Hacktivists Strike At Ransomware's Soft Underbelly
PLUS: Never Get Involved in a Land War in Europe
Your weekly dose of Seriously Risky Business news is written by Tom Uren and edited by Patrick Gray. This week's edition is brought to you by Resourcely.
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. Find this edition here and on Apple podcasts:

A purported group of pro-Ukrainian cyber activists, the Ukrainian Cyber Alliance, has disrupted an active ransomware gang, known as Trigona, by hacking and deleting the group's servers.
If a group of hacktivists can compromise a ransomware gang, these gangs are certainly susceptible to operations run by better organised and resourced state cyber outfits.
While the hacktivists’ actions will hurt, this is probably a speed hump for Trigona rather than an enduring disruption. The group claims that it will return quickly.
We think a competent state-backed group would maximise the grief it caused by quietly degrading a ransomware group's activities over a long period of time.
The ransomware group has operated since the beginning of 2022 but only branded itself 'Trigona' toward the end of last year when it launched a Tor negotiation site. A Trend Micro report on the group from June this year describes it as "highly active”. The report said the group had created both Linux and Windows versions of its malware and was continuously updating them.
Trend Micro detected attempted Trigona ransomware attacks primarily in the technology and healthcare industries, with just over half detected in the US and India. However, Trigona’s attacks could be opportunistic rather than targeted to specific industries and countries. In April this year, for example, the group targeted internet-exposed Microsoft SQL servers using password guessing attacks.
Trend Micro said the Trigona group had "poor operational security when it comes to the implementation of Tor sites". However, the cyber security firm said the group’s targeting of poorly-secured SQL servers was a cut above less technically proficient actors.
The Ukrainian Cyber Alliance said it gained access to Trigona's infrastructure using a known vulnerability in its Atlassian Confluence collaboration platform. A representative of the Alliance, herm1t, said on X (formerly Twitter) that Trigona's "admin panel, landing, blog, leaks site, internal server (RocketChat, Atlassian), wallets and dev servers dumped and erased". In a Facebook post, the same representative said Trigona's "entire infrastructure is completely destroyed" and they told Bleeping Computer that they had taken the gang's cryptocurrency hot wallets.
Herm1t also said data from Trigona had been taken and would be distributed to researchers after the Cyber Alliance had a chance to go through it.
The Ukrainian Cyber Alliance's claimed motivation here is that ransomware groups are bad people that often operate freely in Russia. In their Facebook post, Herm1t says "we simply found one such gang and treated them the same way they treat others".
Now, it can be difficult to be sure that purported hacktivists are genuine and one possibility here is that this breach is a state operation masquerading as a hacktivist action. However, we don't think that this is the case. For a start, the Ukrainian Cyber Alliance has a track record dating back to 2014 as described in Bleeping Computer. And we can't think why a state-backed group would pretend to be hacktivists when hacking a ransomware group. They'd simply disrupt the ransomware group without feeling the need to advertise their success afterwards.
We support the idea that states should use their offensive cyber capabilities to disrupt cyber criminals, and this incident is proof that ransomware groups are susceptible to compromise.
The Trigona incident certainly shows that US Cyber Command or the UK National Cyber Force would have opportunities if they were seriously tasked with tackling ransomware operators.
There's certainly a need for more operations disrupting ransomware — NCC group reports that September 2023 was a record month for ransomware incidents (as covered in the Risky Business News section of this newsletter).
Never Get Involved in a Land War in Europe
The International Committee of the Red Cross (ICRC) has released an advisory board report on "Protecting Civilians Against Digital Threats During Armed Conflict". We doubt it will do much to change the mind of combatants and hacktivists but it does have some useful advice for tech companies and other non-combatants.
We recently covered an opinion piece from two ICRC lawyers that focused more narrowly on the role of hacktivists in combat. This new report doesn't add much in that regard, but in addition to advice for what the report calls "belligerents", it also contains advice for states, tech companies and humanitarian organisations.
The recommendations to tech companies are interesting in that they reflect some of the problems that SpaceX in particular has encountered during the Russian invasion of Ukraine. We have paraphrased these recommendations here:
- Consider whether the services you provide and who you provide them to make your company a military target
- Keep military and civilian infrastructure separate if possible
- Try to protect civilian populations even when following legal obligations such as sanctions
- Try to stop content and disinformation that incites violence or encourages hate speech.
SpaceX, probably inadvertently, made itself a military target in the first month of the invasion by providing Starlink services and terminals to Ukraine. These ended up being used by the Ukrainian military for combat communications and targeting, so Starlink ended up carrying both military and civilian traffic. SpaceX announced in December 2022 that it was launching a new military-specific product called Starshield.
Although Elon Musk was hasty providing SpaceX to Ukraine, in our view he has muddled through pretty successfully. It was the right move to provide Starlink to Ukraine, but it might have helped the company be better prepared if it had thought through some of these issues beforehand.
Before 2022, these kinds of war-related issues must have seemed like off-the-wall scenarios that would never eventuate. Sadly, they now seem like business as usual.
Ukraine's Security Service In Bed With Hackers?
The Record reports that, according to a source within Ukraine's SBU security service, the SBU collaborated with hacker groups to breach Russia's largest private bank.
Two pro-Ukrainian hacker groups, KibOrg and NLB, claimed to have breached Alfa-Bank and stolen customer records, and released some of this data publicly. This data is said to include information that relates to the bank's owner, billionaire Mikhail Fridman, and his pro-Russian blogger son, among others.
The Record writes:
A source within Ukraine's security service who requested anonymity because he is not authorised to speak publicly about the incident confirmed to Recorded Future News that the Ukrainian agency was involved in the operation, but did not provide further details.
We've had our doubts about how useful a hacktivist army can be, but this could be a significant step towards integrating Ukraine's hacktivist army into operations that contribute meaningfully to the country's strategic efforts. But it's hard to know given there is so little information about what "involved" in this case actually means.
It could, for example, mean as little as taking information acquired through the reported breach. This isn't new — Ukrainian officials already claim to have taken advantage of previous leaks for intelligence purposes. Or it could mean as much as specific tasking before Alfa-bank was reportedly hacked. That would be a pretty significant step in turning the hacktivist goodwill that supported Ukraine into a genuinely useful capability.
Three Reasons to Be Cheerful This Week:
- Ransomware double happiness: In addition to the hacktivist disruption of Trigona, an international coalition of law enforcement agencies took down Ragnar Locker ransomware's website and arrested key members of the group. Risky Business News has more coverage.
- Indian tech support scam crackdown: In Operation Chakra-II, India's Central Bureau of Investigation (CBI) raided call centres in 76 locations engaged in scams involving tech support and cryptocurrency. The CBI received help from Microsoft and Amazon who provided a joint referral that Microsoft says "enabled the exchange of actionable intelligence and insights with CBI and other international law enforcement agencies to help them take action at scale". The call centres raided by CBI impersonated Microsoft and Amazon tech support. This is the first time the two companies have collaborated to combat tech support fraud.
- US disrupts illicit North Korean IT workers: The US Department of Justice announced that it had seized 17 websites in connection with the infiltration of North Korean IT workers into foreign companies. These workers were employed in legitimate companies under false pretences and their salaries were used to fund North Korea's weapons program. This comes on top of the previous seizure of about USD$1.5m.
Sponsor Section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Resourcely CEO Travis McPeak about the modern DevOps ecosystem, how giving developers tools with security baked in keeps everyone safe and happy, and how that's easier than expecting your software engineers to become cybersecurity experts overnight.
Shorts
Stealing Tokens From Tech Support
A threat actor has breached Okta's support system and used the access to steal customer credentials.
The intruder gained access to customer credentials by stealing HTTP Archive or HAR files that were uploaded to Okta by customers to help troubleshoot recent support cases. HAR files typically contain cookies and session tokens that can be used to impersonate users, and these were used in attacks detected by Cloudflare, BeyondTrust and 1Password.
In at least one case the intruder tried to add another identity provider or IDP, what we previously called a Bring-Your-Own Identity Provider attack.
In retrospect, Okta probably should have been sanitising these files at ingest, rather than expecting customers to do it.
Krebs on Security has further coverage.
AI Phishing Faster, But Dumber. For Now.
IBM's X-Force security research team has examined how ChatGPT can be used to generate phishing emails, and measured how effective these emails are.
Although ChatGPT has protections in place to prevent it being used maliciously, X-Force was able to convince it to produce phishing emails tailored to specific industries with a series of five prompts. These phishing emails were not quite as good as human-created ones, but they were created much, much faster.
In terms of click through rates, human-crafted phishing emails were better, although not by much. When it came to being reported as suspicious, AI-generated phishing emails were worse, although again not by much when compared to run of the mill human-generated phishing emails.
X-Force red team phishing emails were reported significantly less frequently than either AI or 'regular' phishing emails, but generating these high-quality phishing emails typically takes about 16 hours. This sounds like a long time to write an email, but the process starts with open source research on platforms such as LinkedIn and Glassdoor to find recent events relevant to the company that can be used to build credibility.
By contrast, ChatGPT-generated emails took just five minutes to generate.
Risky Biz Talks
You can find the audio edition of this newsletter and other fine podcasts and interviews in the Risky Biz News feed (RSS, iTunes or Spotify).
In our last "Between Two Nerds" discussion Tom Uren and The Grugq look at "spooky effects" aka when agencies play silly buggers with target computers.
From Risky Biz News:
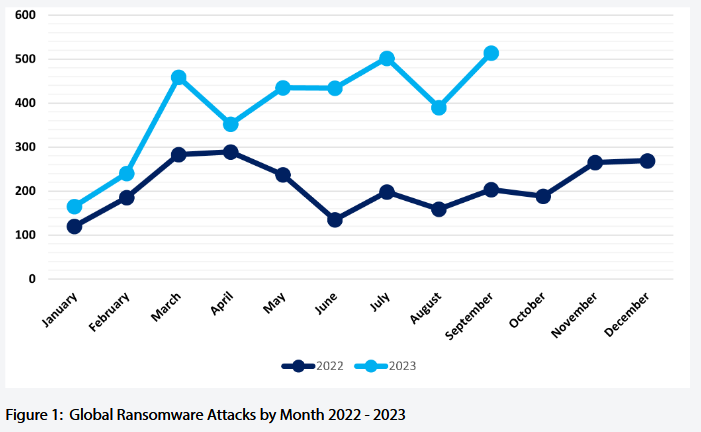
Record ransomware numbers: The month of September 2023 has been the most active month for ransomware gangs on record, with 514 disclosed attacks. September 2023 beats the previous record of 459 ransomware attacks disclosed earlier this year in March. Two groups that launched last month, LostTrust and RansomedVC, ranked in the top five of most active groups. The numbers were compiled by NCC Group using data published on ransomware leak sites.
Australia to get a cyber shield: Microsoft has signed an agreement with the Australian government to build a cyber shield and help the country fend off cyber-attacks. The project's official name will be the Microsoft-Australian Signals Directorate Cyber Shield, or MACS. It is a classic threat-exchange program aimed at improving the detection of threats targeting Australia. Besides MACS, Microsoft will also invest AUS$5 billion to build nine more data centers in the country, raising the total to 29.
Cisco IOS XE hackers are hiding their tracks as patches come out: Over the past three days—since our last newsletter edition—the situation around the latest zero-day attacks targeting Cisco IOS XE devices has drastically changed, and we feel the need to cover it in our featured section and provide a short summary of what has been going on.
Although these attacks have been taking place since at least September 28, news of this campaign came out last Monday, on October 16, when Cisco revealed the existence of a zero-day tracked as CVE-2023-20198 in the web administration panel of its IOS XE operating system.
[more on Risky Business News]



