Risky Biz News: Academics find a tiny crack in Apple's Private Relay
In other news: Neopets got hacked; Chile becomes latest government to get ransomed; and iOS apps leak AWS credentials way more than Android ones.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
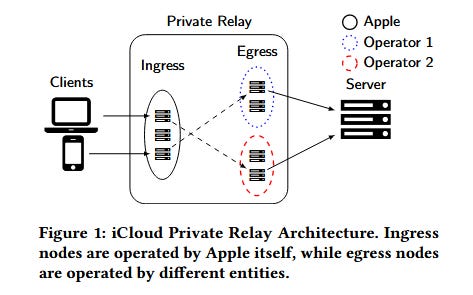
At its WWDC 2021 conference, Apple announced a new security feature named iCloud Private Relay that would work as a two-layer VPN-like system and hide a (paying) Apple user's IP address from their internet service provider and website owners.
At a technical level, iCloud Private Relay would do this by taking internet traffic from a user's Apple device—their iPad, iPhone, or macOS system—and sending it to a first group of servers (called ingress servers), which would then forward the traffic to a second group of servers (called egress servers) before finally connecting the user to the website or service they were trying to access.
This system means that ISPs would only see users connecting to the ingress servers while websites and online services would only see users connecting from the egress servers, effectively preventing both from seeing a user's full network traffic path.
Since its launch, iCloud Private Relay has been viewed as a major win for consumer privacy but has also seen criticism from major telecommunication providers.
While not a secret, very few consumers know that their ISPs are tracking their web browsing history and then reselling it to advertising companies as a secondary source of revenue.
Being blocked from seeing a user's full traffic path by something like iCloud Private Relay—when this goes live—would more than likely put quite a hole in the pockets of these companies and explains why several of them had tried to lobby EU regulators and get the technology banned even before it was going to be released. Looking at you, Vodafone, Telefonica, Orange, and T-Mobile! Some UK ISPs also pointed out that blocking CSAM content may be impossible and prevents them from blocking malicious traffic; hence Private Relay needs to go, similarly to how they opposed to the rollout of DNS-over-HTTPS a few years back.
All in all, it's a very strange thing for telco providers to lobby for, since iCloud Private Relay also encrypts traffic, including DNS queries, and works similarly to a VPN, but telcos have yet to complain about them or try to get them banned. As 9to5Mac's Benjamin Mayo explained earlier this year, this is because while VPNs have been around for years, they are not that widely adopted. But if Apple makes this available, you'll have a huge chunk of the internet's population moving to enable this feature, which even Apple said it was planning to enable by default for most users somewhere in the future anyway.
But in an academic paper pre-print published last month—entitled "Towards a Tectonic Traffic Shift? Investigating Apple's New Relay Network"—a group of German researchers said they spent months scanning the server infrastructure used by the iCloud Private Relay service.
In its official documentation [PDF], Apple said that one of the service's privacy features was all its moving parts, namely that its engineers would run the network of ingress servers while third-party partners would operate the egress layer, allowing the service to scale while still preserving user privacy, as no entity (besides itself, obviously) would be able to glean the user's full traffic path.
To prevent website operators from accidentally blocking the huge amounts of traffic that would soon be spewing out of its egress network, Apple made the list of all egress servers public.
Most likely to prevent shady ISPs (like these two beacons of user privacy) and oppressive governments from blocking users from connecting to its Private Relay service, Apple has kept the list of ingress servers secret.
But following their scans, a team of academics from the Technical University of Munich, Germany, said they were able to discover 1,586 IPv4 and 1,575 IPv6 addresses that Apple was using to onboard users into iCloud Private Relay.
While this opens the door for malicious entities to block Apple users from connecting to the service, this was an issue that Apple engineers knew it would happen since threat actors have long compiled lists of entry and exit nodes to the Tor network so they could be blocked at various points in a country or company's network infrastructure.
The paper's surprising find was, however, another—namely that some of the ingress servers weren't managed by Apple, as the company had initially claimed, and that Akamai was hosting some of them as well. The issue raised by researchers was that Akamai, which also hosted egress servers together with Cloudflare and Fastly, would be able to see the full traffic path of some Apple users in the cases where both the ingress and egress were on its infrastructure, which they said they observed in their tests.
Sure, it sounds like the researchers are nitpicking, but the researchers said they hoped their findings would be used to improve the service, which should be pretty easy to do with some basic traffic shapping rules somewhere.
"Apple could ensure that ingress and egress addresses are not part of the same AS and entity to prevent such an issue in the future," the team said. Other than this tiny detail, the service continues to look as appetitizing for privacy lovers, and probably even more after the acid/panicky response from some telcos over the past few months.
The researchers plan to present their findings in October at the ACM Internet Measurement Conference 2022, to be held in Nice, France.
Breaches and hacks
Chile government ransomware attack: Chile's cybersecurity incident response team said an unnamed government agency was hit by a ransomware attack last week on August 25. Chile's CSIRT said the attack affected the agency's Microsoft and VMware ESXi servers and encrypted files with the ".crypt" extension. According to security researcher Germán Fernández, the targeted agency appears to be Sernac, the country's National Consumer Service. Chile now becomes the latest government across the world to deal with a ransomware attack against one of its official agencies, after similar attacks have recently hit Montenegro, the Dominican Republic, Costa Rica, Peru, Argentina, Brazil, and many others.
Neopets got hacked: Neopets, a website owned by Nickelodeon where users can manage a virtual pet, confirmed on Monday that it was hacked after some of its data popped up on a hacking forum last month. The company said that after an investigation, it discovered two periods where hackers could have had access to its systems, one between January 3 and February 5, 2021, and a second period between July 16 and 19, this year. The company said that data like emails, hashed and unhashed passwords, IP addresses, but also loads of account personal information was stolen in the incident and asked users to change their passwords.
Eni hack: Italian company Eni, considered one of the seven "supermajor" oil companies in the world, confirmed it suffered a "minor" security breach in a statement provided to Bloomberg. The incident is said to resemble ransomware, according to the publication's sources.
General tech and privacy
Mobile apps leak AWS infrastructure credentials: Broadcom's Symantec team said they analyzed 1,859 mobile Android and iOS apps and found that more than two-thirds (roughly ~1,000 apps) contained (and were leaking) AWS access tokens for their backend infrastructure. Symantec said the vast majority of these were iOS applications.
Mandatory security updates for 5 years: A proposed EU draft legislation would require that smartphone vendors provide security updates for all devices sold across the Union for at least five years. [Additional coverage in MacRumors]
Fog Reveal: The Associated Press has published an analysis of Fog Reveal, a little-known cellphone tracking tool by Virginia-based company Fog Data Science, which has been used by law enforcement over the past four years in law enforcement investigations to create "patterns of life" from past cellphone location records. The tool has been used in investigating an assortment of crimes, from murders to identifying participants in the January 6 insurrection.
Government, politics, and policy
Norwegian Parliament fined for APT28 hack: The Norwegian data protection agency, the Datatilsynet, has fined the Norwegian Parliament, the Storting, 2 million NOK (~$200,000) for a data breach that took place in late 2020, during which a threat actor gained access to the personal email inboxes of several government workers and officials. The Norwegian security service, the PST, later attributed the incident to Russian cyber-espionage crew APT28.
Supply chain guide: The National Security Agency (NSA), Cybersecurity and Infrastructure Security Agency (CISA), and the Office of the Director of National Intelligence (ODNI) published today a guidance document for developers on how to secure their software against supply chain attacks.
US debars three former NSA staffers: The State Department has banned three former National Security Agency employees from working on any matters related to International Traffic in Arms Regulations, which regulates the sale of military technologies overseas, due to their involvement in helping the United Arab Emirates carry out a widespread surveillance campaign to spy on dissidents, journalists, and politicians as well as US companies. The three previously settled with the DOJ last year in a criminal investigation for the same charges for a $1.68 million fine. [Additional coverage in Cyberscoop]
Tougher rules for UK telecoms: Starting with October, the UK government says it will have the toughest telecom regulations in the world, and its telecom regulatory agency, Ofcom, will be able to issue huge fines for companies that fail to protect their networks, equipment, and their customers' data.
Ofcom will oversee, monitor and enforce the new legal duties and have the power to carry out inspections of telecoms firms' premises and systems to ensure they're meeting their obligations. If companies fail to meet their duties, the regulator will be able to issue fines of up to 10 per cent of turnover or, in the case of a continuing contravention, £100,000 per day.
GCHQ seeking more female coders: The GCHQ, the UK's intelligence, security, and cyber agency, is funding a series of 14-week "nano-degrees" in data and software programming to help women make a career change and join the agency's ranks. The agency said it's making this effort in order to boost diversity and be better prepared to tackle threats ranging from foreign states to child online safety.
Sponsor section
RunZero (formerly Rumble Network Discovery) is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
Cybercrime and threat intel
Geode scans: SANS ISC says that days after the Apache Foundation issued a patch for an Apache Geode vulnerability, scans have been hitting the internet searching for vulnerable installations.
China-Taiwan tensions: A CyberInt report on the threat intelligence landscape between China and Taiwan claims that although the two countries are not engaged in a physical war, there is lots of cyber-related activity between the two states, with patriotic hacktivist groups carrying out hacks, leaks, and DDoS attacks against opposing targets.
FRP tool abuse: Korean security company AhnLab published a report on Thursday about a threat actor who likes to install open-source fast-reverse proxy (FRP) tools as a way to access internal networks via hacked externally-facing servers.
JuiceLedger: Checkmarx and SentinelOne published more details on JuiceLedger, the threat actor behind the recent phishing campaign that went after the PyPI accounts of Python developers. The two reports found that on top of the phishing campaign through which he tried to take over accounts and then publish malware-infected updates to legitimate libraries, the threat actor has also published their own typo-squatted packages. In all cases, the malware added to the packages was a C#-based infostealer named JuiceStealer, designed to steal browser and Discord data.
Today we received reports of a phishing campaign targeting PyPI users. This is the first known phishing attack against PyPI.
— Python Package Index (@pypi) 2:10 PM ∙ Aug 24, 2022
We’re publishing the details here to raise awareness of what is likely an ongoing threat.
Malware technical reports
ERMAC banking trojan: Intel471 researchers have a basic write-up on ERMAC, an Android banking trojan that abuses the Android Accessibility service to steal user credentials for various apps and online services.
Qbot/Qakbot: Something we missed last week was this pretty cool analysis of the Qbot/Qakbot trojan from Elastic's security team.
Raspberry Robin linked to Dridex: After Microsoft hinted that the Raspberry Robin worm might have been developed by the Dridex (EvilCorp) gang, IBM X-Force published a report showing code similarities between the two.
Asbit: Juniper researchers have analyzed a new remote access trojan named Asbit that first emerged from the Chinese underground last year. One of the trojan's key features is its use of DNS-over-HTTPS (DoH) to resolve the IP addresses of its control servers, a mechanism it uses to bypass network DNS filters.
Prynt Stealer: Zscaler researchers said they found a backdoor mechanism in Prynt Stealer, an infostealer trojan sold on underground markets. Per a report published this week, Prynt Stealer versions sold to cybercrime gangs will also send a copy of the stolen data to a second Telegram channel controlled by malware’s author, allowing them to leech on other gang's operations.
BianLian ransomware: Cybersecurity firm [redacted] (yes, that's their freaking name) has published a technical analysis on BianLian, a ransomware strain first spotted last year and used in targeted attacks against high-profile corporate targets. [redacted] believes BianLian operators are a new entity on the ransomware landscape and not a rebrand of an older affiliate group. Although BianLian operators appear to be extremely skilled at breaching networks, they don't appear to be as good at extorting their victims. [redacted] says the group would often have long delays before communicating with victims, accidentally sent one victim's data to another by accident, and running some pretty unreliable server infrastructure.
DarkAngels ransomware: Uptycs researchers said they discovered a Linux version of DarkAngels, a ransomware strain that was first spotted in May this year in attacks targeting Windows systems.
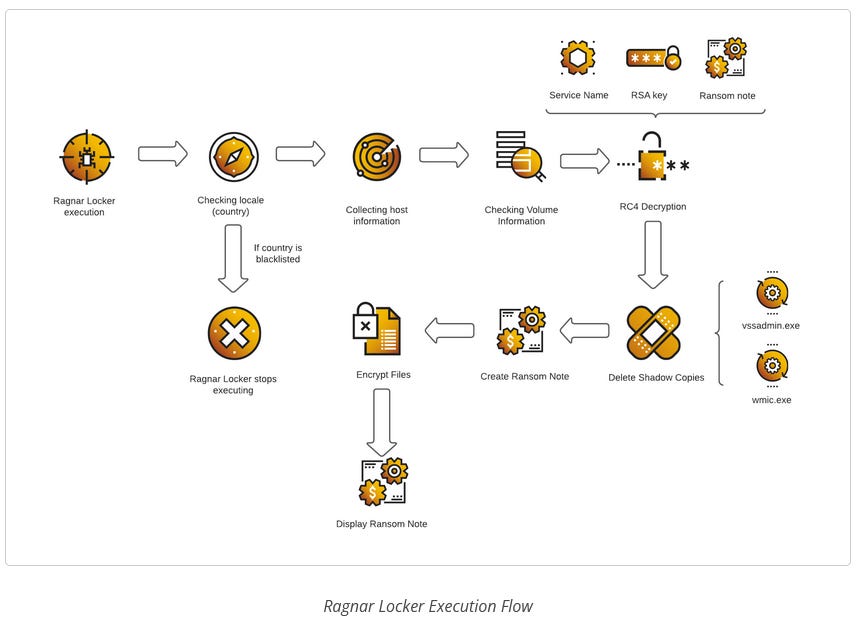
RagnarLocker ransomware: In a similar report, the Cybereason research team also took a similar deep dive into the RagnarLocker ransomware. This group recently hit TAP Air, Portugal's national state-owned airline.
APTs and cyber-espionage
APT-C-08 (Bitter): Qihoo 360's security team has published a report on a recent cyber-espionage campaign carried out by APT-C-08 (also known as Manling Flower or Bitter), a suspected Indian APT. Qihoo called the Bitter "one of the most active overseas APT groups that attack targets in China."
Vulnerabilities and bug bounty
Intel CET bypassed: Security researcher Matteo Malvica details a new technique that can be used to bypass Control Enforcement Technology (CET), a new hardware-based security feature added to modern Intel processors two years ago. That's quite the achievement.
CVE-2022-32250: NCC Group researchers published details on CVE-2022-32250, a vulnerability in the Linux kernel they initially planned to use at the Pwn2Own 2022 desktop hacking contest, but for which they eventually missed the conference deadline.
TikTok for Android vulnerability: Microsoft's offensive security team published details about a now-fixed vulnerability in the TikTok for Android application that could have been exploited to perform one-click account hijacking attacks.
Another Azure Synapse vulnerability: Orca Security researchers have published details about a new vulnerability impacting Azure's Synapse analytics service. The bug is a race condition leading to an LPE. Previously, Orca researcher disclosed the SynLapse vulnerability in the same Azure service earlier this summer. Microsoft's write-up on this is here.
Chrome security updates: Chrome 105 is out and, as usual, comes with plenty of security updates.
Infosec industry
New tool—macos-unifiedlogs: Mandiant has open-sourced a new tool named macos-unifiedlogs that can be used to parse and search macOS Unified Log files for forensic or suspicious artifacts.
BlackHat 2022 slides: You might find this useful, especially since Black Hat organizers are really slow at releasing materials from their conferences.
#Blackhat 2022 all the slides.
— Clandestine (@akaclandestine) 7:27 PM ∙ Aug 30, 2022




