Mature Organisations Still a Security Horror Show
PLUS: Five Eyes to Watch Sticky Fingers
Your weekly dose of Seriously Risky Business news is written by Tom Uren and edited by Patrick Gray. It's supported by the Cyber Initiative at the Hewlett Foundation and this week's edition is brought to you by Airlock Digital.
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. Find this edition here and on Apple podcasts:
Mature Organisations Still a Security Horror Show

CISA and NSA have published a joint advisory on the most common misconfigurations experienced in cases across federal and state governments, the defence industrial base and critical infrastructure operators.
You would expect to see well configured networks at these organisations, but the CISA/NSA advisory says these misconfigurations occurred even in networks with "mature cyber postures". The list is made up of 101-level problems:
- Default configurations of software and applications
- Improper separation of user/administrator privilege
- Insufficient internal network monitoring
- Lack of network segmentation
- Poor patch management
- Bypass of system access controls
- Weak or misconfigured multifactor authentication (MFA) methods
- Insufficient access control lists (ACLs) on network shares and services
- Poor credential hygiene
- Unrestricted code execution
The report describes these misconfigurations as "systemic weaknesses across many networks". Given that getting these settings right is 'basic cyber hygiene', these misconfigurations shouldn't exist in an organisation with a mature cyber posture.
These misconfiguration errors fall into two buckets.
The first bucket includes misconfigurations at least partly attributable to manufacturer's standard practices. Many commercial devices, for example, contain predefined default credentials for built-in administrative accounts. The report cites "network access [devices], printers, scanners, security cameras, conference room audiovisual (AV) equipment, voice over internet protocol (VoIP) phones, and internet of things (IoT) devices" as commonly containing default credentials.
Other examples include insecure or legacy protocols or services enabled by default, or insecure or overly permissive standard configurations.
In these cases network defenders are required to undertake configuration work even before products we would call 'insecure by default' are deployed.
These misconfiguration errors could be reduced by pressuring vendors to improve their security practices. The advisory says "software manufacturers must reduce the prevalence of these misconfigurations… by incorporating secure-by-design and -default principles and tactics into their software development practices".
In the second bucket, the network owner is responsible for the misconfigurations or weaknesses in network segmentation, internal network monitoring, privilege management, and credential hygiene.
Under 'poor credential hygiene', for example, the advisory explains how lax policies result in passwords that can easily be guessed in a relatively short time. In one security assessment it took just 12 hours for a security assessment team to crack 80% of user passwords. Even worse, assessment teams also frequently discover cleartext passwords.
The advisory recommends organisations follow National Institute of Standards and Technologies (NIST) password policy guidelines and suggests they consider using password managers.
Overall, our reading of the advisory is that — even for many US organisations important enough to receive support from CISA and NSA — security is not good enough. And manufacturers actually add to the problem by shipping products that require network defenders to remediate security vulnerabilities before they can be deployed safely.
This advisory, then, explains the reasons why governments should be pressing software manufacturers to embrace secure-by-design principles. Even large organisations struggle with the basics, so it's time that product vendors started helping rather than hindering security efforts.
What is Secure by Design?
Another strand of CISA's effort entails defining what secure-by-design product development actually looks like. This week it released a revised version of the Secure-by-Design guidance document it co-authored with US and international partner organisations.
The document contains high-level principles targeted at senior leadership (eg 'Embrace radical transparency and accountability!', Lol) as well as more practical advice aimed at practitioners ('Actively discourage unsafe legacy features'). It's a heady mix.
The other two principles are 'Take ownership of customer security outcomes' and 'Lead from the top'. From a vendor management perspective these three principles sound more like 'effort and expense' rather than 'profit and dollars'.
However, more practically, the document contains stacks of software development and business process suggestions that would improve security if organisations implement them. These range from the mundane, such as 'eliminate default passwords' to the paradigm-subverting 'replace hardening guides with loosening guides'.
This is all good stuff if a vendor already wants to improve the security of its products. The document describes how vendors can make their development practices more secure. But it doesn't do all that much to convince vendors to invest the time and effort to improve product security.
It also seems that CISA and its co-authors aren't convinced that vendors are on board with secure development either. They write:
Customers should also push their vendors to publicly document the secure by design actions each vendor takes. Collectively, this can create a strong demand signal for security, which can encourage and enable software manufacturers to take steps towards greater security. In other words, just as we seek to create a pervasive secure by design philosophy within software manufacturers, we need to create a "secure by demand" culture with their customers .
This, in essence, is the problem at the crux of the secure-by-design push. What are the incentives that will encourage vendors to adopt these more secure practices? Cyber security authorities don't have the regulatory clout to force vendors to change their ways.
We think there is space here for government regulators to require more transparency from vendors. The document's section on 'embrace radical transparency' has a number of concrete suggestions that would not be too onerous for vendors but could still provide the market with useful information about product security.
These include publishing statistics such as patching or MFA adoption rates, or publishing high level threat models and security roadmaps. Requiring these initiatives by themselves won't change much, but they are the baby steps that could start the ball rolling.
Five Eyes to Watch Sticky Fingers
At an FBI-hosted security summit, Five Eyes security intelligence leaders warned about the threat of PRC-sponsored intellectual property (IP) theft. This was the first-ever public joint appearance of leaders from Five Eyes countries’ security intelligence services and it is good to see this kind of public outreach.
The Australian Broadcasting Corporation reported FBI Director Christopher Wray told the summit that AI technology was a particular target, but the group of leaders also provided specific historical examples of IP theft. Wray cited the story of a US wind turbine company whose market capitalisation plummeted after its IP was stolen by an insider that had been recruited by the company's Chinese joint venture partner.
Mike Burgess, Director-General of the Australian Security Intelligence Organisation, spoke of an Australian company who discovered that inferior counterfeit products were being sold under its brand name. It was subsequently found that PRC state-backed hackers stole the company's IP using malware delivered by a USB drive given to a company employee at an international conference.
"That USB downloaded malware onto that laptop, which later on, when they were connected back to their corporate network, was used to steal their intellectual property," Burgess said.
"That intellectual property was passed from the intelligence services to [a] state-owned enterprise that mass produced the goods and sold them on the market that undercut them."
The UK and Australian governments have already published security guidance tailored for innovative startup companies.
Three Reasons to Be Cheerful this Week:
- NTLM death watch: Microsoft has announced plans to remove support for NTLM authentication in Windows 11 at some point in the future. NTLM has been around since 1993 and is insecure relative to newer protocols, but is still required in some scenarios. Risky Business News has more coverage.
- AI help with access control lists: Google has described a new tool that allows developers to modify security policies using simple English instructions rather than system-specific syntax. CISA and NSA identified poor access control management as one of the 10 most common misconfiguration problems in large organisations, so if it could be extended for systems beyond Google's, this could be a win.
- California's Delete Act signed: so Californians will be able to request their personal data be deleted from the servers of online companies including data brokers. Further coverage in The Verge.
Sponsor Section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Airlock Digital founders Daniel Schell and David Cottingham about the recent Microsoft Digital Defense Report and the problem of properly securing PowerShell.
Shorts
iOS Sandboxing: Two Steps Forward
Google's Project Zero has a write up that likely describes one of the exploits that was used in the Intellexa alliance-related campaign that we wrote about last week. The exploit was part of a chain discovered by Google's Threat Analysis Group in collaboration with Amnesty International, at about the same time Amnesty was examining the Intellexa iOS one-click 0day.
This exploit targeted a buffer overflow vulnerability in the Safari renderer sandbox. Ian Beer, the report's author, describes the bug as "very basic" and says a "simple fuzzer targeting the IPC layer would likely have found this vulnerability in seconds". Although the bug itself was simple, the exploit itself was complex and Beer thinks the authors went to the effort to build a framework that could be reused for future bugs. In other words, they did a lot of work to make things easier for themselves in future.
Forcing attackers to do more work to successfully exploit bugs is good, but Beer suggests it would be good to pay attention to secure coding fundamentals as well. He writes:
This vulnerability was introduced less than two years ago — we as an industry, at a minimum should be aiming to ensure that at least new code is vetted for well-known vulnerabilities like buffer overflows. A low bar which is clearly still not being met.
Your Face Belongs to… Clearview
The Verge has a long interview with New York Times tech reporter Kashmir Hill about facial recognition company Clearview AI. It's a good interview that covers both Clearview AI’s history and also the policy questions that facial recognition technology presents.
Hill covers privacy issues and has recently published Your Face Belongs to Us, a book about Clearview AI.
Sandworm Targets Ukrainian Telcos
Ukraine's CERT has revealed (Ukrainian document) that Russian cyber operators regularly target Ukrainian telcos with combined cyber espionage and disruption operations. These operations typically start with an intelligence-gathering phase where credentials and documents are stolen. This is followed by a destructive phase where they disable network, server and data storage equipment. The Record has more coverage.
Risky Biz Talks
You can find the audio edition of this newsletter and other fine podcasts and interviews in the Risky Biz News feed (RSS, iTunes or Spotify).
In our last "Between Two Nerds" Tom Uren and The Grugq discuss how changing circumstances affect the risk/reward balance and alter whether effects operations are worthwhile.
From Risky Biz News:
Israel warns citizens of security camera hack risk: In the face of an escalating military conflict with Hamas and Hezbollah forces, the Israeli government has asked citizens to secure home security cameras or shut them down completely, fearing the devices could be hacked and used for espionage and intelligence collection.
In a memo on Friday, Israel's National Cyber Directorate asked camera owners to change their passwords, enable two-factor authentication if present, and enable automatic security updates.
If camera owners can't change any of their settings, officials have urged owners to either cover camera lenses or shut down devices completely.
Israeli officials aren't taking any chances and have most likely learned a vital lesson from the recent Russo-Ukrainian conflict, where security cameras across Ukraine have been hacked by Russian hackers to track military aid convoys and adjust missile targeting in real-time.
Aviram Azari case: US prosecutors say that an Israeli private investigator named Aviram Azari hired hackers to steal emails from climate activists and leak them to news agencies. The stolen emails were used to write articles criticising the tactics of climate activists. The articles were then cited in lawsuits involving Exxon Mobil, seeking to dodge investigations about its impact on climate change. US prosecutors have not linked Azari to Exxon Mobile. Prosecutors have asked the judge for a sentence of hundreds of months in prison, while Azari's team is asking for a maximum 60 months prison sentence after he pleaded guilty last year. Azari's sentencing is scheduled this week on October 18. [Additional coverage in Reuters]
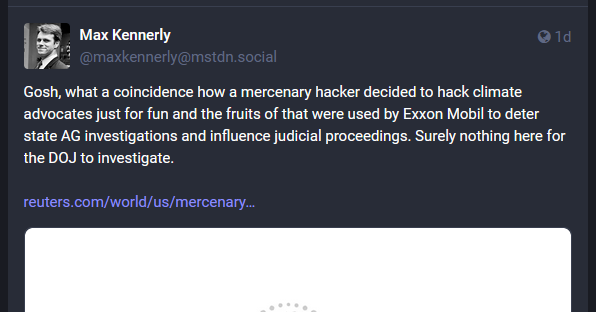
Ransomware payments: A Splunk survey of 350 CISOs found that 96% worked for companies that got hit by ransomware over the past year, and a whopping 83% ended up paying the attackers. The survey found that the vast majority paid the attackers through an intermediary, such as a negotiator or their cyber insurance provider. A quarter of all paid ransoms were above $250,000, making the attacks a very lucrative business for ransomware gangs. [Additional coverage on the Splunk website]
"The cyber insurance process has changed over the past few years. It is getting to the point where we are wondering if it is worth our time."