Risky Biz News: Open-source projects plagued by rash of fake or disputed CVEs
In other news: Russia makes RuStore app mandatory on all smartphones; China sneaks trojaned Signal and Telegram apps on the Google and Samsung app stores; and PyPI malware linked to North Korea.
This newsletter is brought to you by Stairwell. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
An anonymous researcher has sifted through the changelogs of open-source projects and obtained CVE identifiers for old bugs that experts say may not be security flaws.
All the fake CVEs were obtained on August 22nd, and all were filed for open-source projects.
According to a list compiled by Chainguard at RiskyBusiness' request, 138 CVEs were filed in projects such as cURL, PostgreSQL, Python, the Netwide Assembler, ImageMagick, and many smaller libraries.
All the CVEs were obtained without any interaction or confirmation from the project maintainers that they represented an actual security issue.
Chainguard CEO and co-founder Dan Lorenc believes the CVEs might have been filed using an automated tool or some sort of AI system.
"Can you see the pattern? All of these CVEs link out to bug or patch entries on repos or mailing lists, all were filed without maintainer interaction, and all contain an obvious vulnerable sounding string in the commit message or issue," Lorenc said in a LinkedIn post this week.
"Something like 'use after free,' 'denial of service,' or 'buffer overflow.' Someone is clearly scraping old issues and commits to file these in an automated fashion, without ever getting maintainers involved."
The CVEs have caused quite a controversy. Major open-source projects like cURL and PostgreSQL have already disputed the CVEs and called them non-vulnerabilities.
Ryan Cribelar, an R&D Engineer at Nucleus Security, called the vulnerabilities "bogus" and the entire thing a "distraction."
"The fact that this bug [the PostgreSQL issue] went through the entirety of the CVE process without someone stopping and being like, 'Is this actually a CVE?' feels so odd to me," Cribelar told RiskyBusiness.
"We can not be wasting time on stuff like this as it only serves as a distraction to the very few and overworked folks who do actually do manual triage on CVEs."
And if filing the bug reports and obtaining the CVEs wasn't bad enough, the same overworked maintainers of the affected open-source projects now have to go through the long-winded process of disputing or retracting the CVEs. cURL creator Daniel Stenberg was definitely not happy about the CVE being issued behind his team's back and now being put in the situation of having to explain and deal with MITRE about why this bug from way back in 2020 is not a security issue.
"Yes, some have been disputed. Disputed CVEs are just that, they mark it as disputed and then leave it there," Lorenc told us.
"Most scanners don't know about the disputed status, so it's of limited value. This means many maintainers don't bother to even dispute it. The NVD has a retraction process, but I've never seen it actually used."
Both Lorenc and Cribelar argued that using a vulnerability triage or management platform and not taking the NVD CVE database at face value would help avoid having to deal with non-issues like this. Both work for companies that sell such products, but they spotted the fake CVEs, so they also have a point.
Breaches, hacks, and security incidents
DDoS attacks on independent Hungarian news media: The International Press Institute says that independent Hungarian news websites that have been critical of the local government have been hit by a wave of DDoS attacks. Most of the attacks have hit outlets such as Telex, HVG, 444.hu, Magyar Hang, and Népszava, all critical of the Orban regime.
PlayCyberGames breach: More than 3.6 million user records have been stolen and dumped from Thailand-based gaming VPN provider PlayCyberGames. The breach allegedly took place in August 2023.
Phishing victims: CERT-Poland has shared the data of more than 68,000 users who fell victim to phishing attacks with data breach index website Have I Been Pwned. The site is now notifying all affected users.
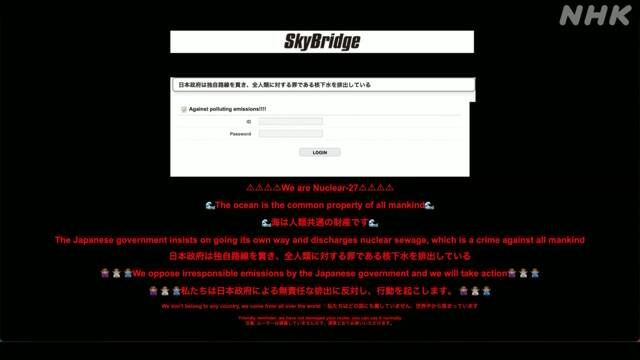
Routers hacked in Japan: Hacktivists have hacked routers across Japan and defaced their login screens with a message of protest against the Japanese government. The message opposed the government's decision to release treated water from the Fukushima nuclear plant into the Pacific Ocean last week. According to reports in local media, roughly 1,500 routers have been affected by the hacks, and all are Seiko SkyBridge and SkySpider models. Several hacktivist groups announced their intentions to attack Japanese organizations last month after the government announced it received approval from the UN to release the Fukushima water into the ocean. It's unclear which one of these carried out the operation.
General tech and privacy
OpenSSH gets keystroke timing attack protection: OpenSSH has received protection against keystroke timing attacks, a type of on-the-wire attack that can infer keystrokes typed over an SSH session. The new feature works by adding fake keystrokes to SSH sessions. The fake keystrokes are added in between real keystrokes, but also for a random interval after a user has finished typing.
Sudo in Rust: The Sudo Linux utility has been rewritten in Rust. Sudo-rs, as it's named, is not included by default with Linux distros but can be installed manually.
AI and gaming toxicity: Activision says it will use new AI tech to combat toxicity in Call of Duty voice chats.
Twitter harassment: Rest of the World has published an article showing how the accounts of Chinese dissidents get flooded with spammy adult content every time they post something critical of the regime. Something similar happened last year when Chinese porn spam bots flooded the site in an attempt to mask news of anti-Covid protests in China.
Twitter to collect biometric data: Right-wing and state propaganda hell-hole Twitter will start to collect biometric and other sensitive data such as employment and education history about its users, per Bloomberg. [non-paywalled]
Government, politics, and policy
RuStore is now mandatory: The Russian government has ordered that all new smartphones and smart gadgets sold in Russia must include a version of the RuStore app. The RuStore is Russia's domestic app store and was created in May 2022 after Russia's invasion of Ukraine. The app is the Kremlin's attempt to create an alternative to the Play Store in order to control what apps can be installed on Russian smartphones. [Additional coverage in TASS]
France's cyberattack warning: France's cybersecurity agency ANSSI has published a security alert warning local companies that upcoming major sporting events held in France may be the targets of foreign hackers seeking to disrupt games. This includes the Rugby World Cup this fall and the Paris Olympic Games next year. Officials have warned event service providers, subcontractors, and sponsors to be on the lookout for cyber espionage and destructive attacks. France's warning comes after Microsoft issued a similar one last month.
New NZ cybersecurity agency: CERT NZ has joined with the National Cyber Security Centre (NCSC) in the first step in creating a unified operational cyber security agency in New Zealand. The unification of CERT teams with cybersecurity agencies in one major organization has been a trend in recent years, with similar actions taking place in countries such as Ukraine, Romania, and the Netherlands.
Japan upgrades cyber police: Japanese government officials say they plan to upgrade their cyber police forces from a small unit to its own self-standing department. The unit was set up in April 2022. and its primary role is to fight against cybercrime and cyberattacks targeting Japan.[Additional coverage in The Japan Times]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Chris St. Myers, Threat Intelligence Lead at Stairwell, on how the company Inception platform can be used for finding old or new threats that sometimes may go unnoticed.

Cybercrime and threat intel
Nigerian scammer sentenced: A UK-Nigerian citizen has been sentenced to 90 months in prison for his participation in an inheritance fraud scheme. Two of his co-conspirators also received 82 and 87 months in prison as well.
"According to court documents, Iheanyichukwu Jonathan Abraham, 44, was part of a group of fraudsters that sent personalized letters to elderly victims in the United States, falsely claiming that the sender was a representative of a bank in Spain and that the recipient was entitled to receive a multi-million-dollar inheritance left for the recipient by a family member who had died years before in Portugal. Victims were told that before they could receive their purported inheritance, they were required to send money for delivery fees and taxes and were instructed to make other payments. Victims sent money to the defendants through a complex web of U.S.-based former victims. Abraham and his co-conspirators also convinced former victims to receive money from new victims and then forward the fraud proceeds to others."
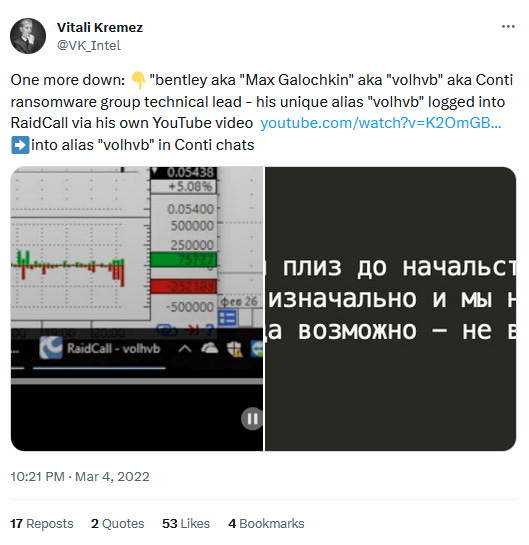
Trickbot member dox: Wired has published an exposé on Bentley, a Russian national named Maksim Sergeevich Galochkin, who leads a software development team inside the Trickbot cybercrime group. Galochkin's mid-tier management role in the Trickbot gang was exposed in the spring of 2022 after internal chats were leaked on social media as a package known as the "Trickbot Leaks." The late Vitali Kremez was the first to identify Galochkin as Bentley. Nisos, which helped Wired with its article, has also published a report showcasing that Trickbot was working with the Russian FSB intelligence agency in some sort of capacity.
Classiscam expansion: The Classiscam cybercrime group has made at least $64.5 million from running a Scam-as-a-Service platform. The platform allows criminals to create listings for fake products on online marketplaces across the globe. Users interested in buying the products are redirected to phishing pages where their financial details are collected by the gang. Group-IB says the group started operating in 2019 and primarily targeted Russia. It expanded to other countries in 2021, and its userbase has since exploded from 40 to more than 38,000 registered users today.
Greatness PhaaS: Outpost24 looks at the Greatness Phishing-as-a-Service platform, previously covered by Talos here.
Hacking forum contests: Sophos has a look at offensive research contests organized on hacking forums in recent years.
DUCKPORT group: Security firm WithSecure has discovered a new threat actor named DUCKPORT focused on infecting users with malware in order to hijack accounts that have access to Facebook's advertising and business platforms. WithSecure says the group is based in Vietnam and appears to have spun out of a group named DUCKTAIL. Despite similarities in their modus operandi and malware, WithSecure says the groups operate separately.
Smishing Triad: A Chinese-speaking cybercrime group known as the Smishing Triad has been spamming US citizens via iMessage. The group uses messages about package deliveries to lure users to phishing sites and collect their personal and financial details. The campaign has been going on since February this year and has collected data from at least 108,000 victims. Besides the US, the group has also carried out similar campaigns targeting users in the UK, Indonesia, Italy, and Poland. Resecurity says the group is also selling access to their phishing kit but that the kit is backdoored, meaning that any data collected by their customers is also sent to the Smishing Triad group.
Malware technical reports
Qakbot vaccine: Security firm Huntress says it secretly developed a vaccine that it has used since December 2022 to prevent infections on its customers' devices. The vaccine worked by creating a file specific to Windows Sandbox environments, tricking Qakbot to stop its own execution. Huntress disclosed the existence of the vaccine after law enforcement seized Qakbot servers and removed the malware from infected systems.
Qakbot uninstaller: Secureworks has analyzed the Qakbot uninstaller module the FBI used to remove the Qakbot malware from infected hosts.
npm malware: Checkmarx looks at a malware campaign that has been active on the npm portal since 2021. This is the same campaign that Phylum spotted last month and tried to impersonate packages from cryptocurrency companies CryptoRocket and Binarium. Just like Phylum, Checkmarx says the malware was designed to steal a victim's source code and dev environment secrets.
Brute Ratel C4: Cyber Geeks have a deep dive into Brute Ratel C4, an adversary emulation framework that's giving Cobalt Strike a run for its money among cybercrime groups.
SapphireStealer: Cisco Talos says that the open-source SapphireStealer malware is seeing increased adoption in cybercrime operations. First released in December 2022, the malware has been forked and improved by several groups, extending it to support additional data exfiltration mechanisms and leading to the creation of several variants.
HiddenBee and Rhadamanthys connections: Check Point researchers have found multiple similarities between the code and design of the HiddenBee cryptominer and the Rhadamanthys stealers. Check Point believes the newer infostealer was developed by the same person who developed the older HiddenBee code.
"The similarity is apparent at many levels: custom executable formats, the use of similar virtual filesystems, identical paths to some of the components, reused functions, similar use of steganography, use of LUA scripts, and overall analogous design."
BlackShadow ransomware: Russian security firm FACCT has an analysis of BlackShadow, a ransomware strain used in attacks against Russian orgs. FACCT says the entity behind this ransomware is also the likely creator of other ransomware strains, such as Proxima and Cylance.
Shadow ransomware attribution: The same FACCT says it has linked the Shadow ransomware to the Twelve hacktivist group. Shadow, just like BlackShadow, is another ransomware strain used exclusively against Russian companies.
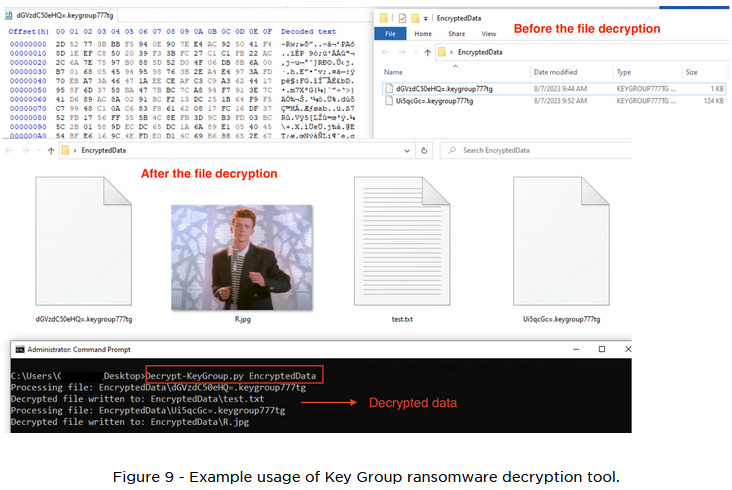
Key Group ransomware decrypter: EclecticIQ has released a free decrypter for the Key Group ransomware, allowing victims to recover their files without paying the attackers. The decrypter exploits multiple cryptographic mistakes in the gang's ransomware to decrypt ransomed files. The group is also known as KEYGROUP777 and has been active since January this year.
Sponsor Section
Stairwell's Mike Wiacek demonstrates Stairwell's file analysis and threat detection platform to Risky Business host Patrick Gray. Stairwell helps you monitor and analyze every executable file in your organization, automatically collecting crucial intelligence and providing your security team with in-depth visibility and detections.
APTs and cyber-espionage
Andariel: AhnLab researchers have published a report on Andariel's latest campaigns and operations. The report covers malware like NukeSped variant Volgmer, Andardoor, AndarLoader, DuarianBeacon, TigerRAT, Black RAT, Goat RAT, and the Troy reverse shell. That's quite the arsenal.
Lazarus PyPI supply chain attack: North Korea's Lazarus Group has planted malicious Python libraries on the official PyPI repository. The libraries imitated popular open-source tools for VMWare and cryptocurrency-related projects. According to security firm ReversingLabs, the campaign has been active for more than a month since the end of July. This marks the first known incident of North Korean hackers planting malware on PyPI after they uploaded malicious libraries on the npm portal earlier this year.
UAC-0057: Ukraine's CERT team has published details on another UAC-0057 (GhostWriter) campaign targeting Ukrainian organizations with Cobalt Strike beacons and the PicassoLoader malware.
Gamaredon: Ukraine's National Coordination Center for Cybersecurity (NCCC) has published a report on the recent activities of the Gamaredon APT group, which Ukrainian officials previously linked to the FSB office in Sevastopol. According to the NCCC, the group is now targeting Ukrainian government targets with the aim of finding and stealing military secrets.
Sandworm's Infamous Chisel: Cybersecurity agencies from the Five Eyes countries have published a joint security advisory exposing Infamous Chisel, a malware toolkit used by Russia's Sandworm military hacking unit. Officials say the new malware was used to target Android devices used by the Ukrainian military. The report most likely relates to malware that was discovered by Ukraine's Security Service that was targeting Android tablets used by the Ukrainian military.
Maui disinformation campaigns: RecordedFuture has observed Russian and Chinese disinformation groups use the Maui wildfires to advance anti-US propaganda. Both groups have pushed campaigns claiming the US prioritizes military spending in Ukraine and Taiwan over the well-being of its own citizens. Other campaigns have also pushed the idea that the US government itself caused the fires by testing "weather or energy weapons."
Empire Dragon disinformation: RecordedFuture researchers say that a Chinese disinformation network they've been tracking as Empire Dragon has slowly shifted its focus from internal Chinese matters to anti-US propaganda and has also started adopting similar narratives propagated by Russian disinformation campaigns. RecordedFuture says the 10 campaigns they analyzed from the group intersect with activity Mandiant tracks as Spamouflage Dragon and Graphika as DRAGONBRIDGE.
"Despite its efforts, Empire Dragon has struggled to generate organic engagement with its narratives, attributed to factors such as poor content quality, machine-translated text, and sporadic content amplification. However, improvements in multilingual large language models and image generation models are anticipated to enhance the network's ability to overcome these challenges in the future."
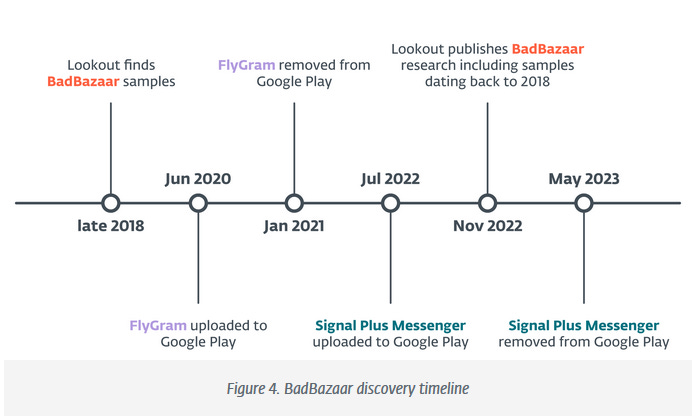
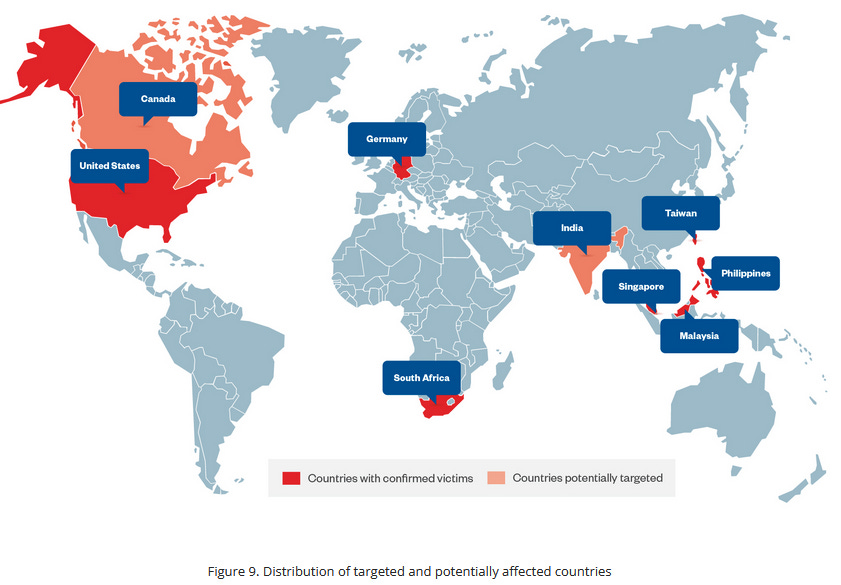
GREF (APT15): A Chinese cyber-espionage group known as GREF (APT15 or Vixen Panda) has planted trojaned versions of the Signal and Telegram apps on the official Google and Samsung app stores. The two apps contained functional versions of the two apps and a copy of the BadBazaar spyware. ESET says the trojaned Telegram app was advertised in a Uyghur Telegram group and that evidence suggests it was installed by more than 14,000 users. The GREF group has a long history of targeting China's Uyghur and Turkic ethnic minorities.
Earth Estries: Trend Micro has discovered a new APT group named Earth Entries that has engaged in cyber-espionage activities against government agencies and the tech sector. The group has been active since 2020, and its primary malware is a multi-functional backdoor named HemiGate. Earth Entries tactics and techniques suggest the group is focused on stealth and avoiding detection for as long as possible. Trend Micro says the group's activity overlaps with what ESET calls FamousSparrow.
Vulnerabilities, security research, and bug bounty
Apple SRDP: Apple has opened admissions for this year's iPhone Security Research Device Program (SRDP). This is a program where security researchers can apply for a custom-configured iPhone where security features are disabled. Apple has been providing these devices to researchers for the past years to allow them to find vulnerabilities in core operating system features that would normally be protected in the standard OS. Apple says security researchers have found 130 vulnerabilities in iOS since the program launched in 2019. The company says it awarded multiple $500,000 awards for bug reports received via the program.
Notepad++ vulnerabilities: Four buffer overflow vulnerabilities have been found in the Notepad++ text editor. No patches are available.
WP plugin vulnerability: Patchstack researchers have identified a vulnerability (CVE-2023-40004) shared by several plugins that are part of the All-in-One WP Migration toolkit. The vulnerabilities impact the OneDrive, Box, Dropbox, and Google Drive migration plugins and can allow unauthenticated threat actors access to sensitive data.
Starlink firmware: Quarkslab has looked into the firmware that runs on Starlink user terminals.
VMWare security updates: VMWare has released security updates to fix issues in its Aria Operations and Tools products.
Infosec industry
Pwn2Own Automotive: Trend Micro's Zero-Day Initiative has announced a new Pwn2Own hacking contest that will be focused on hacking automotive technologies. Called Pwn2Own Automotive, the contest will take place during the Automotive World auto show in Tokyo next January. Contestants will be able to hack smart car operating systems, infotainment systems, and EV charging stations or attempt to take over a Tesla car. The contest's prize pool is more than $1 million.
New tool—EternalHush Framework: A Russian security researcher has released EternalHush Framework, a new C&C framework.
New tool—NosyMonkey: Security firm Anvil Secure has open-sourced a tool named NosyMonkey to perform DLL/API hooking.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at how asset inventory tools aren't a substitute for knowing what a business values.




