Grandpa Biden: Cyber President
PLUS: The iCloud Backup From Hell
Your weekly dose of Seriously Risky Business news is written by Tom Uren, edited by Patrick Gray with help from Catalin Cimpanu. It's supported by the Cyber Initiative at the Hewlett Foundation and founding corporate sponsor Proofpoint.

The White House released its Cyber Security Strategy last week and — by and large — it looks pretty decent.
The strategy divides activities into five different "pillars":
- Defend Critical Infrastructure
- Disrupt and Dismantle Threat Actors
- Shape Market Forces to Drive Security and Resilience
- Invest in a Resilient Future
- Forge International Partnerships to Pursue Shared Goals
Some of these pillars, such as "Defend Critical Infrastructure" and "Invest in a Resilient Future", are ones you'd expect in any cyber security strategy, but there are some genuinely new ideas here.
Under the "Invest" pillar, for example, one objective is to "Secure the Technical Foundation of the Internet". This section identifies that "many of the technical foundations of the digital ecosystem are inherently vulnerable" and then specifically identifies both Border Gateway Protocol and unencrypted Domain Name System requests as "pervasive concerns" that must be mitigated. It’s difficult for individual stakeholders to make any meaningful difference to these kinds of pervasive and systemic risks, so it is a good space for governments to try and drive some improvement.
Two of the other pillars are nice surprises — "Disrupt and Dismantle Threat Actors" and "Shape Market Forces to Drive Security and Resilience".
In the "Disrupt and Dismantle" section, the strategy states:
The United States will use all instruments of national power to disrupt and dismantle threat actors whose actions threaten our interests. These efforts may integrate diplomatic, information, military (both kinetic and cyber), financial, intelligence, and law enforcement capabilities. Our goal is to make malicious actors incapable of mounting sustained cyber-enabled campaigns that would threaten the national security or public safety of the United States.
In other words, we'll use all tools at our disposal to tackle all the cyber threats we face. What we've described as the US government's "portfolio approach" to tackling ransomware is here to stay, and won't be limited to just ransomware groups.
This is good.
The idea is to turn disruption into a business as usual activity. These include efforts to integrate federal disruption efforts, improve collaboration with the private sector to disrupt adversaries, and increase the speed of victim notification.
The strategy leaves military options open, but it isn't clear on exactly how military capabilities will fit into disruption activities:
DoD's new strategy will clarify how U.S. Cyber Command and other DoD components will integrate cyberspace operations into their efforts to defend against state and non-state actors capable of posing strategic-level threats to U.S. interests, while continuing to strengthen their integration and coordination of operations with civilian, law enforcement, and intelligence partners to disrupt malicious activity at scale
Aside from the military's unresolved role, when it comes to this pillar the government has both a strategic goal and relatively concrete plans — it's got a destination and a roadmap.
When it comes to the most significant initiative in "Shape Market Forces to Drive Security and Resilience", however, the government has a destination without a roadmap.
This pillar brings together a grab bag of issues united by the failure of market forces to deliver good security. These include IoT device security, the all-too-often poor security of new technology products, and lax personal data privacy standards.
The big idea here is to make companies that peddle crapware pay for the mess when their products hits the fan:
Markets impose inadequate costs on — and often reward — those entities that introduce vulnerable products or services into our digital ecosystem. Too many vendors ignore best practices for secure development, ship products with insecure default configurations or known vulnerabilities, and integrate third-party software of unvetted or unknown provenance. Software makers are able to leverage their market position to fully disclaim liability by contract, further reducing their incentive to follow secure-by-design principles or perform pre-release testing. Poor software security greatly increases systemic risk across the digital ecosystem and leave American citizens bearing the ultimate cost.
We agree that systemic underinvestment in product security is a problem and that appropriately apportioning liability is part of the solution. We like the boldness of suggesting a big idea that could actually improve product security.
As per the strategy, congress will draft legislation that will prevent companies from fully avoiding liability via their end user licence agreements. The new law should also establish standards for secure software development. The administration will assist in codifying secure development standards that will shield companies from liability if they are followed.
We commend its ambition but think it will be a difficult long-term effort, so much so that the idea of shifting liability is regularly called "cybersecurity's third rail". The administration is realistic about this, and an unnamed senior official told reporters that they see this strategy as a long-term 10-year effort rather than something that will be implemented quickly.
Given that shifting liability is a long-term goal, we think there is a missed opportunity here to define intermediate steps that would be useful on their own merits.
One suggestion here is to focus on transparency.
To some degree, market forces stop working when customers are kept in the dark and companies don't disclose breaches. A much stronger emphasis on transparency using mandatory disclosure requirements could have gone some way to fixing this market failure and would have been far easier to implement in the short term. Last week's edition discussed the trade-offs between liability and disclosure in more detail.
Data privacy is also covered off in this "market forces" pillar. The American Data Privacy and Protection Act (ADPPA) already has broad support and is waiting in the wings, so we expect to see a renewed push here.
We have mixed feelings about the fifth pillar, "Forge International Partnerships to Pursue Shared Goals", particularly the objective to "Build Coalitions to Reinforce Global Norms of Responsible Behaviour".
There have been ongoing efforts to define norms of responsible behaviour for many years now and we are sceptical that building coalitions now will do much to restrain adversary activities that we don't like.
Although we have some quibbles with the strategy in places, we love its ambition and it does what a strategy should do — it articulates how the US will "win" by reshaping the playing field. In the short term, it'll tackle threat actors with all available tools. In the longer term, it will reshape liability to encourage companies to stop flinging out crapware. The path ahead isn't entirely clear, but at least the direction is well defined.
The iCloud Backup From Hell
The New York Times has a great deep dive looking at Chinese Ministry of State Security (MSS) attempts to steal intellectual property from the aviation industry. According to the Chinese, intellectual property theft is a national security imperative:
James Lewis, a former diplomat now at the Center for Strategic and International Studies in Washington, recalls participating in a meeting in 2014 or so at which Chinese and American government representatives, including an officer from the People's Liberation Army, discussed the subject. "An assistant secretary from the US Department of Defense was explaining: Look, spying is OK — we spy, you spy, everybody spies, but it's for political and military purposes," Lewis recounted for me. "It's for national security. What we object to is your economic espionage. And a senior PLA colonel said: Well, wait. We don't draw the line between national security and economic espionage the way you do. Anything that builds our economy is good for our national security."
The story also describes the MSS's horrendously poor operational security practices. Tasked with stealing aviation industry secrets, MSS officer Xu Yanjun contacted potential recruits via Gmail addresses that were linked to iPhones with iCloud backups enabled. Xu used the phones for both personal and work purposes, so search warrants for the iCloud accounts provided an intelligence bonanza. In the backups:
…investigators also found an audio recording of a 2016 conversation with a professor at NUAA [the Nanjing University of Aeronautics and Astronautics] in which Xu had talked about his job in intelligence and the risks associated with travelling. "The leadership asks you to get the materials of the U.S. F-22 fighter aircraft," he told the professor. "You can't get it by sitting at home."
Xu's iCloud backup also contained messages exchanged with other US aerospace industry employees and an audio recording with several Chinese engineers where he explained his approach to soliciting information from potential recruits. It also contained messages showing that Xu helped coordinate a cyberespionage campaign targeting aviation technology companies.
The article also does a good job examining the impacts on the people involved which the author describes as "chess pieces in a geopolitical game". Xu was lured to Belgium, arrested, extradited to the US and has been sentenced to 20 years in prison. The potential recruit that the author spoke to was fired from his job, cooperated with the FBI to avoid prosecution, and is now rebuilding his life.
Three Reasons to be Cheerful this Week:
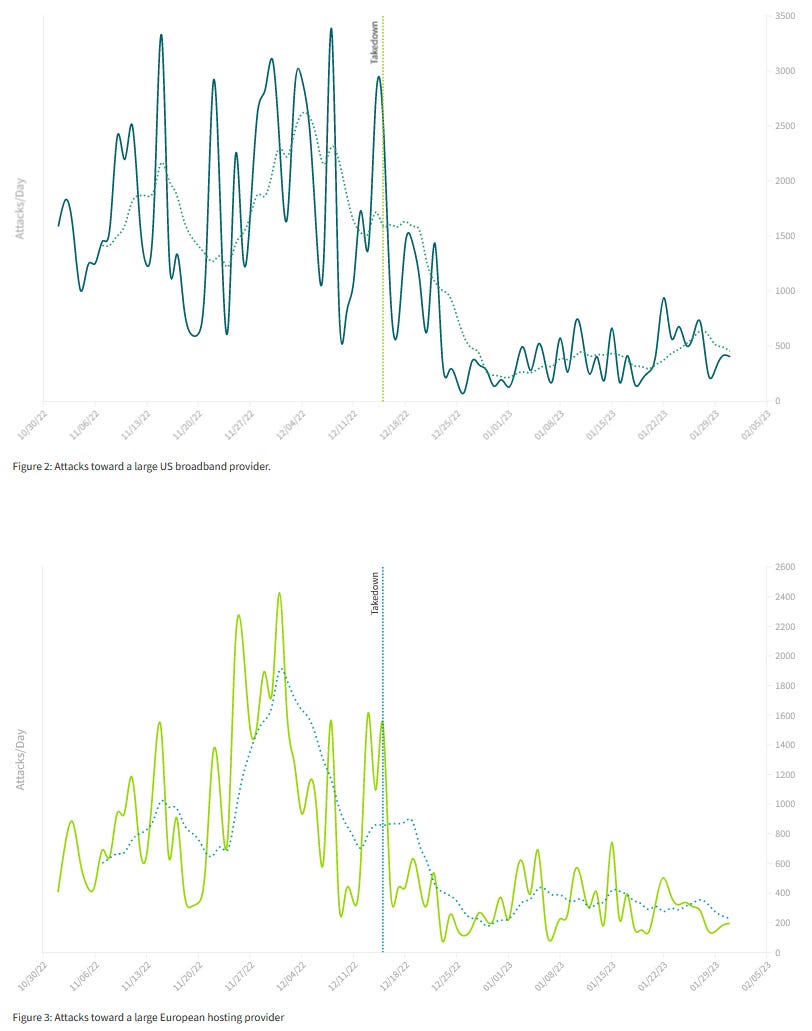
- Takedowns work: security firm Netscout's analysis indicates that DDoS activity fell significantly after an international takedown targeting DDoS-for-hire services took place in mid-December last year.
- DoppelPaymer Raids: German and Ukrainian police took action against members of the DoppelPaymer ransomware gang, including raiding several locations and seizing several suspects and equipment for forensic examination. German police said that over 600 DoppelPaymer victims had been identified worldwide.
- Germany to ban Huawei, ZTE: German media is reporting that the government will ban Huawei and ZTE equipment from its 5G network to address security concerns (English reporting here). We think it is about time.
Sponsor Section
Seriously Risky Business is supported by the Hewlett Foundation's Cyber Initiative and corporate sponsor Proofpoint.
Proofpoint has released a new report on a new threat actor it calls TA499 which tries to engage high-profile North American or European officials in phone calls or video chats. These calls are then edited to produce pro-Russian propaganda.
1/4: TA499 is an information operation threat actor publicly known as Vovan & Lexus. @proofpoint analysts have tracked and blocked scores of attempts to reach out to politicians, CEOs, and celebrities that have spoken out against the war in Ukraine.
— Threat Insight (@threatinsight) 3:24 PM ∙ Mar 7, 2023
Blog: ow.ly/5vnm50NaUgT
Tines No-code Automation For Security Teams
Risky Business publishes sponsored product demos to YouTube. They're a great way for you to save the time and hassle of trying to actually get useful information out of security vendors. You can subscribe to our product demo page on YouTube here.
In this video demo, Tines CEO and co-founder, Eoin Hinchy, demonstrates the Tines automation platform to host Patrick Gray.
Shorts
Mexican Military Misused Pegasus
Hacked materials show that the Mexican military used NSO Group's spyware on journalists and a human rights activist investigating allegations the armed forces had killed innocent civilians.
The leaked documents provide evidence connecting the Mexican military to the deployment of spyware against the targeted individuals, who were investigating allegations the Mexican armed forces killed innocent civilians in a cartel-related shootout. The use of NSO's Pegasus spyware in this case was previously reported by Citizen Lab in October 2022.
"The military wasn’t using Pegasus to combat crime," Luis Fernando García, the director of R3D, a local digital rights group, told The New York Times.
"The military was spying on civilians to protect itself."
The documents were obtained by Latin American hacking group Guacamaya which this newsletter thinks could well be genuine hacktivists.
Chinese Foreign Ministry says USA "Overly Paranoid" on Cranes
The Wall Street Journal reports the Pentagon is concerned that Chinese-made ship-to-shore (STS) cranes operating at American ports could be used by the PRC to monitor shipments of military materiel.
Shanghai Zhenhua Heavy Industries (ZPMC) are relatively cheap and well-built and the company claims it provides 70% of the global market for STS cranes. They are also chock full of sensors to track containers as they are moved, giving rise to fears that they could be used to spy on container movements.
The crux of these concerns is the PRC's National Intelligence Law, under which any Chinese company could potentially be compelled to assist with PRC intelligence collection efforts.
This is the same concern that has driven Huawei and ZTE 5G bans, but there is a difference here… cranes aren't at the heart of a telecommunications network that other critical services depend on. And cranes don't have to talk to every other device on a network.
In other words, cranes at ports are important, but there are lots of standard ways to mitigate these concerns.
Our favourite part of this news story is the Chinese foreign ministry responded by saying concerns about spy cranes were "overly paranoid".
DJI Drones Are Not Your Battlefield Friend
German researchers have reverse engineered the DJI drone protocol that broadcasts an operator's exact location.
This protocol, known as DroneID, was designed to allow regulators and law enforcement to monitor drones and prevent abuse. Being a public safety mechanism, it was deliberately not encrypted.
DJI drones have, however, been used in the war in Ukraine. The Ukrainian government complained that DJI's drone tracking system, known as Aeroscope, was being used by Russian forces to target drone operators. The Twitter back and forth here between Ukrainian Vice Prime Minister Fedorov and DJI is pretty interesting.
Wired has an excellent examination of the issues involved with encrypting DroneID. Our take is that encryption makes perfect sense for military applications, not so much for consumer applications.
Risky Biz Talks
In addition to a podcast version of this newsletter (last edition here), the Risky Biz News feed (RSS, iTunesor Spotify) also publishes interviews.
In our last "Between Two Nerds" discussion Tom Uren and The Grugq discuss how cyber operations have been used in the war in Ukraine. They discuss the limits of what we can know given the "fog of cyber war" and what it tells us about how cyber operations might be used in future conflicts.
From Risky Biz News:
EPA releases cybersecurity guidance for US public water sector: The US Environmental Protection Agency (EPA) is directing states to include cybersecurity in their sanitary surveys, which are periodic audits of public water systems.
To help states get underway, the EPA has published a technical document with guidance [PDF] intended to assist states with integrating cybersecurity into sanitary surveys.
EPA officials say they issued the memorandum after efforts to improve cybersecurity through voluntary measures "yielded minimal progress." The EPA says the document "is designed to be used right away" and can play a major role in "improving the cybersecurity of operational technology used for safe drinking water." [more at Risky Biz News]
Canada's tax revenue agency tries to ToS itself out of hacking liability: This is a guest post from Tanya Janca, CEO and Founder of We Hack Purple.
The Canada Revenue Agency (CRA), the tax department of Canada, recently updated its terms and conditions to force taxpayers to agree that CRA is not liable if their personal information is stolen while using the My Account online service portal—which, ironically, all Canadians must use when doing their taxes and/or running their business. [more at Risky Biz News]
Another low for ransomware gangs: The ALPHV (BlackCat) ransomware gang has published photos of breast cancer patients as part of its extortion of Lehigh Valley Health Network, a Pennsylvania-based healthcare network.



