Move Over NSO Group, There's a New Internet Villain
PLUS: Google's Russia Report is a Mixed Bag
Your weekly dose of Seriously Risky Business news is written by Tom Uren, edited by Patrick Gray with help from Catalin Cimpanu. It's supported by the Cyber Initiative at the Hewlett Foundation and founding corporate sponsor Proofpoint.
An undercover joint investigation by journalists from 30 different media outfits has exposed activities of an Israeli election interference-for-hire company.
The investigation centres around the activities of Tal Hanan, a 50-year-old former Israeli special forces operative, who goes by the pseudonym "Jorge", and his disinformation and interference business known as "Team Jorge". Three journalists posed as prospective clients interested in delaying an election in Africa to receive briefings about what Team Jorge could achieve.
In these pitch meetings Hanan and his associates make a whole host of claims, including that Team Jorge had worked on "33 presidential-level campaigns, 27 of which were successful". They also present a portfolio of different election interference capabilities.
One of these is a social media botnet known as Advanced Impact Media Solutions or AIMS, which can supposedly control 30,000 personas across a variety of platforms including Twitter, LinkedIn, Facebook, Telegram, Gmail, Instagram and YouTube. The Organized Crime and Corruption Reporting Project (OCCRP) reports Team Jorge appears to be using the SMS verification service SMSvpa.com to verify phone numbers and residential proxies to avoid detection by platforms.
Team Jorge makes extravagant claims about the impact of AIMS. Zohar Hanan, Tal's brother and the company's CEO, claimed during a demo that "one operator can have like 300 profiles, so within two hours the whole country will speak the message, the narrative I want."
It's a big claim, and we're sceptical.
A team of reporters from the Guardian, Le Monde and Der Spiegel were able to spider out from the AIMS personas revealed in the demo to get a broader view of the network's activity. Per the Guardian:
We then traced their activity across the internet, identifying their involvement in what appeared to be mostly commercial disputes in about 20 countries including the UK, US, Canada, Germany, Switzerland, Greece, Panama, Senegal, Mexico, Morocco, India, the United Arab Emirates, Zimbabwe, Belarus and Ecuador.
The analysis revealed a vast array of bot activity, with Aims’ fake social media profiles getting involved in a dispute in California over nuclear power; a #MeToo controversy in Canada; a campaign in France involving a Qatari UN official; and an election in Senegal.
30,000 personas sounds impressive but in the grand scheme of things is not a lot, especially when they flit from issue to issue in different countries and continents.
Regardless of its impact, AIMS isn't the only arrow in Team Jorge's quiver.
Tal Hanan also claimed to have run denial of service attacks against his clients' opponents. He said Team Jorge was responsible for the election day interference with a Nigerian political party's phone lines. The Vanguard reported "the calls… were so persistent that genuine calls could not come in while no calls could be made from the phone lines". We're not sure what sort of outcome they're shooting for by doing this on an election day, but sure, whatever.
More worryingly, however, Team Jorge also claims to be involved in hacking operations.
In a live demo to undercover journalists in July 2022, Tal Hanan demonstrated access to the Telegram account of Kenyan political advisor Dennis Itumbi. Itumbi was digital strategist advisor to William Ruto, a candidate in Kenya's presidential race at the time. Per the OCCRP:
Hanan showed proof that not only could he read Itumbi’s personal chats and files — including an internal polling survey related to the upcoming election — but that he could even pose as Itumbi by sending messages from his account. Hanan opened a recent conversation Itumbi had with a prominent Kenyan businessman and sent a text that read simply: "11".
This message was meaningless, designed only as a demonstration of his ability to control the account. But Team Jorge claimed to have sent falsified messages to military commanders and government ministers, all in an attempt to influence events and cause chaos for a high-level target.
Tal Hanan deleted the message, but for the sender only, not the receiver. Reporters were able to verify the Telegram hack by contacting the businessman and confirming that the mystery message had indeed been received.
In a surprising twist, Itumbi claims that he was aware of the Telegram compromise all along and even took advantage of it. Speaking to Nation, Itumbi said "I noticed increased activity on my Telegram account. The pattern showed that it was our competitors behind it. So we formed a few political groups and used them to mislead the hackers. It was clear in my mind that those interested in the information were working for our competitors."
Okay man, sure.
Ultimately, Team Jorge's efforts in this election weren't successful and Ruto is now Kenya's president.
The outfit's cavalier disregard for OPSEC is telling. For Team Jorge the next sale is the most important thing and it's all about appearing to be effective. Whether its dirty tricks work or not is a secondary consideration.
That's no reason to ignore them though. Team Jorge engages in a whole series of dirty tricks that — whether they actually work or not — are corrupting and corrosive for good governance and democracy.
And Team Jorge isn't the only shonky company in this space. Forbidden Stories has a series of reports on what it calls "Story Killers," companies that peddle manipulation in the form of disinformation, influence campaigns, harassment and burying information for hire.
They are all scourges.
Google's Russia Report is a Mixed Bag
Google has released a report on the impacts of the Russian invasion of Ukraine on the cyber threat environment.
The overall "vibe" of the report is that Russian government cyber actors get an A for effort, C for results. Despite engaging "in an aggressive, multi-pronged effort to gain a decisive wartime advantage in cyberspace", they've achieved "mixed results".
When it comes to destructive attacks, well, there's been a lot of them. Google's Mandiant "observed more destructive cyberattacks in Ukraine during the first four months of 2022 than in the previous eight years with attacks peaking around the start of the invasion".
Mandiant observed six unique wipers, some with multiple variants, but despite this flurry of activity the report is ambivalent about the actual impact. It says that while these attacks "did achieve significant widespread disruption initially in some Ukrainian networks, they were likely not as impactful as previous Russian cyberattacks in Ukraine".
The report notes that Russian groups were essentially forced to choose between destruction or intelligence collection:
To conduct the initial waves of destructive activity, Russian actors often employed accesses gained months before, which were often lost as the attack was remediated. The willingness to prioritise destructive attacks at the cost of persistent access indicates their importance to Russia’s overall strategy in Ukraine or the lack of operational preparation that could have sustained some persistent accesses while burning others during destructive activity.
Was destruction (and concomitant loss of access) the "best" approach for these Russian groups? Or would Russia's war effort have been better off if that hard-earned access had been used for intelligence collection? It's impossible for us to know, but this will be a live question for any military contemplating the use of destructive cyber operations.
We do have some quibbles with the report. Google says a group it calls FROZENBARENTS, aka Sandworm and attributed to the GRU, targeted the Turkish Bayraktar TB-2 drone manufacturer. The text implies some sort of causal connection when it says that "Russia subsequently disabled" the drones, but the linked articles don't cite any cyber operations. So… is this based on concrete information or is it just innuendo? We think the reasoning behind including this should be either spelt out explicitly or just removed from the report.
The information operations that the report describes, meanwhile, make sense. It finds that "Moscow leverages the full spectrum of information operations — from overt state-backed media to covert platforms and accounts — to shape public perception of the war". Russia has strategic goals and uses assets like state media, troll farms and fake news fronts to try and achieve them.
When it comes to ransomware, the report finds that although there wasn't an increase in reported ransomware against critical infrastructure in the US or NATO countries, there was an increase in reported attacks in Russia.
We've written several times about the use of cyber operations in warfare and it is great to add Google's contribution to our understanding of this issue.
What Does the CIA Do in Cyber?
Risky Business publisher (and editor of this newsletter) Patrick Gray interviewed the head of the CIA's Center for Cyber Intelligence (CCI), Andrew Boyd, to find out what the CIA is actually up to in the cyber domain. The conversation was published as a podcast today and the whole conversation is extremely relevant to the topics that we cover in this newsletter.
At the highest level the CCI is the owner of the "cyber threat mission", which includes both analysis and also hands-on cyber operations. CCI collects intelligence on cyber threats and also produces all-source analytic reports that might end up in the President's Daily Brief, for example. When it comes to operations Boyd describes CCI as having "one foot in the HUMINT camp and one foot in the technological enabling cyber camp". These operations might involve providing cyber support to HUMINT operations or HUMINT enabling of cyber operations.
The cyber threats CCI examines runs the gamut from cybercriminals to state actors. CCI was "brought into the mix" on the Colonial Pipeline ransomware attack, but although ransomware can be "quite chaotic", Boyd himself does not think its the nation's top cyber threat. He's more concerned about nation state threats and the possibility of being in an "active cyber war".
"That is where we focus a great deal of our countering energy."
When it comes to Russian cyber efforts in Ukraine, Boyd thinks there could be a number of reasons they haven't been more effective. These include the possibility that Ukrainian defences were battle-tested after years of prior attacks, that Russian groups cannot run operations at the "speed, intensity and control" required to be really effective, or that they may have not planned particularly well. Pleasingly for this newsletter, Boyd pointed to our analysis of the war in Ukraine and other reports we've covered as being consistent with CCI's thinking.
Boyd cautioned, however, that the situation would likely be very different in a military crisis involving Taiwan.
"Beijing views their cyber program very differently", Boyd says. "For the Chinese, it's a vastly different thing, how they use their cyber apparatus."
"In the intel community [we] refer to Russia as a tornado in cyberspace and China as climate change".
"We assess, without any concrete evidence, that Beijing is trying to develop network accesses in the United States, and elsewhere amongst our allies to give the PRC a military advantage in any military crisis across Taiwan".
This makes perfect sense, of course, but it is refreshing to hear an intelligence professional speak so clearly about it.
Three Reasons to be Cheerful this Week:
- Axie Infinity hack cryptocurrency recovery: Norwegian police have seized USD$5.8m of cryptocurrency stolen by North Korea's Lazarus Group in last year's Axie Infinity hack.
- Hackers detained in South Korea: South Korean police have detained 12 people for breaching hundreds of websites and stealing personal information of 7 million people. (more on Risky Biz News)
- Belgium launches nationwide vulnerability disclosure policy: Belgium has become the fourth European country to give cybersecurity researchers a legal way to report bugs.
Sponsor Section
Seriously Risky Business is supported by the Hewlett Foundation's Cyber Initiative and corporate sponsor Proofpoint.
Our @threatinsight researchers have tracked a recent rise in campaigns abusing #Microsoft #OneNote.
— Proofpoint (@proofpoint) 3:05 PM ∙ Feb 17, 2023
This graph breaks down the wide variety of #malware distributed using this method. AsyncRAT tops the list, with familiar suspects Agent Tesla and Qbot also appearing.💡
Okta and Passwordless Authentication
Risky Business publishes sponsored product demos to YouTube. They're a great way for you to save the time and hassle of trying to actually get useful information out of security vendors. You can subscribe to our product demo page on YouTube here.
In our latest demo, Brett Winterford and Harish Chakravarthy demonstrate to host Patrick Grey how Okta can be used for passwordless authentication. These phishing resistant authentication flows — even if they are not rolled out to all users — can also be used as a high-quality signal of phishing attempts that can be used to trigger automated follow-on actions.
Shorts
Launder Money and Find Out
This Reddit post is a stellar example of unintentional "play stupid games, win stupid prizes" hilarity. The original poster, Suspendedbankaccs1, is baffled as to why their HSBC, Santander and Barclays bank accounts have been suspended.
It turns out that Suspendedbankaccs1 happens to "sell Monero payment processor software as a SaaS product", but maintains that everything is fine "because it's Monero, I have no way of knowing the real source of the payments". (Monero is a privacy-enhanced cryptocurrency and transactions are theoretically anonymous.)
"I am not money laundering", Suspendedbankaccs1 adds.
All good then. Not money laundering at all.
Twitter, Meta Shake Up User Authentication, Verification
Twitter has announced that it'll require users to subscribe to its premium Twitter Blue service to receive SMS two-factor authentication (2FA) messages. Apparently this was costing USD$60m a year in bogus 2FA authentication texts by fraudsters registering premium SMS numbers with Twitter and collecting revenue by triggering 2FA login events. This fraud is known as "SMS Pumping".
Meta also announced that it will begin testing a new "Meta Verified" subscription bundle that "includes account verification with impersonation protections and access to increased visibility and support".
The Risky Business podcast contains extensive discussion of these initiatives.
China and Russia's Ransomware Problem
ESET's T3 2022 Threat Report (T for trimester), released earlier this month, reports that China had the most ransomware incidents in the last four months of 2022, followed by the US, Russia, Ukraine then Japan. Strikingly, for the whole of 2022 ESET reckons there were more ransomware incidents in Russia than in the US (although it's not actually clear what ESET defines as an incident).
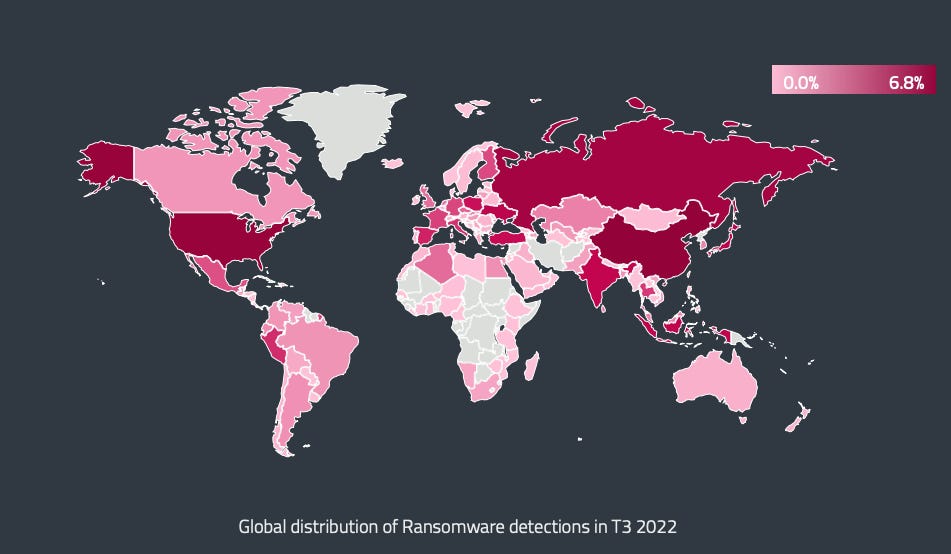
Part of the reason Russia and Ukraine appear so high in the statistics is the use of what ESET calls "wiper mimicking ransomware" in both countries over the course of the war. ESET also points out, however, that there are some ransomware groups that do attack organisations in Russia and points to OldGremlin, an apparently Russian-speaking group that has carried out attacks over the past few years.
Early last year in this newsletter a guest post from Daniel Gordon reported on the extent of China's ransomware problem. At the time we speculated that this could present an opportunity to collaborate with the PRC to counter ransomware. With the way US-China relations are heading, however, we think the odds of that happening are pretty slim.
Risky Biz Talks
In addition to a podcast version of this newsletter (last edition here), the Risky Biz News feed (RSS, iTunesor Spotify) also publishes interviews.
In our last "Between Two Nerds" discussion Tom Uren and The Grugq discuss whether cyberespionage is different from SIGINT and if so, does there need to be a cyberespionage organisation?
From Risky Biz News:
EU cybersecurity agencies warn of Chinese APT spying: ENISA, the EU's Cybersecurity Agency, and CERT-EU, the CERT team for EU official bodies and institutions, have published a joint advisory warning EU countries of the increasing threat of Chinese cyber-espionage operations.
The alert particularly warns about the activities of six Chinese groups (or APTs, advanced persistent threats) — namely APT27, APT30, APT31, Ke3chang, GALLIUM, and Mustang Panda.
ENISA and CERT-EU say operations conducted by these groups "pose a significant and ongoing threat to the European Union." (much more at Risky Biz News)
Applied Materials indirect losses: Semiconductor technology company Applied Materials expects to lose around $250 million in the next quarter after a ransomware attack on one of its suppliers has disrupted its supply chain. Applied Materials didn't name the supplier, but The Record believes the company may be engineering firm MKS Instruments after the firm postponed an earnings call a week before due to a ransomware attack.
DMCA and GDPR abuse: Spanish company Eliminalia is behind a wave of fake GDPR and DMCA complaints that have flooded tech companies over the past year and have been used to remove articles and stories exposing financial fraud and corruption. The company advertises its services to the rich and wealthy, such as politicians, business moguls, and shady companies. According to a report from investigative journalism outfit Forbidden Stories, tech giants have often sided with Eliminalia and enforced their takedown requests, even if they were blatantly fake.



