Risky Biz News: Ransomware wrecks Paraguay's largest telco
In other news: Stuxnet saboteur identified after 15 years; China cracks Apple's AirDrop; and ransomware developer arrested in the Netherlands.
This newsletter is brought to you by Stairwell. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
A ransomware attack has wreaked havoc inside the network of Tigo, the largest mobile operator and internet service provider in Paraguay.
The incident took place last Thursday, January 4, and impacted the telco's business branch.
Around 300 servers in Tigo's data center were encrypted, according to Miguel Ángel Gaspar, director of the Paraguay Ciberseguro Foundation.
At least 300 companies were impacted downstream. The companies lost phone service and files hosted on Tigo servers.
Some government organizations are believed to have been impacted. The Paraguayan Army's cybersecurity team has urged public and private sector institutions to take steps to harden their networks in the incident's aftermath.
The Tigo attack has been attributed by local media to a ransomware group named BlackHunt. According to Fortinet, the BlackHunt group emerged at the end of 2022 and is known to breach victims via unsecured RDP connections.
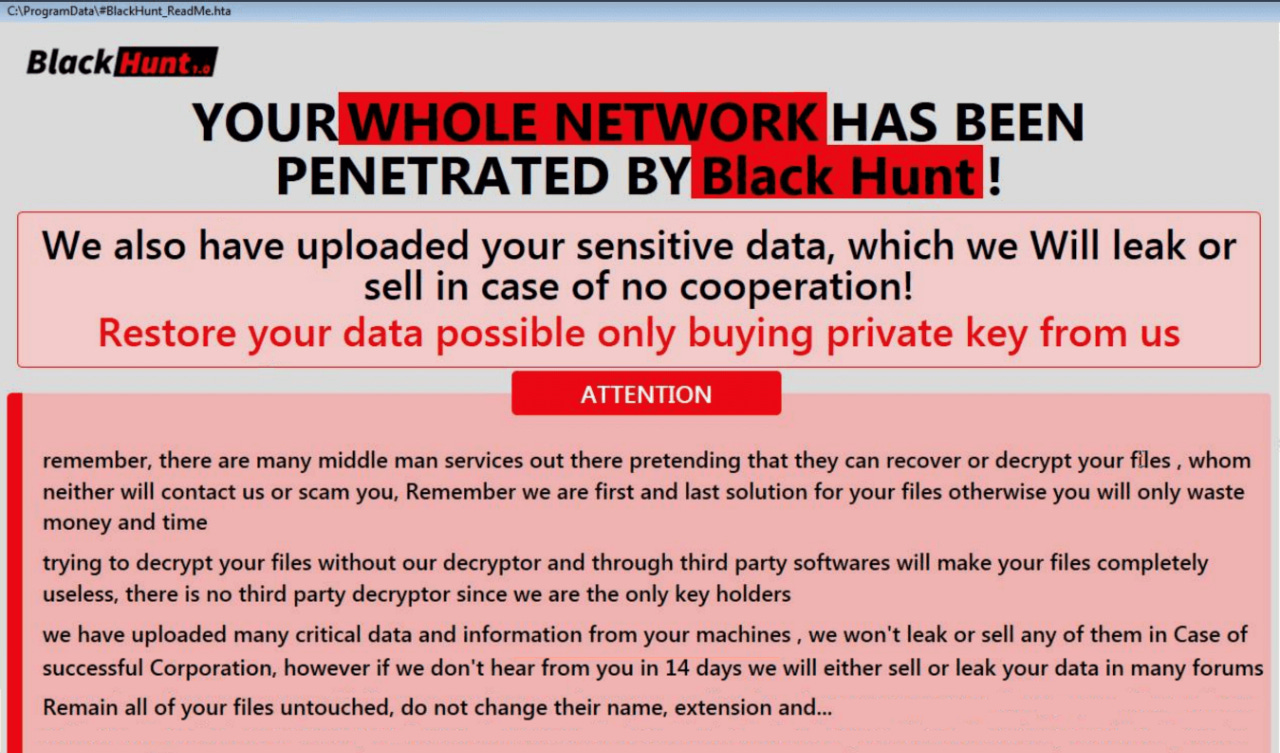
Besides encrypting data, the group is also known to steal files for secondary extortion attempts, although it does not operate a dark web data leak site like other ransomware crews.
According to a local radio station, Tigo has not contacted the group to negotiate a ransom.
The company put out a statement calling all reports on its incident "fake news," which, in turn, led to the company being ridiculed on social media and with some customers announcing plans to switch to another provider.
Breaches, hacks, and security incidents
Bit24 leak: Iranian cryptocurrency exchange Bit23.cash has leaked the personal information of more than 230,000 customers. The data leaked via an unsecured MinIO server that exposed the platform's AWS credentials. The exposed data included photos of passports, IDs, and credit cards, which customers uploaded on the site during the KYC process. [Additional coverage in Cybernews]
Inspiring Vacations leak: Australian travel agency Inspiring Vacations has leaked customer data after leaving one of its databases exposed on the internet without a password. The database leaked 26.8GB of data, containing more than 112,000 records, such as high-resolution passport images, travel visas, and itinerary tickets. [Additional coverage in The Age] [h/t Scrantic]
LoanDepot cyberattack: American mortgage provider LoanDepot has taken some of its IT infrastructure offline in the aftermath of a ransomware attack. The company is the fourth major US mortgage and real estate insurance provider that was hit by a cyberattack over the past months. Similar incidents have also affected Mr. Cooper, Fidelity National Financial, and First American Financial.
WCC cyberattack: The World Council of Churches got hit by a cybersecurity incident over the Christmas holiday. The incident is believed to be a ransomware attack, possibly carried out by the Rhysida gang. [Additional coverage in The Record]
Ukraine repels attack on state payment system: Ukraine says it repelled Russian cyberattacks against its state payment system for the second week in a row. Officials say Russian hackers tried to destroy vital systems used for budget payments. The operation comes after Russian hackers successfully wiped servers inside Kyivstar, the country's largest mobile operator.
AlfaBank leak: Ukrainian hackers have dumped the data of 38 million customers of Alfa Bank, one of Russia's leading banks. The data was dumped by KibOrg and NLB, the groups that hacked the bank in October last year. The bank initially denied getting hacked and later tried to downplay the size of the breach.
M9 Telecom hack: A Ukrainian hacktivist group named Blackjack has breached and leaked data from Russian internet service provider M9 Telecom. The group claims it wiped more than 20 TB of the telco's data, including internal servers and the company's official website. Blackjack says the attack was only a "warm-up," and they plan to target larger telcos as revenge for Russia's attack on Kyivstar. [Additional coverage in UkrInform / English coverage in the Kyiv Independent]
General tech and privacy
Authy EOL: Twillio will discontinue its Authy 2FA authenticator app for Linux, macOS, and Windows in August this year. The company has told customers to switch to its mobile apps, which will continue to be supported.
Project Mockingbird: McAfee has unveiled Project Mockingbird, a tool to detect AI-generated audio deepfakes.
New Sentry ToS: App performance monitoring service Sentry has updated its Terms of Service to give itself the right to use its customers' data to train AI models. No opt-out option will be included.
Copilot key: Microsoft has announced plans to add a new key to its keyboards. The new button will trigger the company's Copilot AI assistant and will sit next to the Right-Alt and Space keys. This marks the first new key added to Microsoft keyboards in nearly 30 years. [Additional coverage in Sky News]
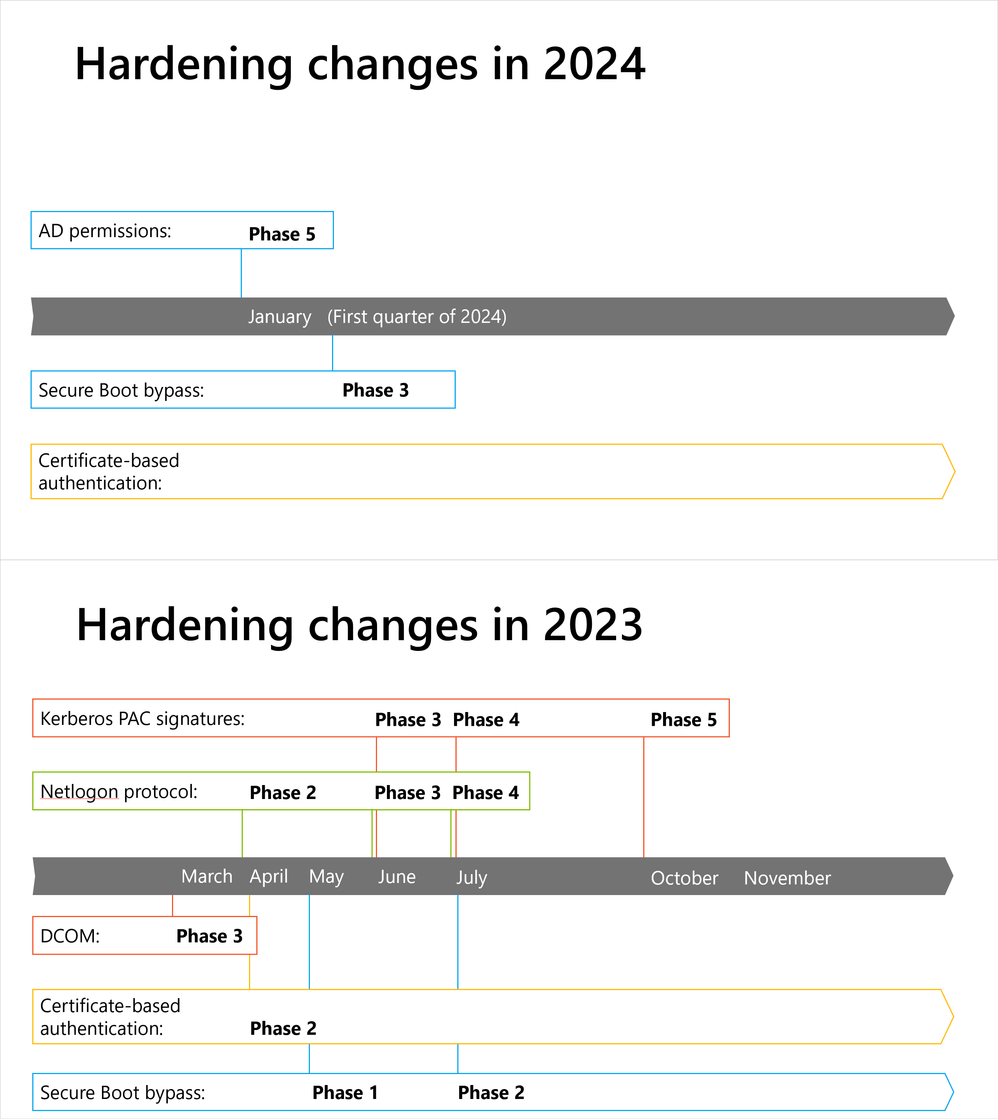
Windows hardening: Below is a calendar with Microsoft's major security and hardening dates for 2024. More details here.
OpenAI GDPR complaint: Polish privacy expert Lukasz Olejnik has filed an official GDPR complaint against OpenAI for the company's data processing practices.
Twitter becomes a problem: Verified Twitter users have pushed a wave of misinformation about the recent earthquake that hit Japan, showing how the social network has devolved from a place where you could get your breaking news to a site that will now endanger people's lives by pushing and promoting wrong information during a time of crisis. [Additional coverage in Vice]
Volkswagen integrates ChatGPT: German automaker Volkswagen announced plans to integrate the ChatGPT service into its vehicles. And now you know what car you should never buy in the next 3,401 years.
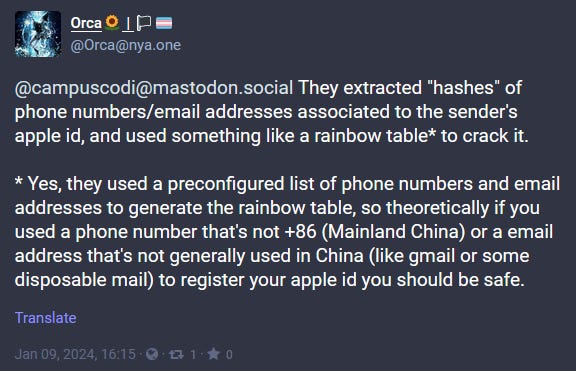
Beijing lab breaks AirDrop: The Chinese government says it detained several suspects who sent inappropriate messages using the Apple AirDrop feature. The arrests come after a local Beijing tech lab named Wangshen Dongjian developed a tool to crack the AirDrop protocol and extract a sender's phone number and email address. AirDrop was widely used in China in 2022 and 2023 to anonymously share anti-government posters and materials criticizing China's leader Xi Jinping. Apple limited access to AirDrop in November of last year at the government's request. [Additional coverage in GlobalTimes]
Government, politics, and policy
DNS4EU: Oxford professor Roxana Radu looks at DNS4EU, the EU's new DNS system designed to be used by EU agencies and member states.
IGIC report: A report [PDF] from the Office of the Inspector General of the Intelligence Community has found that over-classification, lack of guidance, and tensions with cybersecurity companies have hampered the US government's efforts to boost cyber threat intel-sharing efforts. [Additional coverage in CyberScoop]
NSA and AI: An NSA official admitted that the agency is using AI and ML technologies to detect malicious Chinese cyber activity. [Additional coverage in CyberScoop]
China to hunt down aviation-tracking devices: The Chinese government has announced a nationwide operation to identify and remove devices across China that track flights and share data with foreign entities. China's Ministry of State Security says it seized some devices and penalized individuals who installed them. Officials say the devices are a national security threat because they can also track military aircraft and not just public flights. [Additional coverage in SCMP]
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Chris St Myers, Stairwell's head of threat research, about managing the risk from software you absolutely must use.
Cybercrime and threat intel
Spamdot admins identified: Infosec reporter Brian Krebs has identified the real-world identities of Salomon and Icamis, the two administrators of the now-defunct cybercrime forum Spamdot. The two admins are named Alexander Grichishkin and Andrey Skvortsov. Both are Russian nationals and have already been detained by US authorities for running a bulletproof hosting service for malware operations. Both pleaded guilty, and Grichishkin is scheduled to be released from jail in February 2024 after serving his sentence. Skvortsov has yet to be sentenced.
Ransomware dev detained in the Netherlands: Dutch Police have arrested an Amsterdam man for creating and operating the Babuk Tortilla ransomware strain. Officials identified the suspect after receiving a tip from Cisco's Talos security team. Following the arrest, police officers obtained the ransomware's decryption keys, which they shared with Avast and Cisco Talos. The keys have been integrated into the Babuk ransomware decrypter available via the NoMoreRansom portal.
Myanmar rebels take control of scam city: A coalition of Myanmar rebels has taken control of Laukkaing, a city that has been a hub for online scamming operations known as "pig butchering." The Three Brotherhood Alliance is now in control of the city and the surrounding Kokang region. The rebel groups launched their offensive in October of last year with the explicit purpose of rooting out the cybercrime cartels, which they claimed were operating under the military junta's protection. [Additional coverage in The Record]
Coinbase phisher detained: The US Secret Service has arrested a 30-year-old Indian national for his involvement in a phishing operation that targeted Coinbase users. Authorities claim Chirag Tomar was part of a group that set up fake Coinbase login pages and then lured victims to the sites after emailing and calling victims. The gang is believed to have stolen more than $20 million from at least 500 Coinbase accounts. [Additional coverage in 404 Media]
Money launderer sentenced: A US judge sentenced a Nigerian national to 10 years and one month in prison for helping cybercriminals launder money obtained via internet fraud schemes.
Water Curupira: Trend Micro has published a profile on Water Curupira, an affiliate of the Black Basta ransomware gang specializing in the distribution of the Pikabot malware via email phishing campaigns. Trend Micro says systems infected with Pikabot have been used to drop backdoors and, later, the Black Basta ransomware.
RE#TURGENCE: A financially motivated hacking group known as RE#TURGENCE is targeting MSSQL databases to deploy the Mimic ransomware. According to security firm Securonix, the group gains initial access by brute-forcing the database's admin account. The company says the group operates out of the Republic of Türkiye.
YouTube malware campaign: Fortinet is tracking a threat actor using YouTube videos promoting cracked software to distribute apps infected with the Lumma infostealer.
KEV update: CISA has updated its KEV database with six new vulnerabilities currently actively exploited in the wild. The list includes zero-days in ColdFusion, Apple, Apache Superset, Joomla, and D-Link systems.
Q4 2023 DDoS trends: Internet infrastructure company Cloudflare says it saw a massive 61,839% surge in DDoS traffic that targeted environmental protection websites during the 28th United Nations Climate Change Conference (COP 28).
Malware technical reports
None in this edition.
Sponsor Section
Stairwell's Mike Wiacek demonstrates Stairwell's file analysis and threat detection platform to Risky Business host Patrick Gray. Stairwell helps you monitor and analyze every executable file in your organization, automatically collecting crucial intelligence and providing your security team with in-depth visibility and detections.
APTs, cyber-espionage, and info-ops
UAC-0184: CERT-UA has published IOCs and details about a spear-phishing campaign conducted by a group the agency is tracking as UAC-0184. The campaign was initially spotted by Trend Micro and its final payload is the Remcos RAT and the ReverseSSH shell.
Stuxnet saboteur: Dutch journalists have revealed the name of the person who helped the US and Israel deploy the Stuxnet computer virus inside Iran's nuclear program in 2008. Reporters say that a Dutch engineer named Erik van Sabben installed water pumps that contained the Stuxnet inside Iran's uranium enrichment facility at Natanz in 2008. Van Sabben was allegedly recruited by the Dutch AIVD intelligence service, although Dutch officials say they didn't know they were deploying a computer virus. Van Sabben died in a motorbike accident two weeks later near his home in Dubai, and Stuxnet exploded into a global malware epidemic two years later in 2010. [Additional coverage in De Volkskrant / English coverage in NLTimes / 2019 article on the topic]
Vulnerabilities, security research, and bug bounty
Zengo hacking challenge: Crypto-wallet maker Zengo launched a hacking challenge, inviting anyone to hack one of its demo wallets and keep the 10 Bitcoin (~$420,000) stored inside.
Lantronix vulnerabilities: Pentagrid researchers have identified several vulnerabilities in Lantronix EDS-MD IoT gateway devices. Fixes are scheduled to go live on January 12, 2024.
OFBiz exploitation: Prio-n researchers analyze two recent Apache OFBiz vulnerabilities, including one that is under active exploitation.
Bosch Rexroth vulnerabilities: Nozomi researchers have found 23 vulnerabilities in Bosch Rexroth nut-runners, pneumatic torque wrenches used in automotive industry production lines.
Control-M vulnerabilities: Security engineer Guillaume Quéré has found four vulnerabilities that can be chained to take control of the web console of BMC's Control-M, an application workflow orchestration solution.
CS:GO attack surface: Synacktiv researchers have published research looking at the attack surface of Counter-Strike: Global Offensive (CS:GO), one of the internet's most popular games over the past decade. The research was published after Valve launched CounterStrike 2.0 last fall. The found bugs were never fixed, which is a very bad look for Valve.
"Overall code is legacy and does not implement in-depth security protections. [...] Reporting the bug to Valve through HackerOne managed program was a long process, as shown in the timeline available below. The ticket was closed with the release of Counter-Strike 2 and the impacted code is no longer present. In fact, to our knowledge, no patch was released in the meantime, despite multiple follow-ups."
KyberSlash attack: Security researcher Daniel J. Bernstein has published details on KyberSlash, a security flaw in libraries that support Kyber, a quantum-resistant key encapsulation mechanism. Many libraries have yet to be patched.
ZDI stats: Trend Micro says its Zero-Day Initiative (ZDI) private bug bounty program has helped security researchers file and report 1,913 bugs throughout 2023. The company says that "nearly 3 of 4 [of all reported vulnerabilities] were rated Critical/High risk."
Patch Tuesday: Yesterday was the January 2024 Patch Tuesday. We had security updates from Adobe, Microsoft, Cisco, SAP, Fortinet, Zoom, Splunk, Joomla, Firefox, Intel, Siemens, and Schneider Electric. The Android Project, Chrome, Atlassian, Ivanti, and QNAP released security updates last week as well. This month, Microsoft patched 53 vulnerabilities. No zero-days this time.
Infosec industry
Acquisition news: Private equity firm the MC² Security Fund has acquired cybersecurity firm Trustwave from Singtel for $205 million.
New tool—YARA Toolkit: Microsoft security researcher Thomas Roccia has released YARA Toolkit, a web app for writing YARA rules.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk with infosec and anti-virus veteran Martijn Grooten about how the infosec industry has changed over the years.




