Risky Biz News: A third of the world now runs social media influence operations
In other news: FBI's InfraGard hacked; GitHub to roll out mandatory 2FA; 50 DDoS service providers taken down before Christmas.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Risky Business News is taking a break for the (northern) winter holidays. We may run a weekly edition, depending on the news flow, but we'll return to our regular three-times-per-week format on January 9, 2023. Happy holidays!
In a report summarizing its actions against covert influence operations, Meta said that 2022 saw the largest number of Coordinated Inauthentic Behavior (CIB) networks since the company began tracking and cracking down on these operations back in 2017.
The company said it shut down this year more than 200 influence networks operating from 68 countries in 42 different languages.
The number represents 35% of all internationally recognized states today, meaning that roughly a third of countries across the globe have employed or harbored a social media influence network within their borders throughout 2022.
"Russia (34 networks), Iran (29 networks) and Mexico (13 networks) were the three most prolific geographic sources of CIB activity — whether by state actors, political groups or commercial firms," Meta said.

Meta's numbers are eye-opening for anyone today thinking social media influence operations don't work. They obviously do; otherwise, they wouldn't have been around after five years and certainly not exploded like they did this past year.
But Meta says that we all have a skewed view of what influence operations really are and what they're used for.
While back in 2017, when Meta began tracking CIB networks, these operations would target foreign audiences, this has quickly turned, and for the past few years, the vast majority of CIB networks target internal audiences—which explains why we see influence ops in places like Uganda, Finland, or Zimbabwe.
Furthermore, CIB operations have "devolved" from trying to influence US Presidential elections to the lowest level of the political process, with Meta finding PR firms sometimes running "influence" campaigns for two rivals going for the same elected position.
How CIB networks operate also appears to be region specific. Meta said that 90% of the influence ops it saw originate from Asia-Pacific, sub-Saharan Africa, and Latin America typically targeted local audiences. On the other hand, CIB networks in the EU and MENA seem to be mainly focused on international audiences, which makes sense primarily due to the complicated political structure in both regions.
"Uniquely, the Gulf region was where we saw covert influence operations from many different countries target each other, signaling these attempts at influence as an extension of geopolitics by other means. For example, we removed: an Iranian network criticizing Saudi Arabia and the US; a network from Saudi Arabia criticizing Iran, Qatar, and Turkey; an operation from Egypt, Turkey and Morocco supporting Qatar and Turkey and criticizing Saudi Arabia, the United Arab Emirates (UAE) and the Egyptian government; and a network from Egypt supporting the UAE and criticizing Qatar and Turkey."
Meta didn't end its report with a conclusion, but it didn't need to. Nevertheless, I'll end this newsletter edition with an anecdote, something I accidentally heard in a bar 2-3 years back while having lunch with a friend. Five women having coffee, and one of them turned out to be the wife of the local mayor. Helped by a pause in the restaurant music playlist, I was surprised to hear that the Spice Girls behind me were arranging a James Bond covert-level operation to flood the city's Facebook groups and newspaper comments sections with praises for the incumbent mayor ahead of an upcoming reelection campaign. It made me chuckle at the time and go, "Look at these IRA wannabes!"
But if stuff like this was happening years back in a town in the b***hole of Romania, and Meta says it's only seeing ~200 CIB operations, you have to ask yourself how many other CIB operations have gone undetected; and if social networks will ever be able to see anything this small.
Further, as Meta also points out in its report, many of these influence ops also work across platforms and mediums. Now, with Twitter's security team yeeted into the sun, it's going to be much so harder to have an insight into these operations with only Google and Meta looking for them. So, we can confidently say that social media influence ops are here to say.
Breaches and hacks
FBI InfraGard hacked: A hacker used stolen PII data for a fin-tech CEO and has gained access to the FBI's InfraGard portal. Using that access, the threat actor has compiled and is now selling a database that contains the contact information for more than 80,000 InfraGard members. [Read the full story on KrebsOnSecurity]
Social Blade breach: Social media analytics platform Social Blade has confirmed that hackers gained access to its systems and has begun notifying affected users. The company appears to have learned of the breach after a hacker put its data up for sale on an underground cybercrime forum. Per the hacker, customer data was collected via an exposed API.
Gemini leak: Cryptocurrency portal Gemini has confirmed that the emails of some of its customers was pilfered during a security incident at one of its service providers and that its users are now being targeted with phishing attacks. The stolen data is now being sold on different underground forums.
TPG Telecom leak: Australia's second-largest telco, TPG Telecom, said one of its hosted Exchange email servers was hacked, and a threat actor stole the personal details of more than 15,000 of its business customers. [See coverage in SecurityWeek or the original announcement/PDF]
General tech and privacy
GitHub to roll out mandatory 2FA: Microsoft GitHub code hosting service announced that all users who contribute code on the platform will be required to have one form of 2FA by the end of 2023. Throughout next year, users will be enrolled in batches, and once they receive a notification from Microsoft, they will have 45 days to enable 2FA, or they'll lose access to their GitHub account.
GitHub rolls out free secret scanning to everyone: GitHub also announced this week that its secrets/toke-scanning feature is being expanded from private repos to all users. This is a big big win!
Microsoft bans crypto-mining on Azure: Microsoft has updated its terms of service to ban cryptocurrency mining on its online infrastructure, such as its Azure cloud, without its specific approval.
Apple satellite emergency service now in the EU: Apple launched last month "Emergency SOS via Satellite," a new feature for its Health app that can allow phone owners to request emergency services via satellite whenever they are outside WiFi or cellular coverage. The service has now come to France, Germany, Ireland, and the UK after it was initially launched in the US and Canada. Instructions on how to set up the service are available here.
Z-Wave goes FOSS: The Z-Wave wireless protocol has gone open-source.
Free speech for me, but not for thee: Super-sensitive crybaby Twitter CEO Elon Musk has banned a Twitter account that tracked the movements of his private jet. The ban comes after Musk previously promised not to take action against the account. The account has since moved to Mastodon, and then Mastodon's Twitter account got suspended as well. Musk also suspended the accounts of NYT, WaPo, and CNN journalists covering his businesses. Things are getting very petty, very fast.
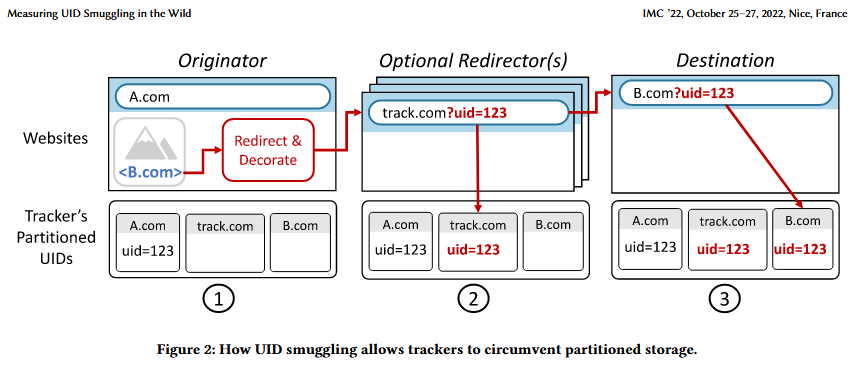
New web tracking technique: Academics from the University of California, San Diego, have developed a tool called CrumbCruncher which they used to measure the usage of UID smuggling in the wild. UID smuggling is a new type of web tracking that advertisers developed as an alternative after browser makers started blocking third-party cookies. The research team says that around 8% of the traffic they analyzed appears to use UID smuggling. Full paper here/PDF.
Government, politics, and policy
SBOM left out of NDAA: After an alliance of tech vendors has complained [PDF] that the SBOM standard is not yet mature enough, US lawmakers have removed language from the National Defense Authorization Act bill that would have required vendors to provide bills of materials for all software provided to government agencies. [Additional coverage in FedScoop]
Cyber postures: The Stockholm International Peace Research Institute (SIPRI) has a report out on the evolution of cyber postures for today's top powers, the US, EU, China, and Russia. It's a good report to read, especially because it covers a little bit of the historical events that shaped national cybersecurity politics in recent years.
5G network slicing guidance: CISA and the NSA have released new guidance this week for 5G network operators as part of a larger series they started earlier this week. This new one [PDF] touches on how mobile networks can best set up and defend 5G networks that have been split into smaller parts—an architecture known as 5G network slicing.
NIST retires SHA-1: US NIST has announced the formal retirement of the SHA-1 cryptographic algorithm and has asked IT professionals, companies, and software vendors to replace it with SHA-2 or SHA-3 and phase it out by the end of 2030.
Russia to ban remote work from abroad: Russian news outlets are reporting that the Russian government is working on a bill that would prohibit remote work for Russians who left the country. The bill appears to be aimed at Russian who fled the country in the aftermath of Russia's invasion of Ukraine but continued to work for their Russian employers.
Sponsor section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
Cybercrime and threat intel
Sextortion campaign hits Australia: OSINT analyst Laura Paxton warns about a massive and aggressive sextortion spam campaign that's currently hitting Australians hard.
MoneyMonger: Zimperium has a report on MoneyMonger, a threat actor that develops and offers money-lending apps but also steals personal information from user devices in order to blackmail victims into paying more than the loan terms.
17k C&Cs: In a report reviewing the 2022 adversary landscape, Recorded Future says it observed 17,233 command and control servers that were set up during 2022, up 30% from last year (13,629 in 2021). Most of these were Cobalt Strike team servers, botnet families including IcedID and QakBot, and popular RATs such as PlugX, it said.
Surveillance-for-hire industry: Meta's security team has published a report on the surveillance-for-hire industry [PDF]. The company said it took down this year several accounts on its social media sites that were being used by various hacker-for-hire companies. This includes:
- About 130 accounts on Facebook and Instagram linked to a known Israeli spyware developer Candiru, co-founded by a former employee of NSO Group.
- About 250 accounts on Facebook and Instagram linked to another known spyware vendor Quadream, an Israeli-based company founded by former NSO employees.
- About 230 accounts on Facebook and Instagram linked to CyberGlobes in Israel.
- More than 100 accounts on Facebook and Instagram linked to Avalanche in Russia, selling access to a platform that enables reconnaissance across the internet.
- About 3,700 Facebook and Instagram accounts linked to Social Links, a web firm originally based in Moscow, Russia, and now operating in New York in the United States.
- More than 40 accounts on Facebook and Instagram operated by an Indian firm called CyberRoot Risk Advisory Private.
Phishing campaign floods package repositories: Checkmarx and Illustria published a joint report on a ginormous phishing campaign that flooded the NuGet, NPM, and PyPi package repositories with more than 144,000 packages. Most of the packages used names related to hacking, cheats, and free resources and contained links in their description that redirected users to phishing sites.
SMS scam campaigns: Bitdefender has a report on some of today's most aggressive SMS scam campaigns taking place in various countries across the globe.
KEV update: CISA has updated its KEV database with six new vulnerabilities that are currently being actively exploited. These include recently disclosed zero-days in Citrix, Fortinet, Windows, and iOS, but also two vulnerabilities patched earlier this year in Veeam backup solutions.
50 DDoS websites taken down: Europol and law enforcement agencies across Europe and the US have shut down 50 DDoS-for-hire portals. The crackdown is part of Europol's yearly Operation PowerOFF, a yearly operation that shuts down DDoS service providers ahead of the winter holidays, a period when many kids use these services to attack gaming servers. The DOJ has also charged six individuals in the US. According to infosec reporter Brian Krebs, the accused allegedly ran DDoS portals such as supremesecurityteam[.]com, royalstresser[.]com, securityteam[.]io, astrostress[.]com, IPStresser[.]com, and TrueSecurityServices[.]io.
Malware technical reports
Royal ransomware: Cybereason researchers have a breakdown of the Royal ransomware operation, which they said appears to be comprised of "former members of other ransomware groups."
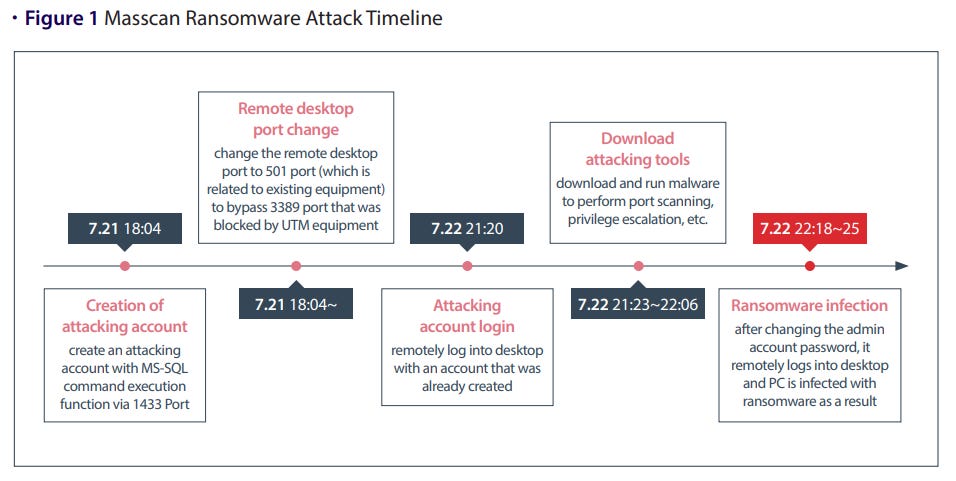
Masscan ransomware: The Financial Security Institute of South Korea has published a report on the Masscan ransomware (aka MaRS), which recently hit multiple South Korean companies.
MCCrash: Microsoft has a report on MCCrash, an IoT botnet operated by the DEV-1028 threat actor and used to launch DDoS attacks against private Minecraft servers.
RedGoBot: Chinese security firm QiAnXin has spotted a new IoT malware strain named RedGoBot that appears to target Vacron NVRs. An analysis of the code shows the malware is intended for DDoS attacks.
BrasDex: ThreatFabric researchers have a report on BrasDex, a new Android banking trojan that originates from Brazil. ThreatFabric says the group behind BrasDex also appears to be involved in attacks using Casbaneiro, a banking trojan that targets Windows devices.
Brute Ratel: OALABS researchers have published tips and IOCs that can be used to detect threat actors that employ the Brute Ratel pen-testing framework.
FreePBX campaign: Sucuri researchers have analyzed a backdoor planted as part of an exploitation campaign that targets FreePBX, a web-based open-source GUI for managing Asterisk VoIP servers.
Anti-debugging in the weirdest places: JFrog says it is seeing anti-debugging techniques leveraged to hide malicious behavior inside malicious Python libraries submitted to the PyPI package report. Their use suggests that malware authors are getting worried/annoyed with their malware being easily detected by the flurry of SecDevOps companies that have begun to routinely scan new PyPI submissions and alert the PyPI security team.
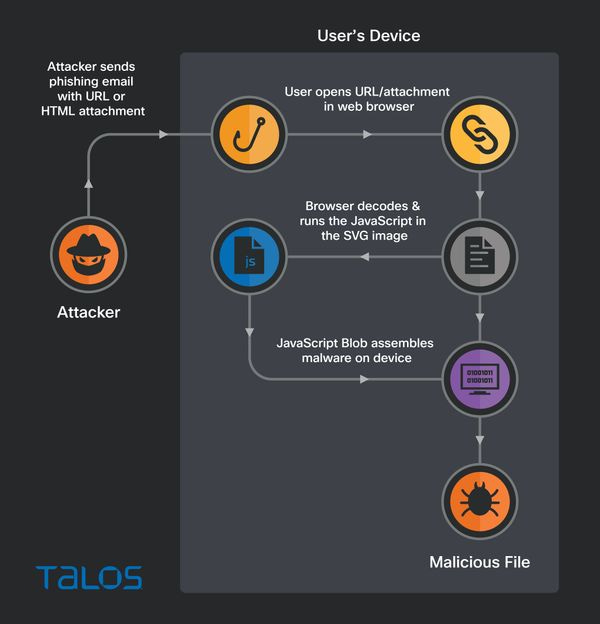
Qakbot: Cisco Talos is seeing the Qakbot botnet utilize SVG images and HTML smuggling in its recent malspam operations.
APTs and cyber-espionage
Twitter employees sentenced: Ahmad Abouamm, the former Twitter employee who was found guilty of spying for Saudi Arabia, was sentenced on Thursday to 42 months in prison.
"According to the evidence presented at trial, Abouammo, 45, formerly of Walnut Creek and currently residing in Seattle, began receiving bribes from an official of the Kingdom of Saudi Arabia (KSA) as early as December of 2014. Abouammo was employed at Twitter as a Media Partnerships Manager for the MENA region. Twitter policies required Abouammo to protect Twitter user information, as well as disclose conflicts of interest and report gifts from those with business with Twitter. Nevertheless, the evidence at trial demonstrated that Abouammo accepted bribes from officials of the KSA in exchange for accessing Twitter user accounts and conveying information on dissidents and critics of the KSA to their government officials and the Saudi Royal family, then lied to the FBI investigators and falsified a document when questioned about the transactions in October 2018. The official of the KSA was head of the 'private office' of a royal family member who, during the relevant time, was a Minister of State and then became the Minister of Defense and Deputy Crown Prince."
Operation LiberalFace: ESET has a report on a campaign launched by MirrorFace, a suspected Chinese APT, that targeted Japanese political entities a few weeks before the House of Councillors elections.
SideWinder APT: QiAnXin reported on recent SideWinder APT spear-phishing operations
UNC4166: Mandiant says that a threat actor it tracks as UNC4166 used trojanized versions of the Windows 10 OS installer distributed via Ukrainian torrent websites to infect locals with malware. Researchers say the group then handpicked government-related targets from their pool of compromised systems and deployed additional malware that could aid with reconnaissance and data theft.
"At this time, Mandiant does not have enough information to attribute UNC4166 to a sponsor or previously tracked group. However, UNC4166's targets overlap with organizations targeted by GRU-related clusters with wipers at the outset of the war."
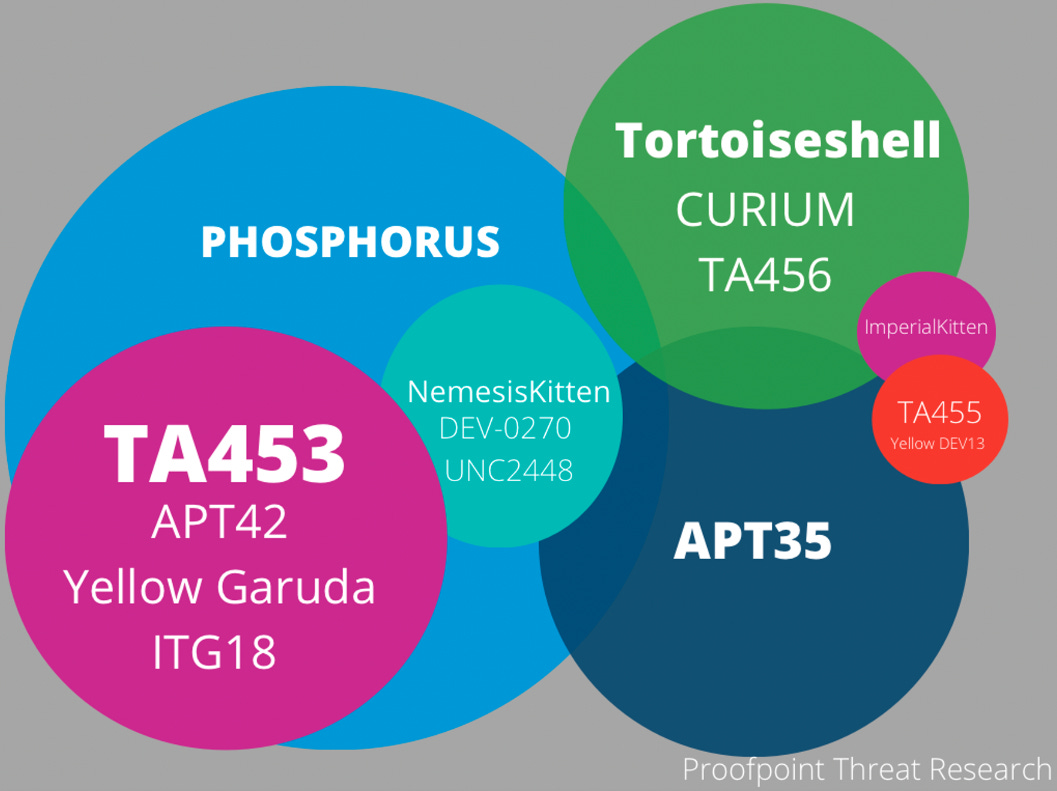
TA453: One of the most interesting APT reports this week came from Proofpoint, which looked at spear-phishing operations from Iranian APT TA453 that deviated from their standard targeting. Lots of interesting stuff in there, like the targeting of travel agencies inside Iran, space programs across the world, women's rights organizations, and research institutes working on organ replacement. However, the one that caught our eye is highlighted below, and Proofpoint researchers appear to believe this might have been intelligence collection for a potential IRGC on-the-ground espionage operation.
"Proofpoint observed a Gmail address targeting a Florida-based realtor with a benign conversation and TA453 affiliated web beacon. Open-source research of the realtor identified they were involved in the sale of multiple homes located near the headquarters of US Central Command (CENTCOM) during the phishing campaign. CENTCOM is the US Combatant Command responsible for military operations in the Middle East."
Vulnerabilities and bug bounty
Meta bug bounty payouts: Meta said it paid more than $2 million in bug bounty payouts to security researchers this year, bringing its payouts since the program's inception in 2011 to more than $16 million.
Cookie expiration issues: Atlassian products like Jira, Confluence, Trello, and BitBucket apparently have an issue with their cookie management, which they fail to invalidate once a user changes their password. This may lead to situations where attackers can retain access to hacked accounts using stolen cookies, even if an organization has reset passwords. See CloudSEK's report.
Cache poisoning attack: Tarunkant Gupta, a security engineer for Disney's Hotstar, has found a novel cache poisoning attack that takes place between Akamai and AWS S3 infrastructure.
CVE-2022-37958: Valentina Palmiotti, a security researcher at IBM's X-Force Red, has released more details about CVE-2022-37958, a vulnerability in the Windows SPNEGO protocol that Microsoft patched back in September. A video demonstration of the bug is here. The tl;dr here is below. Long story short, it's really bad!
"The vulnerability is in the SPNEGO Extended Negotiation (NEGOEX) Security Mechanism, which allows a client and server to negotiate the choice of security mechanism to use. This vulnerability is a pre-authentication remote code execution vulnerability impacting a wide range of protocols. It has the potential to be wormable."
"Unlike the vulnerability (CVE-2017-0144) exploited by EternalBlue and used in the WannaCry ransomware attacks, which only affected the SMB protocol, this vulnerability has a broader scope and could potentially affect a wider range of Windows systems due to a larger attack surface of services exposed to the public internet (HTTP, RDP, SMB) or on internal networks. This vulnerability does not require user interaction or authentication by a victim on a target system."
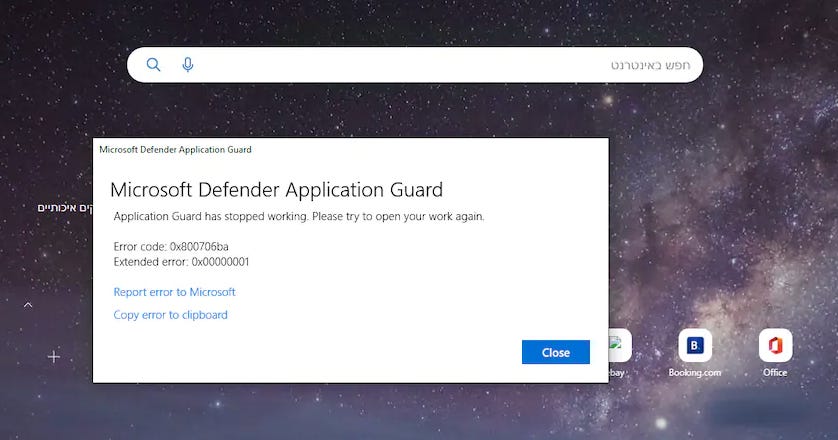
CVE-2022-37998 and CVE-2022-37973: On the same note, Akamai's Ben Barnea also published details this week about two older vulnerabilities that Microsoft patched in October—namely, CVE-2022-37998 and CVE-2022-37973, bugs affecting the Windows Local Session Manager RPC interface. PoCs for both are available on GitHub.
"The vulnerabilities lead to denial-of-service attacks that prevent container and session services (such as Microsoft Defender Application Guard, Sandbox, Docker, and Windows Terminal Server) from working."
Infosec industry
Free service launch: Wordfence launched this week a vulnerability database for WordPress security bugs. The service is free for community use and under a commercial license for hosting companies, security organizations, threat analysts, security researchers, and other commercial projects.
2023 predictions: While I'm not a fan of the yearly infosec predictions shtick, this one from Chainguard on the possible evolution of supply chain security is a little bit more interesting than the rest of the "malware is gonna go up" stuff we see from vendors. Goes well when mixed with the 2022 year-in-review analysis from its CEO, Dan Lorenc.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




