Risky Biz News: $126 million go missing from Multichain in apparent hack
In other news: Revolut hacked for $20 million; Mastodon fixes TootRoot vulnerability; and hacker mass-defaces Hikvision cameras.
This newsletter is brought to you by Kroll. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Spotify:
Roughly $126 million worth of crypto-assets have been mysteriously transferred from the accounts of cryptocurrency platform Multichain in an apparent hack, according to blockchain security firms PeckShield, SlowMist, Lookonchain, and CertiK.
The incident took place on Friday, June 7.
Multichain—which is a platform that interconnects different blockchain platforms and allows users to exchange tokens—has shut down to investigate the incident.
Neither Multichain nor any blockchain experts know exactly what happened. CertiK believes some of the platform's private keys were compromised—although this theory has not been confirmed by anyone else.
Around $65 million of funds moved from Multichain wallets have already been frozen through the quick intervention of platforms like Circle and Tether. Nobody's labeling the incident as a hack, but they are taking steps to prevent funds from being laundered if an exploit is confirmed.
This is the second time this year that Multichain has suspended operations after it also halted trading at the end of May. At the time, the company said it couldn't perform server maintenance because its CEO had gone missing, and they didn't have access to the entire platform. The rumor was that its CEO was detained by Chinese authorities. Multichain never said if its CEO has rejoined the company.
If the recent incident is confirmed, this would also make the company's third hack in the past two years. It lost $3 million in January 2022 and another $8 million in July 2021 (known as AnySwap at the time).
Blockchain experts aren't ruling out a rug-pull either. A rug-pull is when a crypto-platform's developers run away with the money themselves.
Breaches, hacks, and security incidents
Revolut hack: An unknown hacker has exploited a vulnerability in the Revolut payment processing service and has stolen more than $23 million from the company's accounts. The attacks exploited a bug in a Revolut system that analyzed transactions between European and US users. Between late 2021 and early 2022, hackers exploited the bug to carry out non-compliant transactions and receive refunds for money they never spent. Revolut recovered only $3 million of the stolen funds, leaving it with a $20 million hole in its books. [Additional coverage in the Financial Times/non-paywall]
Razer data for sale: Data that hackers claim was stolen from hardware company Razer was posted on an underground data leak forum last week. The hackers are asking for $100,000 paid in Monero for the data. Razer has not confirmed the hack. [Additional coverage in DataBreaches.net]
Bangladesh leak: A Bangladeshi government website is leaking the personal details of millions of citizens, including data such as full names, phone numbers, email addresses, and national ID numbers. Bitcrack security researcher Viktor Markopoulos says he accidentally found the site on Google while searching for details about an SQL error. Markopoulos didn't name the government organization because the website has yet to be secured. [Additional coverage in TechCrunch]
Ashley Madison hack: Since Hulu and Disney+ are running a TV series on the Ashley Madison hack, Brian Krebs is also publishing some of the findings of his own investigation into the hack. In the first part of the series, Krebs looks at the actions and history of William Brewster Harrison, a former Ashley Madison employee who harassed his former bosses. Harrison committed suicide in 2014, a year before the Ashley Madison hack was revealed. It's still unclear if he was involved in the incident in any way, although emails show he still had access to the company's network through an admin account for years.
MOVEit hacks: The Clop cybercrime group has yet to be observed to deploy ransomware in any of the incidents linked to its recent exploitation of MOVEit file-sharing servers. Based on current evidence gathered by security firm HuntressLabs, the attacks appear to have been limited to data theft and data extortion. Huntress also says it has not observed the Clop gang expand its access to full network compromises, with the gang limiting itself to the hacked MOVEit appliance—an important clue for companies still engaged in IR related to last month's MOVEit hacks.
Hikvision camera defacements: A hacker named Faxociety is breaking into Hikvision DVRs and NVRs and defacing video streams with a text message that tells owners to secure their cameras. The incidents have been taking place for at least two months and are believed to have impacted thousands of cameras. Hikvision has confirmed the hacks and has recommended that customers change their DVR/NVR passwords and disable the UPnP feature. [Reports on Reddit, LinkedIn, IPVM, CCTV Global, Vietnam Express]

General tech and privacy
Avast class-action lawsuit: The Consumers United in Court (CUIC) Foundation has filed a class-action lawsuit in the Netherlands against security firm Avast. CUIC alleges that Avast collected data on its users and sold it to online advertisers without its users' knowledge and consent. Users who used Avast antivirus products or browser extensions between May 2015 and January 2020 had their data collected and sold. The list of products includes Avast Online Security, AVG Online Security, the Avast Secure Browser, the AVG Secure Browser, and the AVG Online Security extension. The collected user data was sold through a US-based subsidiary named Jumpshot. Avast shut down Jumpshot in January 2020 after its data trading practices were exposed.
China's openKylin reaches v1: China's homegrown openKylin operating system has finally reached v1.0 after years of development. The OS is based on the Linux 6.1 kernel and is available for x86, ARM, and RISC-V architectures. More than 200 companies and 3,000 developers are said to have contributed to the new OS, meant to replace the country's reliance on Windows. [Additional coverage in It's FOSS News]
Government, politics, and policy
Greece launches national SOC: Greece's National Intelligence Service, the EYP, will launch a new cybersecurity unit named the Security Operations Center. As its acronym, the new SOC unit will operate as a de-facto national SOC and will be responsible for monitoring, detecting, and responding to cyber threats and security breaches impacting Greek organizations. [Additional coverage in Capital and iEfimerida]
ACD yearly report: The UK NCSC has published its sixth yearly Active Cyber Defence (ACD) report. The report covers the agency's efforts to detect, block, and take down malicious URLs. More than 2.4 million URLs were taken down last year, with most being related to online extortion campaigns.

Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Scott Hanson, Head of Global Security Operations at Kroll, on how the company has adopted Detection-as-Code for its approach to writing, managing, and rolling out detection rules for its customers:
Cybercrime and threat intel
Football Leaks hacker charged: Portuguese officials have charged the suspect behind the Football Leaks hacking scandal that exposed some of the deepest secrets of the European soccer world. Rui Pinto was charged with 377 privacy and hacking-related offenses. The charges are related to Pinto hacking the email accounts of soccer stars and soccer clubs. The hacked information was shared between 2015 and 2018 on a website named Football Leaks and with sports journalists across Europe. Pinto's leaks exposed tax evasion and financial trickeries used by Europe's top clubs and the rape allegations made against Cristiano Ronaldo. Pinto was arrested in 2019 in Hungary and was extradited back to Portugal, where he was initially charged with 90 counts of hacking and extortion. He was found guilty in that case and stands to be sentenced on July 13. [Additional coverage in Marca]
Water treatment facility hacker: US authorities have charged a former contractor with hacking the water treatment facility for the town of Discovery Bay, California. Officials say Rambler Gallo accessed the facility's internal network in January 2021, a month after he resigned from his contracting job. He allegedly uninstalled the main monitoring system for the water treatment plant and shut down its servers. Officials say the disabled systems were responsible for monitoring water pressure, filtration, and chemical levels, and the hack caused a threat to public health and safety.
Sachkov case: Former Group-IB CEO Ilya Sachkov was arraigned in court for his treason case last Friday. Sachkov was arrested in September 2021. He was accused of providing details on Russian hackers to foreign intelligence services. Sachkov pleaded not guilty. In a Telegram video posted online in June, Sachkov says the treason charges levied against him are the revenge of two FSB officers. Sachkov's case is scheduled to take place behind closed doors. [Additional coverage in Business FM and BBC Russia]
New npm malware: Twenty-five new malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
Strela campaign: Deutsche Telekom's CERT is warning about a month-long campaign using the Strela stealer and targeting users in Germany, Italy, and Spain.
Malicious ads lead to USPS phishing: Malwarebytes says it found malicious Google search ads that lead users to USPS phishing sites.
Fake Linux PoC spreads malware: Security researchers have spotted a GitHub repository [archived] claiming to host a proof-of-concept exploit for the CVE-2023-35829 Linux vulnerability that actually installed a Bash backdoor on the user's Linux system.
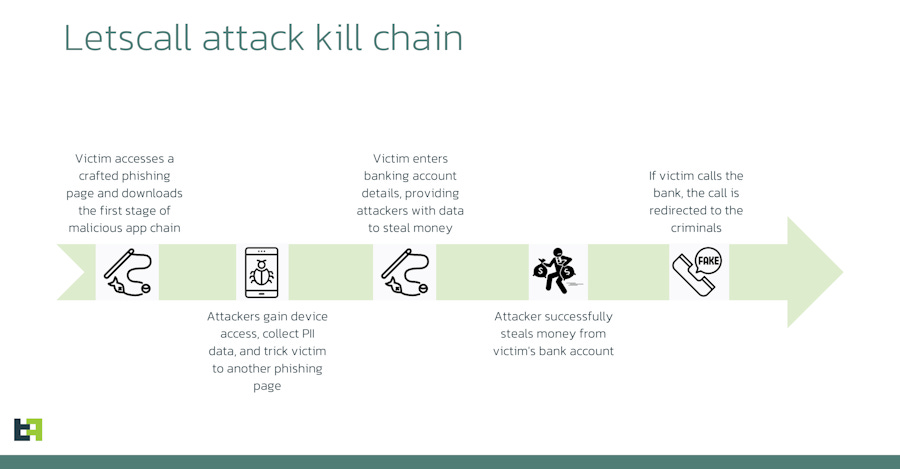
Letscall vishing infrastructure: ThreatFabric looks at Letscall, a toolset used to carry out vishing attacks across South Korea. The interesting part of the toolkit is that if victims detect thefts from their accounts and call the bank, the call is intercepted and rerouted to the thieves instead. Such attacks were first spotted last year by Kaspersky in a campaign known as Fakecalls.
Malware technical reports
Big Head ransomware: Trend Micro researchers have a deep dive into the new Big Head ransomware, first spotted being advertised on YouTube and Telegram in May. It remains unclear if the ransomware was ever used in the wild. Another report on Big Head is also available via Fortinet.
Rancoz ransomware: The same Fortinet team also has a report on the new Rancoz ransomware, first seen in the wild last November.
BlackCat ransomware: Chinese security firm Antiy has published an analysis of the BlackCat (ALPHV) ransomware.
Status Recorded: OALABS has published IOCs for Status Recorder, a new infostealer on the malware market.
Blank Grabber: CyFirma has published an analysis of Blank Grabber, an infostealer builder first advertised on hacking forums in 2022.
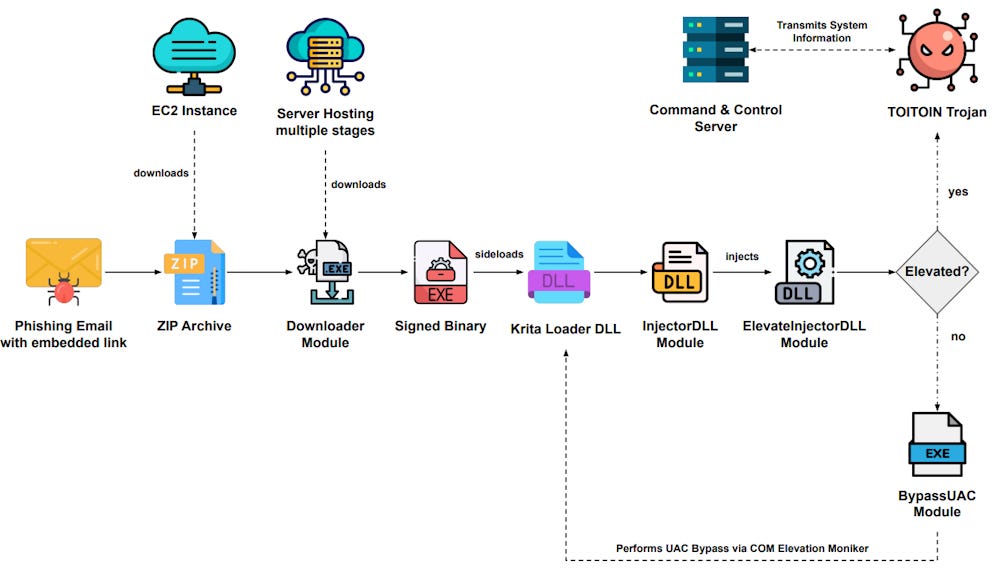
TOITOIN: Zscaler's research team has published details on a malware campaign targeting businesses in Latin America with the TOITOIN trojan.
Sponsor section
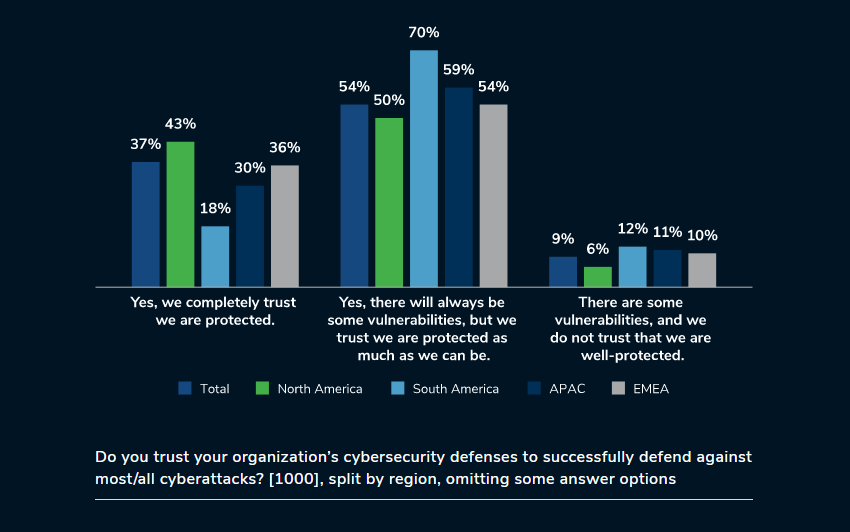
Kroll conducted a survey of 1,000 senior information security decision-makers based in North and South America, APAC, and EMEA. The goal was to understand the current state of cyber defense, the levels of organizational trust, and how true cyber maturity links to trust in facilitating organizations to stay ahead of the curve in a constantly evolving threat landscape.
APTs and cyber-espionage
South Asian APTs: Chinese security firm Sangfor has published a summary of recent South Asian APT groups that are actively targeting Chinese organizations.
APT31 bossman profile: Intrusion Truth has posted a profile on Deng Zhiyong, the CEO of Wuhan Xiaoruizhi, which they claim is a former front company used to employ hackers for the APT31 Chinese cyber-espionage group.
RomCom attacks: The RomCom Malware-as-a-Service has been linked to a campaign targeting guests of the upcoming NATO Summit in Vilnius with malicious documents.
GhostWriter: In the meantime, in Ukraine, the country's CERT team says it spotted the GhostWriter APT (UAC-0057) target government agencies with a campaign delivering the PicassoLoader and njRAT.
APT28: The same Ukraine CERT team has also uncovered an APT28 phishing operation mimicking the Yahoo and Ukr.net portals.
APT29 fake in China: Lab52 researchers have identified an unknown threat actor using APT29's TTP in a phishing campaign against Chinese users. The company says there are several features that suggest that the attack was not perpetrated by the Russian group.
Vulnerabilities, security research, and bug bounty
New MOVEit flaw: Progress Software has released a security update for its MOVEit MFA software. Three bugs were fixed, including a critical one that led to an auth bypass.
GSA RCE: Devcore researchers have identified several vulnerabilities in the Google Search Appliance, an enterprise search device launched by Google in 2002. The device reached EoL in 2018, so no CVEs and no patches.
Ubiquiti fixes: Ubiquiti has released a security update for AirCub devices and EdgeRouters to fix a LAN arbitrary code execution vulnerability.
Mastodon fixes TootRoot vulnerability: The Mastodon project has fixed a critical vulnerability known as TootRoot (CVE-2023-36460) that allows threat actors to take over any Mastodon server by posting a toot with a malicious multimedia file attached. The vulnerability is as bad as it gets and received a severity rating of 9.9/10 on the CVSSv3 scale. Patches were released last week, days before details were published online. TootRoot was discovered by security researchers at Cure53 following a security audit performed at Mozilla's request. The audit discovered four security flaws in total.
Manifest confusion research: Lutra Security has analyzed the top 5,000 packages on npm and found that many are exhibiting signs of manifest confusion.
Apple zero-day RCA: PKSecurity has published a root-cause analysis of CVE-2023-32439, a WebKit zero-day that Apple patched last month on June 21.
Infosec industry
New tool—SlinkyCat: Security firm Lares has open-sourced a new tool named SlinkyCat that provides a PowerShell CLI menu for enumerating a Windows domain.
New tool—ShellGhost: Horizon Security researcher Angelo Frasca Caccia has released ShellGhost, a memory-based evasion technique that makes shellcode invisible from process start to end.
New tool—CybercrimeOps: Threat intel analyst Pancak3 has published an interactive mind map of connections between various cybercrime brands, organizations, and people.

Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the EU's proposed media freedom act and how one of its goals is to protect journalists from spyware.




