Risky Biz News: Malay officials take down BulletProftLink, one of the largest PhaaS providers
In other news: UAE tricks and arrests BEC scam group; Windows Server 2012 gets paid security updates; and Poloniex hacked for $130 million.
This newsletter is brought to you by Gigamon. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Malaysian police have dismantled Phishing-as-a-Service provider BulletProftLink and have detained eight suspects, including the platform's main administrator.
The service launched in 2015 and grew to become one of the largest on-demand phishing platforms known to date.
It operated like your regular SaaS platform—but for email phishing gangs. For a $2,000 monthly fee, the service would provide hosting for phishing sites and access to phishing kits, email templates, and tutorials.
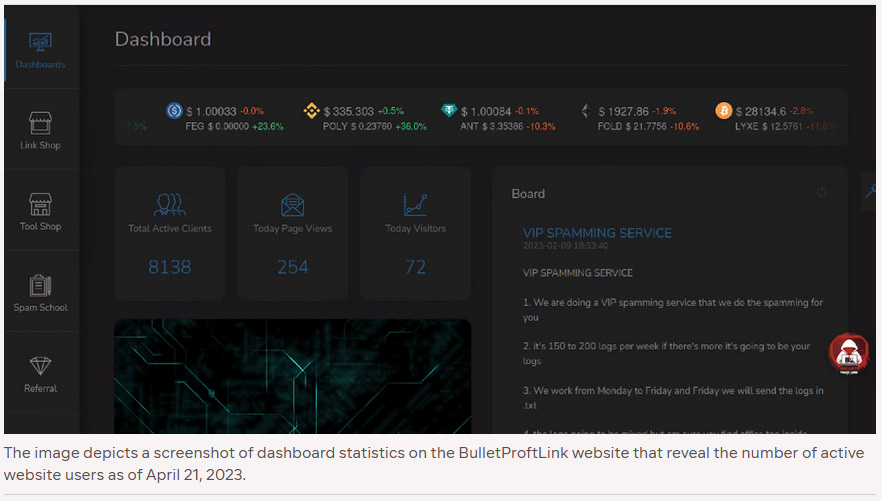
According to a screenshot of the BulletProftLink dashboard captured by threat intel company Intel471 in April this year, the service had 8,138 registered users and was selling phishing templates to impersonate emails and login pages for 327 different brands.
Also known as BPL or Anthrax, the service exploded on the infosec scene in 2021 when Microsoft said it was seeing hundreds of thousands of phishing pages hosted through the platform's infrastructure.
In the fourth edition of its Cyber Signals report [PDF] in May this year, Microsoft said BulletProftLink had become one of the major infrastructure suppliers for BEC gangs across the world.
The service also recently integrated features to provide reverse proxy-based phishing capabilities needed to intercept some types of 2FA challenges and gain access to MFA-protected accounts.
In a press conference, the Royal Malaysia Police said it took down the service after receiving a tip from the FBI and the Australian Police Force in October. Eight suspects were subsequently detained in raids across the cities of Kuala Lumpur, Sabah, Selangor, and Perak.
While Malay officials did not release any of the names of the detained suspects, the site's administrator had been doxxed for more than three years. In a three-part series in October 2020, security researcher Gabor Szathmari identified the BulletProftLink admin as Adrian Bin Katong, a man going online as AnthraxBP and who claimed on LinkedIn to be the CEO of a company named BPL Hosting.
At the time, Szathmari said Katong was flaunting a life of expensive cars, jewelry, and exotic trips—before going dark in the aftermath of the researcher's exposé.
Malay officials did not specify if they received an extradition request.

@pdrmsia_rasmi[VIDEO PILIHAN] OP KHAS BULLETPROFTLINK: HASIL RAMPASAN Ikuti sedutan video Sidang Media Khas oleh Ketua Polis Negara (KPN), IG Tan Sri Razarudin Husain yang memaklumkan pelbagai rampasan telah dilakukan ke atas server yang berpusat di ibu kota, antaranya e-wallet Cryptocurrency bernilai hampir RM1 juta, alatan elektronik, telekomunikasi, kad ATM, barangan kemas dan kenderaan milik ahli sindiket.

Tiktok failed to load.
Enable 3rd party cookies or use another browser
Breaches, hacks, and security incidents
Poloniex crypto-heist: Cryptocurrency exchange Poloniex has lost $130 million worth of assets after hackers drained its hot wallet. Poloniex confirmed the hack, paused transactions, and promised to reimburse user losses. This is the exchange's second heist after also getting hacked in 2014. Poloniex's latest incident is currently ranked as the 14th-largest hack ever.
Raft crypto-heist: Decentralized finance (DeFi) platform Raft has lost $3.3 million worth of cryptocurrency after a hacker exploited a vulnerability in its platform. The company confirmed the hack on social media and paused the minting of its R stablecoin to investigate the incident. Wintermute head of research Igor Igamberdiev has a breakdown of the exploit. [Additional coverage in The Crypto Times]
Maine government joins MOVEit list: Officials from the US state of Maine have disclosed that the personal data of more than 1.3 million residents was stolen in a cyberattack at the end of May. The leak covers the personal information of almost all Maine residents. The data was stolen by the Clop cybercrime group as part of its attacks that targeted MOVEit file-sharing servers. Almost 2,600 companies across the world have been impacted by the MOVEit hacks, and the data of 70 million users was stolen in the intrusions.
Anonymous Sudan DDoS attacks: The Anonymous Sudan "hacktivist" group claims it was behind two DDoS attacks that took down the websites of Cloudflare and OpenAI. None of the companies confirmed, and this may be your run-of-the-mill media-whoring and attention-grabbing attempts from hacktivist groups.
Indian cyber attacks on Qatar: Indian hacktivist group Indian Cyber Force has carried out DDoS attacks, defacements, and hack-and-leak operations against Qatari websites. The attacks come days after a Qatari court sentenced eight former Indian Navy officers to death in a non-public case.
TDS supply chain attack: A threat actor has compromised the systems of Transaction Data Systems (TDS), a software company in the pharmaceutical sector, and has used its remote-access capabilities to pivot into the networks of its customers, according to security firm Huntress Labs.
Optus 2022 hack update: Australian ISP Optus has lost a legal attempt to keep secret a report related to its 2022 hack. The report is a forensic assessment compiled by consultancy firm Deloitte on the root causes of the company's breach that led to hackers getting access to the data of 10 million current and former customers. Optus argued the report was legal advice compiled for internal use. The judge shot down the company's argument because it mentioned the report to journalists, and the judge allowed it to be included in the legal discovery process. [Additional coverage in the Guardian] [h/t Ravi Nayyar]
Australian ports down after cyberattack: Port operator DP World Australia has suspended operations at multiple ports across after a cyber-attack crippled its IT systems. The company says it expects the outage to last for "a number of days." The port terminals in Sydney, Melbourne, Brisbane, and Fremantle are impacted. Ship movements are not affected, but trucks can't load or unload cargo in some of the affected ports. Australian officials say the government's cybersecurity agency is assisting the company's investigation. The incident is suspected of being yet another ransomware attack. [Additional coverage in ABC]
Allen & Overy ransomware attack: A ransomware attack has disrupted the activities of Allen & Overy, one of the largest law firms in the world. The company confirmed the incident after members of the Lockbit ransomware gang took credit for the attack. In a post on their dark web leak site, Lockbit has given the company two weeks to pay its ransom demand. [Additional coverage in Reuters]
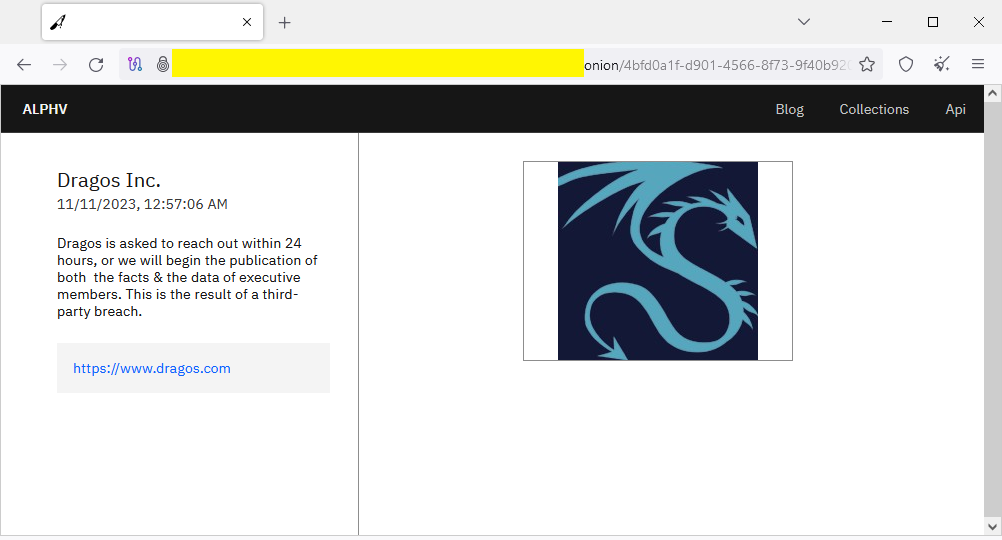
Dragos ransomware claim: The AlphV (BlackCat) ransomware gang claims it breached the IT systems of cybersecurity firm Dragos through one of its third-party vendors. The gang has listed the company on its dark web leak site in an attempt to force the company to pay a ransom. If confirmed, this would be Dragos' second security breach this year after a similar incident in May. [h/t Dominic Alvieri]
General tech and privacy
Intel class-action lawsuit: Five plaintiffs have filed a class-action lawsuit against Intel, alleging the company sold faulty chips for years. The lawsuit revolves around the Downfall vulnerability disclosed in August this year. Plaintiffs say Intel knew about side-channel attacks since 2018 but continued to manufacture and sell "defective" chips vulnerable to these types of vulnerabilities. The lawsuit is seeking monetary damage of at least $10,000 per plaintiff. [Additional coverage in DarkReading]
Tutanota rebrand: Secure email provider Tutanota has rebranded as Tuta.
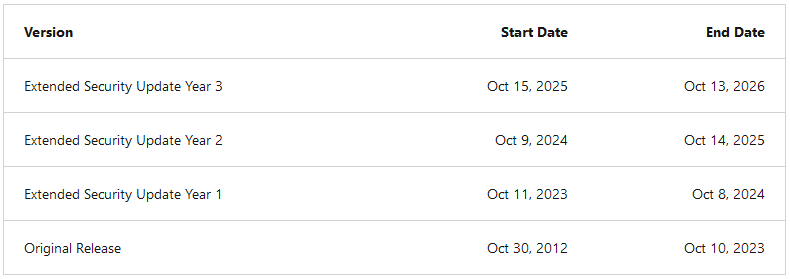
Windows Server 2012/R2 ESU: Microsoft is providing three years of paid security updates for Windows Server 2012/R2 versions to help enterprise customers phase out older systems. The Windows Server 2012 operating system reached End-of-Life last month on October 10. Companies that sign up for the extended support will receive security updates until October 13, 2026. Also known as ESU, this is the same type of paid extended support that Microsoft previously made available for Windows 7 users. Just like the Windows 7 ESU, the paid support is only available for enterprise customers—but not home users.
Government, politics, and policy
Russia moves to formally ban VPNs: Russian officials are preparing to formally ban the use of VPN services in the country. The move comes after Roskomnadzor has been testing blocks for various VPN protocols and services over the past year. Officials say a formal VPN block is needed for the safety of the Russian internet. [Additional coverage in RIA Novosti]
EYP spied on its own: In the print edition of its newspaper, Tovima journalists claim that Greece's EYP intelligence agency used the Predator spyware to spy on its own employees, even on high-ranking officers.
CISA funding support: A group of industry executives has urged Congress in an open letter to support CISA and not cut the agency's funding in next year's budget. The group warns that limiting CISA's budget will derail efforts to protect critical infrastructure and federal government networks, exposing America's sensitive networks to foreign adversaries and criminal groups. Signatories include the CEOs of Tenable, Palo Alto Networks, CrowdStrike, Trellix, and Forescout. [Additional coverage in CybersecurityDive]
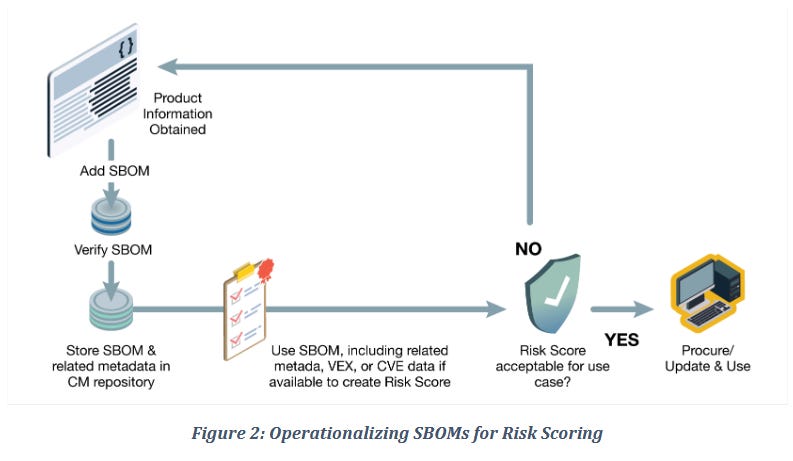
NSA&CISA SBOM guidance: CISA, the NSA, and ODNI have published joint guidance on the proper way to consume and use SBOM files. The guide was developed together with organizations from the private sector as part of the Enduring Security Framework project. The guidance looks at SBOM formats, their use for risk scoring, and query and reporting procedures.
Sponsor section
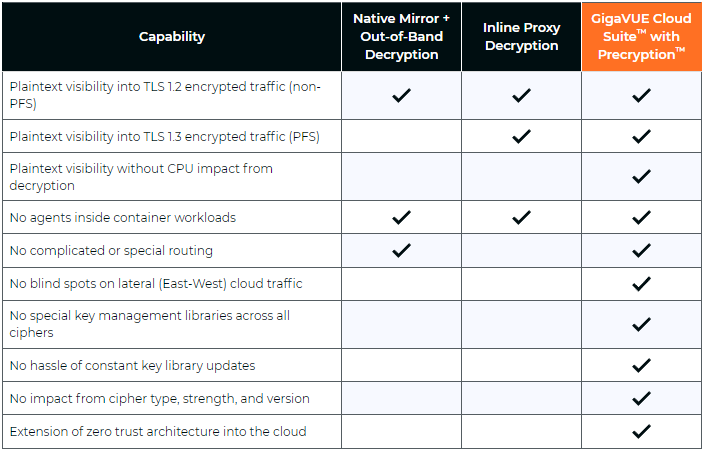
In this Risky Business News sponsor interview Tom Uren talks to Ryan Mahoney, Product Director at Gigamon. The TLS 1.3 encryption standard makes passive network monitoring inside your network difficult without break and inspect contortions. But Gigamon has what they call a “precryption” solution!
Cybercrime and threat intel
Phobos ransomware affiliates charged in France: French authorities have indicted a Russian couple for working as affiliates for the Phobos ransomware gang. Officials say the couple has worked with Phobos since 2020 and has successfully extracted payments from more than 150 victims across the world. The suspects are a couple in their 30s from Sankt Petersburg, Russia. They were detained in Milan, Italy, at the end of September and extradited to France, where they were formally charged last week. [h/t Gabriel Thierry]
Myanmar scam centers update: More than 160 Thai nationals are being returned home after being rescued from Myanmar scam centers. The group was rescued following a joint Myanmarese and Chinese law enforcement operation at the start of September this year. The Thai nationals were taken to China, where they were triaged and are now being sent home. More than 1,000 workers were rescued this year from Myanmar scam centers. [Additional coverage in the Bangkok Post]
BEC gang detained in Dubai: Dubai police have lured a cybercrime group to the UAE and detained 43 of its members for their involvement in a BEC scheme. The group has been active since 2018 and stole more than $36 million from victims. UAE officials began tracking the gang after they received a complaint from a legal firm in Asia that lost $19 million. The group hacked the CEO's email from where they tricked the law firm's account managers into transferring funds to their own bank accounts. Officials say that besides the arrests, they also issued Interpol arrest warrants for 20 other suspects, including the gang's leader.
IOTAseed restitution: UK police are in the process of returning around £1.9 million worth of cryptocurrency that was stolen in January 2018 by a Dutch hacker. Named Wybo Wiersma, the individual operated iotaseed.io, a website that generated seed phrases for the IOTA cryptocurrency wallets. Wiersma stole around £9 million worth of IOTA cryptocurrency by using copies of the seed phrases generated by his site. He was detained in 2019 following a Europol investigation and in January this year to four and a half years in prison.
Youshe gang: Chinese security firm Antiy looks at Youshe, an offshoot of the SilverFox cybercrime syndicate, known primarily for targeting Chinese users with rootkits and stealers via SEO poisoning and malspam phishing.
TAC5279 group: Sophos looks at TAC5279, a ransomware affiliate group that appears to have recently switched from the Vice Society to the Rhysida RaaS. Sophos says this group overlaps with what Microsoft tracks as Vanilla Tempest (formerly DEV-0832).
Gafgyt activity: A SANS ISC report covers the efforts of a Gafgyt botnet trying to hijack Huawei home routers.
New GoTiS ransomware: Symantec has spotted a new ransomware strain named GoTiS, part of the Xorist family, being distributed in the wild. No technical details are out yet.
New npm malware: Seventy-one malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
Malware technical reports
Effluence backdoor: The security team at consulting firm AON has published an analysis of Effluence, a backdoor planted on Atlassian Confluence servers that have been exploited using the CVE-2023-22515 vulnerability. The zero-day was used by a suspected Chinese APT (Storm-0062) in limited attacks since mid-September. AON did not attribute the backdoor to any threat actor yet.
Cobalt Strike: NCC Group has published a report going into the depths of the Cobal Strike framework.
Ducktail: Kaspersky has a report on the Ducktail infostealer and one of its most recent campaigns.
Dragon Babu: Chinese security firm Tinder Labs looks at Dragon Babu, a Windows rootkit used in campaigns targeting Chinese users to hijack victim web traffic and redirect users to advertising sites.
C3rb3r ransomware: Qihoo 360 and Trend Micro have published reports on the C3rb3r ransomware strain that has been recently deployed on hacked Atlassian Confluence servers via the CVE-2023-22518 vulnerability.
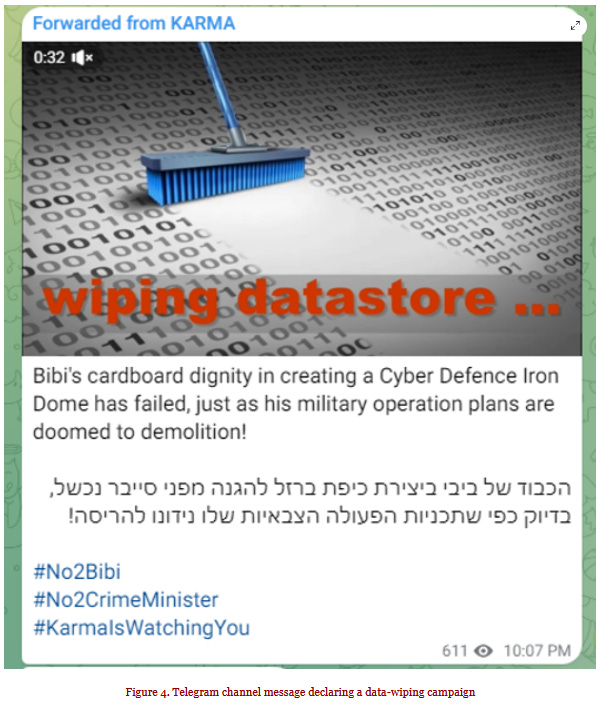
BiBi wiper: The BiBi wiper has been ported to Windows and is being used in a data destruction campaign targeting Israeli organizations. The malware was spotted at the end of October and was initially written for Linux systems. A pro-Hamas hacktivist group named Karma (or BiBiGun) has taken credit for creating and using the wiper, named after the nickname of Israel's prime minister, Benjamin Netanyahu. Researchers at Security Joes say the Karma group has a similar modus operandi as Iran-linked APT group Moses Staff.
Sponsor Demo
Brought to you by Gigamon Precryption, a visibility solution for encrypted traffic across virtual machine (VM) or container workloads. Perform advanced threat detection, investigation, and response across the hybrid cloud infrastructure. To learn more, please visit gigamon.com/precryption
APTs, cyber-espionage, and info-ops
IMPERIAL KITTEN: Crowdstrike is seeing an upsurge in activity from an Iranian APT group named IMPERIAL KITTEN in the aftermath of the Israel-Hamas war. The company says new operations are targeting transportation, logistics, and technology firms in the Middle East with malware such as IMAPLoader and StandardKeyboard. Crowdstrike believes the group is connected to Iran's Islamic Revolutionary Guard Corps (IRGC). IMPERIAL KITTEN is also known under names such as TA456, Yellow Liderc, and Tortoiseshell.
ATPs in Poland: Five different APT groups have launched operations against Poland since Russia's invasion of Ukraine. Four of the five APTs are suspected to be Russian and include the likes of Turla, APT28, APT29, and UAC-0056. The fifth is Chinese group Mustang Panda, Poland's CSIRT team said in a report last week.
Rattlesnake: Chinese security firm Sangfor has published a report on recent operations conducted by Pakistani-based APT Rattlesnake.
Kamran: ESET has discovered a new malicious spyware strain named Kamran hidden inside an Android app distributed via a watering hole attack on Hunza News, a website targeting Urdu-speaking users living in Pakistan's Gilgit-Baltistan region. ESET believes the malware has compromised 20 devices so far. No attribution yet, but this looks like a state op.
Black Cube op in Hungary: Israeli private spy firm Black Cube has targeted Hungarian activists and journalists ahead of the country's presidential election in 2022. Discovered by LinkedIn's security team, which tracks the group as Blue Tsunami, the attacks involved a network of fake companies and employees to reach out to targets with bogus job offers. Speaking at the Cyberwarcon conference, LinkedIn says clips from private conversations between Black Cube operators and targets were used to discredit NGOs in the election run-up. LinkedIn says it removed both the fake profiles and Black Cube's official profile following what it described as a "high volume of abuse." [Additional coverage in Reuters/non-paywall]
National clean-up operation: South Korea's intelligence agency is working with local antivirus makers to remove vulnerable versions of the MagicLine4NX software across the country. Together with AhnLab, Hauri, and ESTsecurity, officials have developed a tool that updates MagicLine4NX to the latest release and removes the older vulnerable versions. The three antivirus makers are pushing the tool to all their customers in what has been described as South Korea's first-ever software clean-up effort. NIS officials warned in June that North Korean hackers were exploiting a vulnerability (CVE-2023-45797) in MagicLine4NX to hijack and infect systems with malware. The software is used for user authentication, including for accessing several government services.
Vulnerabilities, security research, and bug bounty
Android security updates: The monthly security updates for Android smartphones are out.
OpenVPN security updates: OpenVPN has published a security update to fix two memory-related security issues.
QNAP security updates: Taiwanese NAS vendor QNAP has released two security updates for its products.
Lenovo & MSI key leaks: Binarly has an analysis of the private key leaks that took place at Lenovo in September 2022 and MSI in April 2023. The report's main finding was that multiple companies were apparently using the same Intel Boot Guard private keys to sign different types of firmware images.
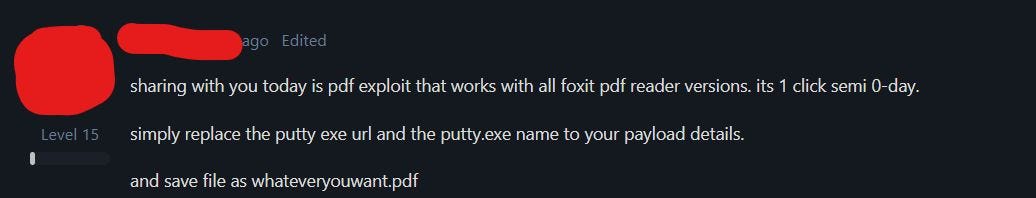
Foxit PDF reader one-click exploit: A threat actor has shared a one-click exploit for the Foxit PDF reader on an underground hacking forum. The Foxit is currently working on reproducing the exploit and preparing a patch, according to CyFirma security researcher Kaushík Pał, who found the post.
Infosec industry
Acquisition news: Security firm SentinelOne has acquired advisory firm Krebs Stamos Group and merged the company into a new entity named PinnacleOne. The new company will continue to provide the same business and geopolitical risk analysis the Krebs Stamos Group provided before. SentinelOne acquired the Krebs Stamos Group after the company laid off a third of all employees in May. [More in Alex Stamos' LinkedIn post]
"The entire KSG delivery team is coming over and we will continue to support our current clients with the same level of diligence and care while we hone and improve our services with the technical and analytical backing of SentinelLabs and the existing services teams."
New resources—Software Supply Chain Security: Security researcher Vishal Garg has published a GitHub repo with a collection of resources about supply chain security.
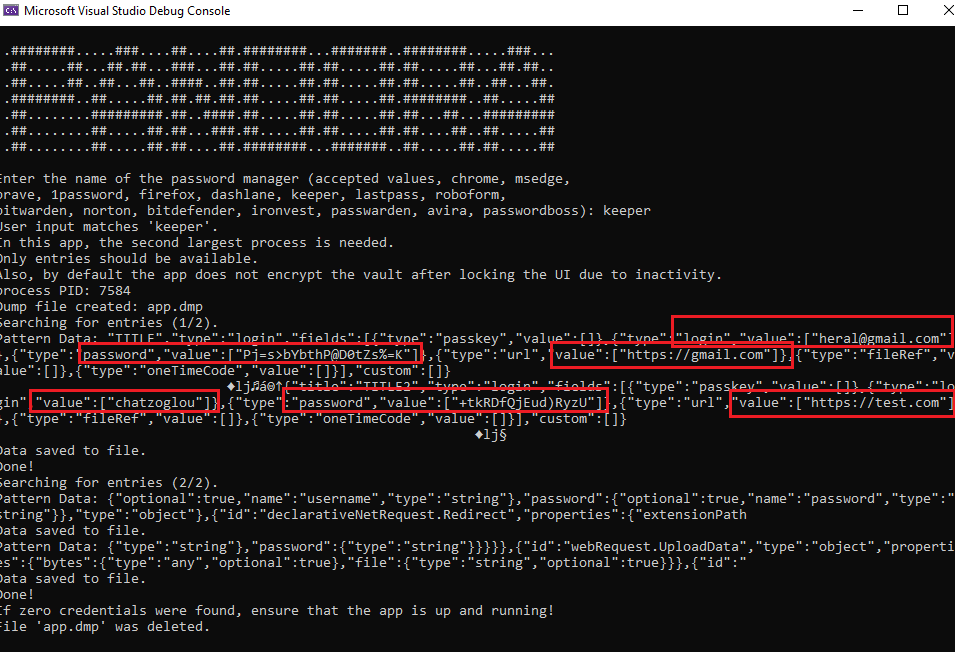
New tool—Pandora: Security researcher Efstratios Chatzoglou has released Pandora, a red-team tool for dumping and extracting credentials from browsers and password managers.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the internet-melting 1988 Morris Worm and how cyber security has changed since then.




