Risky Biz News: New Google exploit lets threat actors revive expired cookies
In other news: Operation Triangulation abused secret iPhone hardware feature; Orbit Bridge hacked for $82 million; and Microsoft disables AppInstaller protocol.
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The RiskyBiz crew behind our newsletters and podcasts is on hiatus between December 8 and January 8 for the winter holidays, but we put out this weekly edition with some of the past week's biggest infosec stories.
Happy holidays!
Breaches, hacks, and security incidents
Albanian cyberattacks: Albania's cybersecurity agency (AKCESK) says that major cyberattacks have targeted the networks of the country's parliament and its largest telco, Albania ONE. The attacks took place on December 25. The agency did not make a formal attribution.
SnappFood leak: An Iranian hacking group named IR Leaks has leaked the data of more than 20 million users of SnappFood, Iran's largest food delivery app. The same group also dumped databases from several other Iranian companies. [Additional coverage in Iran International]
Evotor cyberattack: The IT Army of Ukraine has taken credit for a cyberattack that crippled the operations of Evotor, a Russian company that makes and operates online cash registers used across Russia.
BELTA attack: Belarusian hacktivist group the Cyber Partisans have hacked and wiped the network of the Belarusian Telegraph Agency (BELTA), the country's state-owned news agency.
EPS ransomware attack: Serbian public energy company EPS and the Serbian government are staying silent about a ransomware attack that hit the organization around the Christmas holiday. [Additional coverage in BalkanInsight]
EasyPark cyberattack: EasyPark, the largest parking app operator in Europe, has disclosed a security breach.
Ohio Lottery cyberattack: The Ohio Lottery has suffered a cybersecurity attack, which is preventing some winners from claiming their prizes. [Additional coverage in WCPO]
Downfall incident: A developer for Downfall, a game mod for the Slay the Spire indie game, had his account hacked, allowing hackers to insert malware in the Steam mod. The incident took place on Christmas and deployed an infostealer to user systems.
Telcoin cyber-heist: A threat actor stole $1.2 million worth of tokens from the Telcoin project. [Additional coverage in CoinDesk]
Levana cyber-heist: Hackers stole $1.1 million worth of assets from the Levana Protocol. [Additional coverage in Rekt News]
Orbit Bridge cyber-heist: On the last day of 2023, a hacker stole almost $82 million worth of crypto-assets from cross-chain exchange Orbit Bridge. Happy New Year!!!
General tech and privacy
Microsoft disables ms-appinstaller protocol: Microsoft has disabled the ms-appinstaller protocol in Windows by default after several threat actors began abusing it to install malware on user devices throughout November 2023. The company says that groups like Storm-0569, Storm-1113, Storm-1674, and Sangria Tempest have been spotted abusing the protocol.
Google settles lawsuit: Google has settled the $5 billion lawsuit in which it was accused of tracking users even when they were in Chrome's private mode. The terms of the settlement were not disclosed, but they will most likely become public when the settlement is presented to the court for approval. [Additional coverage in the BBC]
Privacy Sandbox Protected Audience API: Lukasz Olejnik has published a privacy analysis of the Privacy Sandbox Protected Audience API, the new user tracking technology that is currently shipping with Chrome.
Google Groups ends Usenet support: Google is ending support for its Usenet integration on Google Groups on February 22, 2024. The company says it took the decision to combat spam.
Steam drops old Windows versions: With the new year, Steam has dropped support for Windows 7 and Windows 8, citing security reasons.
Cars and the 4th Amendment: Car data is apparently not safeguarded by 4th Amendment protections, meaning cops can access it without a warrant. This is possible thanks to a loophole/exception in US law since the Prohibition era. [Additional coverage in The Record]
XCast settlement: The US DOJ and FTC have settled with XCast Labs, a company that provided infrastructure for spammy telemarketers. Under the proposed court order, XCast Labs will be required to implement a screening process and end its relationships with firms that are not complying with telemarketing-related laws.
Keybase outage: Encrypted instant messaging service Keybase has had a major outage after one of its certificates expired after 10 years and nobody noticed in time. Since the start of the year, the vendor has been shipping software updates to rotate the certificate across its apps.
WiFi 7: The WiFi 7 standard is expected to arrive later this year in 2024. IEEE Spectrum has a breakdown of all the new changes. The main new feature is multi-link (MLO) support.
Apple-Corellium legal battle: Apple and cybersecurity company Corellium have settled their four-year-old legal battle. The terms of the settlement were not disclosed. Apple sued Corellium in 2019 over its iOS sandboxing technology. [Additional coverage in Forbes]
Mozilla outrage: Lots of Firefox and privacy supporters are mad because even if Firefox lost a giant chunk of browser share this year, the Mozilla CEO netted a giant $7 million salary last year.
Let's Encrypt stats: In its end-of-year report, Let's Encrypt says its certificates are now used on more than 360 million websites, up 40 million from last year.
Government, politics, and policy
South Korea sanctions North Korean spy chief: Seoul authorities have
sanctioned eight North Korean officials for their role in the country's intercontinental ballistic missile program. Among the sanctioned individuals is Ri Chang Ho, the head of the country's intelligence agency. South Korean officials say Ri has helped fund the program through the RGB's illicit cyber operations. [Additional coverage in The Straits Times]
Moldova sets up cybersecurity agency: With help from Estonian officials, Moldova has set up a national cybersecurity agency.
Risky Business Podcasts
In this podcast, Patrick Grey and Tom Uren talk about whether election interference will take place in the Taiwanese, US, and Russian elections that are all taking place in 2024. They also look at a ChatGPT-powered online harassment campaign.
Cybercrime and threat intel
Ransomware gang arrest: Chinese police detained two individuals from Hohhot who were involved in ransomware attacks against Chinese organizations. Officials say the group used ChatGPT to optimize the code of their ransomware, which they used to encrypt corporate servers and demand $20,000 in ransom. [Additional coverage in Global Times]
Orgon sentencing: A Colombian judge has sentenced Andres Felipe Cardoso Alvarez to three years and five months in prison. Alvarez was known as Orgon, a member of the Anonymous Colombia hacking group. As part of the group, he launched attacks against a large number of government organizations.
Cyber Toufan wiping spree: The data-wiping spree started by the Cyber Toufan group at the end of November is still going strong. The group has now wiped more than 100 organizations, with the vast majority being based in Israel. Around 40% of the victims were hit after the group compromised their MSP.
Iranian phishing/wiping campaign: Israel's CERT team says Iranian hackers have continued their phishing campaign where they pose as F5 and lure victims into running a data wiper on their equipment. The campaign has now been running for more than a month.
Spyware in India: Amnesty International has confirmed that the Pegasus spyware was used in attacks against Indian journalists. The confirmation comes after Apple notified victims about the attack at the start of December 2023 but did not say what kind of malware was used. Amnesty says the Pegasus spyware was deployed on infected devices between August and October 2023. In the meantime, WaPo reports that Indian government officials have pressured Apple to change the tone of its warnings in a way that doesn't incriminate them.
New ransomware strain: Symantec researchers have spotted a new ransomware strain named TISAK in the wild.
Crypto drainers in 2023: Crypto-draining phishing kits have been used to steal more than $300 million worth of crypto assets from more than 320,000 victims throughout last year.
Redline dominates 2023: The top most analyzed malware on the ANY.RUN platform in 2023 was the Redline infostealer, the same as last year.
Mac malware of 2023: Pattrick Wardle has published a review of last year's most common macOS malware strains.
Malware technical reports
Marble Framework: In an interesting experiment, malware analysts from HackerHouse have used AI/ML tools to reconstruct the (incomplete) source code of the Marble Framework, a malware toolkit initially shared in the CIA Vault7 leaks.
Rhysida ransomware: Logpoint researchers have published a technical report on the Rhysida ransomware, a RaaS that began operations in May 2023.
8base ransomware: Fortinet looks at the rencent activity of the 8base ransomware gang.
Black Basta decrypter: Tobias Mueller of SRLabs has developed a free decrypter for the Black Basta ransomware. The decrypter was released at the 37C3 conference last week. It allows victims to recover files locked by the group between November 2022 and December 2023. The Black Basta gang has fixed the bug exploited by the decrypter.
MetaStealer: eSentire researcher RussianPanda has published part two of an analysis of MetaStealer. Part one is here. The infostealer launched in March 2022 and incorporates code from Redline Stealer, as its creator candidly admitted back then. The malware is different from the MetaStealer that SentinelOne discovered last year, which is written in Go and targets macOS exclusively.
Pure Logs Stealer: The same researcher also has an analysis of Pure Logs Stealer, a more recent infostealer, which RussianPanda claims it "fails to impress."

Sponsor Section
In this product demo, GreyNoise founder and CEO Andrew Norris demonstrates how people use the GreyNoise sensor network.
APTs, cyber-espionage, and info-ops
Kimsuky: AhnLab has published an analysis of recent Kimsuky operations that employed the group's macOS malware AppleSeed.
Kremlin spams overseas Ukrainians: Ukraine's GUR intelligence service says Ukrainians living abroad have received a wave of spam messages urging them to help Russia expel "American Satanists" from Ukraine's "primarily Russian land." The incident comes as Ukrainian officials warned that the Kremlin is preparing new disinformation efforts across the EU, something French officials also warned about.
APT28: Ukraine's CERT team has spotted Russia's APT28 hacking group launching new spear-phishing operations against Ukrainian targets between December 15 and 25. The final payload was malware strains such as MASEPIE, OCEANMAP, and STEELHOOK.
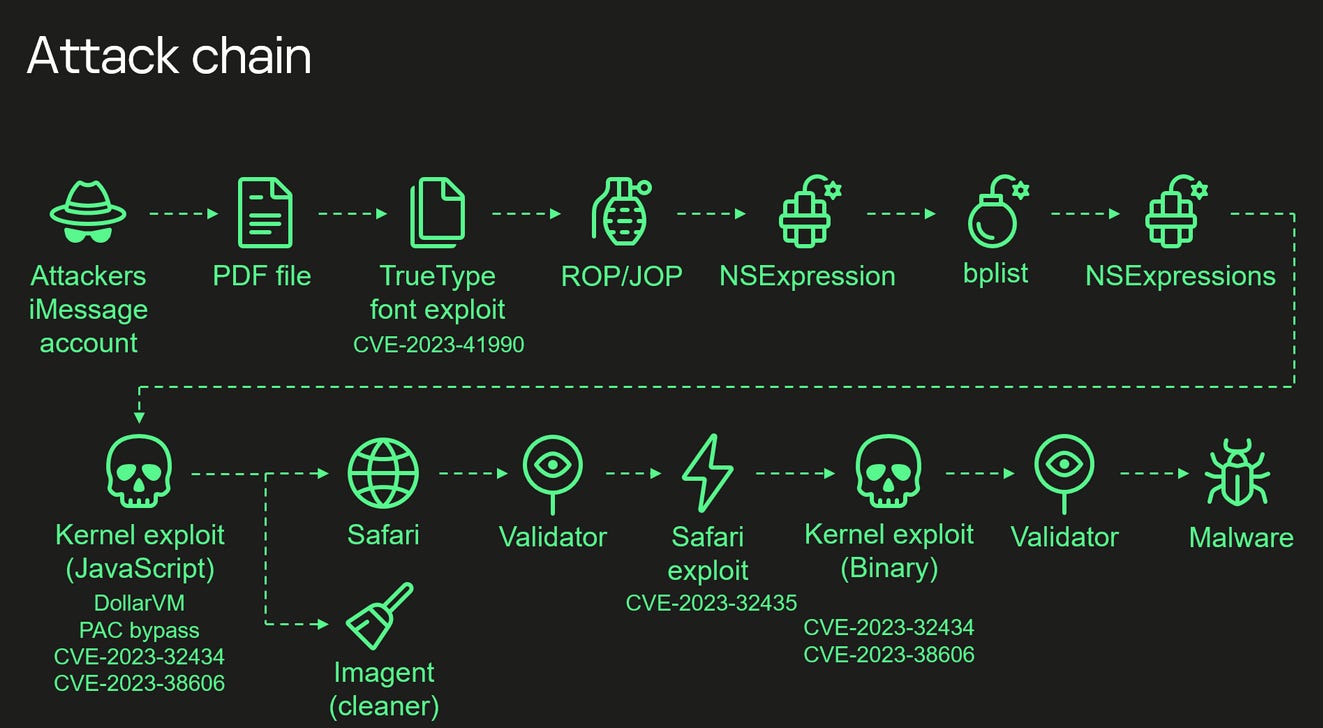
Operation Triangulation: Kaspersky researchers say they found evidence that the Operation Triangulation spyware attacks abused a secret hardware feature in iOS devices to bypass hardware-based security protections (CVE-2023-38606). The operation targeted Russian government officials, foreign diplomats working in Russia, and Kaspersky employees. Russia's FSB intelligence service linked the attack to the NSA and claimed Apple cooperated with the American spy agency.
Vulnerabilities, security research, and bug bounty
New Google exploit: Several malware developers have found a new exploit that allows them to revive expired Google cookies and access accounts even after users change their passwords. The new technique has been used in the wild since October, according to Hudson Rock, CloudSEK, and independent threat intel analysts. Infostealers seen using it include LummaStealer, Rhadamanthys, Risepro, Meduza, and Stealc Stealer. The exploit allegedly resides in an undocumented Google Oauth endpoint named MultiLogin.
Juniper security updates: Juniper has released a security update to patch 18 vulnerabilities in its JSA (Juniper Secure Analytics) series.
D-Link unpatched vulnerabilities: Tenable has found a vulnerability in the D-Link D-View network management utility that can be used to leak device passwords. The issue is still unpatched.
Spreadsheet::ParseExcel patches: A security update has been released for Spreadsheet::ParseExcel, the Perl module that got exploited as part of the recent attacks on Barracuda ESG appliances. Apparently, an exploit for this Perl module has been available in the wild for months.
Apache OfBiz auth bypass: Sonicwall researchers have found an authentication bypass in Apache OfBiz servers (CVE-2023-51467).
GKE Fluent Bit vulnerability: Palo Alto Networks has published a write-up on an EoP vulnerability they found in the Fluent Bit logging agent of the Google Kubernetes Engine, patched earlier in December.
PandoraFMS vulnerabilities: NCC Group has found 18 vulnerabilities in PandoraFMS, an enterprise-scale network monitoring and management application.
Ethereum ABI vulnerability: Trail of Bits has found a parsing vulnerability in libraries that support Ethereum ABI binary parsing functionality.
"At the time of writing, the bug is fixed only in the Python library. All other libraries decided on full disclosure through GitHub issues."
WinSxS hijacking: Security Joes have found a new DLL hijacking technique that exploits the WinSxS folder.
DsmSvc analysis: Germany's BSI cybersecurity agency has published a security analysis of the Windows 10 Device Setup Manager Service (DsmSvc) driver management utility.
Tesla Elon mode: Three security researchers used a voltage drop glitch to jailbreak a Tesla car's autopilot and gain root access to the car and autopilot system. With this access, the group activated a previously unknown feature named Elon Mode, which gave them full control over the car.
Infosec industry
37C3 videos: Talks from the 37th Chaos Communication Congress (37C3) security conference, which took place at the end of December in Germany, are available on YouTube.
New tool—SecButler: Security firm GroundSec has released SecButler, a collection of tools for pen-testers and bug bounty hunters.
New tool—Domainim: Russian software developer pptx704 has released Domainim, a domain reconnaissance tool for organizational network scanning.
New tool—EDRSilencer: Security researcher Chris Au has released EDRSilencer, a tool that silences EDR solutions and prevents them from reporting security events to their servers.
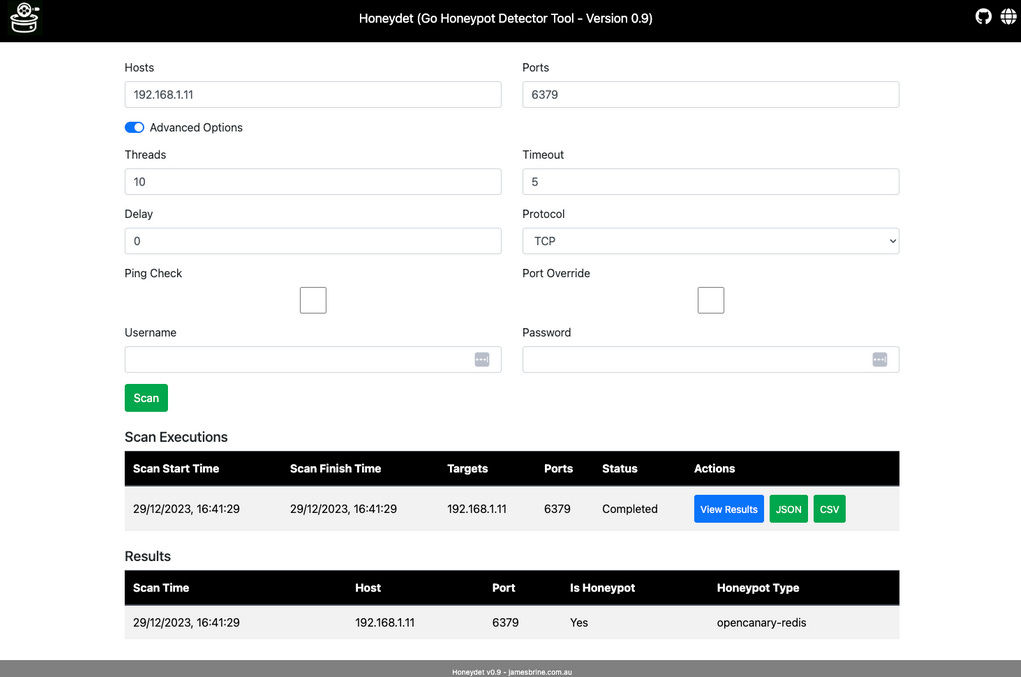
New tool—Honeydet: Security researcher James Brine has open-sourced Honeydet, a tool to detect online honeypots.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about recent hints that the Ukrainian government has figured out how to make use of the IT Army.




