In Beijing, the Fourth Amendment Is Still for Sale
PLUS: Ransomware’s Up. And Down? Sideways, Maybe?
Your weekly dose of Seriously Risky Business news is written by Tom Uren, edited by Patrick Gray with help from Catalin Cimpanu. It's supported by the Cyber Initiative at the Hewlett Foundation and this week's edition is brought to you by Airlock Digital.
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. Find this week's edition here and on Apple podcasts:

New legislation in the US designed to combat law enforcement’s use of commercially procured data is welcome, but won't solve the core problem: that this data is being collected and brokered in the first place, including to foreign intelligence services.
The Fourth Amendment is Not For Sale Act will require government intelligence and law enforcement agencies to obtain a warrant before procuring information about US citizens. The US House Judiciary Committee has just given it a stamp of approval, and so onwards it goes towards becoming law.
The legislation would apply to federal, state and local law enforcement agencies and cover information purchased from data brokers, as well as data acquired from leaks or illegitimate hacks.
This Act covers some data sets that could clearly be used in legitimate investigations by agencies. Online criminal forum database leaks, for example, are very useful to law enforcement.
However, we think the principle here—that government agencies should be subject to checks and balances when acquiring data for investigations—is important, regardless of whether the data is purchased, obtained through legal authority, or acquired through other means.
The Act will make obtaining useful data harder for agencies, but we approve of its intent.
One argument we've heard against the proposed changes is that big tech and foreign intelligence services can already access this data, so government agencies should be able to get it too.
We don't buy it. These changes won't prohibit US agencies from acquiring these data sets, it'll just put some checks and balances in place. And when it comes to citizens, US government agencies have coercive powers that companies and other parties just don't have. Meta can't put you in prison, but US law enforcement can.
Commercially available data can now reveal more about a person than information obtained by US law enforcement or intelligence agencies through court orders in the past. But that doesn't mean US lawmakers should let agencies do what they like. Instead they should adjust laws to force agencies to do what is right.
If these changes get pushed through, lawmakers will be tempted to pat themselves on the back and congratulate themselves for a job well done. But the national security impacts resulting from this loose data ecosystem will remain, and it's almost certain that this ecosystem is already being abused by bad actors, including foreign adversaries.
We've noted previously that Chinese cyber espionage groups have already stolen information from the US Office of Personnel Management, Marriott Hotels, United Airlines, Equifax and Anthem. These data sets include security clearance, travel, financial and insurance information. Combining this data with commercially purchased data could paint a rich picture for exploitation.
It's great that this draft legislation is progressing. But the US still needs far more comprehensive data protection measures to address some pretty significant national security risks.
Ransomware’s Up. And Down? Sideways, Maybe?
Two recent reports show that the ransomware ecosystem continues to mutate to counter government and private sector responses to the threat it presents.
Both reports, however, combine ransom payments from both data extortion cases (extorting companies by threatening to release stolen data) and data encryption ransomware into a single top-line figure, and we wonder whether this obscures a significant shift in actor behaviour.
At first glance, the reports appear to contradict each other. Earlier this month, blockchain analysis company Chainalysis reported that ransomware was back with a vengeance with ransom payments on track for the second biggest year ever, with nearly USD$450m extorted through June. This represents a return to 2021 levels, where nearly USD$940 was extorted over the year, after a significant drop in 2022.
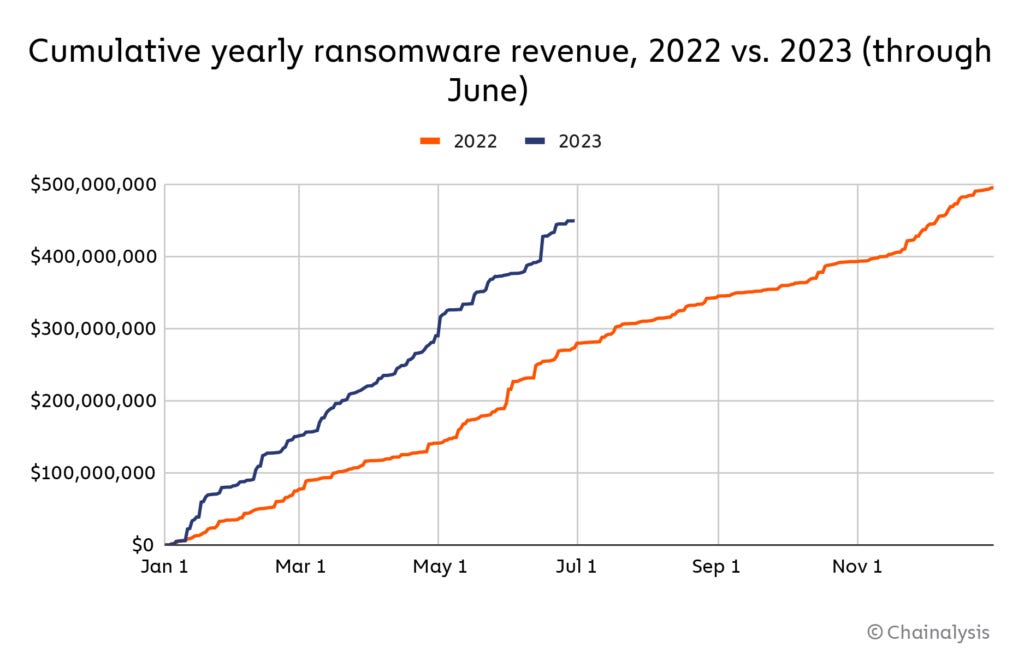
On the other hand, this week ransomware incident response company Coveware reported that ransomware payment rates were down to a record low of 34%. That is, only 34% of victims are paying up. The firm attributed this decline over time to "companies continuing to invest in security, continuity assets, and incident response training".
So… things are getting worse but also better?
Dive into both reports, however, and it appears that although fewer victims are paying, large payments are up.
Chainalysis reports that compared to previous years there are more payments, both smaller and larger. There are a large number of small payments of around USD$300 each that it attributes to the "spray and pray" Dharma and Phobos ransomware strains. At the other extreme, more sophisticated operations such as ALPHV/Blackcat and Cl0p are hitting bigger organisations, where average payments are USD$1.5m and USD$1.7m respectively.
Coveware's data comes from incidents it handles, so it doesn't report on small, low-value ransomware payments. Its report did examine Cl0p's activities in some detail, though. In recent months Cl0p exploited a MOVEit file transfer appliance 0-day to steal customer data from hundreds of firms and has been extorting companies by threatening to publicly release the stolen data.
Here Coveware thinks that Cl0p has responded to low data extortion payment rates (around 30%) by raising ransom demands. Per Coveware:
While the MOVEit campaign may end up impacting over 1,000 companies directly, and an order of magnitude more indirectly, a very very small percentage of victims bothered trying to negotiate, let alone contemplated paying. Those that did pay, paid substantially more than prior CloP campaigns, and several times more than the global Average Ransom Amount of USD$740,144.
…It is likely that the CloP group may earn USD$75-100 million dollars just from the MOVEit campaign, with that sum coming from just a small handful of victims that succumbed to very high ransom payments.
That's a tremendous amount of money. However, data extortion is a 'better' problem to have than encrypting ransomware. It simply doesn't cause the same level of operational disruption.
Although we are proponents of governments using cyber operations to disrupt ransomware gangs, we think that, based on its MOVEit campaign, we'd drop Cl0p down the priority list. Monetarily, it's a big fish, but when it comes to compromising operations, Cl0p's MOVEit campaign is a minnow.
Coveware, which has produced quarterly ransomware reports since October 2018, observes that "ransomware threat actors and the entire cyber extortion economy, continue to evolve their attack and extortion tactics" as governments and the private sector react.
In both Coveware's and Chainalysis's reports, payments to Cl0p's MOVEit campaign are captured as generic ransomware. Is there a significant shift to data extortion by multiple actors? Or is Cl0p just a very significant outlier? It's hard to tell from the data we have.
The lack of quality data isn't limited to the private sector, governments are also essentially flying blind. In an soon-to-be-released interview with Risky Business host Patrick Gray, Australia's Minister for Home Affairs and Cyber Security, Clare O'Neil said "We do not have a picture of the ransomware problem in Australia at the moment".
"We don't have compulsory reporting of ransomware payments," she continued. "We don't know how much people are paying [in] ransomware payments."
So as ransomware tactics evolve, how can we get ahead of the problem without good data on the state of play?
Wiz-gate: The Reckoning
A report from cloud security company Wiz says the recent Microsoft Cloud compromise by likely China-based actor 'Storm-0558' was "more impactful than we thought". Wiz's marketing overeggs the message, but the analysis sheds important light on Microsoft's cloud security architecture.
In this attack, Storm-0558 used a (presumably) stolen Microsoft Account (MSA) key to gain access to target email accounts on Outlook Web Access. Wiz says, however, that email account compromise could have been the tip of the iceberg and Storm-0558 could have used the MSA key to access other Microsoft services such as Teams, Sharepoint, Office and even applications using the ‘log in with Microsoft’ functionality.
Initially, a Microsoft spokesperson responded that "many of the claims made in this blog are speculative and not evidence-based", but the vendor subsequently conceded that the "blog highlights some hypothetical attack scenarios".
Our guess is that Storm-0558 got what it wanted by targeting email and didn't need to compromise other services, but could have done so if required.
Wiz's analysis is important because it points out weaknesses in Microsoft's cloud security architecture, although we do think the company's report overplays its findings and describes "impact" rather than potential impact.
Despite this, the report answers some questions that Microsoft didn't. Overall, the report reinforces our conclusion last week that cloud transparency mandates are needed.
Patrick and Adam discuss this on the Risky Business podcast at 13:00:
Three Reasons to be Cheerful this Week:
- Getting closer to more E2EE interoperability: The Internet Engineering Task Force (IETF) has released the specifications for the new Messaging Layer Security protocol. This has the potential to allow secure end-to-end encrypted messaging between different platforms. Google says it will incorporate MLS into Google Messages.
- Microsoft provides more access to security logs: We briefly mentioned last week that Microsoft had adjusted its security log access pricing policy after criticism following a breach of its cloud services. Risky Business News has a more detailed breakdown of the changes.
- Google’s AI red team: Google announced an AI red team that will help set security standards for the new technologies. We think this practical approach will be more useful than regulation set in the absence of real-world knowledge.
Sponsor Section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Airlock Digital founders Daniel Schell and David Cottingham about vulnerable drivers, BYOVD attacks, and the problem with driver-based attacks.
Shorts
DPRK Focus on Crypto Supply Chain Confirmed
Multiple sources confirm that the hacking of cloud hosting provider JumpCloud was carried out by North Korean actors targeting cryptocurrency companies.
This potential attribution to North Korea was first reported by my colleague Catalin Cimpanu at Risky Business News and has since been confirmed by CrowdStrike, Mandiant and SentinelOne.
This follows an attack in March in which North Korean hackers compromised VoIP software provider 3CX to launch a supply chain attack targeting cryptocurrency companies. This attack was enabled by a prior supply chain attack on Trading Technologies, a firm that facilitates financial futures trading.
At the time we wrote that we expect this kind of "spidering out" behaviour is now standard practice for North Korean groups. Will there be other attacks that spin out from the JumpCloud compromise? We won't be surprised if there are.
Solar Controllers Are a Risky Business
The risk of poor cyber security in distributed solar energy generation, i.e. rooftop solar, has hit the news in Australia and the US. In both cases, Chinese-made internet connected solar inverters are cited as a potential point of weakness that the PRC could exploit.
We've seen poorly secured Chinese solar remote monitoring products before, and there is a genuine question about what is an appropriate regulatory regime for these devices as they become more common. As we wrote at the time:
Current critical infrastructure legislation is focussed on individually significant assets owned by a small number of organisations. This isn't appropriate for rooftop solar, but this doesn't make the potential concern about deliberate or even accidental disruption go away.
A single solar installation being compromised is inconsequential, but what if rooftop solar makes up a significant portion of your energy supply?
TETRA: When Realpolitik Meets Encryption
A group of Dutch researchers have discovered several vulnerabilities in the encryption used by a European radio standard known as TETRA, (Terrestrial Trunked Radio). These vulnerabilities potentially allow TETRA communications to be decrypted or messages injected.
One of the vulnerabilities reduces a notionally 80-bit encryption key in one of TETRA's encryption algorithms to just 32 bits of entropy and is being described as an "encryption backdoor". In practice, this means that this encryption algorithm can now be practically cracked with commodity hardware.
However, we wouldn't describe this as a backdoor, as the encryption was deliberately designed to meet export control restrictions. Although the approach to encryption has moderated over time, 42 countries are currently involved in the Wassenaar Arrangement, which licences the export of dual-use goods and technologies (including encryption). Export control is not exactly a secret.
Kim Zetter has a writeup of the issue in Wired and an excellent interview with Brian Murgatroyd, chair of the European technical standards body responsible for developing the TETRA standard and algorithms on her Zero Day substack.
Risky Biz Talks
You can find the audio edition of this newsletter and other fine podcasts and interviews in the Risky Biz News feed (RSS, iTunes or Spotify).
In our last "Between Two Nerds" discussion Tom Uren and The Grugq look at when it makes sense for governments to invest in developing their own secure phones.
From Risky Biz News:
Proposed Web DRM could stop ad-blockers from working: A team of four Google engineers has proposed a new Web API named Web Environment Integrity that would allow websites to block client apps that modify their code.
The Web Environment Integrity API is couched as a security and privacy solution. The four Google engineers claim that websites will be able to detect when malicious modifications take place to code on the client side and allow websites to cut off malicious clients. The new API sounds like it could be ideal for blocking certain types of threats, such as banking trojans and phishing sites. The developers include several scenarios that could be mitigated with their new API:
- Detect social media manipulation and fake engagement.
- Detect non-human traffic in advertising to improve user experience and access to web content
- Detect phishing campaigns (e.g., webviews in malicious apps)
- Detect bulk hijacking attempts and bulk account creation.
- Detect large-scale cheating in web-based games with fake clients
- Detect compromised devices where user data would be at risk
- Detect account takeover attempts by identifying password guessing
But while this sounds all fine and dandy, people far smarter and more accustomed to Google's BS than me have also pointed out the new API is a poisoned pill. Besides the obvious security pluses, the new API will also allow Google and money-grubbing website operators to effectively kill ad-blockers.
[more on Risky Business News]
Norwegian government hacked with MobileIron zero-day: A threat actor has exploited a MobileIron zero-day to breach twelve Norwegian government agencies, the country's security service said on Tuesday.
The identity of the attacker, the dates of the intrusions, and the names of the compromised agencies have not been revealed.
Norwegian authorities say the zero-day targeted a piece of software named the Ivanti Endpoint Manager Mobile (EPMM), previously known as MobileIron Core. The platform is used to manage mobile devices used by government employees and grant remote access to government systems and applications.
[more on Risky Business News]
Kevin Beaumont has a damning writeup of this vulnerability. The vulnerability is an unauthenticated admin access via API to an internet facing mobile device management product. Yikes:
For example, this allows you [to] run LDAP queries, list user information including potential PII, add administrative users, replace system configuration and change the config of managed mobile devices — including software deployment, device locks and wiping.
All of this can be done with a curl request, or even using a web browser. This is an incredibly easy to exploit vulnerability.



