Risky Biz News: A ransomware attack is putting lives at risk across South Africa
In other news: OpenAI hid a security breach; ransomware attack cripples Florida's Department of Health; major Mastodon security update is out.

This newsletter is brought to you by Devicie. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

For the past two weeks, a ransomware attack has been wreaking havoc among healthcare services and putting lives at risk across South Africa.
The incident took place on June 22 and hit the National Health Laboratory Service (NHLS), a South African government organization that does lab work for the country's hospitals.
The attack and subsequent IT outage crippled 265 NHLS laboratories and their ability to process blood work. According to a report from the Cape Independent, the labs are behind on over 6.3 million blood tests. The lack of proper blood work is delaying accurate diagnostics and has postponed operations, putting countless patient lives at risk.
A hematologist from Johannesburg described the situation as "dire," with patients in emergency wards and intensive care units around the country being in "fatal danger."
NHLS CEO Professor Koleka Mlisana said people were most likely going to die because of the attack and asked provincial heads of health departments to collect mortality data.
As The Record pointed out, the attack also took place days after an outbreak of Mpox (formerly monkeypox) broke out in the country, with PCR tests playing a central role in diagnosing the disease.
South Africa's government news agency reports that while laboratories resumed doing blood work last week, there are still problems with delivering test results to hospitals and their patients. For the utmost urgent tests, hospitals are still mainly using private laboratories. The NHLS labs either call doctors or print results on paper and send them via post or courier. This is a far cry and a far less efficient process than sharing the results via the NHLS dashboard.
The government appears to have opted not to pay the attackers—who, in turn, appear to have grown bitter about their financial loss.
A self-described "middleman" has spent the last week calling NHLS staff and South African journalists, trying to scare officials and the public and put pressure on the agency to pay the ransom before anyone dies.
After Health-E News leaked the attackers' identity on Thursday last week, the Black Suit ransomware group formally took credit for the attack a day later through a post on their dark web leak site—once again trying to blame the government's stubbornness against paying the ransom for all the potential fallout.
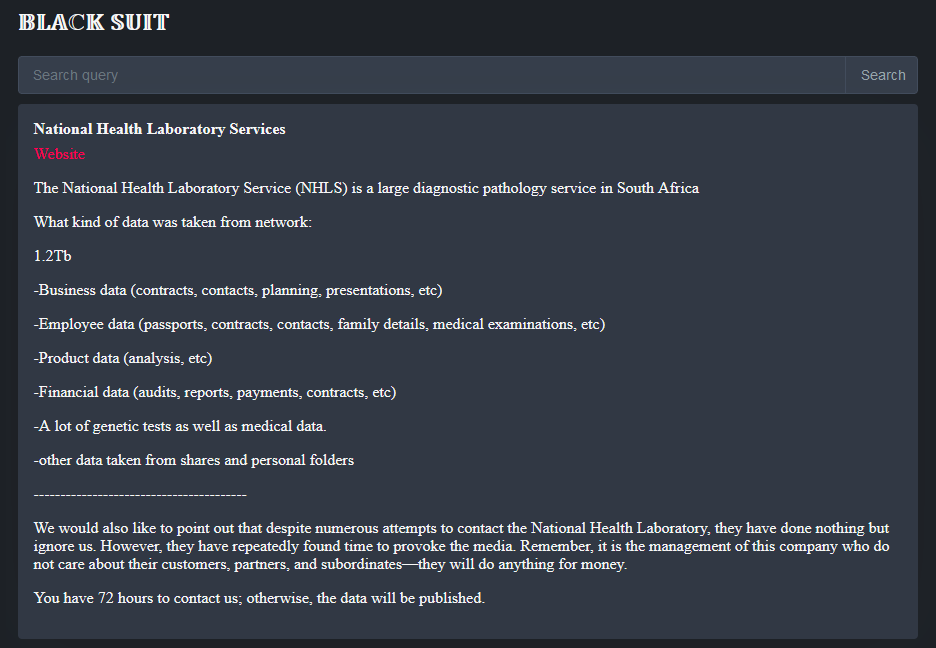
The tactics used here by the gang are the standard for ransomware groups targeting hospitals. Using human lives and the threat of possible deaths to barter for quick ransom payments has been the norm in a field where consequences for attackers have been missing in action for almost a decade. But that's a topic for another discussion.
Although an estimate, research published last year has found that mortality rates increased by around 20% at US hospitals during a ransomware attack.
Breaches, hacks, and security incidents
OpenAI breach: A hacker has breached OpenAI in early 2023 in a security breach the company never disclosed. According to a report from the New York Times, the hacker accessed an internal employee discussion forum. OpenAI decided against disclosing the breach because the hacker didn't access any production systems, customer, or partner data.
Airtel denies breach: Airtel, India's second-largest telecom operator, denied suffering a security breach after a threat actor claimed to be selling the data of 375 million of its users last week. [Additional coverage in TechCrunch]
Cloudflare BGP hijack: Cloudflare says that its free DNS resolver service 1.1.1.1 was the target of a BGP hijack attack that took it out of service for some users for several hours. The incident impacted users from over 300 networks in 70 countries.
Alabama DoE ransomware attack: The Alabama State Department of Education says it fell victim to a ransomware attack last month, on June 17. Officials say they stopped the attack before the intruders could encrypt its internal servers. The Department is now notifying [archived] students and teachers who had data accessed in the intrusion.
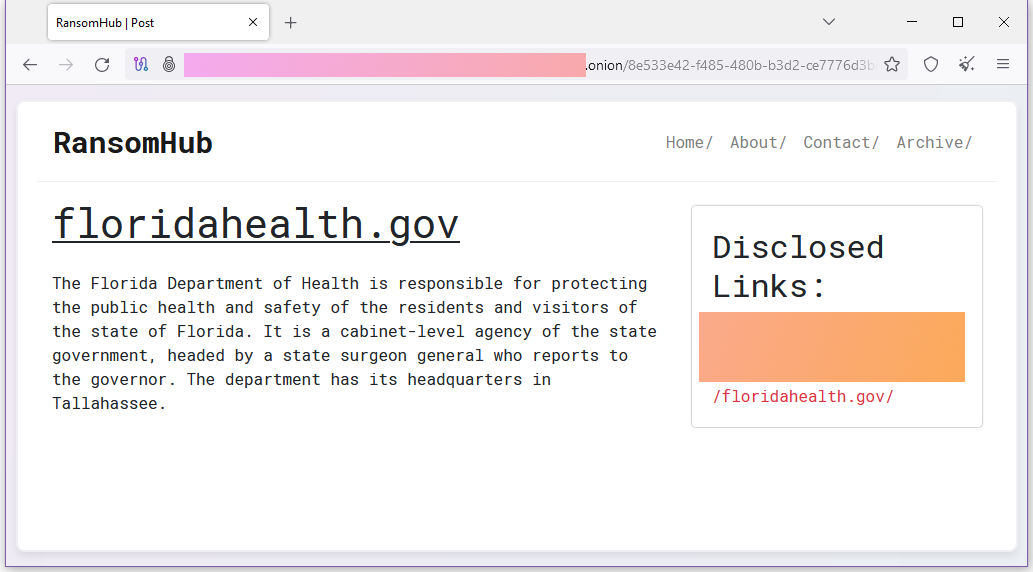
Florida DoH ransomware attack: The Florida Department of Health has confirmed that hackers breached its systems in an incident last week. The attack hit the Department's statistics system, which is used to issue birth and death certificates. Following the attack, the Department is now physically driving new birth and death certificates to state hospitals for processing. A group named RansomHub claimed credit for the attack and leaked some data after the Department refused to pay a ransom. [Additional coverage in the Tampa Bay Times and DataBreaches.net]
General tech and privacy
Fire TV ads: Amazon has started injecting ads on Fire TV devices. Fullscreen ads will now run before the device's screensaver kicks in. [Additional coverage in Cord Cutters News]
Theia IDE: The Eclipse Foundation has open-sourced a new IDE named Theia.
New OAuth app abuse reporting: Microsoft has updated procedures to allow customers to more easily report malicious OAuth apps for its Entra ID service. The company has changed procedures after a rise in malicious OAuth detected on its platform. Customers will be able to quickly report fraudulent publishers impersonating known brands, malicious apps impersonating legitimate apps, and legitimate apps that abuse or mishandle user data. [h/t ScreamingGoat]
Government, politics, and policy
Pennsylvania data breach law: The US state of Pennsylvania has updated its data breach law and will now require organizations to provide a full year of free credit reporting and credit monitoring to affected consumers. The law will apply to data breaches where threat actors have stolen a person's Social Security number, bank account number, driver's license, or state ID have been stolen. The new law passed with unanimous support in the Pennsylvania General Assembly at the end of June. [Additional coverage in Longview News-Journal / h/t DataBreaches.net]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Devicie Technical Product Manager Tom Plant on the upcoming Windows 10 end-of-support and the looming Great Windows 11 Migration.

Cybercrime and threat intel
Sri Lankans cybercrime crew deported: UAE authorities have deported 11 Sri Lankan nationals suspected to have been involved in cybercrime operations. The 11 were detained at the end of June as part of a crackdown against foreign criminal gangs operating in Dubai. Hundreds of suspects from Africa and Southeast Asia were arrested in the raids. Another 26 Sri Lankans are also awaiting deportation. Sri Lankan officials say they will decide how to move forward once they receive more information from UAE police.
REvil case in Russia: The case against eight suspected members of the REvil ransomware gang is finally underway in a St. Petersburg military court. The eight were detained in Russia in January 2022 following a complaint filed by US authorities. The FBI claimed the eight launched the attack against Colonial Pipeline in early 2021. The investigation broke down a month later after Russia invaded Ukraine and US authorities stopped communicating with Russian prosecutors. Since then, the case has been sent between a federal and military court several times before a trial finally started last week. According to Izvestia, Russian prosecutors hinted they don't have a strong case due to a lack of evidence.
Jenkins Script Console abuse: Trend Micro's Shubham Singh and Sunil Bharti have published a report describing how crypto-mining gangs have been abusing the Jenkins Script Console to deploy malicious scripts inside compromised Jenkins instances.
Religious app lures: Broadcom's Symantec says it has seen a threat actor using a fake Quran-related app to target Nigerian users with Android malware.
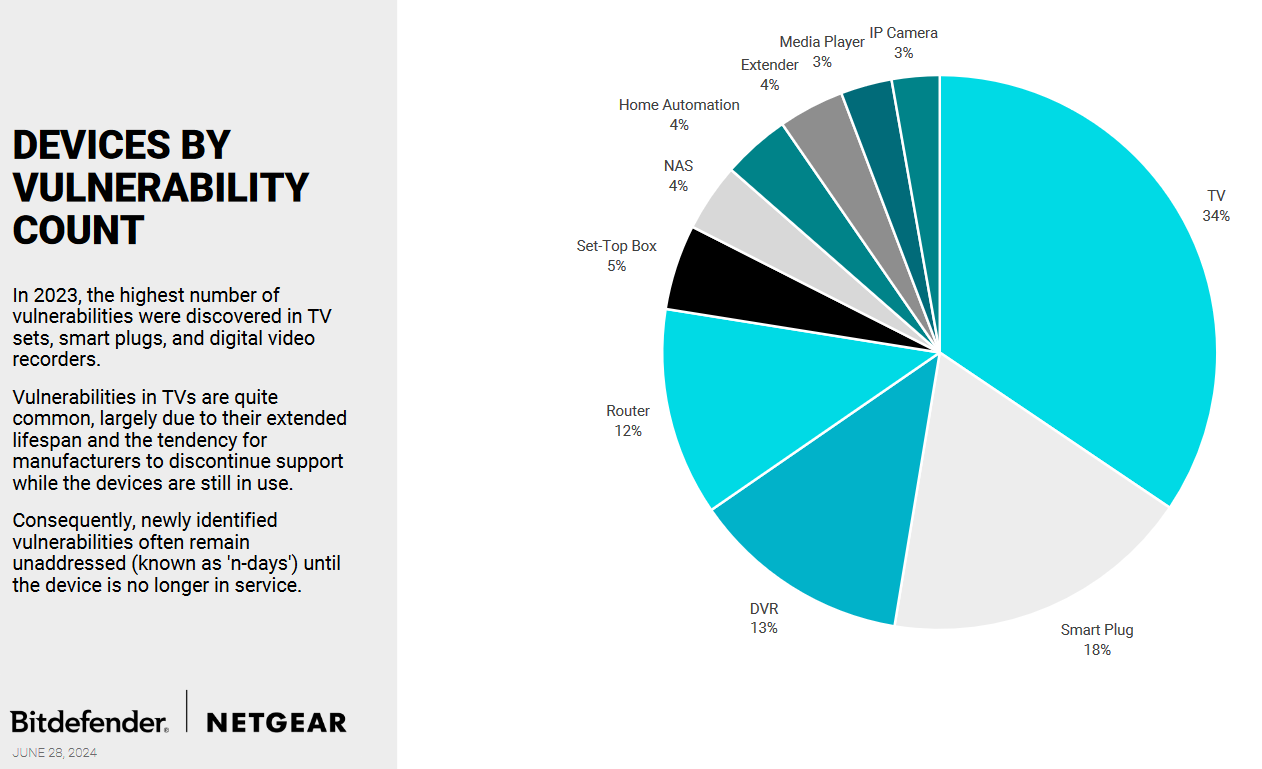
Threat/trend reports: Bitdefender+Netgear and QuoIntelligence have recently published reports covering infosec industry threats and trends.
New npm malware: Three-hundred-thirty-six (yes, 336) malicious npm packages were discovered last week. Check out GitHub's security advisory portal for additional details.
npm account takeover: A threat actor claims to be selling details about a vulnerability that can be used to take over accounts on the npm portal. DevSecOps company Socket could not confirm the threat actor's claims.
HackerOne MFA bypass: A threat actor claims [archived] to be selling details about a vulnerability in the HackerOne bug bounty platform that can bypass MFA checks. The bug would allow a threat actor with valid credentials to access HackerOne accounts and retrieve information about reported bugs. The bypass has not been verified by any reputable party at the time of writing.
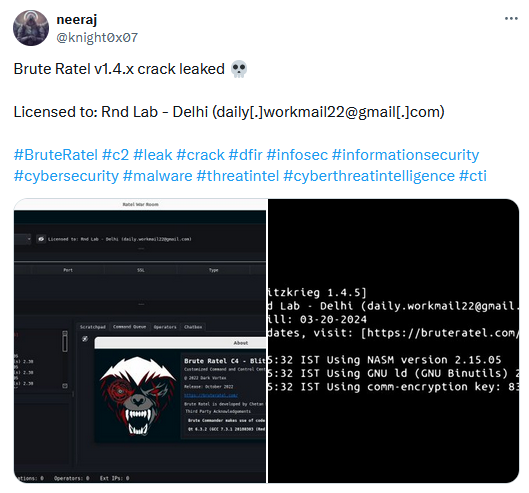
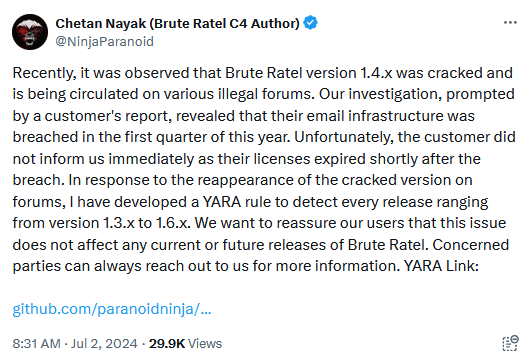
Brute Ratel leak: A threat actor has leaked [archived] a cracked version of the Brute Ratel offensive red team tool. The tool is often abused by cybercrime and state-sponsored groups for their operations. The leak covers Brute Ratel version 1.4, initially released in October 2022. The current Brute Ratel version is 2.0. The tool's creator has released [archived] YARA rules to help defenders detect the leaked version if used inside their networks.
Malware technical reports
Wordfence Evasion Malware: Wordfence says it found a new version of a WP backdoor specifically designed to evade its security product—hence its name of "Wordfence Evasion Malware."
Black Suit ransomware: Arete IR has published a profile on Black Suit, a ransomware group that has been active since May of last year.
SmokeLoader: Zscaler has published part two of its write-up on the SmokeLoader malware. Part one is here.
CSHARP-STREAMER: HiSolutions has published a technical report of CSHARP-STREAMER, a remote access trojan that was used in the past by ransomware gangs such as REvil and Metaencryptor. The company reports seeing usage of the RAT massively increase in Q3 2023 after the Metaencryptor gang intensified its attacks. The gang looks to have later rebranded as LostTrust.
Sponsor Section
Brought to you by Devicie. Be the first to hear about Devicie for MSP, the Intune hyper automation and management platform for modern device management at scale. Visit devicie.com/MSP

APTs, cyber-espionage, and info-ops
Turla: G Data researchers look at the various evasion techniques used by the Turla Russian APT group.
APT-C-26 (Lazarus): Qihoo 360's security team has published a report on the various APT-C-26 (Lazarus) campaigns that tried to plant malware on the PyPI portal.
RU PSYOPS in FR: Ukrainian news outlet InforNapalm has published a profile of Razroev Alexander Denisovich, an officer in Russia's Department of Information and Mass Communications (DIMC) responsible for running PSYOPS targeting French audiences.
"The date of the sponsored postings of the interview coincides with the Russian psychological operation on social media in France – the posting of coffins with the French tricolor in Paris. This was a kind of Russian response to Macron’s statements about possible sending of French military instructors to Ukraine. There also are other sponsored publications, strongly critical of French President Macron and of military aid to Ukraine, entirely in the spirit of Russian disinformation and propaganda narratives in Europe. Some postings on the eve of the European Parliament elections called for voting for the political force of Marine Le Pen, a longtime admirer of Putin."
Vulnerabilities, security research, and bug bounty
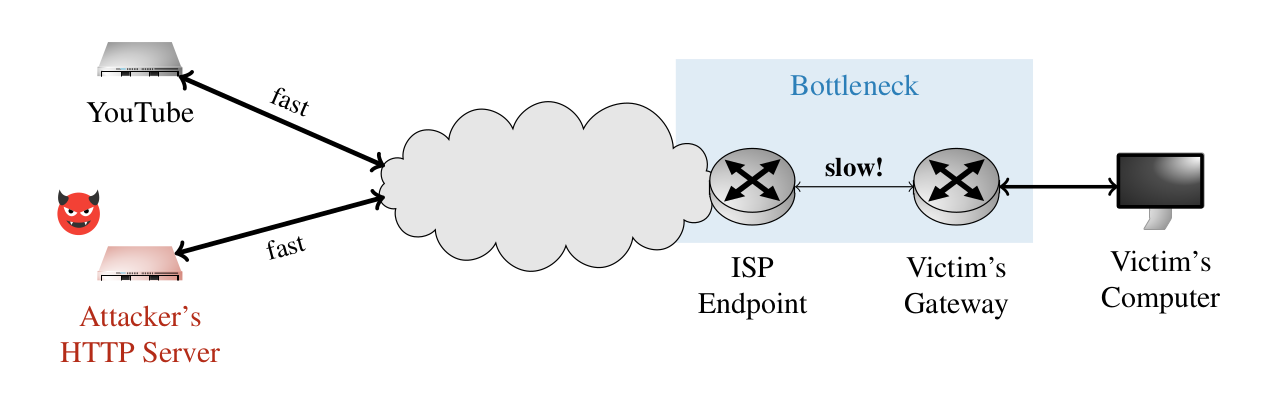
SnailLoad attack: A team of academics has published details about a new side-channel attack named SnailLoad that can be used to infer a remote user's web activity. The attack requires a victim to download data from a malicious server while performing other actions online. This data is compared to network latency measurements to determine what else the target was accessing during the download. The attack doesn't use an AitM, physical proximity, or JavaScript code, but merely relies on connection latency caused by network traffic bottlenecks.
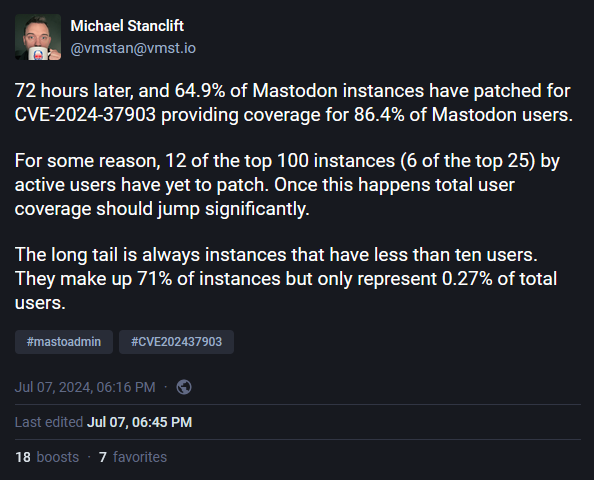
Mastodon security update: The Mastodon project has released a major security update to patch a vulnerability impacting Mastodon social media servers. Tracked as CVE-2024-37903, the vulnerability allows threat actors to modify a post's audience and make private content available to the public. The Mastodon project says it will provide additional details on Monday, July 15. Four days after the patch, 65% of all Mastodon servers have already applied the patch, covering roughly 85% of all Mastodon users.
Infosec industry
bpfconf 2024: Slides from the bpfconf 2024 conference, which took place in May, are available on the conference's website.
New tool—DonPAPI: French security firm Login Securite has released DonPAPI, a tool to dump DPAPI credentials remotely.
New tool—BADUnboxing: Security researcher LaurieWired has released BadUnboxing, an automated Android unpacker.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about why governments have failed to protect the private sector from state-backed cyber espionage.
In this podcast, Tom Uren and Patrick Gray talk about how South Korean internet regulations inadvertently encouraged a large ISP to hack their own customers to cut down on torrent traffic.
Abhishek Agrawal is the CEO and co-founder of Material Security, an email security company that locks down cloud email archives. Attackers have been raiding mailspools since hacking has existed, and with those mailspools now in the cloud with services like o365 and Google Workspace, guess where the attackers are going?




