Iran: Fake It Till You Make It
PLUS: In China, You're Under Arrest! Because… Reasons!
Your weekly dose of Seriously Risky Business news is written by Tom Uren, edited by Patrick Gray with help from Catalin Cimpanu. It's supported by the Cyber Initiative at the Hewlett Foundation and founding corporate sponsor Proofpoint.

Some interesting research has been published lately on cyber-enabled influence operations. Unsurprisingly, different countries — Iran, China, and even the UK — are taking different approaches here.
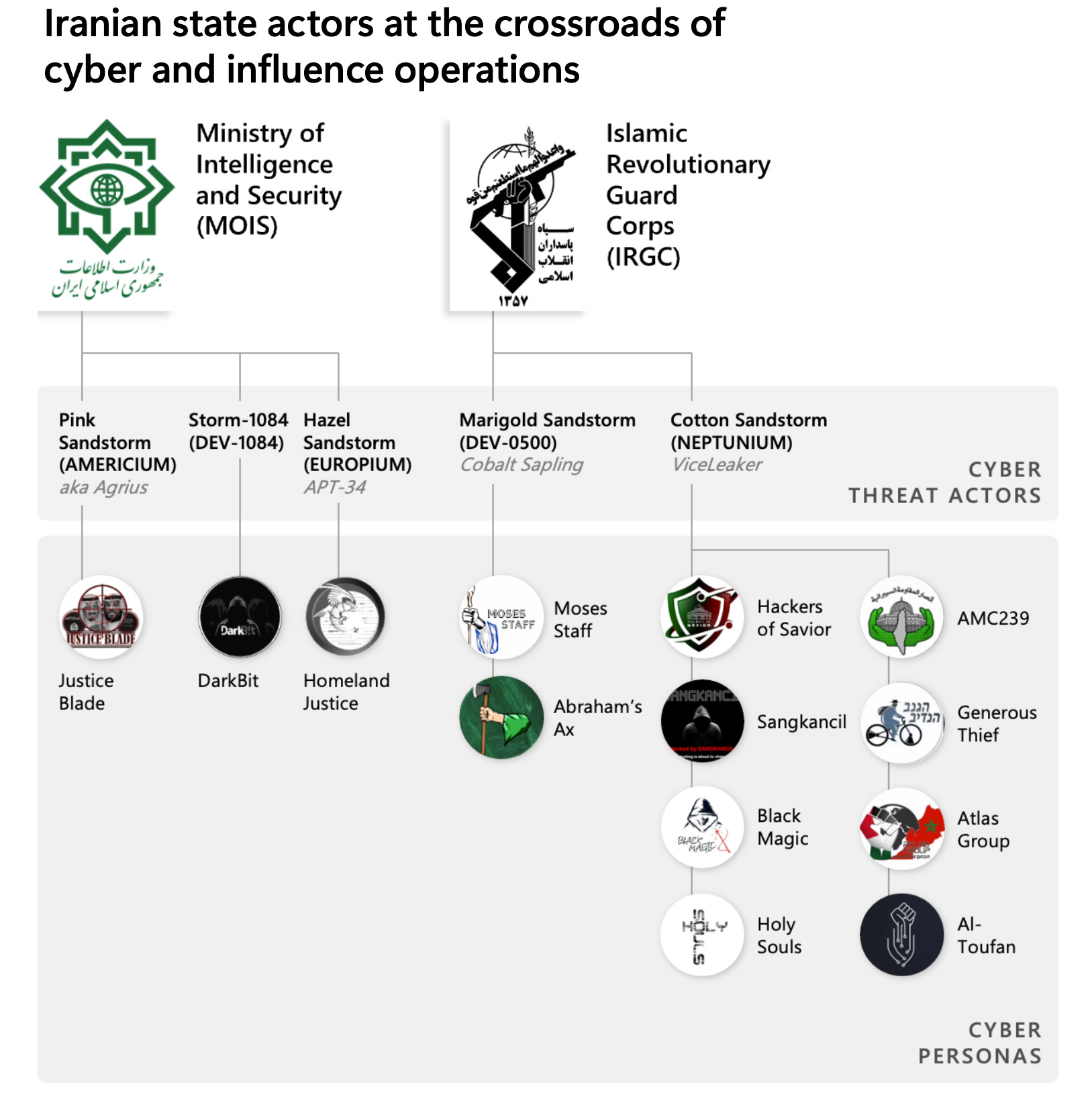
Firstly, Iran is taking a "fake it till you make it" approach. A Microsoft Threat Intelligence report this week describes how the new standard practice for Iranian state actors is to combine cyber operations with influence operations in what it calls "cyber-enabled influence operations".
Microsoft defines these types of operations as ones that combine "computer network operations with messaging and amplification in a coordinated and manipulative fashion to shift perceptions, behaviours, or decisions by target audiences to further a group or a nation’s interests and objectives". An operation might include, say, a website defacement coupled with publication and amplification on social media such as Telegram and Twitter.
The report describes a significant uptick in these operations over recent years — just seven in 2021 but 24 in 2022 and not showing any signs of slowing down in 2023.
Microsoft thinks that this shift is driven by the desire to get the biggest bang for the buck out of cyber operations and even to "compensate for shortcomings in their network access or cyberattack capabilities".
The report notes that the shift in Iranian tradecraft seems to be a response to similar attacks against Iran. An anti-Iran group Edaalate Ali, for example, attacked Iran's notorious Evin prison and released dramatic CCTV footage showing prison surveillance monitors hacked to display a protest image.
Some months later, Iranian operators disrupted Albanian police systems and leaked CCTV footage of an Albanian border crossing. (This was apparently payback for a police raid on Iran's embassy in Tirana, Albania.)
Unlike the Edaalate Ali incident, however, the CCTV leak didn't make much of a splash. Video footage of bored guards noodling about on their smartphones is about as exciting as bus travel. So they managed to make a steak, but there was absolutely zero sizzle.
The report also provides examples of several other retaliatory strikes that lacked the necessary pizzazz.
Despite that, Microsoft says Iranian capabilities are improving across both cyber and influence operations. The report cites Iran's increasingly rapid adoption of n-day vulnerabilities, custom tooling and the use of victim websites for C2 as examples of improving capabilities. They're also embracing tools like mass SMS messaging on the influence side.
Iran is also tying its destructive attacks to influence operations. Recent attacks that targeted on-prem and cloud environments that we wrote about in recent weeks were coupled to "messaging encouraging action in response to Israel's policies towards Palestinians".
Microsoft calls this destructive "probable Iranian group" Storm-1084, and although the report doesn't explicitly say it, a diagram in the report links this group to the Iranian Ministry of Intelligence and Security (MOIS).
Meanwhile, in China…
By contrast, an ASPI report released last week describes how the PRC's influence operations appear to be intended to push government narratives rather than amplify the impact of cyber operations.
Many of the narratives the report describes are cyber-related, but they don't rely on or amplify the output of the PRC's cyber operations. For example, one of these narratives promotes the concept of "US cyber hegemony" and asserts that the US government is irresponsibly conducting cyberespionage operations targeting China and other countries. The report speculates that these narratives are to "support the expansion of Chinese cybersecurity services into Southeast Asian markets" and also to counter or blunt accusations of voracious Chinese cyberespionage.
The report doesn't find strong evidence for links between Chinese APT groups and these influence campaigns, which probably makes sense given the CCP already has an extensive apparatus for information control. Why task cyber operators with social media manipulation if you've already got several bureaucracies with that function already?
Additionally, PRC cyber espionage groups are already kicking goals and satisfying government priorities. They don't need to embiggen their own operations to look good.
And in the Land of Crumpets:
When it comes to the UK, this newsletter examined the National Cyber Force's recently published "Responsible Cyber Power in Practice" document describing its approach to cyber operations. These operations are described as offensive cyber operations, ones that disrupt, deny, degrade, destroy, rather than as influence operations, but the NCF's "doctrine of cognitive effects" really describes a way of working that influences people's thinking and, therefore, their actions.
But in contrast to Iran and China, these influence operations are carried out by manipulating computer systems close to the target rather than the mass media. James Babbage, the head of the country's National Cyber Force, told The Economist it doesn't engage in large-scale social media manipulation.
"The wider our audience, the more critical it is that what we're putting out is true," he said. "And so our currency really is the truth."
The NCF describes its operations as "accountable, precise, calibrated and therefore proportionate".
Even leaving aside whether the ultimate goals of these different countries' operations are justifiable, the UK's approach here is the most appealing because it deceives the fewest number of people.
To us, speaking as a bunch of decadent westerners committed to luxuries like human rights and truthful government, the UK's approach seems like the sensible one. It's controlled and measurable and — in our view — has the highest chance of success because its objectives have to be narrowly defined.
Still, watch this space. China and Iran will learn from each other and probably from the West, too. This will remain a moving target.
In China, You're Under Arrest! Because… Reasons!
The PRC has broadened the scope of its counter espionage law to include cyber espionage and cover a wider range of information. To us, this looks less like a law designed to control espionage and more like a law designed to restrict the free flow of information.
Article 4(e) of the law now includes both network intrusions and also disruptions:
Network attacks, intrusions, obstructions, control, or disruptions targeting state organs, units involved with secrets, or critical information infrastructure that are carried out, prompted, or funded by a espionage organization and its agents, or carried out by agencies, organs, individuals, or other collaborators domestically or outside the PRC borders;
Article 36 deals with response to reporting and response and "relevant departments" can "order the telecommunications operators or internet service providers to promptly employ measures such as repairing vulnerabilities, solidifying network protections, stopping transmission, deleting programs or content, suspending related services, removing related applications, or closing relevant websites, and store the related records".
This part feels a bit like Australia's critical infrastructure law that allow for government intervention when the proverbial hits the fan, although Australia's laws are limited to just critical infrastructure. So it's not entirely different to laws we might recognise.
But, as this newsletter has discussed before, it's not so much the laws themselves, but rather how they are applied and what they are intended to achieve.
Then there are the less familiar-feeling parts of the new law. For example, it contains very broad definitions of what "acts of espionage" actually are, and what type of material is covered by the law:
Activities carried out, instigated or funded by foreign institutions, organizations, and individuals other than espionage organizations and their representatives, or in which domestic institutions, organizations or individuals collude, to steal, pry into, purchase or illegally provide state secrets, intelligence, and other documents, data, materials, or items related to national security, or in which state employees are incited, enticed, coerced, or bought over to turn traitor.
You'll note "related to" (bolded by us above) is not defined. It's hard to see how a due diligence firm, for example, could avoid falling afoul of this type of law. It gives the government a very broad brush to apply the law in a discretionary way. Do what we want or else, basically.
The law comes into effect on July 1, but foreign firms researching Chinese business conditions are already facing troubles, including having their offices closed and staff detained.
This is a good example of the PRC government's willingness to use coercive tactics to pursue its perceived national security goals — even if it means trampling over business interests.
Three Reasons to be Cheerful this Week:
- Faster Security Updates for Apple devices: Apple rolled out its first "Rapid Security Response" software update this week. RSR is a way to more quickly roll out security updates to user devices rather than waiting for an overall OS update. Apple's announcement also states that they may be used to mitigate security issues being exploited in the wild.
- Compromised networks detected faster: three separate cyber security firms have now reported that the "dwell time", the length of time that attackers spend within a compromised network before being detected, has declined to just weeks. A Sophos report this week indicated dwell time had declined to 10 days, while previously Mandiant reported 16 days and Secureworks 11. We are choosing to believe this is good news, although Sophos rightly points out this depends on how you interpret the data. The proliferation of ransomware could be driving dwell time down because the whole point is literally to get noticed in a big way, but they also point out that non-ransomware dwell times declined from 34 days to 11 as well.
- Google disrupts CryptBot malware operation: Google announced it had launched litigation against distributors of the CryptBot infostealer and a New York court has granted a temporary restraining order that allows it to take down current and future domains tied to the distribution of CryptBot. [more on Risky Biz News].
Sponsor Section
Seriously Risky Business is supported by the Hewlett Foundation's Cyber Initiative and corporate sponsor Proofpoint.
Tines No-code Automation For Security Teams
Risky Business publishes sponsored product demos to YouTube. They're a great way for you to save the time and hassle of trying to actually get useful information out of security vendors. You can subscribe to our product demo page on YouTube here.
In this video demo, Tines CEO and co-founder, Eoin Hinchy, demonstrates the Tines automation platform to host Patrick Gray.
Shorts
It's Not Dumb if it Works, Tyranny Edition
A report from Lookout's Threat Lab documents a new Android surveillance tool named BouldSpy that is deployed in Iran. The interesting thing here is that Lookout believes Iranian law enforcement install the malware on devices when the owner is detained. Data recovered from BouldSpy's C2 server indicates that initial infection occurs close to police stations, border checkpoints, and other locations where device access could be used to install the malware.
This isn't the first time this kind of thing has happened. In the PRC's Xinjiang province ethnic Uyghurs have had phones confiscated and subsequently returned with spyware installed.
Juice Jacking? Seriously?
Ars Technica has a good write up on how recent US government warnings and subsequent media reporting have resulted in a circle of fear mongering over the threat of "juice jacking". Juice jacking is the idea that mobile devices may be compromised when they are plugged into malicious chargers in public places such as airports. The conclusion:
What this means is that state and federal authorities and hundreds of news outlets — none of them with any expertise in cybersecurity — have generated a continuous feedback loop. This vicious cycle has done little more than scare the public into eschewing charging stations when there’s wide consensus among security professionals that there’s no reason for anyone other than high-asset targets of nation-states to do so.
It's always been weird that so many governments publish advice on this when, to the best of our knowledge, it isn’t really a thing.
Mandia's Top Tip: Know Thyself
At last week's RSA Conference, Mandiant's CEO Kevin Mandia provided seven pieces of advice for cyber defence. We are particularly struck by his first tip to "mine institutional knowledge". He said "you should know more about your business, your systems, your topology, your infrastructure than any attacker does".
This is exactly the same point that NSA's Rob Joyce made in 2016 at the Usenix conference when he was head of Tailored Access Operations (NSA's hacking operations).
"We put the time in ...to know [that network] better than the people who designed it and the people who are securing it," Joyce said. "You know the technologies you intended to use in that network. We know the technologies that are actually in use in that network. Subtle difference. You'd be surprised about the things that are running on a network vs. the things that you think are supposed to be there."
Making the Cyber Safety Review Board a Fixture
The US government is working to establish the CSRB via legislation. This will mean ongoing funding and subpoena power to compel victims to speak honestly. We think the board's reports so far have proven the concept although the effort will no doubt continue to evolve over time.
US Gov Missed Solar Winds Detection Opportunity
Speaking of incident reviews, Wired reports that the US Department of Justice detected early signs of the SolarWinds breach nearly six months before the significance was realised. The DoJ found unusual traffic from a trial version of SolarWind's Orion software in May 2020 but an investigation at the time didn't uncover the supply chain hack. The scope of the whole incident was subsequently discovered in December 2020.
Not only did the DoJ detect something, other security firms also had indications that something was amiss with Orion. What are the steps that should be taken to avoid these kinds of missed opportunities in future? Presumably there was a classified government review here. If there was, we'd love to see a declassified version so we can see what the lessons were. If there wasn't, well… that's something to think about, isn't it?
CIA Deputy Director Justifies 702
In a recent Lawfare podcast CIA Deputy Director David Cohen spoke about the value of the intelligence gathered using Section 702 of the US's Foreign Intelligence Surveillance Act in an unusual amount of detail. This section allows US intelligence agencies to compel service providers to help conduct targeted surveillance of foreigners outside the US and will expire at the end of the year unless Congress renews it.
Cohen says information gathered under 702 is: used to identify and protect against cyber operations from China, Russia, Iran and North Korea; used in efforts to prevent US technology being acquired by adversaries for weapons systems; used to uncover atrocities committed by Russia in Ukraine, including the murder of noncombatants, the forced relocation of children from Russian-occupied Ukraine to Russia, and the detention of refugees who were trying to flee violence; used to identify foreign spies and protect US ones; and also produced intelligence on foreign drug cartels illuminating their networks and global supply chains.
Merck 2: Insurers 0
A New Jersey court has upheld a previous ruling that insurers should cover pharmaceutical company Merck for losses sustained in the NotPetya attack.
Risky Biz Talks
In addition to a podcast version of this newsletter (last edition here), the Risky Biz News feed (RSS, iTunesor Spotify) also publishes interviews.
In our last "Between Two Nerds" discussion Tom Uren and The Grugq discuss listener feedback and come up with even more reasons it is hard to deter cyber operations.
From Risky Biz News:
Hacker exposes 986 Bitcoin addresses operated by Russian intelligence agencies: A suspected hacker has exposed 986 Bitcoin addresses allegedly operated by Russia's three main intelligence services—the Foreign Military Intelligence Agency (GRU), Foreign Intelligence Service (SVR), and Federal Security Service (FSB).
The hack and subsequent leak were discovered by blockchain analysis company Chainalysis. The company believes the hacker gained access to the private keys of several GRU wallets.
[This is well worth reading and much more on Risky Biz News]
AT&T cryptocurrency hacks: A hacker group is exploiting an API vulnerability in AT&T's system to gain access to customer email addresses in order to hijack cryptocurrency exchange accounts. AT&T has confirmed the attacks. The company told TechCrunch the API vulnerability allowed the hackers to generate "secure mail keys" that granted access to any user email without needing to know the account's password. TechCrunch's source claims the `hackers have used their access to steal between $15 and $20 million—although this could not be independently confirmed at the time of writing.
Apple and Google release new spec to combat the use of Bluetooth devices for unwanted tracking: Apple and Google have put forward a new technical specification that aims to combat the misuse of Bluetooth devices (such as AirTags) for unwanted tracking.
The new spec introduces a universal interface that can detect when a Bluetooth device keeps following a smartphone or tablet and show an alert warning the owner of potentially unwanted tracking.
[much more on Risky Biz News]



