"Putin's Chef" Cooks up Infosec Disaster
PLUS: The Problem With Security is Security Software
Your weekly dose of Seriously Risky Business news is written by Tom Uren, edited by Patrick Gray with help from Catalin Cimpanu. It's supported by the Cyber Initiative at the Hewlett Foundation and founding corporate sponsor Proofpoint.
A group of "unknown hackers" have stolen a million internal documents from businesses controlled by Yevgeny Prigozhin, a.k.a. "Putin's Chef", an influential Russian businessman and the founder of the Wagner Group mercenary outfit.

In addition to Wagner, Prigozhin controls other state-linked companies such as a large catering business and the Internet Research Agency, which used social media to interfere with the 2016 US Presidential election. At various times he's been described as a close confidant of Vladimir Putin, although that closeness has probably been overstated in most public reporting.
The investigation into his business empire's IT operations, fueled by an analysis of the stolen documents, was published by Dossier Center, a Russian transparency initiative funded by exiled Russian opposition figure Mikhail Khodorkovsky.
The expose (English translation here) based on the leaked documents makes for remarkable reading. There's the substance of the documents — he's apparently been keeping two sets of accounting books, for example — and then there's the meta revelations about how Prighozin's organisation approaches security. Its approach to infosec is, to put it one way, extremely not great.
His team deployed highly visible security controls that are pretty much pointless because they're built on awful foundations.
A great example of this is the Wagner Group's "closed" smartphones. These were commercially available Samsung phones running a custom Android OS on top of an OpenVPN network using self-signed certificates.
This VPN network could be accessed directly from Prigozhin's Concord conglomerate's corporate network, since, after all, why not mix private military forces with construction and catering?
These closed phones weren't exclusive to Wager Group, however, and were also given to Russian Defence officials, foreign partners such as the president of the Central African Republic, and also "designers, video editors and other PR people".
As for Prigozhin himself, after a prior breach, he swapped his beloved iPad for a non-internet-connected Psion personal digital assistant.

For a high-profile figure like Prigozhin, not connecting to the internet is good. Unfortunately (for him, anyway) his Psion device was regularly backed up to the corporate network. All the information it contained, including meeting schedules and contact details, was stored in a shared network folder. And this corporate network was riddled with old Windows — Server 2008R2 and even XP were everywhere.
So here we have two measures — fancy encrypted phones and offline devices — completely undermined by their reliance on a tragically insecure enterprise network.
And what a wild place that network was. Check out their password handling practices:
Prigozhin's employees often used the same passwords by default, stored them in plain text files, and sent each other files with server addresses, login passwords, and user certificates. Based on the data in these files, multiple mail accounts use the same passwords. The Dossier Center has refrained from checking their relevance, but there are good reasons to suspect that they are never changed. On the other hand, the study of passwords makes it possible once again to make sure that Prigozhin's employees have certain tendencies: the numbers 1488 often turn out to be part of the password. However, sometimes Prigozhin's employees added these significant numbers to the outgoing numbers of official documents.
Dossier Center describes the paradox of highly visible security measures coupled with "an absolute disregard for digital security — no [infosec] employees, no training, no instructions, no encryption, no quality monitoring of the network infrastructure". The Center's report speculates that this is because Prigozhin is primarily concerned about being investigated by the FSB.
This makes sense — the real threats to Prigozhin come from Putin's regime, and compromise by US intelligence probably has relatively few consequences for him personally. Appearing on the FBI's most wanted list just makes him look cool.
We wonder, however, if there is also an element of security theatre at play here that's designed to "embiggen" Prigozhin's operation. Giving "special" phones to dignitaries and PR people is surely about sprinkling magic secret pixie dust on his ventures rather than providing genuine OPSEC benefits. Anyway, go read the full report. It's really funny.
The Problem With Security is Security Software
Security firm Mandiant has published an analysis of the 55 0days exploited in the wild in 2022, examining who used them and what they were used for. The report's figures show that the soft underbelly of security is… security and network products.
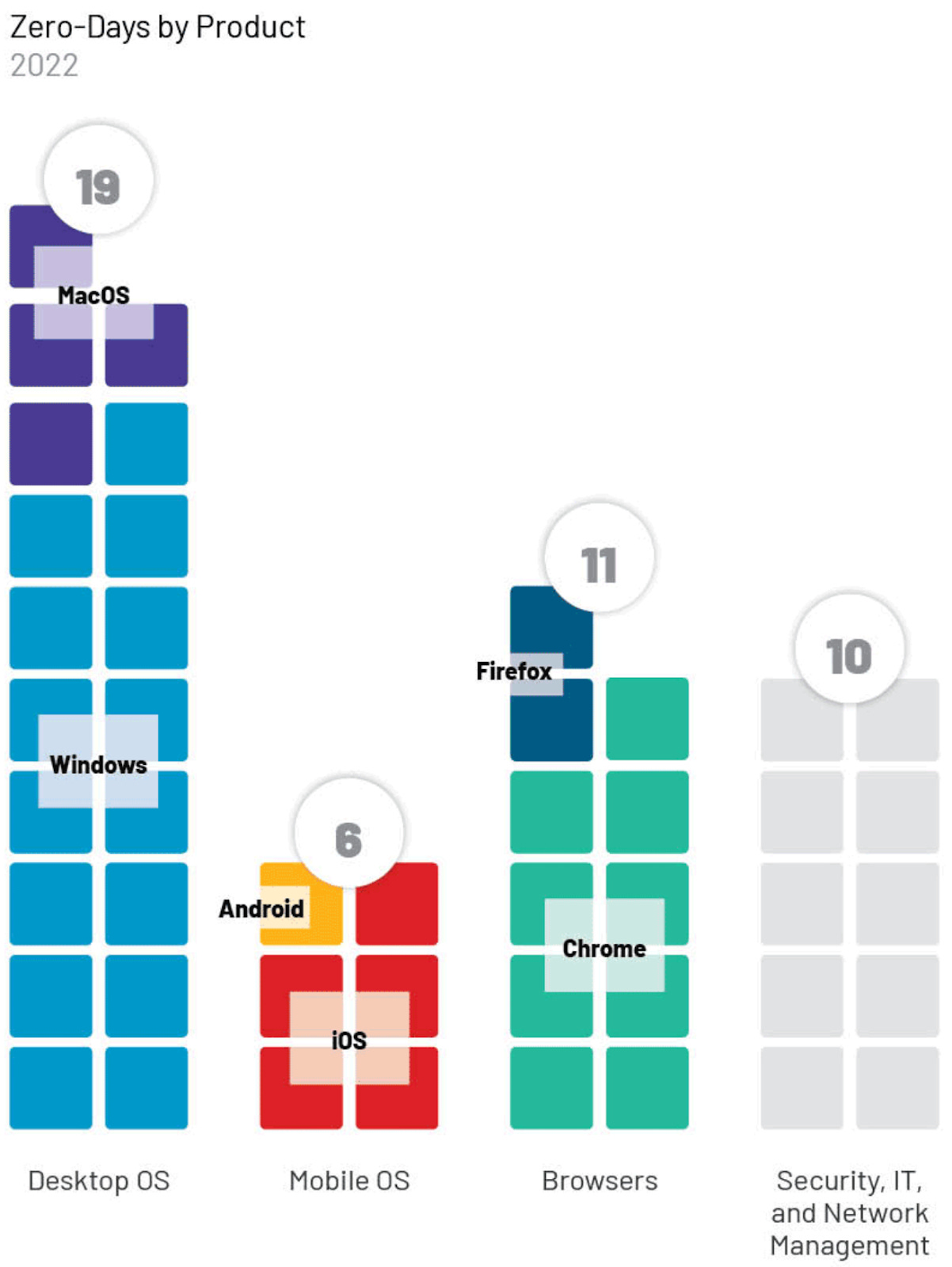
In the most illuminating part of the report, Mandiant looks at 2022's 0days by product type and vendor.
When it comes to vendors, the most popular ones get the most attention, with Microsoft, Google and Apple each getting their fair share. There were, however, a swathe of 0days (nearly 20%) in a range of more niche providers that provided security, IT, or network management products from vendors such as Sophos, Cisco, Trend Micro, and Fortinet, among others.
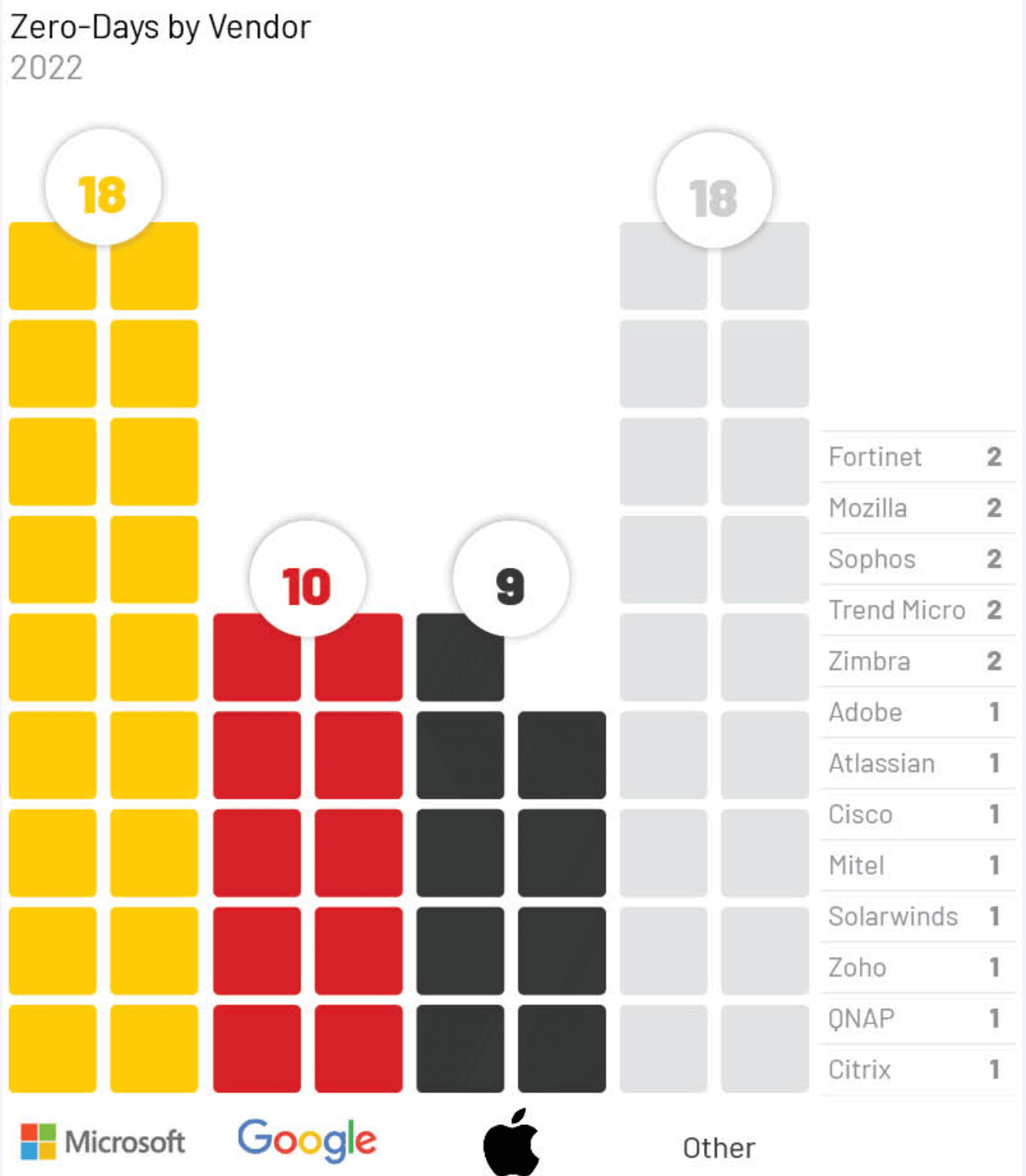
Mandiant notes that many of these devices are what it calls "edge infrastructure" and are attractive targets for attackers. Benefits for attackers include that these devices are accessible from the internet, often don't run endpoint detection solutions, and can provide access to networks without user interaction.
In 2021 this newsletter railed against vulnerabilities in these types of devices as they were often being exploited by ransomware actors to cause havoc once they were publicly disclosed. Although most aren't attributed to any particular actor, Mandiant thinks that Chinese state-sponsored actors are focusing on network devices, citing last year's Fortinet SSL-VPN and firewall device 0days.
This all makes sense. Big, popular platforms and products like Windows, iOS, and Chrome, to name just a few, get a lot of attention because that is where the people are. Relatively niche security products get a lot of attention because that's where network access opportunities are.
When it comes to who is using 0days, however, the data is a lot more sparse.
Mandiant thinks that 13 of the 55 0days were used by cyber espionage groups with "moderate to high" confidence. Chinese groups led with seven 0days, Russia and North Korea with two each and commercial vendors were responsible for three 0days. (One 0day, a Microsoft Office one known as Follina, was exploited by multiple cyber espionage groups so the total doesn't match the sum of attributions to individual actors.)
The prominent PRC use of 0days is consistent with previous years, but given that most campaigns using 0days couldn't be attributed, it's a bit hard to know what to make of this. Are Chinese state-sponsored actors just noisier and getting caught more relative to other countries' espionage programs? Is their OPSEC just as good as anyone else's, but they simply run more operations?
Only four of the 55 0days were pegged to groups looking for financial gain, i.e. cybercriminals. So the majority of 0days couldn't be attributed to any actor at all (39 of the 55). Given the difficulty of solid attribution, looking at 0days through the lens of the actor responsible may just not be the right way of approaching this data.
Overall, our take home message is that critical enterprise network products are still a trash fire. It's a small consolation that poor security in this class of products is precisely what the recent National Cybersecurity Strategy aims to remedy.
The big idea in the strategy is to prevent software vendors from absolving themselves of any liability — via their end user license agreements — when things go wrong. Companies that can demonstrate adherence to modern secure development frameworks will be exempted from this liability shift, though. This will give vendors strong incentives to do better and Mandiant's 0day report shows why it is needed.
Everyone Gets Out Alive in Forced TikTok Sale
The Biden administration is reportedly demanding that TikTok's China-based owners ByteDance sell the app. The political realities mean that this is absolutely the least bad move for everyone involved.
One naive view is that TikTok is no different from, say, Facebook, Twitter, or Instagram. When we first wrote about TikTok in June of last year, Fergus Ryan, Senior Analyst at the Australian Strategic Policy Institute and author of a report on censorship on TikTok and WeChat, told this newsletter there was one very significant difference.
"[Different social media platforms] are all influential in their own way, but only TikTok is under the thumb of the Communist Party," he said.
Reinforcing Ryan's comments is a recent submission to an Australian parliamentary Committee on Foreign Interference through Social Media. Among other things, the (113-page long!) submission details the links between TikTok, its Chinese parent ByteDance and the Chinese Communist Party (CCP) and provides examples where ByteDance has responded to CCP concerns. In one case, for example, ByteDance promised to prioritise recruitment of CCP members as content reviewers after the company was criticised for disseminating "pornographic and vulgar" information.
The submission also makes it clear that developing overseas propaganda capacity is a goal of Xi Jinping and the CCP:
In May 2021, Xi returned to another Politburo "Study Session" and instructed his colleagues to use the "external discourse mechanisms" that they had built in order to "target different regions, different countries, and different groups of audiences" with "precise communication methods" in order to "make friends, unite and win the majority, and constantly expand our circle of friends who know China and are China-friendly."
The submission also tries to quantify the likelihood and consequences of different risks that TikTok represents (see chart).

We think some of these risks are overstated, or could be easily mitigated by, say, not installing the app in the first place. These are also untreated risks without any compensating controls, so TikTok's proposal to mitigate some of these concerns probably could make some difference.
Conceptually, the sober analyst in us likes the idea of spelling out specific concerns, mitigating them and seeing if we can live with the residual risk. When balanced against the benefits that TikTok provides to both creators and consumers the treated risk might even be small enough to let TikTok push ahead with its plans.
All this analysis is irrelevant, however, given the polarised political environment and anti-CCP sentiment.
It's an absolute certainty that TikTok will be used to influence upcoming US elections — legitimately, by US citizens, expressing real political sentiments, being amplified by TikTok because that is just how the app works. Both political parties will be able to point to campaigns on TikTok that hurt their interests and it'll be impossible to confirm that they weren't somehow buffed or nerfed by secret CCP influence.
The nightmare scenario here is that if the 2024 US presidential election is at all close the losing party could dispute the election's legitimacy by claiming that the CCP used TikTok to swing the election. Even assuming no manipulation, how would TikTok prove a negative? This would be bad for US democracy, bad for TikTok, and even bad for US-China relations. A disputed election is a huge problem regardless, but there is only one way to ensure that TikTok isn't in the centre of it.
From the US perspective a forced sale is the only way to resolve concerns about CCP interference. As for ByteDance, a forced fire-sale is bad, but TikTok being banned after a close and contentious election would be far, far worse.
It's not an ideal situation. Looking down the road, however, the intent behind the RESTRICT Act that we covered last week is to prevent these situations arising in the first place.
Three Reasons to be Cheerful this Week:
- BreachForums owner "Pompompurin" arrested: A New York man, Conor Brian Fitzpatrick was arrested last week by the FBI and is allegedly the owner of the BreachForums data breach website and uses the alias Pompompurin. BreachForums is a popular English-language cybercrime forum and Krebs on Security has a good potted summary of some of Pompompurin's exploits, including that he claims to have used an FBI portal software misconfiguration to send fake emails from the FBI. In doubly good news, BreachForums is apparently down for good after the new administrator decided the site "is not safe anymore" after discovering evidence of government infiltration of the site. [more at Risky Biz News]
- MeowCorp ransomware decryptor: Kaspersky has released a free decryptor for a variant of Conti ransomware used by a group known as MeowCorp. The private keys were published on a forum when MeowCorp shut down. Based on their analysis of the data that was published Kaspersky thinks that only 14 of 257 victims paid a ransom.
- Darknet crypto laundering site ChipMixer takedown: Last week a coalition of international law enforcement agencies took down ChipMixer, a darknet cryptocurrency mixer. The site is accused of laundering over $USD3bn worth of cryptocurrency since 2017, including more than USD$700m associated with North Korean actors alone. [more details at Risky Biz News]
Sponsor Section
Seriously Risky Business is supported by the Hewlett Foundation's Cyber Initiative and corporate sponsor Proofpoint.
Proofpoint's 2023 State of the Phish report finds that paying ransoms is a coin toss. Only 52% of victims got their data back after making a single ransom payment.
According to our 2023 State of the Phish report, only about half of #ransomware victims received their #data after making an initial payment.
— Proofpoint (@proofpoint) 3:05 PM ∙ Mar 20, 2023
Over 40% were required to pay >1 ransom before regaining access. 1% paid and got nothing at all in return.
More: ow.ly/bnkA50NlEYe
Tines No-code Automation For Security Teams
Risky Business publishes sponsored product demos to YouTube. They're a great way for you to save the time and hassle of trying to actually get useful information out of security vendors. You can subscribe to our product demo page on YouTube here.
In this video demo, Tines CEO and co-founder, Eoin Hinchy, demonstrates the Tines automation platform to host Patrick Gray.
Shorts
DJI Drone Fears Slide Into Slippery Slope Tropes
A group of US Senators has formally asked CISA to reassess the risk of using DJI drones.
The Senators said the use of DJI drones to inspect critical infrastructure would allow the Chinese Communist Party "to develop a richly detailed, regularly updated picture of our nation’s pipelines, railways, power generation facilities, and waterways". The letter continues that this information could "better enable targeting efforts in the event of conflict".
We think this chain of risk here is a bit too long. If DJI is passing that rich information to the PRC and if there was a conflict and if the PRC were willing to attack US critical infrastructure its targeting might be better. This has to be weighed against the ongoing benefits that inspection of critical infrastructure with cheap Chinese drones provides right now.
The letter also cites a Department of Homeland Security warning about DJI drones. This warning states that after a California wine producer bought DJI drones to monitor grape production Chinese companies began purchasing vineyards in the same area "soon afterwards". The DHS warning continues "according to the SOI [source of information], it appeared the companies were able to use DJI data to their own benefit and profit".
That tale strikes us as extremely thin. The source said "it appeared" the companies used DJI data? So… Chinese companies were just waiting for somebody to fly a DJI drone before they bought wineries? Or perhaps they used satellite imagery or even… flew their own drone!
There certainly are organisations that shouldn't accept the risk of using DJI drones. But for most we think practical guidance about how to minimise risks is probably better. Or industrial policy that encourages the development of a trusted competitor.
Meta Employee Targeted by Greek Spyware
Artemis Seaford, a US-Greek national who worked on Meta's security and trust team was wiretapped by the Greek national intelligence service and also hacked with Predator mobile spyware, according to The New York Times.
Predator is mobile spyware developed by a company called Cytrox, and it looks like those responsible for the wiretap and Predator hack were connected. After booking a Covid-19 vaccination booster and receiving an SMS confirmation, Seaford later received a second text message asking to confirm her appointment details by clicking a link. This link infected her phone with Predator, suggesting that the details in the first text were used to craft the subsequent message used to compromise Seaford's phone.
It is always possible that Seaford was the lawful target of authorised surveillance. On the other hand, the Greek government denies the use of Predator and what is known of the spyware's use is… sketchy.
Risky Biz Talks
In addition to a podcast version of this newsletter (last edition here), the Risky Biz News feed (RSS, iTunesor Spotify) also publishes interviews.
In our last "Between Two Nerds" discussion Tom Uren and The Grugq discuss the balance between offence and defence. Network defenders control the environment and should have total visibility, so why don't they always "win"?
From Risky Biz News:
Samsung smartphones impacted by no-user-interaction zero-days: Google's Project Zero research team has identified 18 vulnerabilities in Exynos, a modem chipset manufactured by South Korean company Samsung and used by multiple smartphone vendors [including some of Google's Pixel devices] and even some vehicles.
Project Zero says that of the 18 vulnerabilities, four are incredibly dangerous as they allow for what the company calls "Internet-to-baseband remote code execution attacks" with no user interaction and only require that the attacker knows the victim's phone number.
[more at Risky Biz News, including mitigation steps if you own an affected device]
Monti leaks Donut: The Monti ransomware gang has leaked the cPanel (web hosting software) credentials for one of their rivals, the Donut data extortion group. In a post on the Monti leak site, Monti claims the Donut gang did not fulfill the terms of a "deal" and stole $100,000. No other details at the moment, but grab your popcorn.
Google wants to reduce lifespan of TLS certificates from one year to just 90 days: Google has announced plans to reduce the maximum lifespan of a TLS certificate from the current value of 398 days to only 90 in a move that is going to send shockwaves across several IT industries. [more at Risky Biz News]



