Risky Biz News: PowerShell's official package repo is a supply chain mess
In other news: LinkedIn hit by wave of account hijacks; the US Chamber of Commerce wants one-year delay for SEC cyber rules; and China passes AI regulation.
This newsletter is brought to you by Thinkst, the makers of the much-loved Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
PowerShell Gallery, the official repository for the PowerShell scripting language, contains (still-unfixed) design flaws that can be abused by threat actors for typosquatting and impersonation attacks.
Discovered by cloud security firm AquaSec, these issues can be weaponized in supply chain attacks to trick developers into downloading and running malicious PowerShell packages on their systems or inside enterprise applications.
The first issue researchers found was that PSGallery does not come with any kind of protection against typosquatting, allowing threat actors to register packages that mimic the names of more successful PowerShell modules just by adding punctuation inside the name.
This behavior is the exact opposite of what GitHub does on npm, where developers can't register new packages that resemble popular libraries just by adding dots, dashes, and underscores in the names.
Even worse, the PSGallery also allows threat actors to copy the metadata of any PowerShell module, including the highly-coveted "Author(s)" and "Owners" fields, allowing threat actors to pass malicious packages as coming from legitimate developers and companies.
A proof-of-concept package showcasing both of these issues can be seen here, where a PowerShell module developed by AquaSec named Az.Table perfectly mimics the original AzTable package, including the author field, which lists a Microsoft employee as its creator.
A last bug also allows threat actors to list a user's entire list of packages, including private and unpublished libraries. Such information could be used for more targeted supply chain or dependency confusion scenarios, where knowledge of private packages can help attackers fine-tune their copycat modules.
AquaSec has disclosed its findings this week after reporting the three issues to Microsoft last September. The company says that although Microsoft tried to fix the issues twice, the design flaws are still present on the PSGallery portal and are still reproducible/exploitable. Hmm... I wonder where I've heard something like this before.

Knowledge of these issues and the fact that they're still open to exploitation will most likely contribute to a rise in attacks targeting PSGallery.
Right now, npm and PyPI bear the brunt of most typosquatting and supply chain attacks, mostly because of their popularity and ease of attacks.
With PowerShell playing a crucial role in enterprise automation operations, the PSGallery checks all the boxes on an attack vector ripe for exploitation.
Breaches, hacks, and security incidents
LinkedIn account hacks: Hackers are breaking into LinkedIn accounts and locking users out of their profiles, according to reports on Reddit, support forums, and security firms. The accounts are allegedly being compromised due to password reuse. Compromised accounts typically have their email address changed to a Rambler[.]ru alternative, suggesting most of the recent hacks are being conducted by the same threat actor. Some users reported receiving ransom demands, with the hackers offering to restore their account access for a small sum of cryptocurrency.
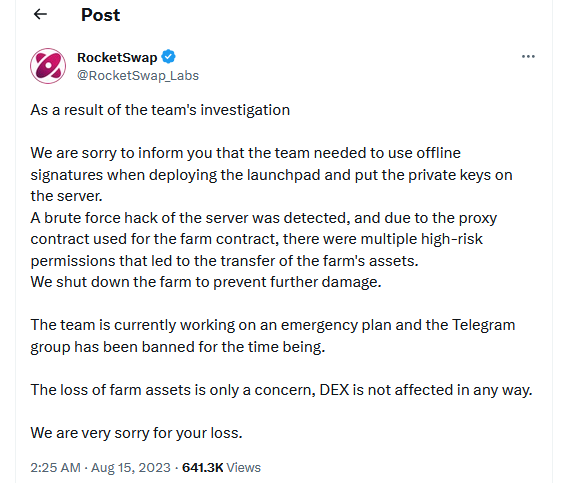
RocketSwap crypto-heist: The RocketSwap cryptocurrency platform was hacked for $860,000 worth of assets. The crypto-heist took place after the hackers brute-forced one of the company's servers and stole one of its wallet's private keys.
General tech and privacy
Quantum resilient FIDO2 security key: Google has developed the first-ever version of a FIDO2 security key that includes protections against quantum computing attacks. The implementation is a new version of OpenSK, an open-source project that provides free firmware for security keys. Google says this new OpenSK firmware version uses a novel ECC/Dilithium hybrid signature schema its engineers co-developed together with academics from ETH Zurich.
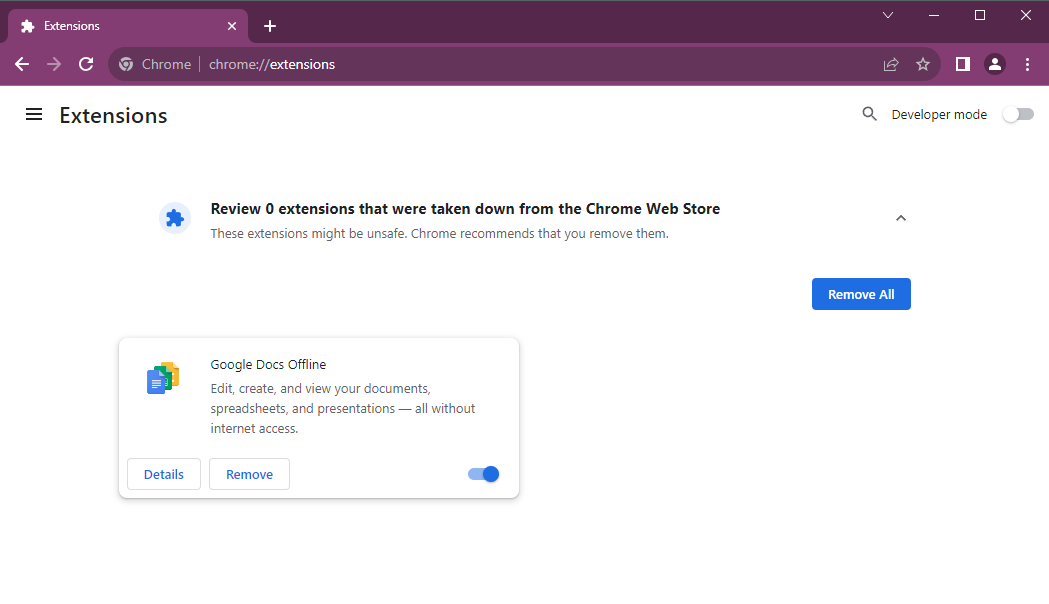
Chrome extensions scan: Google will show notifications to Chrome users when one or more of their installed extensions are removed from the official Web Store. The notifications will be shown when an extension is marked as malware, the extension is removed for ToS violations, or when the extension is unpublished by its developer. The new feature will come in Chrome 117, scheduled for release at the start of September. Chrome 116 users can enable it right now via this Chrome flag:
chrome://flags/#safety-check-extensions
Chrome HTTPS-First Mode: Google says it is running tests to enable HTTPS-First Mode for all its users in the near future.
Stupid Windows Server bug: There's a dumb bug making the rounds where Windows Server will reset system clocks to random times. The issue has been traced to a bug in the Windows Secure Time Seeding system. [Additional coverage in ArsTechnica]
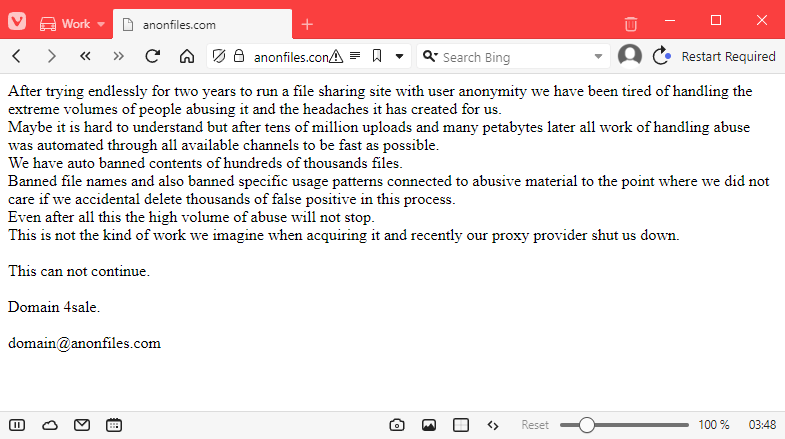
AnonFiles shuts down: Anonymous file-hosting service has called it quits and shut down its service out of the blue. In a message posted on its former homepage, admins say they got "tired of handling the extreme volumes of people abusing" its service.
Government, politics, and policy
US CoC wants delay of SEC cybersecurity rules: The US Chamber of Commerce has asked the SEC to delay the implementation of its new cybersecurity and data breach disclosure rules for at least a year. The new rules mandate that companies report security breaches to the SEC within four days after an incident has been deemed to have caused material losses. The new reporting guidelines are set to enter into effect in December for larger companies and June next year for smaller organizations. In a letter sent to the SEC this week, the Chamber says the new procedures are vague and create conflicting obligations for companies. Former CISA Director Chris Krebs also criticized the new rules, pointing out they overlap with already-existing CISA breach reporting rules. [Additional coverage in CybersecurityDive]
White House plan to replace legacy IT: The White House is working on a plan to replace legacy IT systems across federal civilian agencies. The Office of Management and Budget will be in charge of developing and implementing the ten-year IT modernization effort. The plan is part of the Biden Administration's recent National Cybersecurity Strategy, a concerted effort to improve the nation's cyber posture. [Additional coverage in GovTech]
CISA RMM plan: CISA has published a proactive plan to help government agencies mitigate the risks of deploying and using Remote Monitoring and Management (RMM) software in the environments.
Space Force satellite targeting unit: The US Space Force has established its first-ever squadron dedicated to targeting enemy satellites. From the official press release, it is unclear if this will involve any cyber capabilities or if this is a classic kinetic, space, and electromagnetic warfare.
Japan hiring cyber-personnel: Japan's Ministry of Defense is looking to hire 500 people for space and cyber-personnel jobs. The hiring effort is part of a multi-year plan to boost Japan's cyber defense forces by more than 20,000. [Additional coverage in Nikkei/non-paywall]
China's passes AI regulations: The Cyberspace Administration of China has introduced new regulations for the development and use of generative artificial intelligence (AI) systems. The new regulations introduces rules that developers must ensure their AI systems follow, such as marking their content as AI-generated and making sure the generated content doesn't damage the party or national security. The new regulations entered into effect this Tuesday, August 15.
SORM laws update: The Russian government has proposed an amendment to its SORM laws to give the FSB and other intelligence services access to internet data intercepted via the SORM system in real-time. Previously, the FSB could only access internet logs but not real-time traffic. Officials say this is to allow law enforcement to detect "crimes using bank cards," but we all know this is not the real reason. [Additional coverage in Forbes Russia]
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Jacob Torrey, Thinkst's Head of Labs. Jacob produces ThinkstScapes, a brilliant quarterly summary of the most interesting security research from around the world. Jacob talks about his favorite research in this edition, why Thinkst invests the time and effort in producing ThinkstScapes, and also talks about Thinkst Citation, a companion product that contains information about nearly 70,000 security talks going all the way back to 1993.
Cybercrime and threat intel
LABRAT: Sysdig researchers have discovered a new threat actor they named LABRAT that hijacks GitLab self-hosted servers. The purpose of the attacks is to deploy cryptomining scripts or enlist the hacked servers in a Russian-affiliated proxy bandwidth-jacking scheme. Sysdig says LABRAT stood out compared to other similar gangs because of its emphasis on stealth and defense evasion in their attacks.
0ktapus becomes AlphV affiliate: Newly uncovered evidence suggests the 0ktapus (Scattered Spider) threat actor is now working as an affiliate for the AlphV ransomware operation. The group has made a name for itself by extorting Riot Games and Reddit in January and February this year. Early signs that 0ktapus switched to working with AlphV came in June this year when Reddit's data was posted on AlphV's dark web leak site. This was later confirmed a month later when the Canadian Center for Cyber Security released a security alert for an AlphV attack that included both AlphV and 0ktapus IOCs.
Phishing campaign targets energy sector: Cofense spotted a massive phishing campaign using malicious QR codes sent via email, targeting companies in the US energy sector.
Zimbra phishing campaign: ESET has detected a worldwide phishing campaign targeting Zimbra email users.
New Gozi campaigns: IBM X-Force analyzes some recent Gozi malware campaigns.
PlayCrypt campaign: Adlumin researchers have spotted a threat actor targeting Fortinet firewalls to breach networks and deploy the PlayCrypt (Play) ransomware.
Unsupported archive formats: Mobile security firm Zimperium is seeing an increase in the number of malicious Android apps that use exotic or unknown compression algorithms to archive their APK files. The technique prevents mobile security tools or researchers from decompiling apps and analyzing their code and behavior. The downside to this technique is that many apps also trigger errors and may not load on an infected device. So far, Zimperium says it has seen more than 3,300 malicious apps use this technique to avoid detection, but only 71 loaded and ran properly.
"None of these applications are currently available in the Google Play Store and we do not have any evidence to support that they were at any point in time. For this reason, it's likely that the distribution method was through third party stores or through tricking the user to sideload the app using some sort of social engineering or phishing attack."
Cloudflare R2 abuse: Between February and July 2023, security firm Netskope says it observed a 61-fold increase in traffic to phishing pages hosted on Cloudflare's cloud storage service R2. Netskope says R2 is one of the 162 different cloud apps and services that have been abused to host phishing content last month. A similar report from RecordedFuture found widespread abuse of cloud services, with Google Drive, Telegram, and Discord being the most abused services.
Malware technical reports
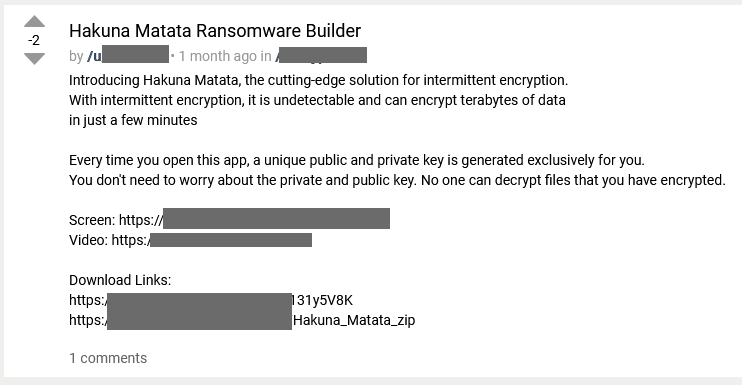
Hakuna Matata ransomware: AhnLab researchers have spotted attacks with the Hakuna Matata ransomware. The ransomware has been around since 2017, but the new attacks come after its builder was leaked last month, in July.
Silver Fox: Qihoo 360's CERT team has a breakdown of the malware used by Silver Fox, a malware gang targeting Chinese companies using SEO poisoning attacks to classic email phishing operations.
Boat (Ripper) botnet: Chinese security firm NSFOCUS says that activity from the Boat botnet has ramped up this month, growing into a force "that cannot be ignored." The botnet, which appeared in June of last year, has evolved into a threat that can target CCTV systems, routers, and even Android devices. The Boat botnet can now also spread via both vulnerability and weak password exploitation, and its main functionality is carrying out DDoS attacks. QiAnXin researchers track this botnet as Ripper.
KmsdBot: Akamai says the KmsdBot botnet has returned to life after its researchers crashed its operations back in December 2022. The malware's new version seems to be focused on infecting IoT devices for the purpose of DDoS attacks. This is a change from its original purpose of performing hidden cryptocurrency mining. Just like last year, the malware still spreads by targeting systems that use weak SSH login credentials.
Proxyware network: AT&T researchers say they have found the Windows version of the malware used to turn macOS systems into exit nodes for a residential proxy network. The malware, written in Go, enlists infected devices into a proxy network ran by a company that claims to provide access to more than 400,000 different IP addresses.
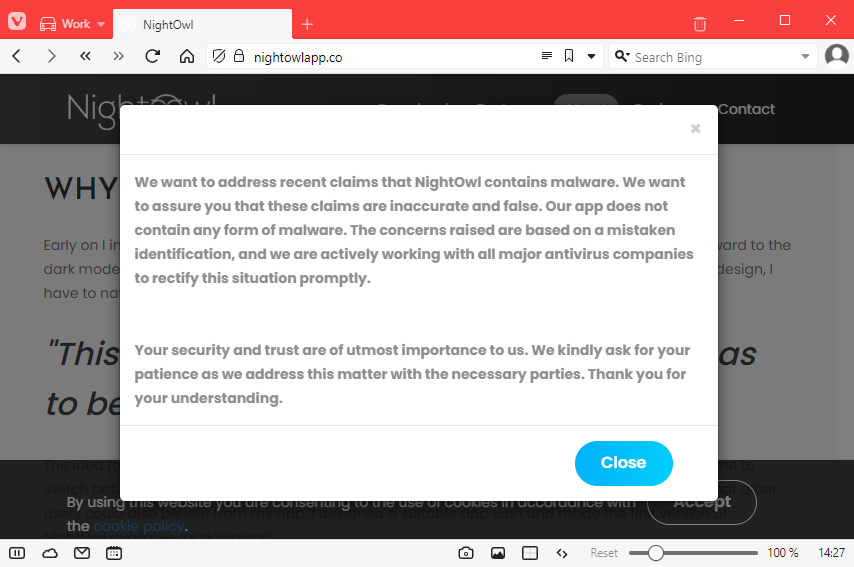
NightOwl: A formally legitimate macOS application named NightOwl has been observed enrolling its users in a residential proxy botnet, according to research published by macOS security firm Intego and web developer Taylor Robinson. Neither Intego nor Robinson spotted the app relaying any malicious traffic, but this was enough for Apple to revoke its signing certificate and prevent it from being launched on macOS systems. The malicious behavior was spotted months after the app's developer sold it to a new company. In a message posted on its website, the app's new owner said the app was mistakenly identified as malware and is now working with antivirus companies to correct the situation.
"Robinson also notes that NightOwl contains code related to a service called Pawns (or Pawns.app), which supposedly pays users up to 20 cents per gigabyte for sharing their network bandwidth. Again, this seems to imply that some third party could theoretically leverage NightOwl users' Internet connections as proxies to send DoS or click fraud traffic."
Sponsor Section
This is a section where we typically feature one of our sponsor's products. This time, we're gonna feature a tip on how to use Thinkst's canaries to spot "canary text files" being opened from the terminal, a typical giveaway of threat actor activity.
APTs and cyber-espionage
APT-C-35 (DoNoT): Qihoo 360 has a report on Indian group APT-C-35 (aka the DoNoT Team) and its recent campaigns against Bangladesh and Sri Lanka, a campaign that took place between June 2022 to February 2023.
Chinese APT targets gambling sector: Security firm SentinelOne says it has observed a Chinese APT group launch a new wave of attacks against organizations active in the Southeast Asian gambling sector. Clues from SentinelOne's investigation have led the company to believe the group is associated with a state-sponsored operation Secureworks tracks as BRONZE STARLIGHT and ESET as ChattyGoblin [PDF].
"Our analysis has led us to historical artifacts that represent points of convergence between BRONZE STARLIGHT and other China-based actors, which showcases the complexity of a Chinese threat ecosystem composed of closely affiliated groups."
APT-K-47 (Mysterious Elephant): Chinese security firm KNOW Chuangyu has published an English version of their report claiming that the APT-K-47 (Mysterious Elephant) overlaps with the older Bitter APT group.
Vulnerabilities, security research, and bug bounty
New Citrix exploitation: CISA has confirmed that a new vulnerability in the Citrix ShareFile appliance is currently being exploited in the wild. Tracked as CVE-2023-24489, the vulnerability was discovered by security firm Assetnote and patched in June. CISA's confirmation of active attacks comes after security firm GreyNoise warned of "a significant spike in attacker activity" targeting this vulnerability a week after Assetnote publicly disclosed the bug.
Ivanti Avalanche vulnerability: Tenable has discovered an unauth stack buffer overflow bug in Ivanti's Avalanche MDM solution.
OpenNMS Horizon vulnerability: Synopsys researchers have found a vulnerability in the OpenNMS Horizon network monitoring platform.
MSFT Exchange security updates: Microsoft has re-released its Patch Tuesday security updates for Microsoft Exchange email servers after the original patches were crashing servers.
Cisco security updates: Cisco has released 17 security updates for various products. Only high and medium-rated bugs in the updates this week. No critical-rated bugs this time.
Chrome security updates: Google is now releasing security updates for Chrome on a weekly basis, every Tuesday. Here's the first batch containing 26 security fixes.
Jenkins plugin security updates: The Jenkins project has published a security advisory warning about vulnerabilities in 13 plugins.
OpenSSL Downfall impact: The OpenSSL team says that the Downfall vulnerability in Intel CPUs can be used to steal OpenSSL cryptographic material from the CPU, and as such, the vulnerability poses a "particularly high" risk to its library. On the other hand, the team doesn't seem to be particularly worried about the Inception vulnerability in AMD CPUs.
Fake Airplane Mode exploit: Jamf researchers have developed a novel exploit for iOS 16 that creates a fake Airplane Mode to hide malicious activity from infected users.
New DllNotificationInection process injection technique: Security firm Shorsec has developed a new process injection technique they are naming DllNotificationInection. The new "threadless" technique uses DLL Notification Callbacks in local and remote processes to load a malicious DLL file in legitimate processes. A PoC is on GitHub.
SpamChannel: Security researcher Marcello Salvati has discovered a vulnerability in the platform of automated email delivery platform MailChannels. Named SpamChannel, the attack allows an attacker to spoof any of the two million domains hosted on the platform and send out spam in their names. After Salvati presented his findings at the DEFCON security conference, MailChannels released some fixes to prevent the researcher's PoC from working. Salvati described the fix as addressing a symptom and instead recommended that all MailChannels users enable a feature named Domain Lockdown to prevent their domains from being spoofed and abused. [Additional coverage in Axios]
Moonlighter hacking contest: Three security teams have successfully hacked a US Air Force satellite at this year's edition of the DEFCON security conference. Named Moonlighter, the satellite was deployed in space in June specifically for this year's Hack-A-Sat competition. The winning team was an Italian group consisting of researchers from five Italian security firms. The group won $50,000. A Polish team came second, and a joint British-American team came third. They were the only teams from a total of five that successfully hacked the Moonlighter satellite. [Additional coverage in Space.com]
Infosec industry
Naomi Wu: A report from Jackie Singh documents how Chinese authorities have harassed and silenced Naomi Wu, a well-known hardware expert and privacy advocate. It's unclear what led Chinese authorities to take a harsher approach. Singh lays out several reasons, such as Wu's LGBTQ activism, her relationship with an Uyghur man, and Wu tweeting about a vulnerability in Tencent's Sogou app—covered days later in a CitizenLab report.
"Her account concluded with an unsettling revelation about the risk she would face if she were to continue tweeting: having already received two 'strikes' from the authorities, a third could mean a years-long prison sentence."
New tool—NoFilter: DeepInstinct's Ron Ben Yizhak has released a tool named NoFilter that abuses the Windows Filtering Platform for privilege escalation.
New tool—LogLicker: Cloud security firm Permiso has open-sourced a tool named LogLicker, designed for anonymizing (and anonymizing) logs when sending them over the wire.
New tool—Bomshell: DevSecOps company Chainguard has open-sourced Bomshell, a query language for SBOM files.
COVID-19 cases at DEFCON: There are more than 175 cases of DEFCON participants who tested positive for COVID-19 after attending the conference.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at why 'juice jacking' is a forever fear even though it's not a real-world threat.




