Risky Biz News: Let's revisit the Ivanti Connect Secure clusterfudge
In other news: Hackers steal data on hundreds of Mexican journalists; State Farm sued because of a ransomware gang's lies; and Proofpoint and Okta lay off staff.

This newsletter is brought to you by enterprise browser maker Island. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
All journalists take pride in being able to put together smart and intelligible sentences that convey a story. However, three weeks after Invanti disclosed the existence of two zero-days in its Connect Secure VPN appliance, things have become so twisted and convoluted that, at this point, I feel like it's time to bring out the bulleted list format in order to put some order in the ginormous clusterf**k that these zero-days have become.
So, for the sake of clarity—both mine and yours—let's review where things stand with the recent batch of Ivanti zero-days and their exploitation.
- On January 10, Ivanti published a security advisory on two vulnerabilities in its Connect Secure (formerly Pulse Secure) VPN appliance that were exploited in the wild. These two zero-days were assigned CVE-2023-46805 (authentication bypass) & CVE-2024-21887 (command injection).
- The security advisory did not include firmware patches but only temporary mitigations in the form of an encrypted XML file that customers were supposed to run on their devices.
- On the same day, security firm Volexity published a blog post and linked the attacks exploiting the two zero-days to a Chinese cyber-espionage group they were tracking as UTA0178.
- Two days later, on January 12, Mandiant confirmed the attacks and linked them to a group they were calling UNC5221.
- The threat actors were installing webshells and backdoors on the compromised devices. Attackers also installed JavaScript on the login pages to capture employee logins.
- Malware installed on infected devices includes stuff named GLASSTOKEN, GIFTEDVISITOR, BUSHWALK, WIREFIRE, LIGHTWIRE, FRAMESTING, THINSPOOL, ZIPLINE, WARPWIRE, and KrustyLoader. (These are detailed in technical reports from Volexity, Volexity, Volexity, Mandiant, Mandiant, QuoIntelligence, and Synacktiv)
- Some of these webshells and backdoors were exposed on the internet and could be fingerprinted, allowing security firms to determine the location of infected devices across the world. The number of infected devices is usually around a few hundred infected systems per day, but at one point, it peaked at around 1,700.
- A week later, on January 18, attacks against Connect Secure devices entered the mass-exploitation phase after proof-of-concept code was published online. Cryptominers botnets were the first to get in the act, per GreyNoise and Volexity. Initial access brokers and ransomware most likely followed—although unconfirmed for now.
- Exploitation could be detected by looking at the device's network traffic, the device's logs, or by running Ivanti's Integrity Checker Tool.
- The attacker also backdoored the device's configuration file. This meant that companies that applied the mitigation and then re-applied a backup of an older configuration file were reinfecting themselves.
- After the attacks were exposed and Ivanti released mitigations, security firms saw the Chinese APT bypassing both mitigations and Ivanti's Integrity Checker Tool.
- The APT's efforts to remain on the infected devices were most likely what caused Ivanti to delay its firmware patches, initially scheduled for January 22.
- On the day of the scheduled patch, Ivanti released an "external" Integrity Checker Tool that companies could use on their devices instead of the default (internal) one that was shipped with its devices and most likely compromised/altered.
- These firmware updates came out on January 31—but with a surprise. They also patched two other vulnerabilities tracked as CVE-2024-21888 (privilege escalation) and CVE-2024-21893 (server-side request forgery).
- Ivanti said that CVE-2024-21893 was also exploited in the wild. Neither the company nor Volexity, Mandiant, or other security firms linked this zero-day to the Chinese APT or any other threat actor.
- With the release of the firmware updates, the company also updated its mitigations file.
- Ivanti also told customers to factory reset their devices before applying the firmware patch, as a way to prevent attackers from remaining on infected devices.
- The company's firmware update covers only recent Connect Secure versions, and patches for older versions are scheduled for the coming weeks.
- The same vulnerabilities also affect Ivanti Policy Secure network gateways, although no attacks have been reported against these systems so far.
- In light of the Ivanti update, CISA has told federal agencies to disconnect affected Ivanti instances from their networks by Saturday, February 3. Agencies are allowed to reconnect devices only if they've been factory reset and updated according to Ivanti's instructions.
Breaches, hacks, and security incidents
Ripple founder hacked: A threat actor has hacked and stolen $112.5 million worth of crypto-assets from Chris Larsen, the co-founder and executive chairman of the Ripple (XRP) cryptocurrency. Larsen confirmed the hack and said that only personal accounts were affected. Even if Ripple Labs accounts were not affected, Ripple's price dropped 5% in the aftermath of the hack. [Additional coverage in CoinTelegraph]
Binance leak: Congratulations to Binance for leaving sensitive source code and internal passwords exposed on GitHub for months. [Additional coverage in 404 Media]
GAC data breach: The Canadian government is investigating a security breach at its foreign affairs department. A spokesperson for Global Affairs Canada (GAC) says the agency has restricted remote access to some of its networks following the detection of "malicious cyber activity." The breach took place on January 24 and impacted the department's network across Canada. Overseas embassies and consulates are not affected. [Additional coverage in The Canadian Press]
Mexico government hack: A threat actor has breached the account of a Mexican government employee and has stolen the personal details of 263 journalists. The hacker is believed to have stolen data such as names, home addresses, and copies of passports and voter ID cards. Government officials say the breach took place on January 22 and impacted journalists accredited to attend the President's daily press conferences. [Additional coverage in Reuters]
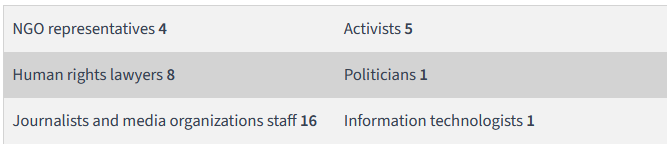
Pegasus in Jordan: Researchers from AccessNow, CitizenLab, and HumanRightsWatch have found traces of the Pegasus spyware on the smartphones of 35 individuals in Jordan. Targeted victims include journalists, political activists, civil society members, and human rights lawyers. The earliest infections date back to March 2021, while the latest was in October 2023. Researchers say Pegasus was installed using PWNYOURHOME, FINDMYPWN, FORCEDENTRY, and BLASTPASS, all known zero-click exploits linked to the NSO Group, the spyware's maker.
General tech and privacy
Uber GDPR fine: American ride-hailing and food delivery company Uber was fined €10 million by the Dutch data protection agency for breaking the EU's GDPR rules. The agency says Uber made it unnecessarily complicated for drivers to see how their data was used, shared, and where. Besides Dutch drivers, the agency says it received complaints from France as well.
M365 Rust rewrite: Microsoft is hiring engineers to help it rewrite its Microsoft 365 platform in Rust as part of an effort to modernize its services.
CAA for S/MIME: The CA/Browser Forum has voted to require certificate authorities to support Certification Authority Authorization (CAA) for S/MIME certificates.
Fastly moves to BoringSSL: CDN provider Fastly has migrated from OpenSSL to BoringSSL.
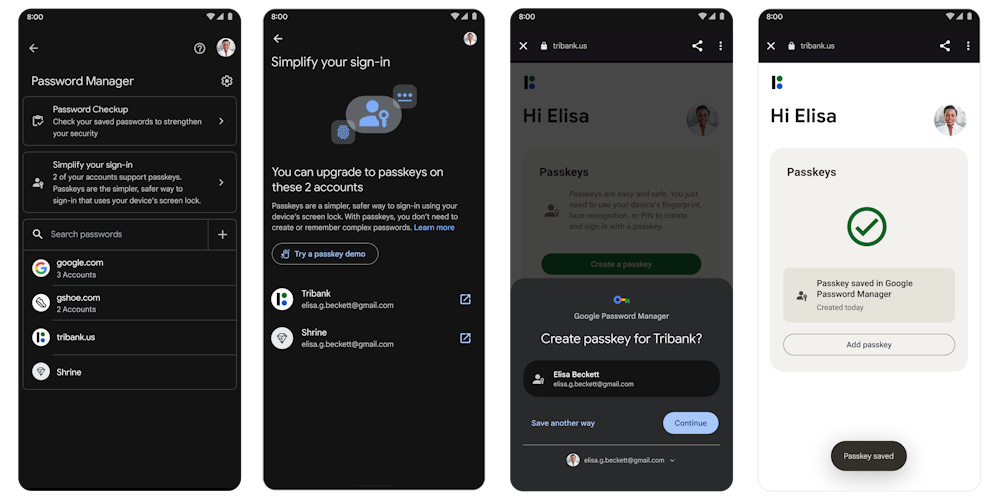
Pixel passkey upgrade: Google has updated the built-in password manager on its Pixel smartphones to scan saved accounts and tell users which online services support passkeys. If passkey-compatible accounts are found, the Pixel Password Manager will prompt users to add passkeys to the accounts just by tapping a few buttons.
Government, politics, and policy
Children Online Safety Senate hearing: The CEOs of Discord, Meta, Snap, Twitter, and TikTok testified in front of a US Senate Judiciary Committee on how they protect children on their platforms. Let's just say all five got an earful from the present Senators since the platforms have done a terrible job so far. [Additional coverage in CNBC, The Record]
CISA SbD alert: CISA has asked SOHO router vendors to overhaul procedures and take security features into account when designing new products. The agency has urged vendors to include a firmware update mechanism in their routers and ship devices that have security features enabled by default. In addition, the agency also asked vendors to ship routers where the web management interface is only accessible from the internal LAN. CISA's requests are part of its Secure-by-Design initiative and were published on the same day the US disrupted a Chinese botnet of compromised SOHO routers.
White House OS3I report: The Biden Administration has published its year-in-review report covering the Open-Source Software Security Initiative (OS3I), a crucial component of its new National Cybersecurity Strategy. The 7-page document aggregates all of OS3I's efforts last year to secure open-source software and its impact on software supply chains.
SEC cybersecurity rules: The White House has told the Senate that President Biden would veto any attempts to walk back the SEC's new cybersecurity rules. [Additional coverage in The Record]
GAO ICS ransomware report: A GAO report found that federal agencies for critical sectors like manufacturing, energy, healthcare, and transportation systems are mostly blind to how companies in their industry vertical can deal with a ransomware attack. [Additional coverage in CyberScoop]
EUCC launched: The EU has formally launched the European Common Criteria-based cybersecurity certification scheme (EUCC), a cybersecurity certification framework for ICT (Information and Communication Technology) products, such as routers and other electronics. The scheme is based on the Common Criteria international standard.
EU commits to not pay ransoms: During a visit to Washington this week, EU Commissioner Thierry Breton formally committed the EU and its 27 member states to the Counter Ransomware Initiative. As part of this project, member states have pledged not to pay ransoms to cyber criminals extorting companies. More than 50 countries across the world pledged to support the project, although none have passed laws officially banning ransom payments yet.
EU-US cybersecurity cooperation: The EU and US had a meeting in Brussels to enhance their cooperation in cyberspace
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Bradon Rogers, Chief Customer Officer at enterprise browser Island, on how a modern enterprise browser solution like Island can be used to replace, complement, or enhance some enterprise security tools or technology stacks.
Cybercrime and threat intel
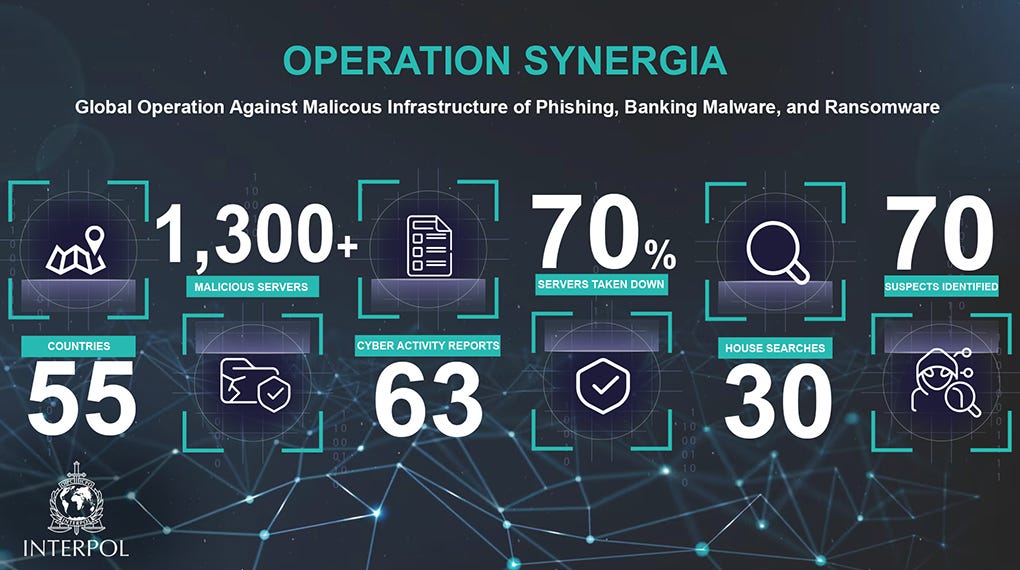
Operation Synergia: Interpol has detained 30 individuals as part of a global operation against malicious server infrastructure that enabled phishing, ransomware, and banking malware operations. The arrests took place between September and November 2023 and were part of Interpol's Operation Synergia. Twenty-six suspects were detained across Europe, and another four in South Sudan and Zimbabwe. According to Group-IB, Interpol and national security agencies managed to take down 70% of the servers they initially targeted.
DraftKings hacker sentenced: A New York judge has sentenced a 19-year-old from Wisconsin to 18 months in prison for his role in hacking user accounts on sports betting website DraftKings. According to prosecutors, Joseph Garrison used credential-stuffing attacks to take over accounts and then steal user funds. The teenager hacked more than 60,000 DraftKings accounts and stole $600,000 from around 1,600 of the site's users. Days before Garrison's sentencing, US authorities arrested and charged two other suspects involved in the attacks. The two helped Garrison sell the hacked accounts on their online cybercrime shops.
BTC-e arrest: The US Department of Justice has charged a Belarusian and Cypriot national for his role in operating BTC-e, a now-defunct cryptocurrency exchange that helped launder ransomware proceeds. Aliaksandr Klimenka, 42, was arrested in Latvia on December 21, 2023, and extradited and arraigned in a US court this week. He faces up to 25 years in prison on money laundering charges and for operating an unlicensed money services business. Klimenka is the second BTC-e operator to be detained after Russian national Alexander Vinnik, the platform's founder. Vinnik was detained in Greece in 2017 and extradited to the US in 2022.
Pig-butchering leaders arrested: Chinese officials have arrested ten Myanmar nationals who allegedly operated large-scale cyber scam centers in Myanmar's northern Kokang region. The suspects were detained after China issued an international arrest warrant in their names at the start of December last year. All ten are believed to have had leadership roles in running the scam centers, and some were also members of the Kokang Border Guard Force. The suspects were handed over to Chinese authorities on January 30.

Russian mathematician arrested: The FSB has arrested a mathematician named Artem Khoroshilov for launching DDoS attacks against Russian critical infrastructure. [Additional coverage in TASS]
Akira exploits Cisco devices: The Akira ransomware gang is using a four-year-old vulnerability (CVE-2020-3259) in Cisco ASA and FTD devices as a way to breach corporate networks.
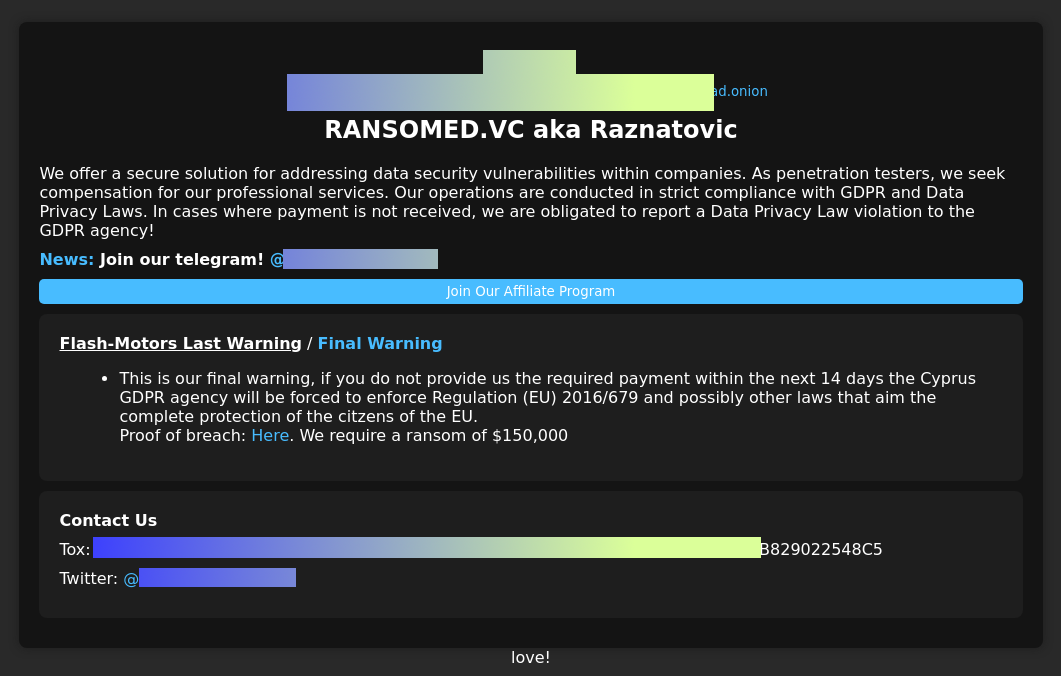
RansomedVC rebrand: The RansomedVC ransomware operation has rebranded under the new name of Raznatovic. The group's name change comes after the gang ruined its brand throughout 2023 after lying about many of its intrusions. RansomedVC's lies reached a peak in October 2023 when American insurance company State Farm was sued in a class-action lawsuit over a breach that never occurred. According to a new report from Analyst1's Jon DiMaggio, the group appears to be run by a Bulgarian national who previously worked as part of the now-defunct Ragnar Locker ransomware operation.
New DaaS project: CyFirma looks at CG, a new Drainer-as-a-Service project that provides access to a phishing kit specialized in compromising and draining cryptocurrency wallets.
ApateWeb: Palo Alto Networks has discovered a network of over 130,000 domains that are being used to deliver scareware, online scams, adware, and rogue browser extensions. The domains appear to be part of a coordinated campaign the company has called ApateWeb. The campaign has been active since August 2022 and appears to be primarily driven by malicious JavaScript code implanted on the compromised domains.
UNC4990: A financially motivated threat actor has been targeting organizations in Italy using a malware strain that spreads via USB devices. Tracked as UNC4990, the group has been active since early 2023. Its primary malware is a downloader EMPTYSPACE (aka VETTA Loader and BrokerLoader), which has been used to later deploy a backdoor named QUIETBOARD and cryptocurrency miners. The group's operations also stand out because of their use of Vimeo and tech news site ArsTechnica to host some parts of their malware.
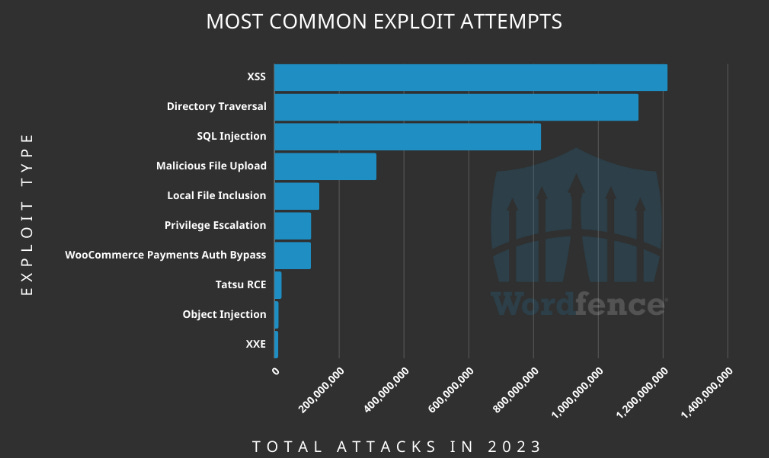
State of WordPress 2023: Credential stuffing attacks have been the most common type of attack against WordPress sites in 2023. WordPress firewall provider Wordfence says it blocked more than 100 billion credential stuffing attempts throughout the year. Scans for exposed configuration files were the second most popular attack vector, while vulnerability exploitation was third. Wordfence notes that 2023 marked the first time that the exploitation of XSS vulnerabilities was the most popular vulnerability type. The company blames this on the rise of more sophisticated payloads designed to insert malicious administrative users and install backdoors via unpatched XSS bugs in themes and plugins.
Malware technical reports
Trigona to Mimic: AhnLab researchers have spotted the operators of the Trigona ransomware installing the Mimic ransomware on compromised MS-SQL servers.
Play ransomware: CyberArk has published a technical analysis of the Play ransomware encrypter.
Nitrogen: Malwarebytes has an update on Nitrogen, a malware spotted last year (Sophos, Bitdefender, eSentire, and Trend Micro), deployed via malicious ads, and used in attacks on corporate networks.
RedLine Stealer: Security researcher Ayush Anand has published a report on a RedLine Stealer sample seen in a recent phishing campaign.
Grandoreiro: ESET has published another technical report on Grandoreiro, the banking trojan they discovered in 2020 and recently helped Brazilian authorities take down.
DiceLoader: Sekoia researchers have published a report on DiceLoader, a malware loader used by the FIN7 cybercrime group.
DIRTYMOE (PurpleFox): Ukraine's CERT team says that more than 2,000 computers across the country have been infected with a malware strain named DIRTYMOE. Also known as PurpleFox, the malware has been active since 2018 but has mainly been active in China. Its operators began expanding in September 2023, when Proofpoint saw the first signs of operations targeting international users. Per Proofpoint's description, PurpleFox appears to be a MaaS.
"Proofpoint does not attribute all the Chinese-themed malware campaigns to the same threat actor at this time, but some activity clusters do overlap, suggesting threat actors may be using the same infrastructure to deliver multiple malware families."
FritzFrog: Akamai has discovered a new variant of the FritzFrog botnet that has now incorporated exploits for the Log4Shell vulnerability.
Commando Cat: Cado Security has discovered a new cryptomining botnet named Commando Cat that is currently targeting Docker servers. The botnet targets Docker instances that have their API endpoints exposed online. Once they compromise a host, the attacker escapes the container and runs malicious code on the underlying Docker host.
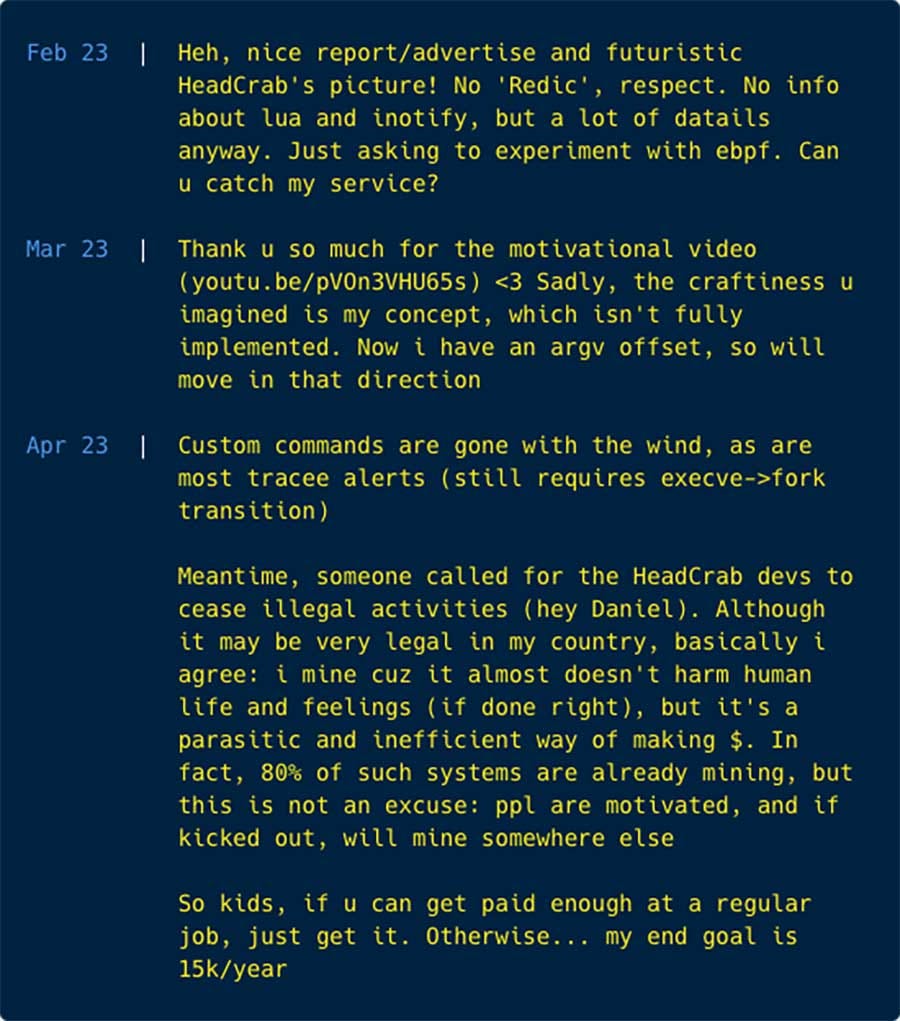
HeadCrab 2.0: AquaSec researchers have discovered a new version of HeadCrab, a crypto-mining malware strain known to infect Redis databases. The new version features fileless execution capabilities and a new command and control system. In addition, the malware's author also seems to be running a mini-blog in the malware's code (screenshot below).
Sponsor Section
Island is an enterprise browser that embeds access policies, data protection, and security controls to create a safe environment that works on unmanaged as well as managed endpoints. Take a look at Island's essential features below [PDF].

APTs, cyber-espionage, and info-ops
Patchwork's VajraSpy: ESET researchers have found 12 malicious Android apps containing a remote access trojan named VajraSpy. The company linked the apps to Patchwork, a Pakistani APT group. According to ESET, some of the apps managed to reach the Google Play Store, where they were downloaded more than 1,400 times. All apps are still available on third-party Android app stores. ESET identified 148 victims across both India and Pakistan.
Scaly Wolf: Security firm BI.ZONE is tracking a new threat actor named Scaly Wolf and its attacks on Russian organizations using phishing emails disguised as government communications. The final payload in these attacks is White Snake, an infostealer advertised on Telegram and used in a bunch of campaigns all over the place. The group appears to have been active since June 2023. BI.ZONE has not made any attribution about the threat actor yet.
"Continuing to distribute the White Snake stealer almost continuously, the group began to pose a serious threat to Russian businesses. Moreover, the fact that attackers send emails over and over under the guise of government services, especially the Investigative Committee of the Russian Federation, indicates the existence of a working scheme and the success of the ongoing campaigns. Judging by the attacks already committed in January 2024, Scaly Wolf will continue to attempt to compromise Russian companies and may not leave this field for quite some time."
APT28: Security firm Harfang believes that Russian cyber-espionage group APT28 is using a network of compromised Ubiquiti devices to proxy and hide its attacks against government organizations across Eastern Europe. Another report from security firm Trend Micro delves into APT28's (which they call Pawn Storm) use of a Net-NTMLv2 hash relay attack exploiting an Outlook vulnerability tracked as CVE-2023-23397. These attacks were first documented by Microsoft in this report last December.
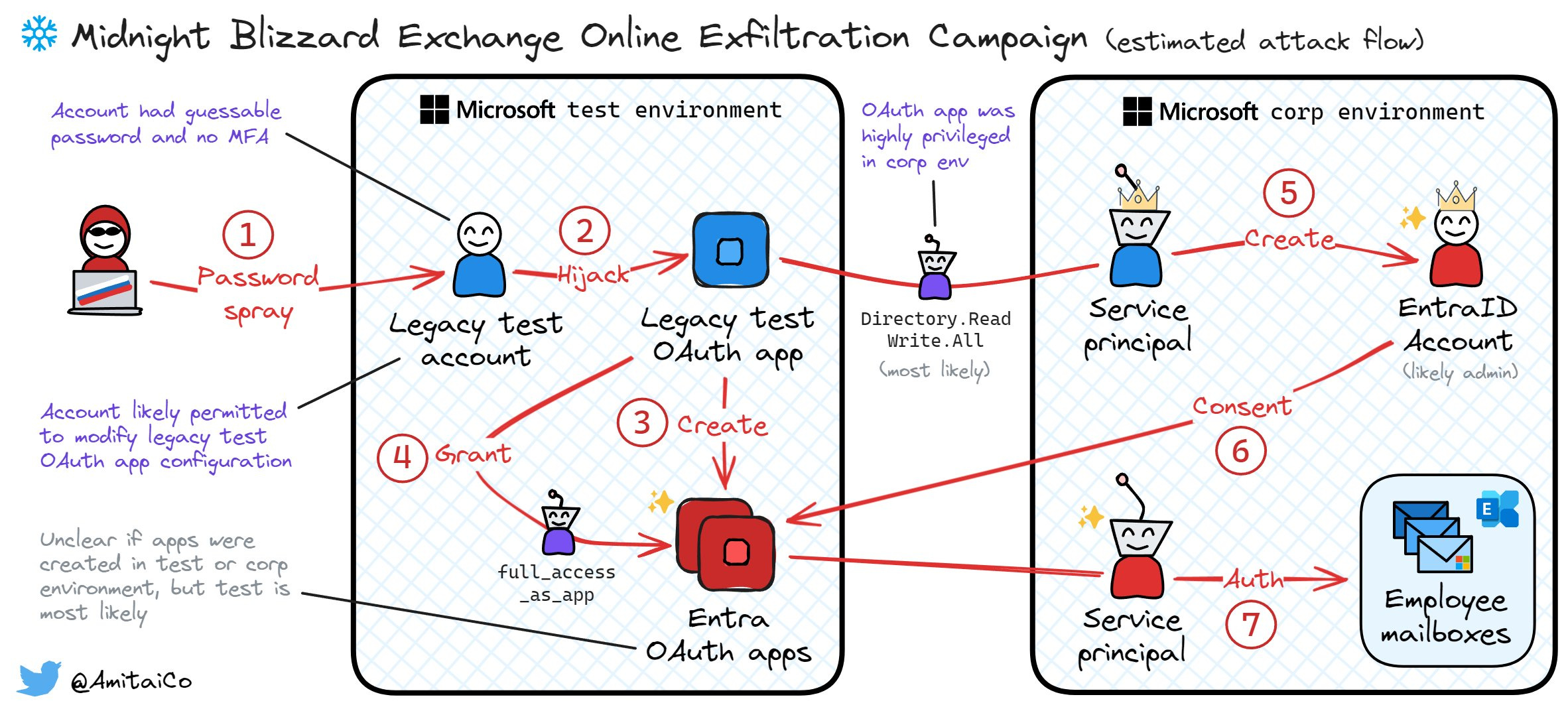
Midnight Blizzard's attack flow: If you're having problems understanding how Midnight Blizzard (APT29) breached Microsoft's internal corporate email, Wiz researcher Amitai Cohen has you covered.
Volt Typhoon: In our last newsletter edition, we featured a Reuters exclusive about the US government's efforts to take down hacking infrastructure owned by Chinese APT group Volt Typhoon. The FBI and DOJ officially confirmed this on January 31. As we suspected, the two agencies obtained court orders to take down Volt Typhoon's infamous KV botnet. The top heads of the FBI, CISA, ODNI, and the NSA also appeared in a Senate hearing that discussed China's hacking campaigns targeting US critical infrastructure—embedded below. On the same day, German security firm DCSO also published a technical report on one of the KV botnet's clusters.
Vulnerabilities, security research, and bug bounty
Mastodon security update: The Mastodon project has released a security update to patch a security flaw tracked as CVE-2024-23832.
WordPress security update: The WordPress team has released a security update for the WordPress CMS that fixes two minor vulnerabilities.
Kubernetes security update: Google has released a security update for its Kubernetes engine.
iOS bug exploited in the wild: CISA says that a threat actor is exploiting an old 2022 vulnerability to compromise Apple devices. Tracked as CVE-2022-48618, the bug was initially patched in December 2022 but was listed in Apple's actual security advisories this year on January 9. Apple says it received a report that the vulnerability was exploited against versions of iOS released before iOS 15.7.1.
Linux vulnerabilities: Qualys security researchers have discovered a severe vulnerability in the GNU C Library (glibc) that impacts Linux operating systems. Tracked as CVE-2023-6246, the vulnerability affects major distros such as Debian, Fedora, Red Hat, and Ubuntu. The bug impacts versions going back to August 2022 and is an elevation of privilege flaw that can allow attackers with access to a system to get root access on the compromised host.
Vision Pro security update: Three days before its official launch, Apple has shipped the first security update for its Vision Pro VR headset. It's a fix for a WebKit zero-day (CVE-2024-23222) the company patched last week and, which it ported to its new device as well. [h/t Simon Tsui]
Leaky Vessels vulnerability: DevSecOps company Snyk has found four vulnerabilities in Linux-based container deployment tools such as Docker and RunC.
Apache OfBiz vulnerabilities: SecureLayer7 has published root cause analysis reports for several Apache OfBiz vulnerabilities, including one recently abused by the Syssrv botnet.
TP-Link vulnerability: CyFirma has published an analysis on CVE-2024-21833, a vulnerability in TP-Link's Archer and Deco router series discovered by JPCERT/CC.
MySQL RNG issues: The MySQL database—and its MariaDB offshoot—uses a weak RNG function that returns low entropy random numbers with predictable sequences.
EventLogCrasher zero-day: ACROS Security has published a micro-patch for an unpatched vulnerability that can crash the Windows Event Log on local or remote systems. The company provided a micro-patch after Microsoft declined to patch the issue. There are arguments this bug could be used to hide malicious behavior on already-compromised systems.
Infosec industry
Proofpoint layoffs: Proofpoint is laying off 280 employees, representing roughly 6% of its global workforce. The company becomes the latest cybersecurity vendor to lay off employees over the past few months after Splunk, Truesec, Malwarebytes, Secureworks, and Rapid7.
Okta layoffs: Identity provider Okta announced plans to lay off 400 employees, representing 7% of its staff. The company fired another 300 employees exactly a year ago, on February 1, 2023. [Additional coverage in CybersecurityDive]
Avast/AVG stop working in Russia: The free versions of the Avast and AVG antivirus programs have stopped working for Russian users. The company announced its intention to stop catering to the Russian and Belarusian markets in March 2022, shortly after Russia's invasion of Ukraine. Avast's CCleaner app also stopped working as well.
New tool—SmuggleFuzz: Security researcher Charlie Smith has released a free tool named SmuggleFuzz, an HTTP/2-based downgrade and smuggle scanner.
New tool—CSS Canarytoken: Thinkst has launched a new version of its Cloned Website Canarytoken. The new version works via CSS, and just like the first JS-based version, it can help website owners when attackers are attempting AitM phishing attacks against one of your domains.
Tool update—ANY.RUN: The ANY.RUN platform now supports running and analyzing Linux malware.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how the war in Ukraine is showing how useful mobile devices are in a war. Using them is risky, but those risks need to be managed.




