Risky Biz News: New CVSSv4 vulnerability scoring system is out
In other news: Mozi botnet goes down; Boeing confirms ransomware attack; and Microsoft goes through a second Trustworthy Computing moment.
This newsletter is brought to you by vulnerability management and analysis platform Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
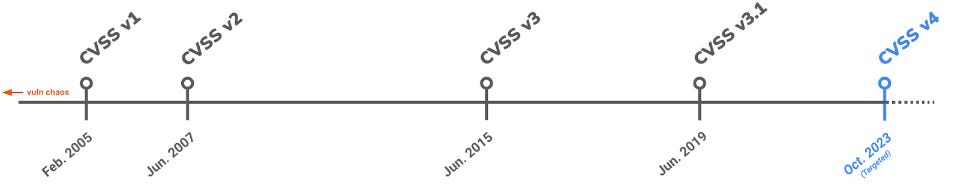
The Forum of Incident Response and Security Teams (FIRST) has officially released a new version of the Common Vulnerability Scoring System (CVSS), the most widely used standard for rating the severity of software vulnerabilities using a score from 1 to 10.
With this week's release, the standard has now reached version 4.0—also more commonly known as CVSSv4.
Work on this new version began years ago and comes after a period of public comments and feedback and after a first CVSSv4 draft was presented in June at the FIRSTcon 2023 security conference.
There are several new additions in CVSSv4 that expand CVSSv3.1, the standard that has been in use for the past several years. The four most important ones are below:
- New CVSS scoring metrics have been added to improve the granularity of CVSS scores. This was done because in previous versions of the standard, you'd end up with different types of vulnerabilities bunched around the same score that didn't particularly reflect each one's severity. More scoring metrics in CVSSv4 means a better spread across the whole scale.
- There are now ICS, OT, and IoT-specific scoring metrics. This includes scoring metrics such as "Safety," "Automatable," or "Recovery," which will let critical infrastructure operators know if a security flaw just looks bad on paper or if it's actually exploitable and dangerous to their networks.
- New scoring metrics such as "Value Density," "Vulnerability Response Effort," and "Provider Urgency" have been added to help responders evaluate and prioritize vulnerabilities. The last two are particularly interesting since they allow vendors to tell customers that a vulnerability needs to be patched ASAP. This is a capability that was not present in the current CVSS.
- The "Temporal" metrics group from CVSSv3 has been replaced with a new group called "Threat Metrics." Just like the previous one, this group deals with exploitability and proof-of-concept availability but is way easier and clearer.
Because of all the changes, the new CVSSv4 also means a new way to score vulnerabilities, and the way the scores are now calculated has also changed. While in previous versions, most CVSS scores were the "base score," in CVSSv4, we now have four types of scores, depending on which groups of "metrics" apply to a vulnerability. The four new CVSS score types are now the ones below. Use the image below to understand how they are calculated.
- CVSS-B: CVSS Base Score
- CVSS-BT: CVSS Base + Threat Score
- CVSS-BE: CVSS Base + Environmental Score
- CVSS-BTE: CVSS Base + Threat + Environmental Score
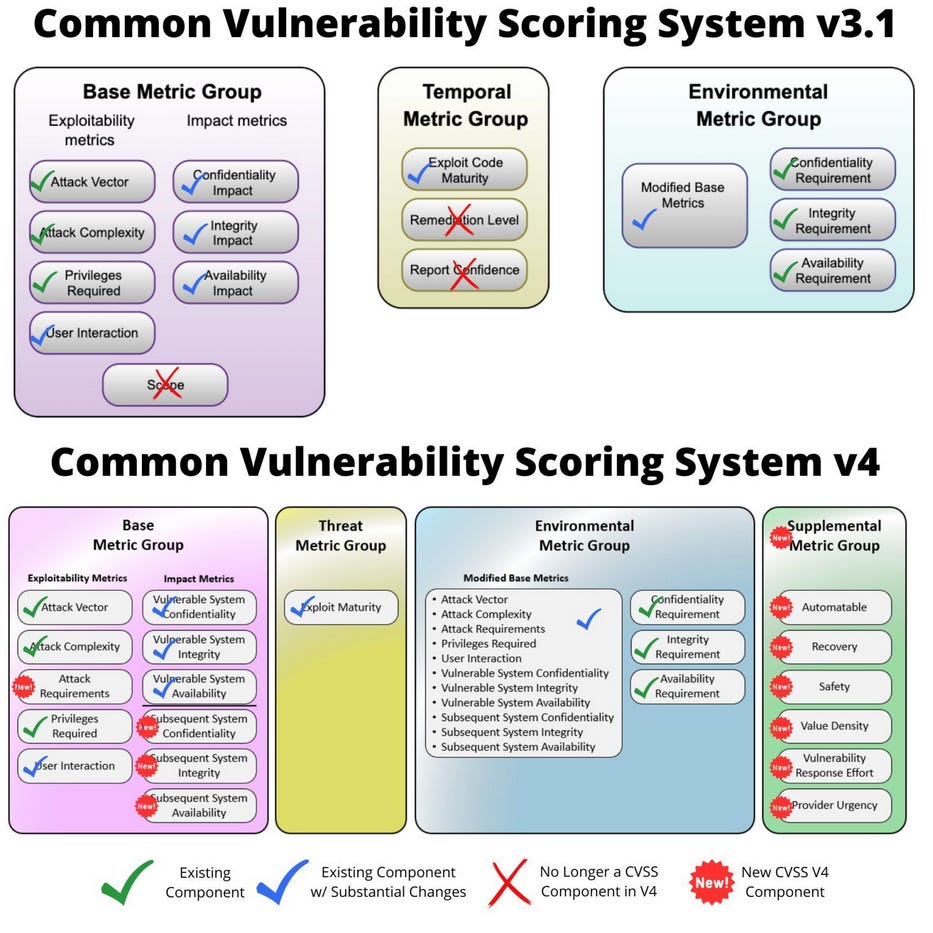
As with most previous editions, CVSSv4 also comes with its own score calculator. You can probably see the differences between CVSSv3.1 and CVSSv4 just by looking at the metrics groups.
If that's not enough, BASE4 Security, Rapid7, Qualys, and Tenable published deep dives into the new standard earlier this year that will help you navigate all the changes. Nucleus Security (by coincidence, this week's sponsor) also published a YouTube video going over the new CVSSv4 changes back in June. Probably the best description of the new CVSSv4 standard comes from BASE4's write-up, which describes it as a "pursuit of precision."
Breaches, hacks, and security incidents
Advarra hack: A threat actor claims to have hacked and exfiltrated data from Advarra, a major provider of IT services to the US healthcare sector. The attack took place on October 25. The threat actor says they plan to leak the data after the company has refused to negotiate or pay a ransom. The attack has been claimed by one of the AlphV ransomware affiliates, and the company's name was listed on the AlphV dark web leak site on November 1. [Additional coverage in DataBreaches.net]
Boeing ransomware attack: Airplane maker and defense contractor Boeing has confirmed that a ransomware attack has impacted its parts and distribution business. The LockBit ransomware gang first listed Boeing's name on its dark web leak site on October 27 before the company admitted to the incident. The gang claimed it accessed Boeing's network using an unnamed zero-day. [Additional coverage in DarkReading]
Onyx Protocol crypto-heist: A threat actor has stolen $2.1 million worth of crypto assets from DeFi platform Onyx Protocol. The attacker used an illiquidity market exploit to manipulate interest rates and steal funds from the platform's wallets. According to blockchain security firm SlowMist, the same exploit was also used to steal $7.4 million from the now-defunct Hundred Finance platform back in April.
General tech and privacy
Microsoft Secure Future Initiative: Microsoft President Brad Smith has made a public pledge that Microsoft will improve the security of its cloud products. Named the Secure Future Initiative, the company's commitment comes after hackers have constantly exploited Microsoft products for attacks on government and private sector entities. Smith says the initiative will focus on three areas—the use of AI for cyber defense, fundamental changes to software engineering, and advocacy for stronger international norms. The new initiative wants to mimic a similar pledge made by Bill Gates in 2002. Named Trustworthy Computing, that initiative led to significant changes to Microsoft's security posture and the creation of what we now know as Patch Tuesday.
Microsoft Secure Future Initiative (the engineering part): As part of Microsoft's latest SFI effort, Charlie Bell, Executive Vice President of Microsoft Security, has published a blog post describing what the changes to the company's software engineering practices will entail. The effort will primarily focus on improving the company's cloud services and will center around 1) transforming software development, 2) implementing new identity protections, and 3) a faster response to cloud vulnerability reports. Microsoft will also change its signing key infrastructure, which was compromised earlier this year by a group of Chinese state-sponsored hackers.
YouTube's ad-blocking crusade: Google has confirmed that it launched a "global effort" to crack down on the use of ad blockers on YouTube. The company seems to be set in its way to bombard users with ads and prevent people with ad blockers from accessing its site. According to previous reporting, the company plans to force users to either view ads or subscribe to YouTube Premium. Those who use an ad blocker will have access to the site restricted.
New ING TLD: Google has launched a new top-level domain named ING. Because of the way the TLD was set up, all new domains must use HTTPS.
EU bans Meta's data processing: The European Data Protection Board has banned social media company Meta from processing and using the data of EU users for targeted advertising. The decision applies to all Meta sites, such as Facebook, Instagram, WhatsApp, and adjacent advertising services. The EDPB says Meta has failed to obtain the explicit consent of EU users to use their data for targeted ads. The EDPB imposed an EU-wide ban at the request of the Norwegian data protection agency, which has been investigating the company's abuses for months.
eIDAS open letter: More than 300 cybersecurity experts, researchers, and NGOs have signed an open letter asking the European Union to drop its new eIDAS (Electronic Identification, Authentication and Trust Services) regulations. Experts say new articles will force web browsers to automatically trust certificate authorities and cryptographic keys mandated by EU governments. Experts say these changes open the door to mass surveillance and the interception of encrypted web traffic across the EU. The latest modifications were adopted behind closed-door meetings and added to the eIDAS text without public debate. Signatories include Mozilla, the EFF, the Linux Foundation, Cloudflare, Fastly, and multiple VPN providers.
GoGuardian privacy invasion: An EFF investigation has found that the GoGuardian student surveillance software regularly flags innocous websites as harmful content. The GoGuardian software is used by thousands of schools to monitor the internet traffic of more than 27 millions K-12 students across the US. The EFF says GoGuardian is plagued by false positives that often flag benign educational or informative websites as harmful and sexual explicit and then flag non-existing issues to the student's schools and parents, creating unneeded stress for the monitored children.
HBO troll accounts: A Rolling Stone investigation has found that HBO executives used networks of Twitter trolls to harass TV critics who gave poor reviews of their shows.
Avast SDK bug: Avast says a bug in its SDK is to blame for Google apps being flagged as malware on Huawei and other Chinese phones.
Chrome 119: Google has released version 119 of its Chrome browser. See here for security patches and webdev-related changes. Major changes include that all cookies now have an expiration date capped at 400 days. This applies to current but has also been applied retroactively to old cookies as well. On mobile, Chrome has ended support for Android Nougat (7.0). WebSQL has also been disabled and will be removed in v123. Chrome can now also sync Tab Groups.
Government, politics, and policy
China cracks down on social media stars: Seven of China's top social media platforms have jointly announced that users with more than 500,000 followers will have to list their real names in their profiles. The move comes to deter social media stars from criticizing the government or meddling in global or national affairs. It also comes after China's Central Cyberspace Affairs Commission ordered online platforms to crack down on accounts spreading rumors or fake news. Accounts that will not reveal their real name will be demonetized and restricted. The seven platforms that notified users of the new rule include Baidu, Sina Weibo, WeChat, Douyin (TikTok), Kuaishou, Bilibili, and Xiaohongshu. [Additional coverage in GlobalTimes]
CRI summit: The White House has published the results of the third meeting of the International Counter Ransomware Initiative (CRI).
The Bletchley Declaration: Twenty-eight countries and the European Union have signed the Bletchley Declaration, a document agreeing to cooperate on the safe development of AI technologies.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Patrick Garrity, VP of Marketing and security researcher at Nucleus Security, on the rise and evolution of vulnerability threat intel and how CISA KEV's new ransomware section will be a game changer.
Cybercrime and threat intel
Two Russian hackers detained: The Russian FSB has detained two men this week on accusations of carrying out cyberattacks against Russian IT systems on behalf of Ukraine. Officials detained a student from Tomsk and a 36-year-old from Belovo, Kemerovo. The FSB says the two suspects joined Ukraine's "cyber troops," received orders from Ukraine's security services, and attacked Russian critical infrastructure. The two have been charged with high treason and face prison sentences from 12 years to life in prison.
Israel-Hamas hacktivism: The number of hacktivist groups involved in the Israel-Hamas conflict has now reached 137, surpassing the 128 groups involved in the Russian-Ukrainian conflict. According to threat intelligence analyst CyberKnow, most of the groups are from Asia and have sided with the Hamas/Palestinian side. Most of the groups are carrying out DDoS attacks and website defacements. Some groups have been involved in hack-and-leak operations, but many of the hacks have proven to be fake.
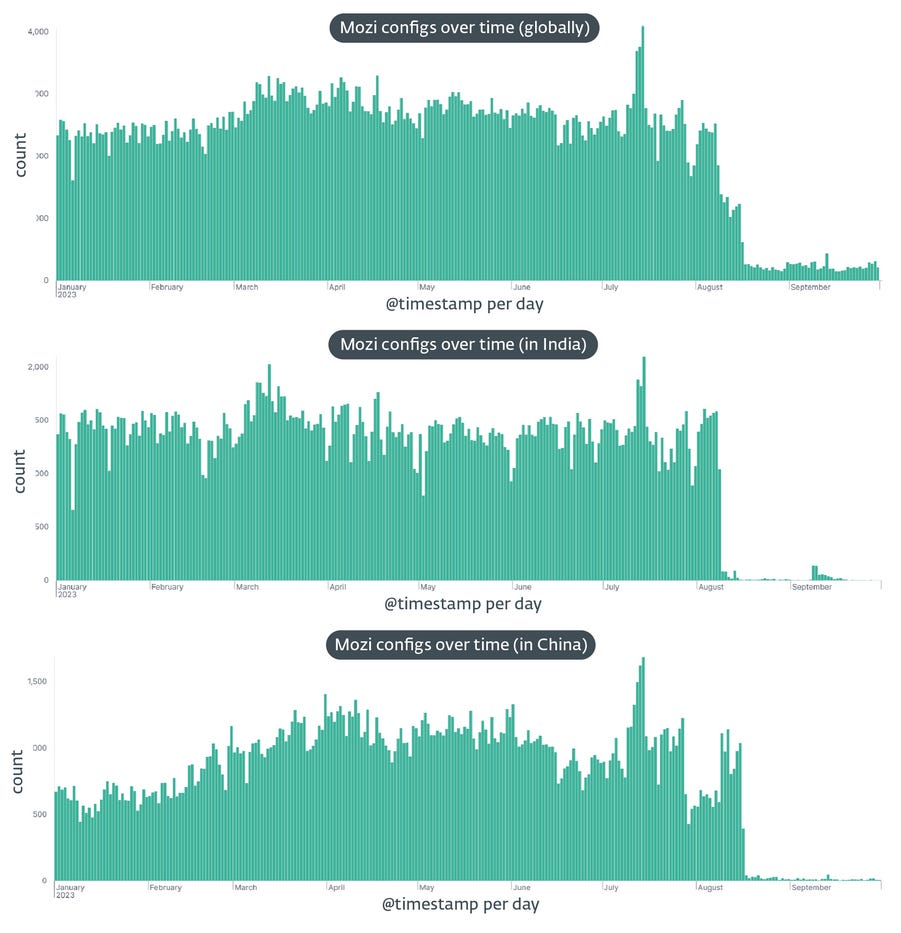
Mozi botnet goes down: The Mozi botnet has finally gone down for good after a mysterious entity removed its malware from infected IoT devices across the globe. The removal took place at the end of August, with infected hosts being first removed from systems in India and then from China. Security firm ESET says the Mozi takedown was executed with a special killswitch component that was signed with the malware's original private key. The company couldn't say if the killswitch was activated by the Mozi botnet creators or by Chinese law enforcement, which detained some of the Mozi authors in June 2021. First spotted in November 2019, the botnet infected more than 1.5 million devices across its lifetime, peaking at 160,000 infected systems in September 2020.
Wiki-Slack Attack: eSentire researchers have discovered that you can use Wikipedia links to redirect Slack users to malicious sites in what they're calling the Wiki-Slack Attack.
Malware technical reports
MoneyMessage ransomware: Sophos has some details on the new-ish MoneyMessage, a ransomware gang targeting corporate networks.
SparkRAT: OALABS has published IOCs for SparkRAT, a Go-based remote access trojan spotted being abused by a Chinese threat actor.
DarkGate: Netskope researchers have spotted a new version of the DarkGate malware loader.
Blister: NCC Group has a deep dive into recent versions of the Blister malware loader, previously linked to Evil Corp.
BlackCat/AlphV: NCC Group has published IOCs from recent BlackCat/AlphV intrusions.
Sponsor Demo
Nucleus Security's COO Scott Kuffer shows Risky Business podcast host Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information, and then allows vulnerability management teams to do things like assign responsibility for certain types of bugs to the correct people.
APTs and cyber-espionage
Kimsuky's FastViewer: S2W researchers have analyzed a new version of FastViewer, an Android malware strain previously used by the Kimsuky North Korean APT.
MuddyWater: DeepInstinct and Group-IB are tracking a MuddyWater spear-phishing campaign targeting Israeli entities.
Mysterious WhatsApp spy mod: Kaspersky has looked at a WhatsApp mod that contained a version of the CanesSpy spyware. The mod was being distributed to Arabic-speaking users via Telegram channels. Unclear what threat actor this was, but it is most likely espionage and intelligence collection related.
Vulnerabilities, security research, and bug bounty
SketchUp vulnerabilities: Zscaler researchers have discovered 117 vulnerabilities across the Microsoft 365 application suite related to support for 3D file formats. Zscaler says all the bugs originate from a library that supports the SketchUp (SKP) 3D format that Microsoft added in June 2022. Because of the large number of bug reports it received from Zscaler and other researchers, Microsoft temporarily disabled support for the SKP format across all Microsoft 365 apps in June this year.
Thorn SFTP vulnerabilities: Praetorian researchers have found a vulnerability (CVE-2023-47174) in Thorn SFTP Gateway Admin portals. The bug is a Java deserialization issue that can be used to execute malicious code on unpatched file-transfer systems.
WhatsApp vulnerabilities: Meta's security team has patched two vulnerabilities in the WhatsApp service. Tracked as CVE-2023-38537 and CVE-2023-38538, the two are the first security issues patched in WhatsApp this year. Both were discovered by the company's security teams.
Signal PQXDH security audit: A team of security experts has analyzed Signal's new post-quantum protocol, PQXDH.
CitrixBleed exploitation: Google's Mandiant division says it is now tracking four different threat actors exploiting the CitrixBleed vulnerability (CVE-2023-4966) to compromise corporate and government systems. At least two of these are ransomware gangs. The first attacks targeting the vulnerability were recorded at the end of August when the bug was still an unpatched zero-day. They expanded last week after free exploits were posted online.
Apache ActiveMQ exploitation: Security firms Rapid7, Censys, and the Shadowserver Foundation are reporting exploitation of a recently patched Apache ActiveMQ vulnerability tracked as CVE-2023-46604. The vulnerability was patched at the end of October, and attacks began after proof-of-concept exploit code was published online. The vulnerability is a pre-auth RCE with a severity of 10/10. According to Censys and Shadowserver, there are between 7,000 and 8,000 ActiveMQ servers currently connected to the internet. Rapid7 says some of the hacked servers were encrypted with a version of HelloKitty, a ransomware family that was leaked online in October.
ApatchMe vulnerability: Tenable researchers say that Apache Airflow instances on Amazon and Google’s cloud services are running a vulnerable version of the software. According to researchers, the servers are vulnerable to a stored XSS bug tracked as CVE-2023-29247 and also known as ApatchMe.
Vulnerable kernel drivers: VMWare Carbon Black researchers have identified 34 vulnerable kernel drivers that can be used to elevate the access of non-admin users. VMWare says it reported the issues to vendors whose drivers had valid signatures at the time of discovery, but only two fixed the reported issues.
Cisco security updates: Cisco has released or updated 25 security advisories for various products, including an advisory for two recently exploited zero-days. There is also a security update for a critical vulnerability the company tracks as CVE-2023-20048, a command injection bug in Firepower firewalls.
Infosec industry
Group-IB US expansions: After finishing its exit from the Russian market, security firm Group-IB says it's preparing for a US expansion. In today's political context, allow me to be extremely skeptical about this one.
Splunk layoffs: Security firm Splunk has laid off approximately 7% of its workforce, representing around 550 of its 8,000 total staff. CEO Gary Steele says the layoffs are part of its agreement with Cisco, which agreed to buy Splunk for $28 billion. This is Splunk's second round of layoffs this year after it also fired 4% of its staff back in January.
Acquisition news: Proofpoint has entered into an agreement to buy cloud email security company Tessian.
"The agreement is expected to close in late 2023 to early 2024, subject to customary closing conditions and required regulatory approvals. "
New tool—Raven: Security firm Cycode Labs has open-sourced a tool named Raven that can perform massive scans on GitHub Actions CI/CD workflows and report the presence of vulnerabilities and other issues.
New tool—LdrLockLiberator: Security researcher Elliot Killick has open-sourced a tool named LdrLockLiberator that can unlock locked DLLs and perform DLL hijacks.
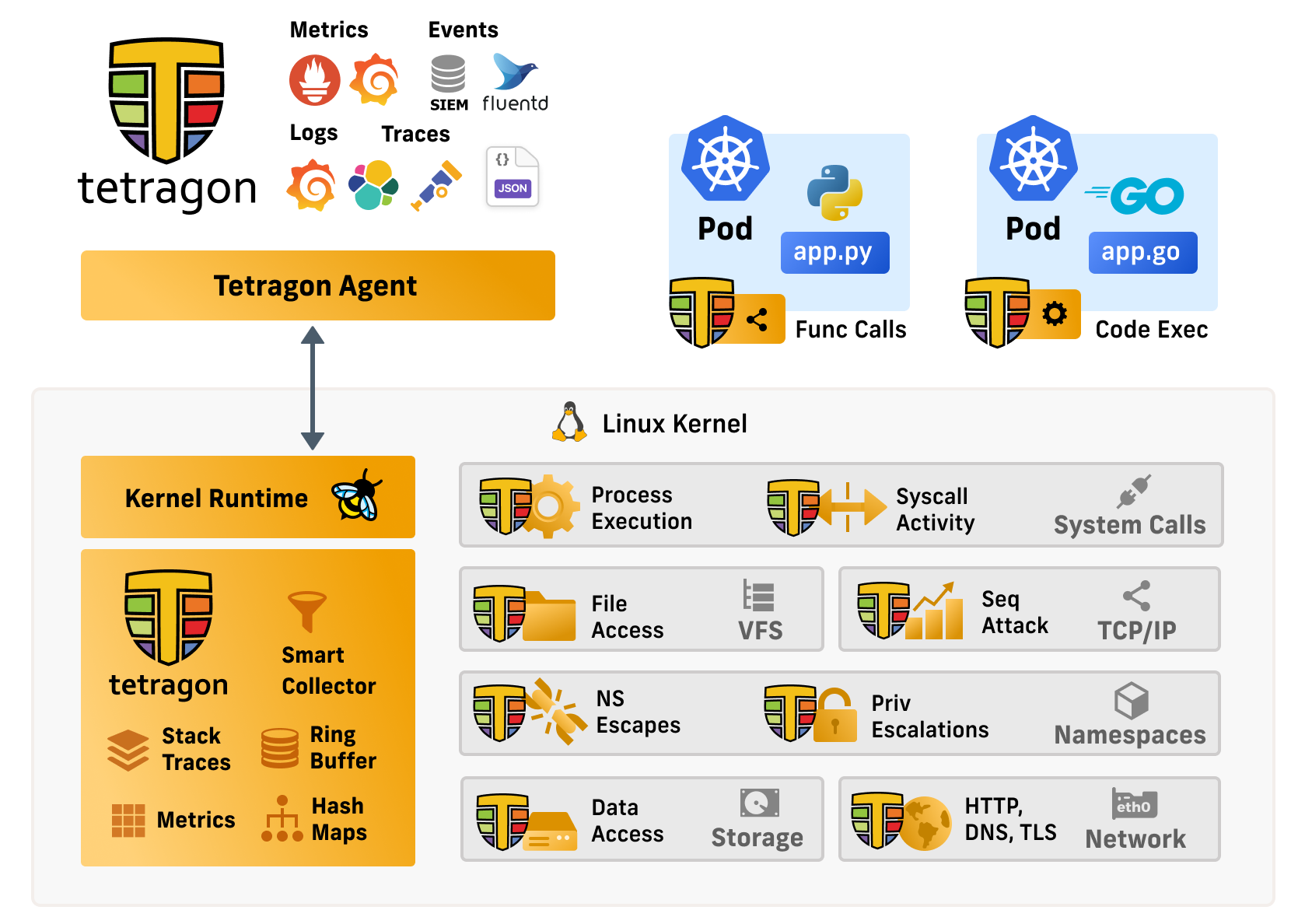
New tool—Tetragon: Cloud security firm Cilium has open-sourced Tetragon, an eBPF-based security solution for Kubernetes environments.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss what is really at stake when it comes to cyber security.




