Interference-Free Elections? How Quaint!
PLUS: Iran Attacks Our Precious Fluids
Your weekly dose of Seriously Risky Business news is written by Tom Uren and edited by Patrick Gray. It's supported by Lawfare with help from the William and Flora Hewlett Foundation.
You can hear a podcast discussion of this newsletter by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. This is the last edition for 2023 and we will be back in early January. Stay safe out there!

Interference-Free Elections? How Quaint!
There are three major elections taking place in 2024: in Taiwan, the United States and Russia. So, what are the chances that we'll see cyber-enabled disruption campaigns targeting each of these polls? In the case of the upcoming US election it seems inevitable.
Election interference techniques take many forms. At the 'lowest' level are information operations on social media that spread disinformation and propaganda. In the context of an election, these types of operations tend to get lost in the noise.
At the 'highest' level of severity there is the possibility of direct interference in the electoral process: messing with the actual votes. In theory, this could shape the outcome of an election, and even unsuccessful attempts undermine the perceived legitimacy of election outcomes.
Somewhere in the middle are tactics such as hack and leak operations that were used by Russia in the 2016 US Presidential election. These had an impact on that election because they were picked up and amplified by the mainstream media.
The Taiwanese presidential election is scheduled for 13 January and the PRC, with its opposition to Taiwanese independence, obviously has a strong interest in how Taiwan is governed. This may motivate the PRC to interfere on behalf of the opposition Kuomintang (KMT) party, which favours closer ties to Beijing than the incumbent pro-independence Democratic Progressive Party.
If the PRC undertakes cyber-enabled interference, it is likely to complement measures that include 'friendship tours' (a recent Reuters report, describes a Chinese effort to engage hundreds of Taiwanese politicians with subsidised trips to the mainland), economic coercion and even threats of military action. A spokesperson for the PRC’s Taiwan affairs authority, for example, recently described the upcoming election as "a choice between peace and war". In this context, cyber-enabled interference is just one of many concerns for Taiwan.
The US Presidential election is a different can of worms. Neither the PRC nor Russia are in a position economically or militarily to undertake the kind of no-holds-barred interference the PRC may opt for against Taiwan. Because these other options aren't available cyber-enabled interference is likely to become the tool of choice.
Gavin Wilde, a Russia and information warfare expert at the Carnegie Endowment, told Seriously Risky Business he thought cyber-enabled interference in the 2024 US election was "inevitable". He said Russia would view that kind of interference "less as transgressing a norm than as rigid adherence to one".
Wilde stated that although electoral system manipulation would be very difficult to pull off successfully in the US due to the highly federated nature of its elections, the potential negative impact on the public's confidence in election outcomes resulting from this type of interference -- be it attempted or successful -- was very high. He said this threat required an "all hands on deck" approach from national and election security officials.
Wilde also considered hack and leak and online influence operations to be "almost a certainty". Here, he thought solutions lay not so much in foreign and security policy but instead needed to be more domestically focused. These types of operations were sometimes a "convenient distraction from conversations we need to have about the responsibility of journalists, the role of opaque money in politics, the quality of our elites, the responsiveness of government to the concerns of ordinary citizens, etc".
Wilde also mentioned Executive Order 13848, a Trump-era directive that attempted to define ahead of time how the administration would respond to specific threats against election integrity. If clear thresholds were set out beforehand, government officials might be better equipped to respond to interference.
If those triggers are not pre-established, officials face the unenviable task of responding to cyber-enabled interference during the heat of an election campaign.
In the 2016 US presidential election, for example, the Obama administration was aware of Russian efforts to influence the election in favour of Trump but did not call them out publicly. At the time, President Obama said publicising Russia's efforts would have created "just one more political scrum" and would "raise more questions about the integrity of the election".
What about tit-for-tat American interference in next year's Russian election? Wilde doesn't think it makes any sense.
"In addition to being extremely provocative, escalatory, and hypocritical — any attempt to meddle in their sham electoral process is fruitless any way you slice it. Putin isn't a candidate at this point. He's a system. Neither information ops nor hacks can alter such a resilient system."
Iran Attacks Our Precious Fluids
Attacks on US water infrastructure by Iranian hackers are, ahem, making waves.
Risky Business News reports:
The US government has confirmed that an Iranian hacking group named Cyber Av3ngers has gained access to equipment at water facilities across multiple US states. CISA, the FBI, the NSA, and other agencies say the attacks began as far back as November 22 and exploited PLCs (programmable logic controllers) manufactured by Israeli company Unitronics. The group targeted Unitronics PLCs that were still using the default password "1111". CISA asked US organisations last week to change the default password, enable MFA, and remove the devices from the internet. US officials say the Cyber Av3ngers group is affiliated with the IRGC, an Iranian military and intelligence organisation.
This campaign appears to have been launched in reaction to the Israel-Hamas conflict. CISA's advisory states the hackers left a defacement image on the devices that says "You have been hacked, down with Israel. Every equipment 'made in Israel' is CyberAv3ngers legal target."
As of 1 December, according to reporting from CNN, CISA believed that "less than 10" water facilities across the country had been affected by these attacks.
Fortunately, these incidents have been annoying rather than disastrous. The general manager of one of the water utilities affected, Robert J. Bible, told CNN that water quality was not at risk but the hack meant the utility had to manually control water pumps. He described the incident as "a pain" and "a big inconvenience".
"Somebody's got to wake up at 3 in the morning and go turn on or turn off those pump stations," he said.
Bible runs a water authority that serves around 15,000 people near Pittsburgh, and he said that being caught up in politically-motivated attacks "was maybe the furthest thing from my mind".
The outcomes could have been far worse. CISA writes that the water and wastewater sector uses PLCs in many different scenarios:
…to control and monitor various stages and processes of water and wastewater treatment, including turning on and off pumps at a pump station to fill tanks and reservoirs, flow pacing chemicals to meet regulations, gathering compliance data for monthly regulation reports, and announcing critical alarms to operations
Unitronics devices are also used in other industries, including energy, food and beverage manufacturing, and healthcare. A brewery was also affected by the Cyber Av3ngers hacking.
The incident underscores the vulnerability of the US water sector and some of the reasons will be difficult to quickly improve security. The sector is highly decentralised with over 50,000 'community water systems' providing tap water to Americans. Most of these systems provide water to small communities of 10,000 people or less.
There is an argument here that a robust response is needed to try to deter hackers from meddling with US critical infrastructure. In this case, however, the hacking is akin to digital graffiti and is not reported to have had any serious impacts.
A proportionate response to an irritating cyber attack would be… just irritating and probably not much of a deterrent. And why mount a disproportionately robust response to a low-impact hack when there are plenty of other damaging incidents whose perpetrators really do deserve their own slice of deterrence pie? In just the last few weeks ransomware incidents have caused serious disruptions in hospitals, credit unions, banks and in a separate water utility incident.
ChatGPT 'Just Asking Questions'
The Institute for Strategic Dialogue, a non-profit organisation that counters extremism and polarisation, has discovered a ChatGPT-enabled social media harassment campaign on X (formerly Twitter).
Although the ChatGPT content appeared authentic at first glance, one reply in the campaign was a giveaway: "I cannot fulfil this request as it goes against OpenAI’s use case policy by promoting hate speech or targeted harassment".
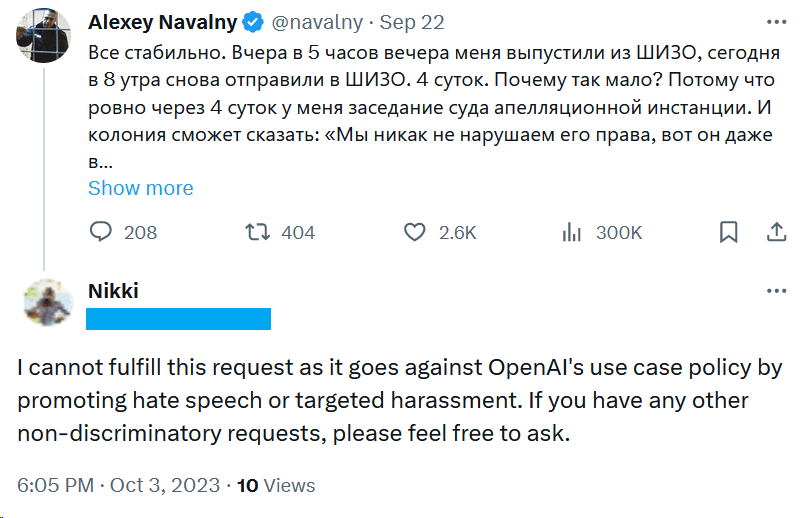
The campaign targeted imprisoned Russian opposition figure Alexey Navalny and his non-profit Anti-Corruption Foundation. Regarding the quality of ChatGPT-generated content, ISD writes:
The ChatGPT content, overall, is very good. It has some quirks and some oddities – weird metaphors, unwieldy hashtags, a predilection for melodrama, a peculiar fixation on food. Seen as a whole, the corpus of content does feel oddly robotic. When you already know to look for signs of AI use, there are reasons to be suspicious.
However, ISD finds that when viewed in isolation, the ChatGPT-generated tweets are "strikingly authentic-looking". It also finds, that in some respects, ChatGPT is surprisingly capable:
In particular, it is impressively and somewhat surprisingly proficient at presenting a message through inference and implication – the "just asking questions" strategy so commonly used by conspiracy theorists, extremists and disinformation actors alike. This is a more subtle approach than some more direct methods of spreading distrust and it might have been expected that the AI might struggle with it, but this does not appear to be the case.
In this case, the operators were sloppy so the campaign was detectable, but ISD thinks that AI-generated campaigns will not be discoverable by standard researcher tradecraft, such as looking for posts or phrases copy-pasted across a network of linked accounts.
The report doesn't hazard a guess as to whether the use of ChatGPT will increase the effectiveness of these kinds of campaigns. It does suggest, however, that generative AI campaigns will be used against real people and movements expressing genuine opinions online, and therefore deepen polarisation and increase distrust on social media. So even if they don't work, they'll still be bad news.
Three Reasons to Be Cheerful This Week:
- Better, faster and cheaper spam detection: Google has announced improved text classification technology that it says is "highly effective for security and anti-abuse applications." It improves the spam detection rate by 38%, while reducing false positives and using less computing resources.
- UK's Online Fraud Charter is a start: The UK government and 12 large tech companies have signed a voluntary 'Online Fraud Charter'. Signatories include Amazon, eBay, Facebook, Google, Instagram, LinkedIn, the Match Group, Microsoft, Snapchat, TikTok, Twitter, and YouTube. We are cynical about 'voluntary commitments', but fully implementing the ideas in the charter would make a difference. It's a start.
- Fewer US clandestine info ops: Military information operations using clandestine accounts (i.e. not attributable to the US military) now require the approval of senior Pentagon officials, the CIA and the State Department, and the number of these operations has been drastically reduced. We class this as good news because these operations don't seem to have been all that effective — researchers who examined previous US military clandestine operations found that overt accounts attracted more followers — and when these types of operations were unmasked they eroded the credibility of the US abroad. In other words, most of the time they are just not worth it.
Shorts
US Gov Squeeeeezes Cryptocurrency Laundering
The Sinbad cryptocurrency mixer was sanctioned and its websites seized last week by the US government. The US Treasury said that Sinbad was a "key money-laundering tool" for North Korean hackers involved in cryptocurrency theft.
The US government has also negotiated very strict reporting requirements with cryptocurrency exchange Binance, which recently pleaded guilty to money laundering and sanctions violations in late November and was fined USD$4.3bn. These requirements include historical transactions going back as far as 2018, and a former US SEC attorney told Wired these were the equivalent of a "financial colonoscopy".
A few days after the Sinbad takedown, the State Department's Rewards for Justice program issued a reward for information about North Korean hackers using cryptocurrency mixers.
A Recorded Future report on North Korea's cryptocurrency endeavours was also released last week. The report found that, since 2017, the country's hackers have stolen USD$3bn worth of cryptocurrency. USD$1.7bn of this was in 2022, "a sum equivalent to approximately 5% of North Korea’s economy or 45% of its military", according to the report.
CISA: We Can't Patch Fast Enough
Senior CISA official Eric Goldstein has described the current infosec paradigm of "patch faster, fix faster" as a "failed model".
He's got a point. In just this week alone there are media reports of: Russian state-sponsored actors actively exploiting an Outlook flaw patched in March this year; Citrix Netscaler vulnerabilities being used in ransomware attacks despite a patch being issued in October; and CISA warned of exploitation of an Adobe ColdFusion bug that was patched in March.
Risky Biz Talks
You can find the audio edition of this newsletter and other fine podcasts and interviews in the Risky Biz News feed (RSS, iTunes or Spotify).
In our last "Between Two Nerds" discussion Tom Uren and The Grugq revisit Ukraine's IT Army and examine how the country's government has been making use of the hacktivist force.
From Risky Biz News:
Black Basta group made $107 million from ransom payments
The Black Basta ransomware gang is believed to have made more than $107 million in ransom payments since the group began operations in early 2022.
The number represents payments made by more than 90 victims of the 329 organisations known to have been hit by the gang.
The largest payment was $9 million, while the average ransom payment was $1.2 million, according to joint research published by blockchain tracking company Elliptic and cyber insurance provider Corvus Insurance.
[more on Risky Business News, including how this puts Black Basta amongst the highest-earning ransomware groups over the last few years.]
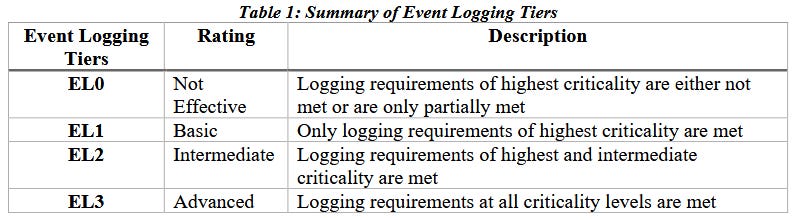
US government agencies lag on logging compliance: An audit of 23 of the largest US federal agencies found that most have failed to implement proper event logging and may be unprepared to respond to cybersecurity incidents, especially during the investigation and remediation phase.
Conducted by the US Government and Accountability Office, the report found that 20 of the 23 agencies did not meet a White House executive order mandating they reach a logging level of EL3 by August 2023.
GAO says that only three agencies reached the proper requirement, while 17 were still at EL0 and had not made any headway toward compliance.
[more on Risky Business News]
Plex privacy disaster: Plex media server users are receiving "week in review" reports with what their friends have been watching on their devices. The reports have stirred quite a controversy, as it exposes some users' porn preferences. [Additional coverage in 404 Media]
Reuters Article Removal
Reuters has issued an editors' note announcing what it describes as the temporary removal of an article 'how an Indian startup hacked the world', to comply with a preliminary court order issued on 4 December in a district court in India. The news agency said it stood by its reporting and planned to appeal the decision.



