Risky Biz News: ACEMAGIC mini PCs shipped with pre-installed malware
In other news: North Korean hackers are stealing semiconductor secrets; JetBrains tries to hide a security patch; and the US sanctions Intellexa and its founder.

This newsletter is brought to you by Corelight. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Chinese company ACEMAGIC has confirmed that early batches of some of its new mini PC models were shipped with pre-installed malware.
Malware such as the Redline infostealer and the Bladabindi backdoor were found in the Windows OS system recovery section of its mini PCs. In some cases, malware was also found in the mini PCs' RGB lighting driver.
The infections were initially found by YouTube hardware review channel The Net Guy Reviews, later confirmed by The Gadgeteer and reconfirmed by other reviewers and some of the company's customers.
Based on public comments, the malware seems to have made its way on ACEMAGIC mini PC models such as S1, AD08, and AD15.
The company has never confirmed which models were impacted, but based on its statement, it appears that all models may have had issues.
In a rare sight among modern tech companies, ACEMAGIC took full blame for the incident, confirming that its software engineers cut some corners and bolted some unverified code on top of the Windows OS that shipped with the devices.
While ACEMAGIC didn't go into details, The Net Guy Reviews says the malware was in a section of the mini PC's installer that allowed customers to install Windows 11 with a local account and without a Microsoft profile, a widely known gripe with Microsoft's new Windows 11 OS.
All signs point to ACEMAGIC grabbing some code off the internet and plugging it into their custom installer without reviewing it or scanning for malware.
The company says the incident only affected "a specific batch of mini PCs," most of which were sold in Europe and the US. It claims it removed the malware from its code since the reports in early February.
Breaches, hacks, and security incidents
Ukraine hacks Russia's Defense Ministry: Ukraine's military intelligence agency claims it successfully hacked Russia's Defense Ministry. Ukraine's Defence Intelligence Main Directorate (GUR) says it obtained data on Russia's military encryption software. The GUR says it also obtained documents exchanged between more than 2,000 units of Russian security services. Ukrainian officials say the documents have helped to recreate the full structure of the Russian Defense Ministry. The GUR claimed they gained access to the network via one of Sergei Shoigu's deputies.
AlphV exit scams after Change Healthcare payment: The AlphV ransomware gang has exit-scammed after receiving a huge ransom payment from US healthcare platform Change Healthcare. AlphV admins listed a fake FBI seizure banner on their dark web leak site and are selling the ransomware's source code on hacking forums. The new development comes after security firms spotted a $22 million payment to the gang's Bitcoin wallets. Posts on underground hacking forums from AlphV members accused AlphV admins of taking the Change Healthcare ransom and running away without dividing the profits. [Additional coverage in DataBreaches.net]
General tech and privacy
Twitter exposes user's IPs: Twitter's new voice calling feature leaks users' IP addresses. Threat actors can obtain any user's IP address just by initiating a call. All users are impacted after Twitter rolled out and enabled the feature by default for all accounts last week. Privacy groups are warning the feature could be used to deanonymize dissidents in and by oppressive regimes. [Additional coverage in iNews]
Government, politics, and policy
US sanctions Intellexa again: The US government has sanctioned Intellexa and two of its executives for the company's role in developing and selling the Predator spyware. Sanctions were imposed on five companies part of the Intellexa Alliance, including its Cytrox branch, which develops and maintains the Predator platform. Sanctions were also levied on Intellexa founder Tal Dilian and corporate off-shoring specialist Sara Hamou. These are official economic sanctions. The US previously added four Intellexa and Cytrox entities to its export entity list in July of last year.
Call for ransomware payments ban: In an op-ed, Ciaran Martin, former chief executive at the NCSC, as called for the UK government to ban ransomware payments.
Cybersecurity olympiad: Romania's cybersecurity agency and Ministry of Education are holding the country's first-ever olympiad on cybersecurity topics. The contest follows the pattern of regular school olympiads, starting with regional city and state contests before a national-level competitive exam for the best students. The winner will have the chance to be part of Romania's team for ENISA's European Cybersecurity Challenge (ECSC).
EU telco cyber resilience: The European Union has published a report on the cybersecurity and resiliency of the EU communications infrastructures and networks. [h/t Ravi Nayyar]
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Vijit Nair, Corelight's VP of Product, about how cloud security was once an afterthought but is now on the improve.

Cybercrime and threat intel
Threat/trend reports: Some infosec reports covering industry threats and trends came out from Kroll and Positive Technologies.
Clever wallet drainer: The team at ScamSniffer has discovered a novel wallet drainer phishing kit that contains features allowing it to bypass security alerts on phished accounts and silently steal funds.
GitHub abuse for malware ops: OALABS looks at a malware campaign using a cloned game cheat website, SEO poisoning, and a bug in GitHub to trick would-be-game-hackers into running Lua malware.
RAT campaigns: Zscaler and CyFirma have analyzed several malware campaigns distributing various RATs to Windows and Android users.
Rappler CEO scam: Qurium has published a report on a campaign that is using deep fake videos of Rappler CEO Maria Ressa to scam users out of their Bitcoin. The NGO has tied the campaign to a Russian-based scam group.
"Russian controlled infrastructure was used to set up the clone articles that featured the deepfake of Maria Ressa promoting Bitcoins. Although the deepfake video followed the rule book of a regular scam where a celebrity was used to promote Bitcoins, it was made by Russians, and disseminated to a Philippine audience to maligning Maria Ressa."
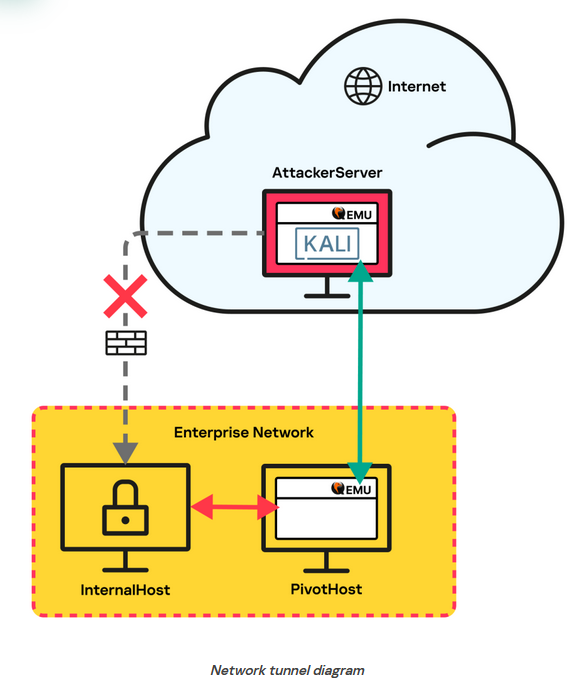
QEMU tunneling: Kaspersky researchers have spotted malware that uses QEMU emulators for tunneling and exfiltrating data out of compromised networks.
Malware technical reports
Terminator EDR killer: Sophos researchers say they are seeing an increase in usage of the Terminator EDR killer toolkit. Malware gangs use the tool to shut down EDRs and deploy their payloads undetected. The tool first appeared in cybercrime circles in early 2023. It was sold on cybercrime forums and then leaked online. Sophos says it has now seen multiple variations of the original Terminator EDR killer used in the wild over the past months.
Godzilla webshell: The DFIR Report team looks at a campaign that deploys the Godzilla webshell on hacked WordPress sites.
Copybara: Cleafy researchers have published a report on Copybara, an Android banking trojan installed on devices through various social engineering and vishing schemes. Its campaigns have currently targeted Spain, Italy, and the UK.
WogRAT: AhnLab has discovered a new remote access trojan named WogRAT distributed via a backdoored app named aNotepad. The malware is capable of infecting both Windows and Linux.
Snake: Cybereason researchers have published a technical analysis of Snake, a relatively new Python-based infostealer.
TA577 and PikaBot activity: After Intel-Ops published a report on new TA577 infrastructure last week, Proofpoint has also published a new report looking at the gang's latest campaigns. TA577 is a known email spam group. According to Proofpoint, the group's recent campaigns have distributed the PikaBot malware. Tony Lambert has a breakdown of these PikaBot versions here.
DarkGate: LogPoint takes a deep dive into DarkGate, the new darling of the malware loader scene.
RA World: Trend Micro analyzes RA World, a rebranded version of last year's RA Group RaaS platform.
8Base: Intel-Ops looks at 8Base, a ransomware group operating a RaaS platform on top of the leaked Phobos ransomware code.
GhostLocker 2.0: The GhostSec hacking group has launched a second version of its GhostLocker RaaS platform. The new version is written in Go and was co-developed with the Stormous ransomware group. Attacks using this new ransomware have already been spotted in the wild.
WinDestroyer wiper: Security firm CyFirma has discovered a new data wiper named WinDestroyer designed to render Windows systems unusable. CyFirma says the malware was developed for hacktivism against the backdrop of the Russia-Ukraine conflict. Researchers say that by investigating leaked databases, they identified the malware's creator as a Russian national.
Sponsor Section
James Pope, Corelight's Director of Technical Marketing Engineering, demonstrates the company's Open NDR Platform and how it combines network detections with a whole host of other data sources.
APTs, cyber-espionage, and info-ops
DPRK goes after ROK's chip industry: North Korean hackers have targeted South Korea's semiconductor industry, seeking to steal proprietary information. South Korean intelligence agency NIS says hackers targeted internet-connected servers seeking to gain entry to internal networks. North Korean hackers were successful on at least two occasions. NIS officials believe North Korea may have begun preparing to produce its own semiconductors to use for satellites and missiles.
APT37: Chinese security firm Anheng has looked at APT37 campaigns that targeted South Korean entities with political-themed phishing campaigns and the ROKRAT trojan.
Kimsuky goes after ScreenConnect: North Korean APT group Kimsuky is targeting ConnectWise ScreenConnect servers for access to corporate environments. Kroll researchers have spotted the group deployed the BabyShark malware on compromised networks. The attacks exploited two vulnerabilities patched by ConnectWise in mid-February. The same vulnerabilities are also widely exploited by ransomware gangs.
Vulnerabilities, security research, and bug bounty
RT-Thread vulnerabilities: HN Security has discovered ten vulnerabilities in RT-Thread, an open-source real-time operating system (RTOS).
VMware security update: VMware has published a security update to fix four vulnerabilities in its ESXi and Workstation products.
Hikvision security update: Chinese equipment vendor Hikvision has released a security update to fix two vulnerabilities in its HikCentral Professional security management platform.
Android Security Bulletin: Android security updates for March 2024 are out. No zero-days, and there are no security issues addressed in Google Play system updates (Project Mainline) this month.
Apple security updates: Apple has released version 17.4 of its iOS operating system. The new update patches four vulnerabilities, including two zero-days exploited in the wild. The two zero-days impact Apple's kernel and RTKit real-time OS framework, respectively.
KEV update: CISA has updated its KEV database with two new vulnerabilities that are currently actively exploited in the wild. The list includes a 2023 Android vulnerability and a 2021 bug in SureLino, an OS used in surveillance gateway products.
Memory-safety bugs: In the aftermath of the White House's executive order asking developers to use more memory-safe programming languages, Google has published a whitepaper on how the company looks at memory safety.
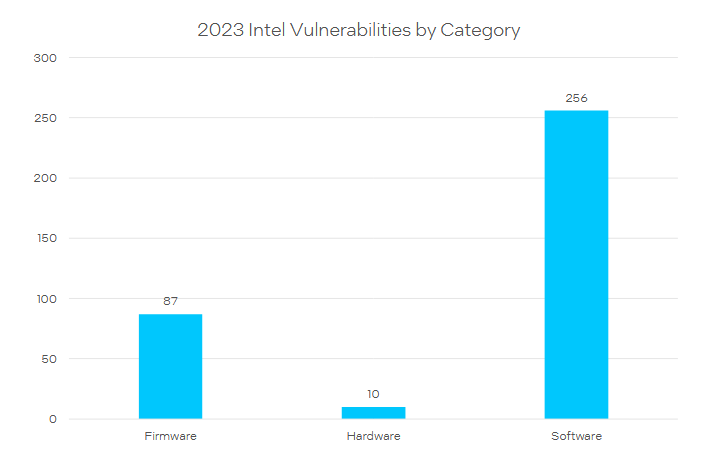
Intel bug bounty program: Intel says it patched 353 vulnerabilities across its products over the past year. The company says that only ten vulnerabilities were classified as hardware-related bugs. Eight of the ten impacted its CPUs, while the other two impacted its Arc graphics cards. More than 70% of bugs last year were rooted in its software, such as SDKs, drivers, and custom apps.
macOS API bug: Apple and macOS security expert Patrick Wardle has discovered a bug in one of the macOS APIs that could have allowed macOS malware to avoid detection and security tools. There is no evidence of in-the-wild exploitation (yet).
"So instead of fighting the efforts of the EU to make the Apple ecosystem more open and user-friendly, maybe Apple should instead make sure its code works in the first place? 🫣"
JetBrains tries to hide security patch: Software company JetBrains has released a security patch to fix two authentication bypass vulnerabilities in its TeamCity on-premises servers. The two vulnerabilities (CVE-2024-27198 and CVE-2024-27199) were discovered by Rapid7. The security firm accused JetBrains of releasing the software update without notifying customers about the presence of the two security flaws. JetBrains eventually published a blog post about the two issues after Rapid7's complaints. Attacks leveraging the two bugs began hours after Rapid7 published details on the bug, justifying JetBrains' reticence to disclose the issues without giving most customers the chance to patch.
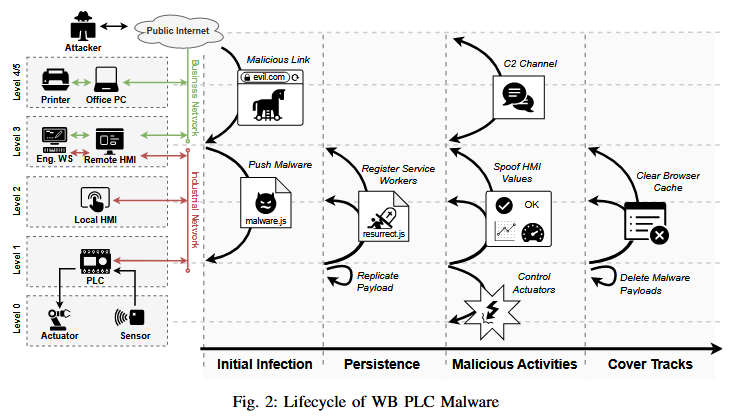
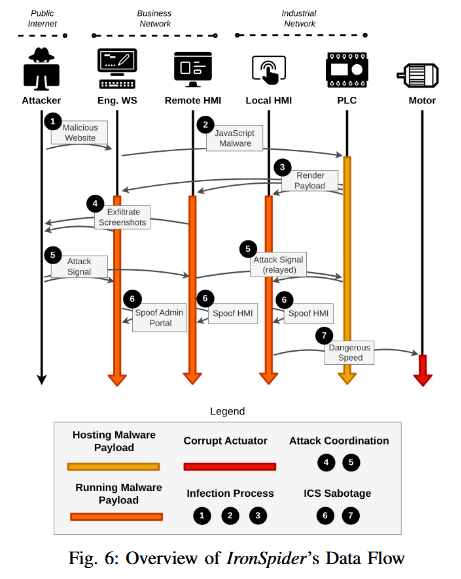
IronSpider attacks: A team of academics from the Georgia Institute of Technology says that remote Stuxnet-like attacks are now possible against many modern programmable logic controllers (PLCs). The team says that many modern PLCs come with embedded servers and a web interface that can be leveraged for a web-based delivery attack. They demoed the attack with a piece of malware named IronSpider that targeted Wago PLCs to sabotage industrial motors. [Additional coverage in SecurityWeek]
Infosec industry
Silly Iran is silly: Documents leaked from the Iranian government suggest the regime is considering security researcher Bob Diachenko—known for his work of security internet-exposed databases—as a very dangerous hackerman.
New tool—Tazama: The Linux Foundation has launched Tazama, an open-source software solution for real-time fraud prevention.
New tool—Excel Anonymizer: Software engineer Siddharth Bhatia has released Excel Anonymizer, a tool to synthesize, replace, and populate Excel files with anonymized data.
Free resource: CISA has published a free guide for university cybersecurity clinics.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the shift that has taken place in Ukraine's cyber strategy as it has gone on the front foot and its cyber forces have launched multiple cyber strikes in the last few months. They discuss reasons why Ukraine might want to make this change and ask whether it makes sense.




