on most QNAP NAS systems.
Malware technical reports
BUGHATCH: Elastic's security team published a report last Friday on BUGHATCH, a backdoor and dropper previously used in campaigns that deployed the Cuba ransomware. [Also see this older report from Mandiant]
Lampion: Cofense researchers said they are seeing new malspam campaigns distributing Lampion, a rare banking trojan that hasn't been seen in active campaigns since this spring and even rarer before that.
Monti ransomware: Blackberry's security team has published a technical report on the new and emerging Monti ransomware strain, which, based on its name, is an obvious clone built on top of the leaked Conti ransomware source code.
"MONTI strain"
— MalwareHunterTeam (@malwrhunterteam) 7:45 PM ∙ Jun 30, 2022
Not only the note has parts of the note that Conti gang used, the encrypted files seems similar to encrypted files by a Conti version, so possible code reuse...
🤔
APTs and cyber-espionage
APT29: Security researcher Lina Lau describes a technique to detect if Russian cyber-espionage APT29 has used the SDelete utility to wipe files on your system and hide traces of their intrusion.
1\ #DFIR: Russian IRON HEMLOCK (APT29) is still abusing sdelete to wipe attacker files as defence evasion.
— InverseCos ᐡ ꒳ ᐡ (@inversecos) 6:52 AM ∙ Sep 6, 2022
sdelete tool overwrites filenames with 26 alphabetic entries "AAAA.AAA"... but this is how you can recover the original filename 👇
inversecos.com/2022/09/forens…
APT magic quadrant: In this month's silliest marketing material, Qihoo 360 has built a magic quadrant thingey for APT groups based on their sophistication and level of activity. If the APT names sound new and weird, they're based on this list.
Russia's cyberwarfare capabilities: The Center for European Policy Analysis (CEPA) has published a comprehensive report that attempts to map Russia's cyber landscape and its intricate web of actors, which include government intelligence services (GRU, FSB, SVR), underground cybercrime groups, and private security firms (Digital Services, Positive Technologies), entities the Russian government uses to bolster its cyber capabilities. The report's conclusions are below:
- Coordinated through a set of political processes centered on the Presidential Administration and the Security Council, rather than a traditional, military-style command structure;
- Characterized by significant overlap in mission and capability, often leading to competition for resources and sometimes to problems of coordination and conflict;
- Subject to a significant degree of informality and political maneuvering, as different actors report to the Presidential Administration and Security Council via different channels and with differing degrees of accountability; and
- Heavily dependent on the private sector for training, recruitment, and technology, leading to a high degree of informal interagency integration at the grassroots level.
Vulnerabilities and bug bounty
Jenkins security updates: The Jenkins security team has published security updates to fix a vulnerability in Jetty, one of its core components.
Misconfigured servers rule the internet: According to the 2022 State of the Internet Report, a report from IoT search engine company Censys, misconfigurations accounted for 60% of the issues observed across internet-exposed services. Vulnerable software only accounted for 12%.
HPE vulnerabilities: The Binarly security research team said it found vulnerabilities in the firmware of HP enterprise devices. The company presented its findings at the Black Hat security conference and said that HP fixed six bugs related to code execution in System Management Mode (SMM) but that patches are not broadly available.
Unfortunately, at the time of writing, some HP enterprise devices (laptops and desktops) have still not received updates to patch the aforementioned vulnerabilities, despite them being publicly disclosed for over a month.
AWS Firecracker vulnerability: Researchers from Grapl have cracked Firecracker, a virtualization technology open-sourced by the AWS team that can deploy and monitor lightweight and secure micro-VMs. Read more about the novel vulnerability here.
Excellent deep dive into Firecracker security, and the subtleties that come with multiple memory regions on x86. "Ultimately, we walk away from this research with a very positive view of Firecracker"
— Marc Brooker (@MarcJBrooker) 12:20 AM ∙ Sep 9, 2022
Infosec industry
New tool—Qemuno: Cybersecurity firm Sygnia open-sourced last week a tool named Qemuno. According to the company, Qemuno aims to help researchers execute red-team operations and evade detection of endpoint security solutions, even without the need for administrative privileges.
New tool—Sandbox Scryer: Crowdstrike open-sourced earlier this month a tool named Sandbox Scryer that can take detonation data from security sandbox tools and generate threat hunting and intelligence data, including in the MITRE ATT&CK format.




