Risky Biz News: Mysterious APT compromises Asian government's secure USBs
In other news: 30k+ Cisco devices compromised with IOS XE zero-day; Kansas courts down after suspected ransomware attack; and Sandworm hacks 11 Ukrainian telcos.
This newsletter is brought to you by application allow-listing software maker Airlock Digital. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
A mysterious APT group has compromised secure USB drives used by an Asian country's government to safely store and physically transfer data between sensitive government systems.
Spotted by Kaspersky, the attacks took place in early 2023. While the security firm has not attributed the operation to any particular APT group or state, the campaign is extremely likely to be Chinese in origin. Chinese APT groups—such as Camaro Dragon, Temp.Hex, UNC4191, Mustang Panda, and Troppic Trooper—have used USB drives as a way to distribute malware across the APAC region for the past several years, and some of these campaigns have been recently seen in Africa and Europe as well.
But while previous campaigns targeted your run-of-the-mill USB thumb drives, Kaspersky says this campaign targeted "a specific type of a secure USB drive" used by that country's government agencies.
Secure USB drives are also known as encrypted USBs and are typically used to store sensitive information in a separate partition. Everything on this partition is encrypted. The USB uses software stored in an unencrypted part of the USB device along with a user password to access the encrypted data.
Such devices are typically used by companies and government agencies to store extremely sensitive data and then physically transfer the USB drive to a secure location and plug it into an air-gapped network.
Kaspersky says the APT group crafted malware that would hide in the secure USB's software, working as a worm and loading itself on all computers the secure USB would be plugged into. A more technical explanation is below:
"The attack comprises sophisticated tools and techniques, including virtualization-based software obfuscation for malware components, low-level communication with the USB drive using direct SCSI commands, self-replication through connected secure USB drives to propagate to other air-gapped systems and injection of code into a legitimate access management program on the USB drive which acts as a loader for the malware on a new machine."
Attacks so far have been "extremely targeted," and Kaspersky says the APT made only a "limited number of victims." Which is extremely good for an intelligence collection operation targeting air-gapped systems. Not good is the part about getting caught.
Updated on October 19 to add that Kaspersky has named this APT as TetrisPhantom and plans to provide more details about the group at its upcoming SAS security conference.
Breaches, hacks, and security incidents
BlackHole crypto-heist: Hackers have stolen $1.2 million worth of funds from the BlackHole cryptocurrency project after they exploited a vulnerability in the token's smart contract.
Guatemala hacktivism: Hackers associating with the Anonymous collective have launched DDOS attacks against Guatemalan government websites. The hackers said their attacks are in support of the country's pro-democracy protests. Public rallies have been taking place in Guatemala since August when the country's president challenged the results of recent elections and has delayed the new president from taking office. [Additional coverage in the Associated Press]
Belgian govt DDOS attacks: Belgium's cybersecurity agency says several government websites were taken offline last Thursday following a series of DDOS attacks. Affected websites included the website of the Royal Palace, the Chancellery of the Prime Minister, and the Senate.
Colonial Pipeline denies second ransomware incident: US oil pipeline operator Colonial Pipeline has denied rumors that it got hit by ransomware for a second time. The company denied a claim made by the operators of the Ransomed.vc gang. This comes as no surprise, as the gang has made several unfounded claims about intrusions at several big-name companies over the past two weeks. [Additional coverage in The Record]
Ampersand ransomware attack: TV advertising company Ampersand has confirmed it dealt with a ransomware attack after the Black Basta crew claimed it breached the company earlier this year. [Additional coverage in The Record]
Kansas courts cyber incident: Court systems across Kansas have switched to using pen and paper in the aftermath of a cyberattack that took down some of its IT systems. Residents who have to pay court fees or file paperwork have been asked to visit courthouses in person or deliver documents via fax or mail. Kansas officials say that recovering from the attack will take at least two weeks, if not more. The incident is suspected to be another ransomware attack, with a similar incident hitting some Florida courts last week. [Additional coverage in the Wichita Eagle]
D-Link data breach: Taiwanese networking equipment maker D-Link has confirmed a security breach after some customer data was posted for sale on an underground hacking forum earlier this month. The company says the breach occurred after an employee fell victim to a phishing attack. D-Link says the attacker accessed an old 2015 management system where it extracted customer names and emails. The hacker claimed to have stolen "three million lines of customer information," but D-Link says that only 700 customers were impacted.
General tech and privacy
Tech layoffs: LinkedIn and StackOverflow have laid off employees this week. 700 at LinkedIn and 28% at StackOverflow.
WhatsApp adds passkeys: Meta's WhatsApp messaging platform has announced support for passkeys, following in the footsteps of Google, Apple, Amazon, and many other tech companies.
Non-consensual deepfake porn: There are now almost 250,000 videos of non-consensual deepfake porn. [Additional coverage in Wired/non-paywall]
Government, politics, and policy
New NCF commander: Air Vice-Marshal Tim Neal-Hopes has been appointed as Commander of the UK's National Cyber Force (NCF). Neal-Hopes becomes the agency's second commander. He succeeds James Babbage, who left the NCF for the UK's National Crime Agency earlier this year.
Secure by design guidance: CISA has updated its "Secure by Design" guidance that the agency first released back in April. The guidance has been updated with advice from seven new international partners, on top of the ten organizations who crafted the original document.
"[T]his joint guidance urges software manufacturers to take urgent steps necessary to ship products that are secure by design and revamp their design and development programs to permit only secure by design products to be shipped to customers."
Foreign intelligence guidance: The US National Counterintelligence and Security Center has published a guide to mitigating foreign intelligence threats to private organizations. The guide promotes basic concepts such as identifying critical assets, risk and vulnerability assessments, and mitigation planning. The guide [PDF] covers basic scenarios of dealing with possible foreign intelligence entities, such as insider threats, visitor vetting, foreign travel reporting, and more.
China's IPv6 legislation: China's government has passed new legislation mandating that all new wireless-capable devices support the newer IPv6 standard. The act also requires that telecom operators to support the protocol.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Airlock Digital founders Daniel Schell and David Cottingham about the recent Microsoft Digital Defense Report and the problem of properly securing PowerShell.
Cybercrime and threat intel
Navy IT manager sentenced: A judge has sentenced a former US Navy IT manager to five years and five months in prison for unlawfully gaining access to a computer database and selling the personal data of thousands of users on the dark web. Marquis Hooper used his Navy credentials to trick a company into gaining access to its database to perform background checks. US officials say Hooper used the access to collect data on 9,000 individuals that he sold on the dark web and earned $160,000. The stolen information was used to perform fraud, such as crafting fake IDs to withdraw money from bank accounts. Hooper also granted access to the account to his wife, who is scheduled for sentencing in November.
IDF data for sale: A threat actor claims to be in possession and is selling the personal data of Israeli military and intelligence agents on a Russian-speaking underground hacking forum. The data allegedly contains information on Israel Defense Forces and Israel Security Agency members. According to threat intel firm ZeroFox, the data is being sold for $15,000.
"The threat actor advertising the compromised data for sale instead of sharing it for free indicates that their incentive is unlikely ideological. The initial date of compromise for the advertised data is unclear; however, it is likely perceived as more valuable after the outbreak of hostilities between Israel and Hamas. This is further demonstrated in the price, which is above average for the amount of data advertised."
Discord abuse: Trellix examines how threat actors are abusing Discord for their operations, such as using it for C&C data collection, storing malware payloads, or social engineering.
Discord campaign: And speaking of Discord abuse, Trend Micro published a report on a threat using Discord to host and distribute the Lumma infostealer. Just like the Trellix report, Discord was used here for spamming targets via DMs, as a malware CDN, and as C&C.
CobaltStrike hunting: Cyphur Labs have published instructions on how security researchers can hunt for Cobalt Strike 4.9 C&C servers. v4.9 of Cobalt Strike got leaked on a Chinese hacking forum earlier this month, and its usage among threat actors is expected to rise in the coming weeks. So far, Cyphur analysts have identified at least two Cobalt Strike v4.9 servers.
Fake browser updates: Security firm Proofpoint has seen an increase in activity from threat actors that use fake browser updates to deliver malware. The most active groups include SocGolish, FakeSG (RogueRaticate), ZPHP (SmartApeSG), and ClearFake. Proofpoint says these threat actors plant web pages on hacked websites that promote an update for the user's browser. When users download and run the update, they also install malware on their systems. The technique has been used for more than a decade but is seeing a recent resurgence, being primarily used to distribute infostealers and sometimes ransomware.
Malware technical reports
Lumma Stealer: Intrinsec has a report on the Lumma Stealer.
XorDDoS: Palo Alto Networks takes a look at the recent campaigns delivering the XorDDoS malware to Linux systems.
"The XorDDoS Trojan spread around the world during July and August 2023. This threat infects Linux devices and transforms them into zombies for launching DDoS attacks. The attackers coordinate the botnet with C2 domains that they have abused before. However, they have recently relocated their C2 servers to new IP addresses from public hosting services."
BADBOX: Chinese security firm QiAnXin has independently confirmed a Human report on the PEACHPIT ad fraud botnet and the BADBOX threat actor. I was hoping for more info on this threat actor from beyond the GFW, but nothing of the sort for now.
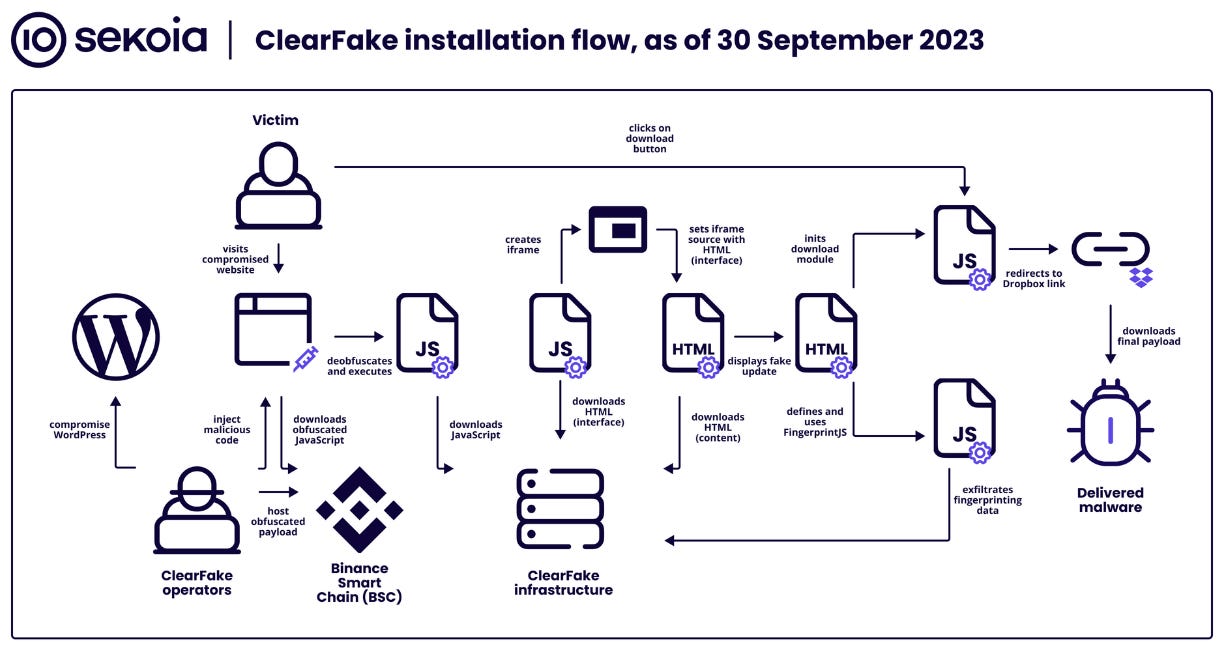
ClearFake: Sekoia researchers have published a technical analysis of ClearFake, a new malicious JavaScript framework deployed on hacked websites to deliver malware using drive-by downloads. This is the same JS framework that stores part of its malicious code inside smart contracts on the Binance blockchain, covered by Guardio and FINSIN over the past weeks. The new framework was first spotted in August and is currently installed on a few hundred sites.
"ClearFake is another 'fake updates' threat leveraging social engineering to trick the user into running a fake web browser update, as for SocGholish and FakeSG malware. By linking the 'fake updates' lure to the watering hole technique, ClearFake operators target a wide range of users and conduct effective, scalable malware distribution campaigns."
Sponsor Demo
Airlock Digital CEO David Cottingham shows Patrick Gray how Airlock's execution control and allowlisting solution works.
APTs and cyber-espionage
Confucius: Chinese security firm Anheng Hunting Labs has published a report on recent Confucius APT operations distributing the River Stealer.
Kimsuky: AhnLab looks at how the Kimsuky APT is using RDP across different campaigns as a way to access and control compromised environments and exfiltrate data.
BadRory: Kaspersky researchers have identified a new APT group named BadRory that has mounted two waves of spear-phishing attacks against Russian organizations. The campaigns took place in October 2022 and April 2023 and leveraged boobytrapped Office emails. Targets included government entities, military contractors, universities, and hospitals. Kaspersky classified the threat actor as "Russian-speaking."
HideBear: QiAnXin has published a report on Operation HideBear, a campaign from the RomCom group spreading a version of the MINEBRIDGE backdoor via spear-phishing emails.
UAC-0165 (Sandworm) telecom attacks: Russian cyber-espionage group Sandworm (UAC-0165) has breached the networks of 11 Ukrainian telecommunications providers. The intrusions took place between May and September this year. According to Ukraine's CERT team, Sandworm operators deployed backdoors (Poseidon, PoemGate) to harvest data and scripts that disrupted equipment, causing outages for telco customers. The Sandworm group has carried out multiple destructive attacks against Ukrainian networks since Russia's invasion of Ukraine, with the latest taking place in May when it hit a government organization.
Vulnerabilities, security research, and bug bounty
CISA, FBI warn of Atlassian widespread exploitation: CISA and the FBI have asked organizations to patch a recently disclosed Atlassian Confluence zero-day (CVE-2023-22515). The zero-day was used by a suspected Chinese APT (Storm-0062) in limited attacks since mid-September. The agencies say they expect the vulnerability to see widespread abuse due to its ease of exploitation and the availability of proof-of-concept code.
Cisco zero-day: A threat actor is exploiting a zero-day vulnerability in the Cisco IOS XE operating system. Tracked as CVE-2023-20198, the zero-day impacts the web UI, and allows a remote, unauthenticated attacker to create an account that has full access to the device. Cisco says its customer support teams discovered the attacks in late September while investigating customer complaints. The company says it's working on a patch and has asked customers to disable the HTTP Server feature on their IOS XE routers and switches. Security firm VulnCheck says it found thousands of Cisco systems that have been compromised and has released a free scanner to detect malicious implants. LeakIX has the number at more than 30,000. The zero-day has a severity rating of 10/10, and this is the second IOS XE zero-day that Cisco discovered over the past month (after CVE-2023-20109).
More Exim patches: The developers of the Exim email server have released a security update to patch three zero-days disclosed by the ZDI project. Exim developers released a patch for the first and most severe three zero-days at the start of the month. This latest update has now fixed all the six vulnerabilities initially disclosed by ZDI researchers. The Exim team has also deprecated all previous Exim server versions, and only the current 4.96.2 version is now formally supported.
Liferay vulnerabilities: The Liferay Portal CMS has released security updates to patch three persistent XSS vulnerabilities, including one with a severity score of 9.1/10 that can allow threat actors to hijack the entire website. Swiss security firm Pentagrid has a write-up of the bugs here.
CasaOS vulnerabilities: SonarSource researchers have found two vulnerabilities in CasaOS, an open-source OS used by some NAS makers. The two vulnerabilities allow attackers to bypass authentication and gain full access to the CasaOS dashboard. Patches for both bugs were released back in July.
Chrome RCE: GitHub's security team has an analysis of CVE-2023-4069, a type confusion to RCE vulnerability that was patched in the Chrome browser in July this year.
"Vulnerabilities like this are often the starting point for a "one-click" exploit, which compromises the victim's device when they visit a malicious website. What's more, renderer RCE in Chrome allows an attacker to compromise and execute arbitrary code in the Chrome renderer process."
More MFT vulnerabilities: Security firm Rapid7 has found six vulnerabilities in Titan MFT and Titan SFTP, two file-transfer solutions from South River Technologies. Although hard to exploit, the vulnerabilities can allow for full device takeover and have been patched by the vendor. These mark the third and fourth file-transfer solutions where Rapid7 found bugs after finding similar issues in the JSCAPE MFT and Fortra's Globalscape EFT Server. The company says it started looking into the security of file transfer appliances after several products had been widely exploited over the past two years.
Infosec industry
New tool—open-source-web-scanners: Security researcher Simon Bennetts is maintaining a list of open-source web security scanners.
New tool—CloudRecon: Gunnar Andrews and Jason Haddix have open-sourced CloudRecon, a collection of red-team tools for cloud reconnaissance. The tool was presented at this year's DEFCON conference.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss how changing circumstances change the risk/reward balance and change whether effects operations are worthwhile.




