Risky Biz News: Germany warns of Chinese APTs hijacking SOHO routers for espionage
In other news: Okta customers hit by mysterious attacker; LogicMonitor customers hit by ransomware; and Microsoft retires WordPad.
This newsletter is brought to you by enterprise browser Island. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The German government says Chinese APTs are hijacking SOHO routers, NAS devices, and smart home automation systems to conduct cyber-espionage operations.
The hacked devices are used as a giant mesh of proxies that relay and hide the origin of the attack.
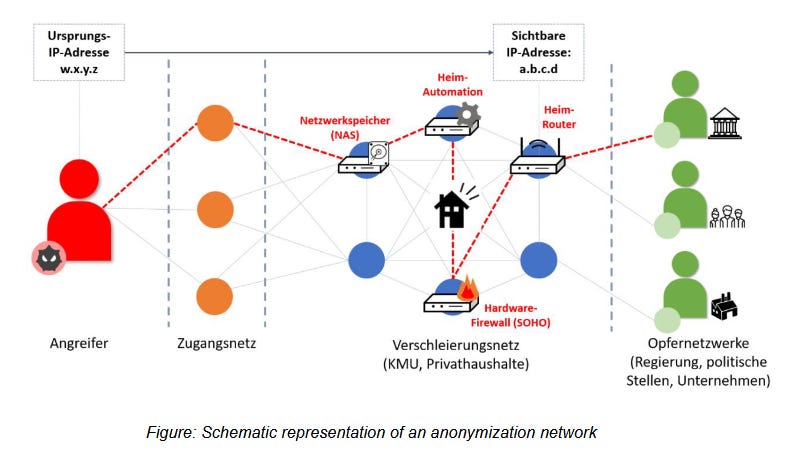
Chinese cyber-espionage groups like APT15 (Vixen Panda, Ke3chang) and APT31 (Zirconium, Judgement Panda) have been observed utilizing the tactic, according to a security advisory published by the German Federal Office for the Protection of the Constitution (BfV) last week. A Google Translate machine-translated version of the alert is here.
Targets of their attacks included government and political bodies.
Although the BfV did not name any victims, German-language news outlets DerStandard, DerSpeigel, and ZDF say APT15 used a network of hacked routers to hide the origin of their attack against the Federal Agency for Cartography and Geodesy (BKG).
The agency, which analyzes satellite imagery and creates highly detailed maps for the German Ministry of the Interior, was successfully compromised by APT15 in December 2021.
The use of hacked routers and IoT devices as proxies for disguising the locations of attack infrastructure has been gaining widespread adoption over the past decade. It was first seen being used by US intelligence agencies before being later adopted by Russian, Vietnamese, and now Chinese APT groups.
Some APT groups like the APT28 and OceanLotus build and operate their own proxy networks, such as VPNFilter and Torii. Some take the easier route and rent proxies from the operators of proxyware (residential proxy) networks and IoT botnets. The proliferation of IoT malware like Mirai and its brethren has led to an explosion of proxy-for-hire networks offered in underground marketplaces.
Chinese APT groups have been late to adopting proxy networks to hide their operations, but it now seems that all of China's top APT groups use them as a standard practice to at least hide their C&C servers, as seen in recent reports.
Breaches, hacks, and security incidents
Okta attacks: Identity and access management company Okta says a threat actor has been targeting and compromising some of its US-based customers. The attacks followed the same pattern and targeted employees in the IT help desk of Okta customers. Okta says the attacker tricked help desk personnel into resetting MFA on their company's Okta Super Administrator account. The attacker then used this account to impersonate other users and move laterally inside compromised networks. Okta says it observed attacks following this specific pattern between July 29 and August 19 but did not say how many customers were attacked. The company published indicators of compromise from the intrusions.
LogicMonitor hacks: Cloud infrastructure monitoring company LogicMonitor has suffered a security incident after hackers gained access to some customer accounts. The company says the incident affected a small number of customers who used default or weak passwords for their accounts. A TechCrunch report claims some of the compromised accounts were used to pivot to internal IT networks and deploy ransomware.
Sourcegraph incident: AI-based coding tool Sourcegraph says a hacker gained access to one of its admin access tokens and used it to allow free access to its service. Sourcegraph says the intruder created an app and used the admin access token to grant it unlimited access to its API. The company believes the attacker advertised free access to its service through the app. Sourcegraph blamed the breach on an employee error who accidentally included the admin access token in one of their code commits in July.
University of Sydney breach: The University of Sydney says it suffered a cybersecurity incident after a breach at one of its third-party providers.
Hafhashtad hack: Hacktivist group Black Reward has hacked the Iranian financial app Hafhashtad. The group breached the company's servers and sent mobile notifications to customers urging citizens to rise against the country's oppressive regime again. The Black Reward group rose to prominence last year when it hacked and leaked files from Iran's Atomic Energy Organization and the government's Fars news agency. [Additional coverage in Iran International]
General tech and privacy
Subject rights and privacy fines to hit $1 billion: Market analytics company Gartner estimates that by 2026, fines due to mismanagement of subject privacy rights will increase tenfold and grow to over $1 billion/year. Subject rights requests (SRRs) are a right that some states give consumers to control how their data is stored and managed by companies. SRRs are a key element of the EU's GDPR. [Additional coverage in Zawya]
Microsoft retires WordPad: Microsoft has formally retired the WordPad text editor. The app's deprecation came out of the blue with no prior message. WordPad was officially retired on September 1, 28 years after it was first added to Windows 95. Microsoft says it will remove the app from all PCs in a future release of Windows.
Windows TLS 1.0 and 1.1 deprecation: This month, Microsoft is scheduled to remove support for the TLS 1.0 and 1.1 protocol at the OS level. Support will first be removed in Windows 11 Insider Preview builds and then with stable OS versions.
Two BGP leaks: Kentik looks at two recent BGP leaks that had minimal impact on the general state of the internet.
"Years ago large routing leaks like these might have been the cause of widespread internet disruption. Not so much anymore. Humans are still (for the time being) configuring routers and, being human, are prone to the occasional mistake. What has changed is that the global routing system has become better at containing the evitable goof-ups. Route hygiene has improved due to efforts like MANRS and the hard work of network engineers around the world."
Government, politics, and policy
Apple's CSAM reply: Apple has responded to a child safety advocacy group that was protesting the company's decision to scrap its iCloud child sexual abuse material (CSAM) detection tools last year. Apple told the group that deploying CSAM tools on iCloud would open new avenues for private data theft and bulk surveillance, creating more problems than it fixes. [Read Apple's full reply in Wired]
NIST Supply Chain Security Framework: The US National Institute of Standards and Technology (NIST) has published a draft framework with the best practices for securing the CI/CD pipelines of cloud applications against software supply chain attacks. The draft document includes recommendations like using attestation policies, scanning dependencies for vulnerabilities, and signatures generation and verification. The framework is going through a public comment period, and organizations can submit feedback until October 13.
NIST NFT standard: The same NIST also published a draft framework for the security of non-fungible tokens (NFTs).
New NCSC CTO: The UK National Cyber Security Centre (NCSC) has announced that Ollie Whitehouse will become the agency's new CTO. Whitehouse has worked in the private sector for 27 years and was previously CTO for NCC Group. Whitehouse replaces Ian Levy, who left the NCSC last October to join Amazon.
ENISA report on subsea cables: The EU's cybersecurity agency has published a report on subsea cables and has warned against operators having single points of failure due to a concentration of cables in a single route, which opens internet networks to easy sabotage in the event of a conflict or protest.
Twitter helped Russian propaganda: An EU study found that Twitter's new policies under Musk have helped Russia spread its propaganda on the site. The EU found that Instagram, Facebook, and Telegram also failed to stop Russian disinformation, but not as bad as Twitter. [Additional coverage in the Washington Post/non-paywall]
"Preliminary analysis suggests that the reach and influence of Kremlin-backed accounts has grown further in the first half of 2023, driven in particular by the dismantling of Twitter's safety standards."
Sponsor section
In this Risky Business News sponsor interview Tom Uren talks to Mike Fey, CEO and co-founder of Island about the idea of an ‘enterprise browser’. Tom and Mike discuss what an enterprise browser actually is, what problems it solves, and why browsers focussed on business requirements haven’t been a product category until now.
Cybercrime and threat intel
PyLocky case falls apart due to clerical error: A French court has dropped the case against Algerian hacker BX1 after the prosecution made a clerical error in court documents. French prosecutors had accused 34-year-old Hamza Bendelladj of orchestrating attacks with the PyLocky ransomware against French companies from his prison cell in the US. Bendelladj's legal team argued that court documents included wrong citations that referenced the JobCrypter ransomware and not PyLocky. The judge dismissed the case after the prosecution confirmed the error. Bendelladj, also known as the Smiling Hacker, was sentenced in 2016 to 15 years in prison by US authorities for operating the SpyEye trojan. [Additional coverage in ZDNet France]
Digicel Pacific abused in SS7 tracking: A Fiji-based telco named Digicel Pacific appears to have rented its infrastructure to spy-for-hire operations. The company's systems have been used to pinpoint the location of surveilled targets and intercept their communications. Digicel's infrastructure has been linked to incidents of spying on journalists, activists, and political dissidents. Some targets were murdered hours after their location was tracked. Investigators from CitizenLab say the company's systems have been used to make more than 21,000 suspicious queries over the past year. Digicel operates cellphone networks in Fiji, Papua New Guinea, Samoa, Tonga, and Vanuatu, and was acquired last year by Australian telco Telstra. [Additional coverage in the OCCRP & ABC]
New npm malware: Fifty-three malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
16Shop: Trend Micro takes a detailed look at 16Shop, the Phishing-as-a-Service platform managed by an Indonesian man and destructured by Interpol in August. Poor OpSec strikes again!
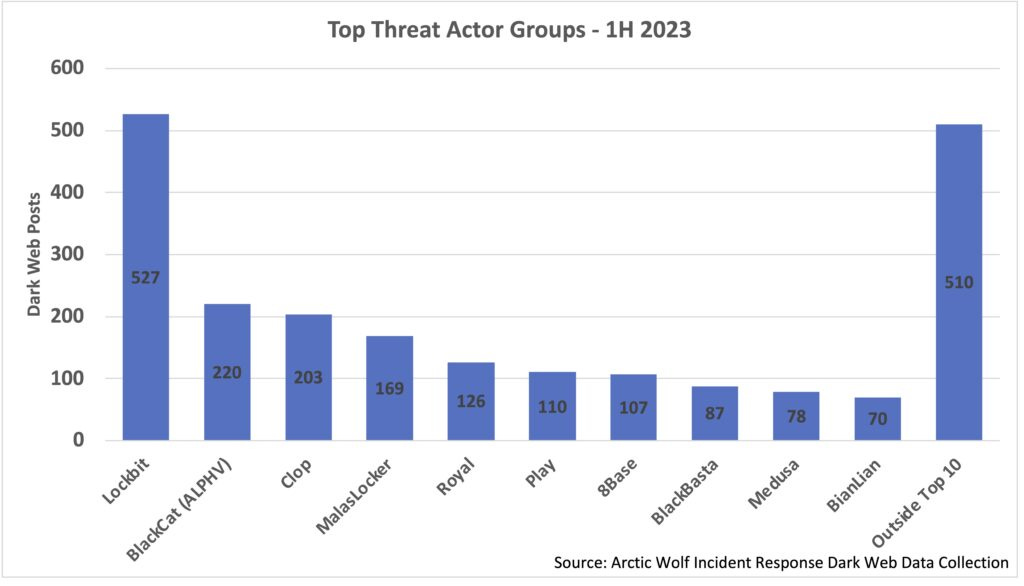
Ransomware H1 numbers: ArcticWolf has some numbers of ransomware activity during H1 2023, based on dark web leak site posts. Lockbit still at the top, despite the drama.
Malware technical reports
Prysmax: Security firm CyFirma has discovered a new Malware-as-a-Service being advertised on underground forums named Prysmax. The service launched in June and offers criminals access to an infostealer-RAT combo. The malware extensively uses Powershell and can collect data from infected hosts, such as browser credentials, authentication cookies, and crypto-wallet databases.
Ducktail: Zscaler takes a look at the activities of Ducktail, a Vietnamese cybercrime group specialized in hijacking Facebook and TikTok business accounts.
Emotet in 2023: Trellix has taken a look at how Emotet has been doing throughout the year and its recent malspam campaigns.
Rhysida ransomware: Fortinet has a write-up on the Rhysida ransomware group.
Chaos ransomware: ThreatMon has a report on the fourth version of the Chaos ransomware.
Cloak ransomware: Cyberint published a report on Cloak, a new RaaS that appeared at the end of 2022.
FreeWorld ransomware targets MS-SQL servers: A threat actor named DB#JAMMER is hacking into unsecured MS-SQL databases to breach corporate networks and deploy ransomware. The final payload is FreeWorld, a new version of the older Mimic ransomware. Security firm Securonix says the attacker is using brute-force attacks to target MS-SQL servers that use weak credentials.
Sponsor Section
Island CEO Mike Fey and CSO Brian Kenyon talk about how the Island enterprise browser came to be and its early days.
APTs and cyber-espionage
Kimsuky's SuperBear: South Korean security firm Interlab has discovered a new RAT used by the Kimsuky North Korean APT in attacks against dissidents living abroad. The new RAT is named SuperBear and appears to have been based on open-source code. The same campaign was also spotted by Qihoo 360. A deep dive into the malware is also available here, courtesy of a security researcher named Ovi.
APT34: Chinese security firm NSFOCUS has published a report on a recent spear-phishing campaign carried out by the Iranian cyber-espionage group APT34, also known as OilRig. The campaign targeted US organizations and aimed to infect victims with a new GGCC-compiled version of the SideTwist trojan.
Saaiwc (Dark Pink): Chinese security firm Rising has a report on Saaiwc, also known as Dark Pink.
Vulnerabilities, security research, and bug bounty
Linux exFAT vulnerability: A local privilege escalation (CVE-2023-4273) exists in the Linux exFAT driver.
Linux kernel vulnerability: An LPE vulnerability (CVE-2023-35001) affects Linux kernel versions going back for nine years. The vulnerability is part of a trio of LPEs impacting Windows, macOS, and Linux that Synack researchers used at this year's Pwn2Own Vancouver hacking contest earlier this spring.
Ubuntu TPM bypass: You can bypass TPM full disk encryption on a Ubuntu by mashing your ENTER key really fast during boot.
VMWare Aria PoC: The Summoning Team has published details and a PoC for a VMWare Aria vulnerability (CVE-2023-34039) they found and helped VMWare patch last week.
SharePoint bug write-up: A detailed write-up is now available for CVE-2023-29357, an EoP in Microsoft SharePoint. The bug was used at the Pwn2Own hacking contest earlier this May.
Splunk security updates: SIEM maker Splunk released security updates last week to fix 11 vulnerabilities.
GitLab security updates: GitLab has released security updates to fix 12 vulnerabilities in its enterprise and community products.
Adobe ColdFusion exploitation: Fortinet says it is seeing multiple threat actors exploit three ColdFusion vulnerabilities that Adobe patched in July. Attacks have included network scans, the installation of web shells, and the deployment of backdoors that could be leveraged for future access. In some instances, Fortinet has seen Adobe ColdFusion servers being added to crypto-mining and DDoS botnets.
AtlasVPN zero-day: An anonymous researcher has published details [archived] about a zero-day vulnerability in the AtlasVPN Linux client. The AtlasVPN daemon on Linux runs an HTTP server on 127.0.0.1:8076 that accepts CLI commands with no kind of authentication. The vulnerability allows threat actors to lure AtlasVPN users on malicious sites where they can send requests to the local server to execute malicious operations. The researcher says they published the details on Reddit because he couldn't contact the company's security team. The zero-day has been independently confirmed.
Infosec industry
SentinelOne sale drama: After rumors that the company was up for sale and that Wiz was interested in acquiring it, SentinelOne CEO Tomer Weingarten says the company is now not for sale. [Additional coverage in CNBC]
Malwarebytes layoffs: Antivirus maker Malwarebytes has laid off 100 employees. The layoffs come weeks after the company parted ways with its CIO, CTO, and CPO. Malwarebytes CEO Marcin Kleczynski says layoffs are part of a plan to split its consumer and corporate business units. Malwarebytes previously laid off 14% of its workforce in August of last year. [Additional coverage in TechCrunch]
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at how asset inventory tools aren't a substitute for knowing what a business values.




