Risky Biz News: Microsoft to phase out 3rd-party printer drivers for security reasons
In other news: Akira and Lockbit exploit Cisco ASA/FTD zero-day; FBI links Stake crypto-heist to North Korea; Ukrainian hacktivists unmask Russia's Cuban mercenary recruiting scheme.
This newsletter is brought to you by Red Canary, your Managed Detection and Response ally. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
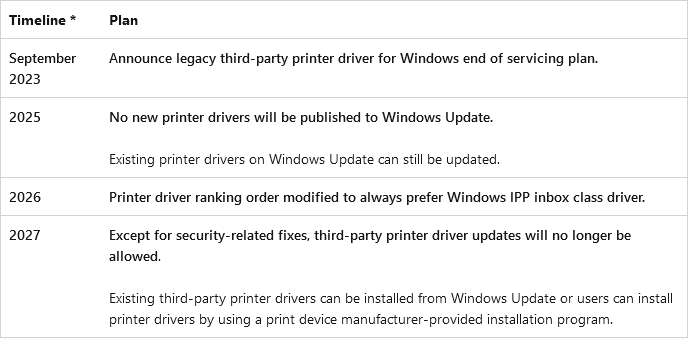
Microsoft will phase out the use of third-party printer drivers in Windows in favor of a new and more secure interface.
"In the near future, Windows will default to a new print mode that disables 3rd party drivers for printing," said Microsoft security engineer Johnathan Norman.
"That new system will have quite a few big security improvements, which we plan to detail in a future blog post."
Currently, companies such as Canon, Epson, HP, and others submit printer drivers to Microsoft, which then uses the Windows Update process to ship them to users across the world. This system covers printers for new devices but also security updates for existing drivers.
As part of its deprecation plan, Microsoft will stop accepting new printer drivers from device manufacturers in 2025.
Windows Update will continue to deliver already-existing printer drivers, but after that date, printer makers will need to rely on their own download portals to distribute new (legacy mode) drivers.
Starting with 2026, both Windows 10 and Windows 11 will prioritize the installation of printer drivers for its newer "IPP Class Driver" platform.
After 2027, Windows Update will only deliver security updates for old-gen third-party printer drivers.
Microsoft says it will allow printer makers to use Windows Update to deliver security patches for their drivers until the end-of-servicing of all its current operating systems.
The plan is to have most printers up and running on the new and more secure printer driver framework by the end of the decade.
Third-party printer drivers have been a security nightmare for Windows systems for decades. Because most infosec research work focuses on improving the OS, vulnerabilities in printer drivers tend to remain undetected for years and years.
Breaches, hacks, and security incidents
Stake crypto-heist attribution: The US Federal Bureau of Investigation says North Korean hackers are responsible for stealing $41 million worth of crypto-assets from crypto-gambling platform Stake[.]com. The FBI has linked the hack to a group it tracks as Lazarus, APT38, or TraderTraitor. The FBI says the group has stolen more than $200 million from crypto platforms this year alone. This includes more than $60 million worth of assets from Alphapo, $37 million from CoinsPaid, and $100 million from Atomic Wallet users.
Sri Lanka ransomware attack: A ransomware attack has encrypted email servers operated by the Sri Lankan government in an incident that has led to severe data loss. More than 5,000 government employees have lost emails received between May 17 and August 26 this year. Officials blamed the data loss on the lack of recent server backups and say they've implemented a daily backup routine in the aftermath of the attack. [Additional coverage in Ada Derana]
Dymocks breach: Australian book retailer Dymocks has confirmed a security breach after the personal data of its users was posted on a hacking forum. The hack took place earlier this month and impacted more than 836,000 users. The breach exposed the details of users who signed up for Dymocks' website and included details such as names, dates of birth, genders, emails, phone numbers, and physical addresses.
Traderie breach: Gaming platform Traderie is notifying users to a data breach that took place this year. The website allows users to trade in-game items from titles such as Roblox, Rocket League, Diablo, and Elden Ring. [Additional coverage in TechCrunch]
Cuban leaks: Pro-Ukrainian hacktivist group Cyber Resistance has hacked a Russian military officer and leaked documents showing that Russia is recruiting Cuban citizens to fight in Ukraine. The group published 199 passport scans of Cuban mercenaries who signed contracts with the Russian Armed Forces. The group's leak comes after the Cuban government issued a statement claiming it dismantled a human trafficking network operating from Russia that was recruiting and transporting Cubans to fight for Russia in Ukraine.
General tech and privacy
Chrome Web Store redesign: After Google announced Chrome itself will get a redesign, one is also coming to the Web Store. Just a UI revamp. Nothing about the invasion of malicious extensions posing as legitimate extensions.
Twitter bans scraping: Right-wing propaganda cesspool X (formerly Twitter) has updated its terms of service to ban content scraping. Data protection agencies from 12 countries called for the protection of web data against data scraping last month, but don't let yourself fooled. Musk just wants to prevent AI companies from scraping Twitter content and monetize it instead. [Additional coverage in TechCrunch]
Android Automotive side-loading: Car owners have figured out a method to side-load unapproved apps on their Android cars. The technique relies on creating a Play Store dev account, uploading the wanted app as an "internal beta," and then loading it on the car. Because the app is labeled as an internal beta, it is available to the dev account only and without needing to go through the normal Play Store scan and approval process.
Government, politics, and policy
Yesh Atid investigation: The Israeli Shin Bet intelligence service is investigating a suspected hack of 15 members of Yesh Atid, Israel's main opposition party. Yesh Atid officials claim that 15 of its members lost access to their WhatsApp accounts at the same time for several hours last week. Opposition leader Yair Lapid and members running in local council elections were among those affected. [Additional coverage in The Times of Israel]
NY police social media tracking: An investigation has discovered that New York law enforcement agencies have spent millions of US dollars on contracts to track social media activity. One of the contracted companies is Voyager Labs. The company stands out because it was sued by Meta earlier this year for creating 40,000 fake Facebook profiles in order to scrape data from 600,000 users.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Red Canary Principal Readiness Engineer Gerry Johansen about the need to prepare IR plans in advance and why that’s just as important as the IR playbook itself.
Cybercrime and threat intel
Myanmar fraud crackdown: China's Ministry of Public Security (MPS) says it received 1,207 suspects from Myanmar law enforcement. The suspects were detained last week as part of a coordinated large-scale crackdown against scam call centers in the Myanmar's northern regions. The suspects are accused of scamming Chinese citizens in telecom fraud and extortion schemes. A Chinese police report claimed that 95% of the Chinese nationals working in northern Myanmar call centers had gone there "voluntarily" after failing to find employment in China. Previous reporting on the topic and a UN report say the opposite, claiming that many are trafficked and forced to work in the call centers against their will.

South Korean hacker detained: South Korean authorities have arrested a 30-year-old man from Seoul for creating and selling access to doppelganger online accounts. The suspect is accused of creating more than 100 accounts on the Blind social media app that used the names of employees of large companies and public institutions, including police officers. Officials say the suspect exploited a bug in Blind's identity verification process. Authorities had been looking for the suspect after one of the accounts posted fake police alerts about crimes across Seoul last month.
Turkish cybercrime ecosystem thrives: A Financial Times report [non-paywall] claims that Turkey's cybercrime ecosystem is seeing an explosion in activity after Russian hackers fled their country to avoid military conscription and are teaming up with the local Turkish crews.
New npm malware: Twenty-eight malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
DDGroup: Security researcher Gi7w0rm has discovered a threat actor named DDGroup that has been running malspam campaigns spreading remote access trojans for years.
Qakbot: The Shadowserver Foundation looks at Qakbot's historical bot infections. Most of it is in the US, the EU, and India. The FBI took down Qakbot two weeks ago.
MrTonyScam: A Vietnamese threat actor going by the name of MrTonyScam has been conducting expansive Facebook Messenger spam campaigns delivering malware using malicious attachments. Security firm GuardioLabs says the malware steals browser cookies and credentials and exfiltrates the data to Discord and Telegram channels controlled by the attacker. The data is then put up for sale on dedicated marketplaces. Guardio says the attacker seems to value Facebook advertising accounts above anything else.

Malware technical reports
XMRig campaign: CloudSEK has a report on a new cryptomining campaign hitting servers via weak SSH accounts.
HijackLoader: Zscaler has spotted a new malware loader named HijackLoader. The loader was first spotted in July and is being used to drop numerous malware families, such as Danabot, SystemBC, and RedLine Stealer.
Bumblebee: The Bumblebee malware is still active and spreading in the wild. After the FBI's Qakbot takedown, keep an eye on this one (and IcedID).
Gozi: Corelight has published some detection rules for the Gozi malware.
Necurs and Pushdo DGA: Akamai's security team analyzes the domain generation algorithms (DGAs) used by the Necurs and Pushdo botnets.
HardBit ransomware: Rostelecom's security team has developed a decrypter for the HardBit ransomware. The decrypter can recover files locked by the ransomware's v2 and v3 versions. These versions have been used in attacks dating back to October of last year. Rostelecom says the two versions used a weak encryption scheme that allowed data decryption.
Sponsor Section
Timing and response plans could mean the difference between an attempted attack or a full-blown compromise. Red Canary's Incident Response & Readiness Guide arms security teams with the blueprint for a modern and effective incident response plan.

APTs and cyber-espionage
Spamouflage Dragon IO on Gab: A Chinese threat actor named Spamouflage Dragon (aka DragonBridge) has been observed pushing pro-CCP propaganda on alt-right platform Gab. The group was first spotted in 2019 and is one of China's most proficient disinformation groups, with a large presence on Facebook, Instagram, and Twitter. Disinformation analysis company Alethea says this is the first time the group has been active on Gab. Alethea says Spamouflage Dragon posted CCP talking points on topics such as Xinjiang, Chinese political dissidents, and rare earth mining.
Another Telegram doppelganger: Kaspersky has spotted another fake Telegram app infected with spyware, uploaded on the official Google Play Store, and targeting Chinese-speaking users. Unclear if this is related to BadBazaar, but sure sounds like it.
ScarCruft/Reaper: South Korean researchers have analyzed a recent ScarCruft/Reaper campaign that is exploiting the recent release of treated water from the Fukushima nuclear plant.
Vulnerabilities, security research, and bug bounty
Cisco ASA/FTD zero-day: The Akira and Lockbit ransomware groups are exploiting a zero-day (CVE-2023-20269) in Cisco ASA VPNs and Cisco FTD firewalls to gain access to corporate networks. The zero-day allows attackers to conduct unlimited authentication attempts, brute-force a device's valid credentials, and then connect to the device. Cisco plans to release security updates but has recommended that customers enable MFA on ASA and FTD devices in the meantime.
QNAP security updates: Taiwanese NAS vendor QNAP has released three security updates for its products.
Orbeon Forms RCE: watchTower Labs has published a write-up and PoC for an RCE in the Orbeon Forms form-building web app.
Zavio vulnerabilities: BugProve researchers have identified 33 vulnerabilities in Zavio IP security cameras. Seven of the reported vulnerabilities are pre-authentication remote code execution flaws that can be used to hijack affected security camera models. The company has published details and proof-of-concept scripts for all issues after the vendor failed to respond for almost nine months.
SEL vulnerabilities: Nozomi researchers have discovered nine vulnerabilities in the Windows apps of Schweitzer Engineering Laboratories (SEL). The two apps are used by engineers to configure and manage power grid equipment. Nozomi says some of the vulnerabilities allow RCE on an engineer's workstation, and the vulnerabilities could be abused as an entry point for attacks on power grids. SEL has released patches for all reported issues.
PyPI malware persists in mirror sites: An academic study of 4,600 malicious Python libraries found that 72% of packages persisted across PyPI mirror sites even after the libraries were removed from the main PyPI website.
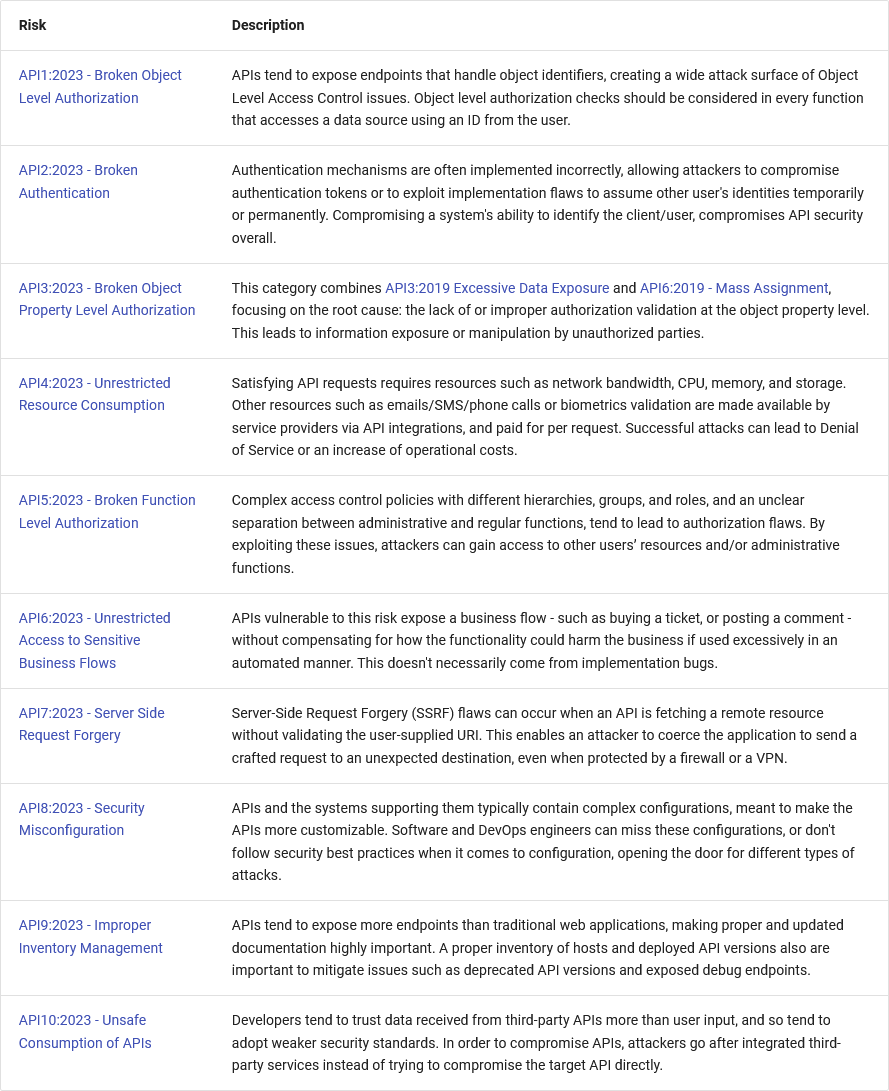
OWASP API Security Top 10 (2023 edition): OWASP has finalized the 2023 edition of its API Security Top 10 security risks.
Infosec industry
New tools—SocketSleuth: DevSecOps company Snyk has open-sourced a Burp extension named SocketSleuth to aid in pen-testing WebSocket-based applications.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at how companies often make unilateral decisions that constrain states' behavior, for better and worse.




